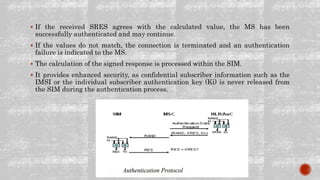
The document outlines the security features and mechanisms of the GSM cellular telecommunications system, emphasizing its methods for maintaining end-to-end confidentiality, subscriber anonymity, and resistance to fraud. Key components include authentication through a challenge-response protocol, encryption via the ciphering algorithm, and the use of temporary identities to protect user privacy. It highlights the importance of secure communications, correct billing, and prevention of fraudulent activities in GSM networks.