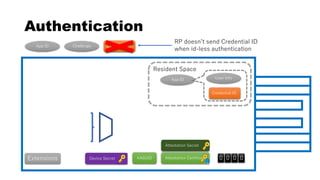
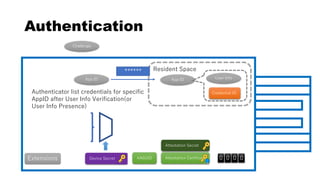
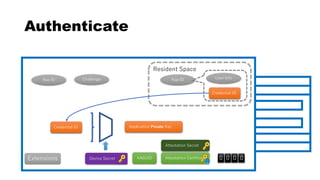
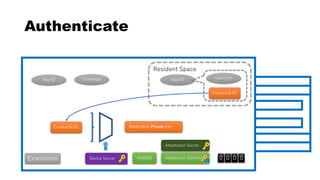
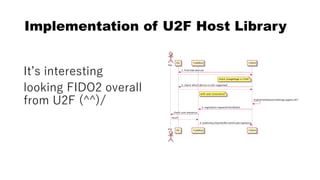
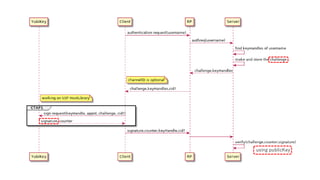
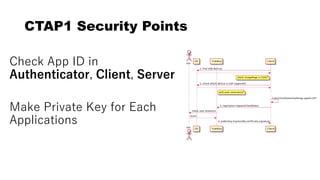
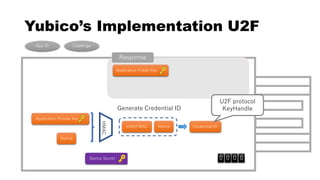
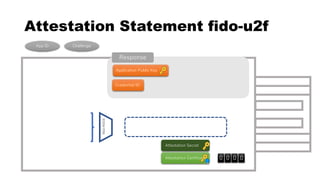
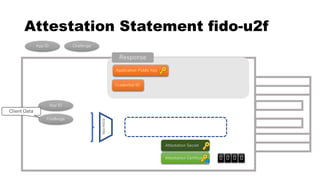
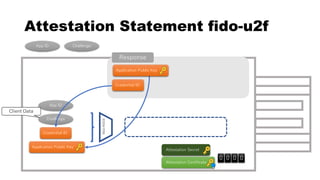
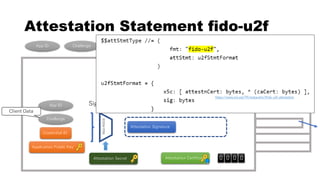
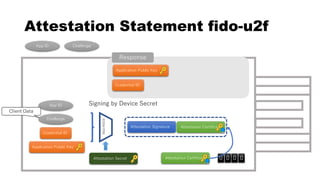
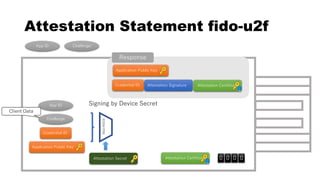
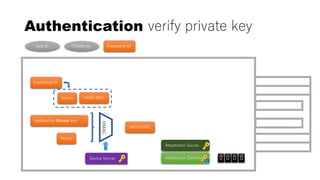
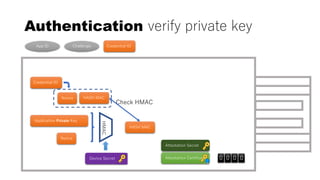
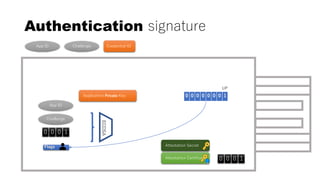
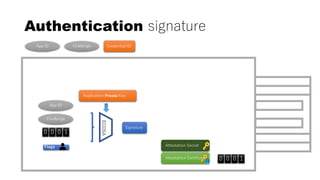
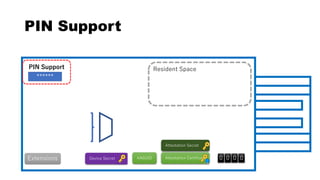
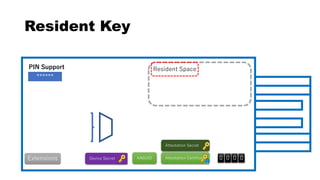
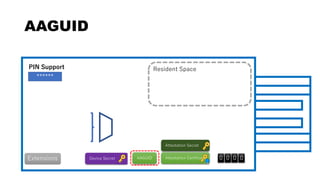
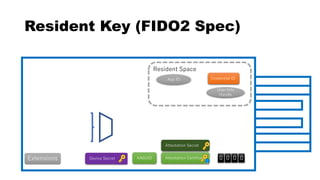
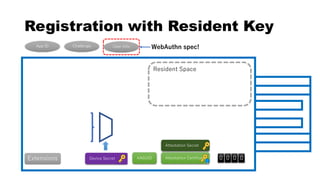
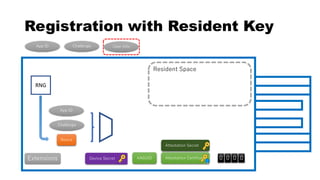
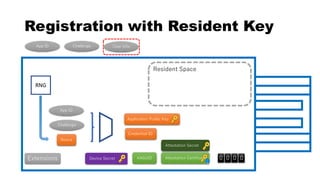
