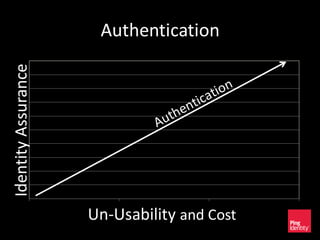
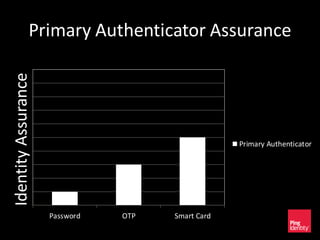
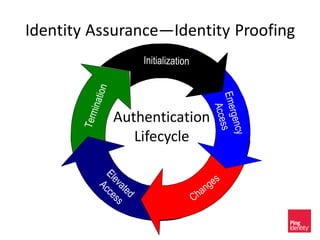
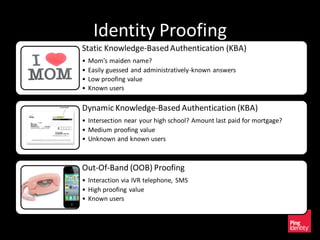
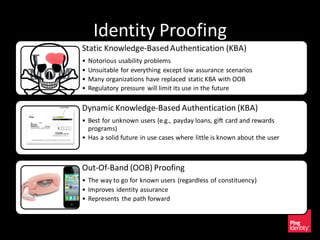
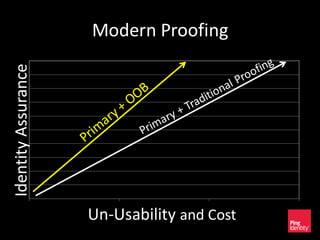
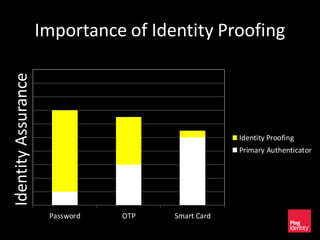
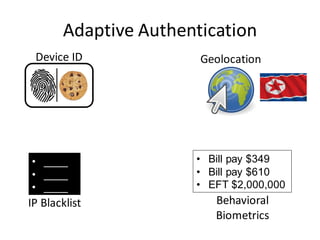
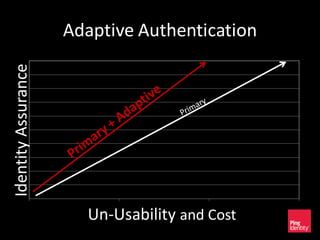
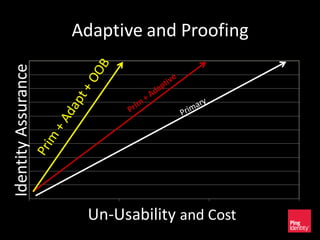
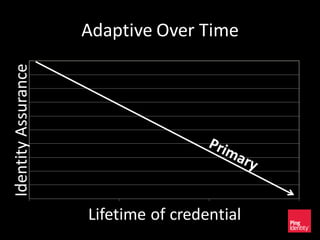
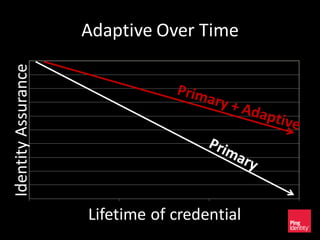
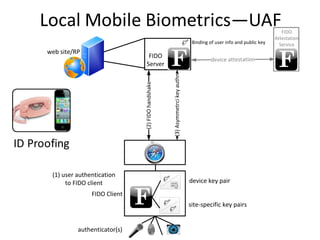
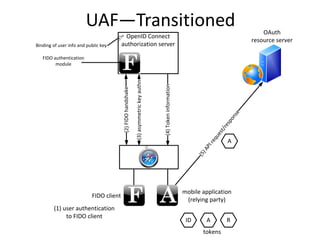
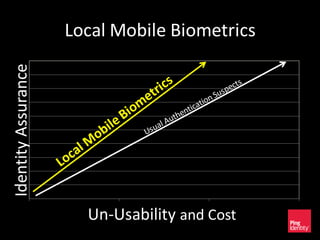
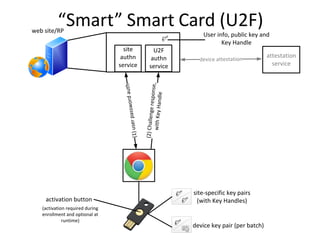
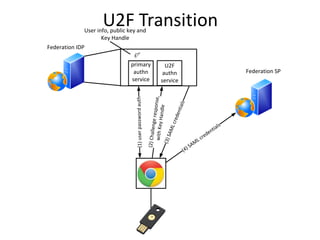
The document discusses the evolution of authentication methods, emphasizing the shift from traditional systems like passwords to modern solutions using biometrics and protocols such as FIDO. It outlines the components of identity assurance, the roles of primary and secondary authenticators, and various identity proofing techniques, highlighting the advantages of adaptive authentication and out-of-band proofing. The FIDO framework is presented as a significant advancement, with local mobile biometrics and universal second factor protocols aiming to enhance security and user experience.