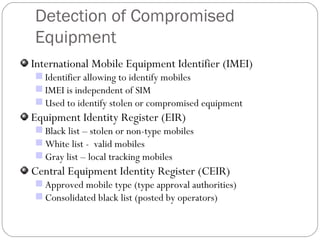
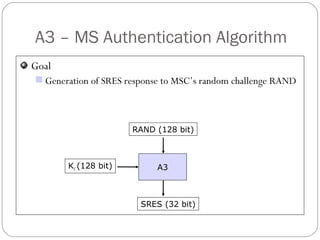
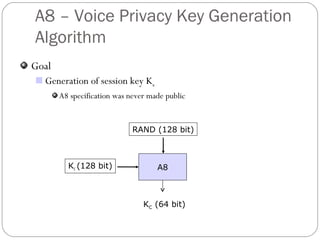
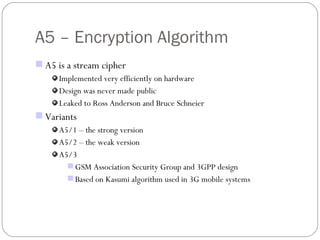
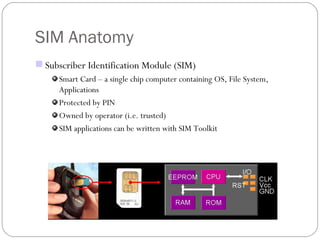
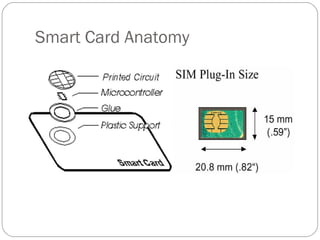
The document summarizes GSM security mechanisms. It discusses GSM security objectives of confidentiality, anonymity, and authentication. It then describes some key GSM security mechanisms like TMSI for subscriber identity protection, key management using Ki, and the A3/A8/A5 authentication and encryption algorithms. It also provides details on the SIM card anatomy and its role in the authentication process.
![Presentation by , 1] Sanket Yavalkar Sardar Patel Institute of Technology,Mumbai ME(EXTC) GSM SECURITY](https://image.slidesharecdn.com/gsmsecurityfinal-111205214021-phpapp01/75/Gsm-security-final-1-2048.jpg)
![Contents…. 1]INTRODUCTION 2] GSM Security Objectives 3]GSM Security Mechanisms 4]SIM Anatomy 5]Algorithms and Attacks 6]CONCLUSION](https://image.slidesharecdn.com/gsmsecurityfinal-111205214021-phpapp01/85/Gsm-security-final-2-320.jpg)