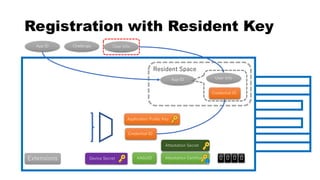
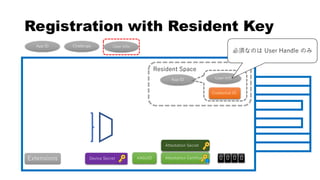
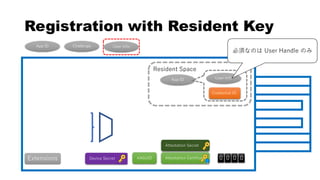
This document discusses Yubico's implementation of the U2F and FIDO2 authentication protocols. It covers key topics like key generation during registration, signature generation during authentication using an application private key, and the use of attestation certificates to verify the authenticator. Resident keys, PIN support, and extensions are also mentioned as differences between U2F and FIDO2.

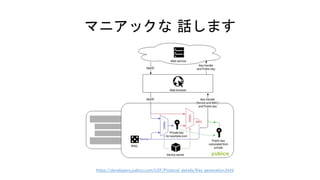


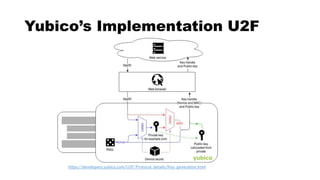
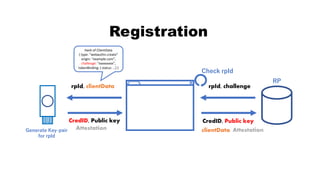
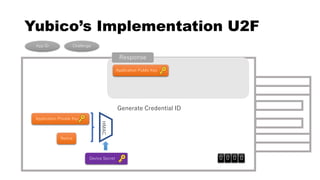
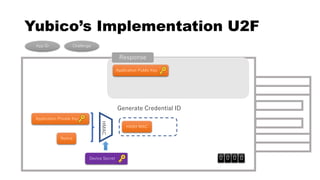
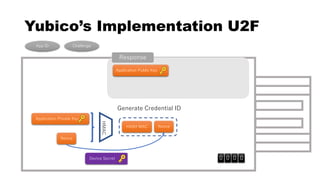
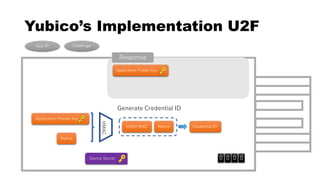

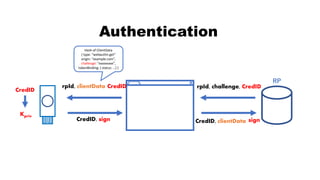
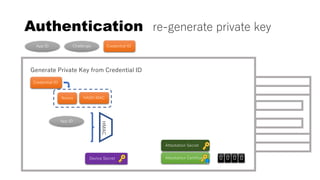
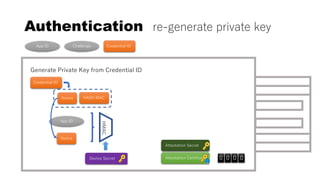
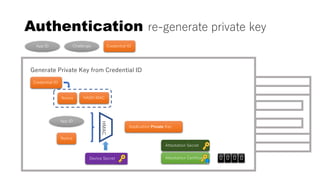
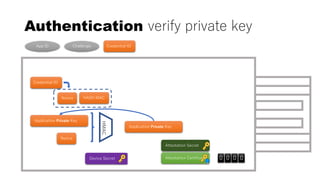




