The document discusses Universal 2nd Factor (U2F) authentication as a solution to enhance security by replacing passwords with a secure device that generates a unique key pair for each user-service interaction. It outlines the mechanics of U2F, including user verification through device challenges, and emphasizes its resilience against phishing and man-in-the-middle attacks. Additionally, it provides implementation guidance for servers and devices, encouraging engagement with the FIDO Alliance and reference resources.

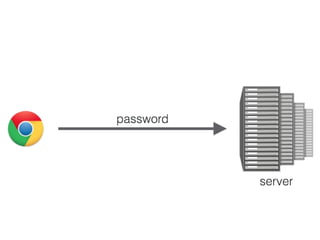






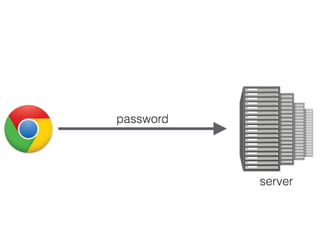







![User Presence API
u2f.register([{
‘version’ : ‘U2F_V2’,
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘appId’: ‘https://www.google.com/facets.json’
}], callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘registrationData’]);
};](https://image.slidesharecdn.com/presentation-fidou2f1-160324171357/85/FIDO-U2F-1-0-Specs-Overview-and-Insights-17-320.jpg)
![User Presence API
u2f.register([{
‘version’ : ‘U2F_V2’,
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘appId’: ‘https://www.google.com/facets.json’
}], callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘registrationData’]);
};
{
"typ":"register",
"challenge":"KSDJsdASAS-AIS_AsS",
"cid_pubkey": {
"kty":"EC",
"crv":"P-256",
"x":"HzQwlfXX7Q4S5MtCRMzPO9tOyWjBqRl4tJ8",
"y":"XVguGFLIZx1fXg375hi4-7-BxhMljw42Ht4"
},
"origin":"https://accounts.google.com"
}](https://image.slidesharecdn.com/presentation-fidou2f1-160324171357/85/FIDO-U2F-1-0-Specs-Overview-and-Insights-18-320.jpg)
![User Presence API
u2f.sign([{
‘version’ : ‘U2F_V2’,
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘appId’: ‘https://www.google.com/facets.json’,
‘keyHandle’: ‘JkjhdsfkjSDFKJ_ld-sadsAJDKLSAD’
}], callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘signatureData’],
response[‘keyHandle’]);
};](https://image.slidesharecdn.com/presentation-fidou2f1-160324171357/85/FIDO-U2F-1-0-Specs-Overview-and-Insights-19-320.jpg)
![User Presence API
u2f.sign([{
‘version’ : ‘U2F_V2’,
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘appId’: ‘https://www.google.com/facets.json’,
‘keyHandle’: ‘JkjhdsfkjSDFKJ_ld-sadsAJDKLSAD’
}], callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘signatureData’],
response[‘keyHandle’]);
};
{
"typ":"authenticate",
"challenge":"KSDJsdASAS-AIS_AsS",
"cid_pubkey": {
"kty":"EC",
"crv":"P-256",
"x":"HzQwlfXX7Q4S5MtCRMzPO9tOyWjBqRl4tJ8",
"y":"XVguGFLIZx1fXg375hi4-7-BxhMljw42Ht4"
},
"origin":"https://accounts.google.com"
}](https://image.slidesharecdn.com/presentation-fidou2f1-160324171357/85/FIDO-U2F-1-0-Specs-Overview-and-Insights-20-320.jpg)