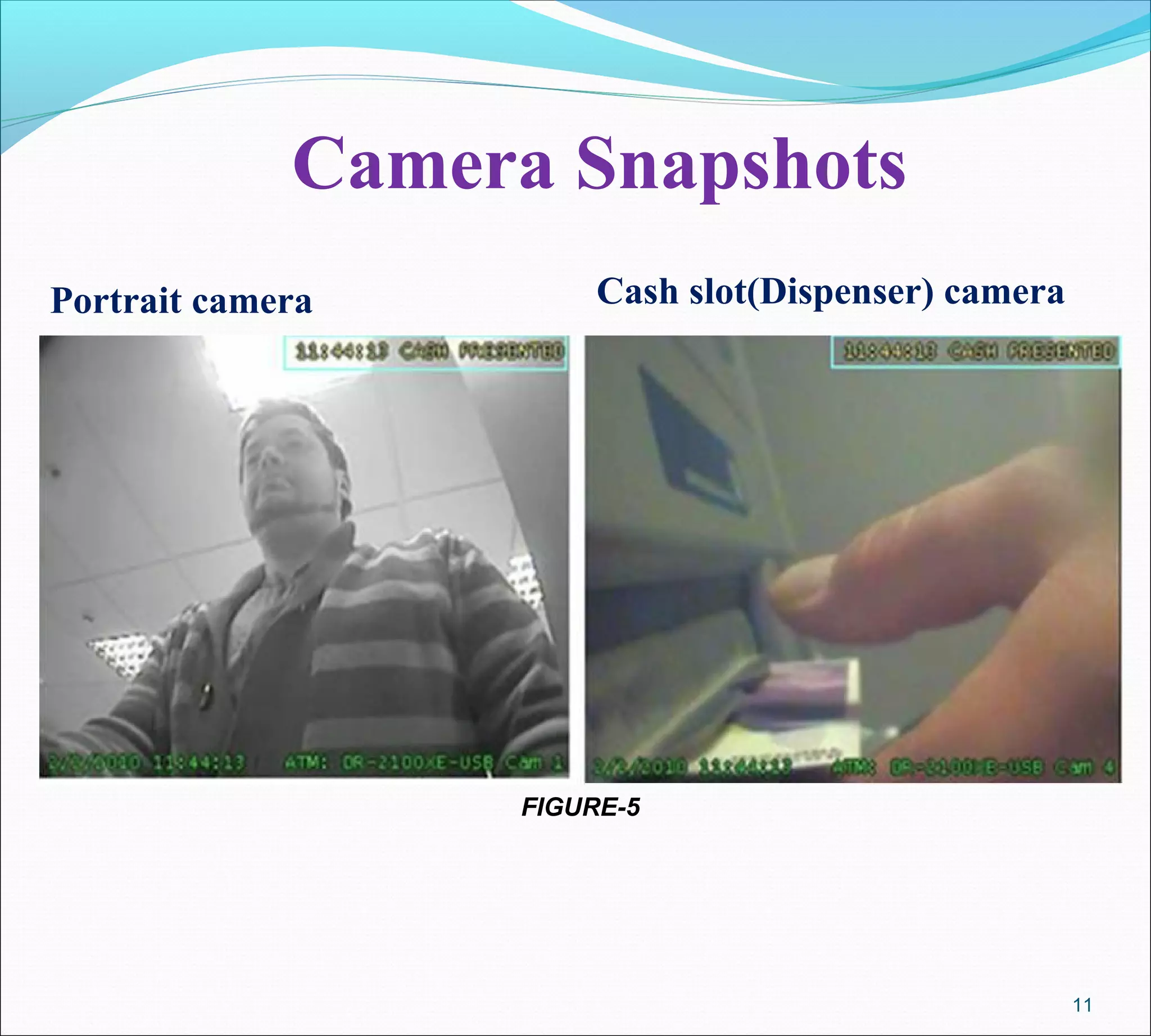
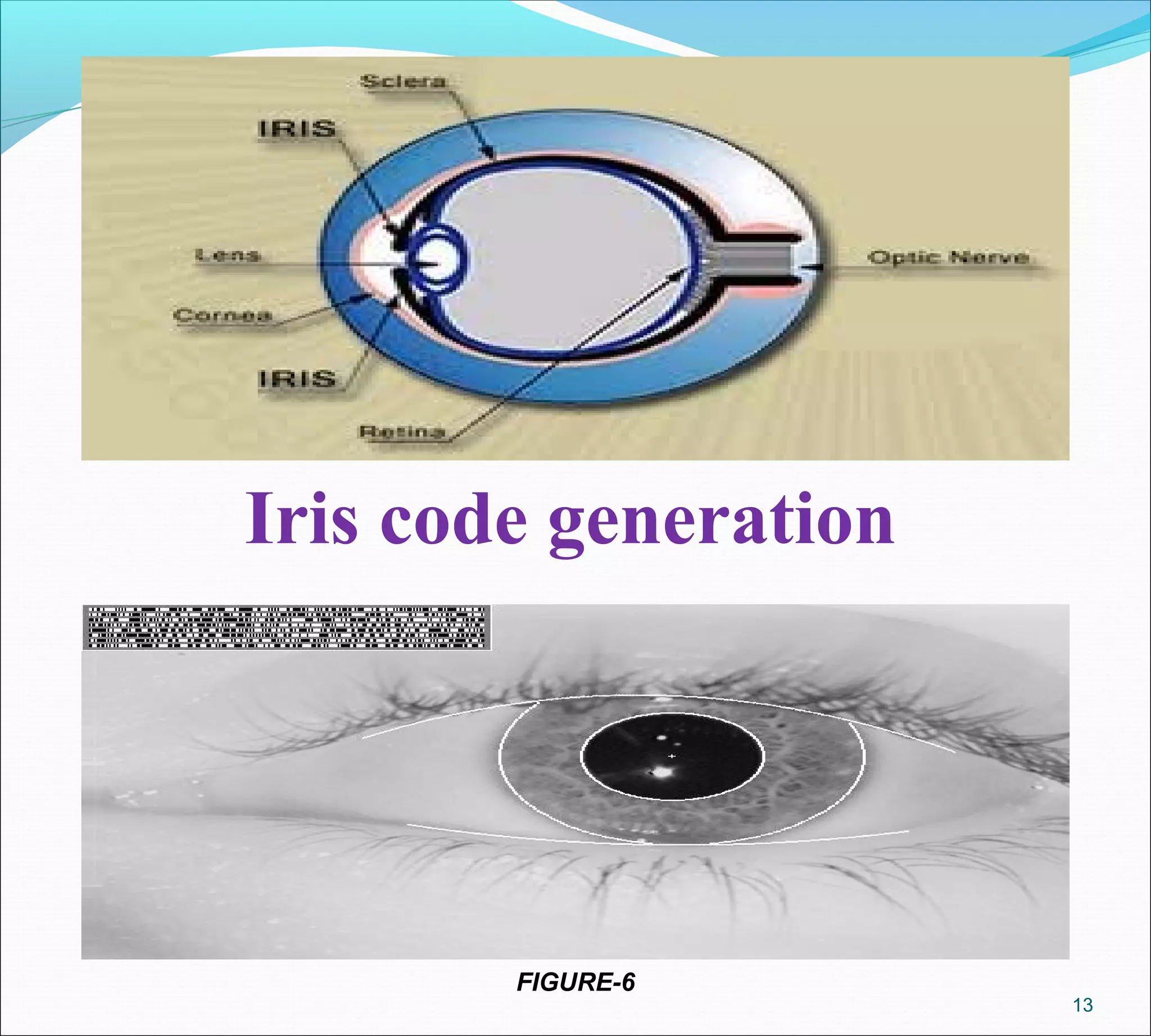
An ATM with facial recognition and iris scanning is proposed to improve security. It would use cameras to capture images of the user's face and iris to match against stored images associated with their bank account, replacing the need for an ATM card and PIN. If the live and stored images match, the user would be verified. This system aims to make ATM transactions more reliable, efficient and secure compared to existing card/PIN verification methods. The document provides background on ATMs, biometric identification techniques, and describes how a facial/iris recognition system could work and the potential benefits.














![REFERENCES
[1] www.nationmaster.com
[2] www.google.co.in
[3] www.atmeye.net
[4] Wikipedia
18](https://image.slidesharecdn.com/526-170608174150/75/AN-ATM-WITH-AN-EYE-BY-SAIKIRAN-PANJALA-18-2048.jpg)