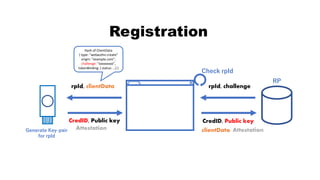
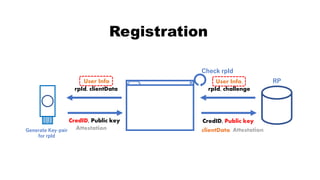
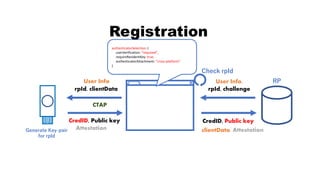
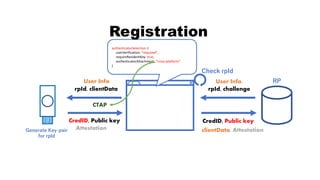
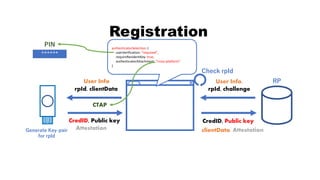
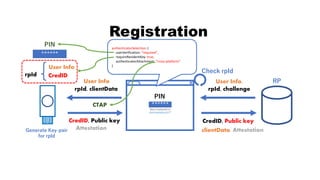
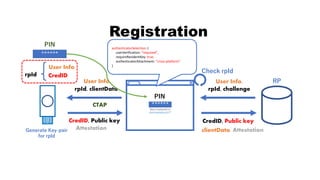
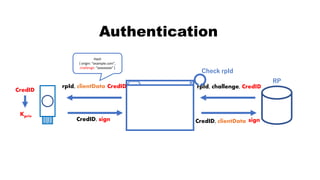
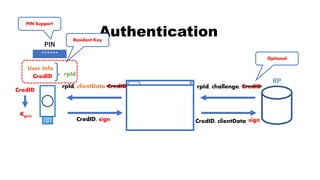
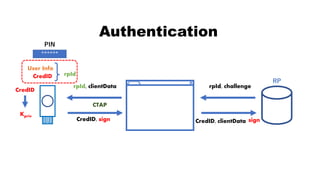
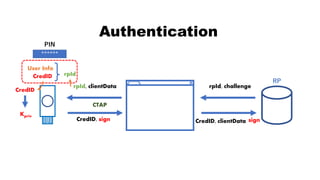
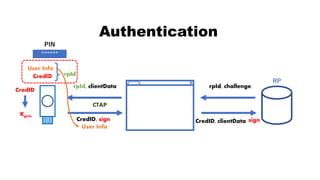
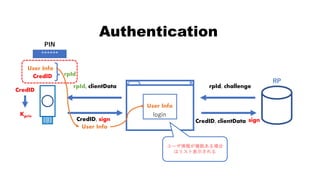
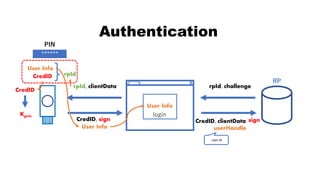
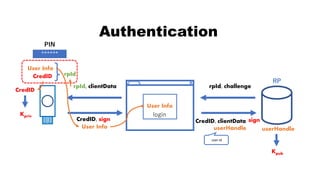
![rpId, clientData
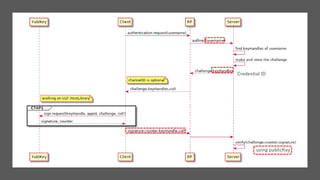
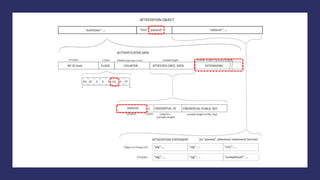
CredID, sign CredID, clientData
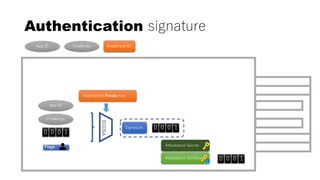
Authentication
CredID
sign
Kpriv
User Info
CredID
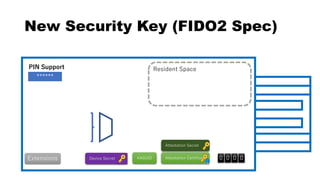
******
PIN
rpId
RP
rpId, challenge, CredID
[空にする]](https://image.slidesharecdn.com/fidoattestation-no-animation-181210150850/85/U2F-FIDO2-implementation-of-YubiKey-62-320.jpg)