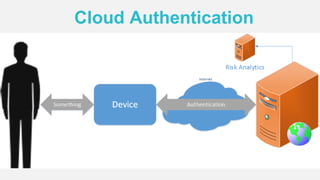
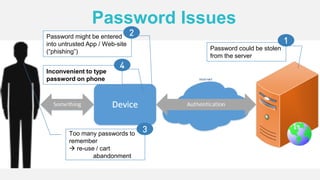
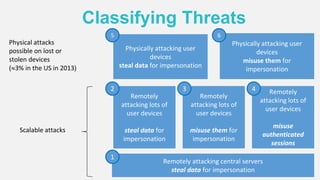
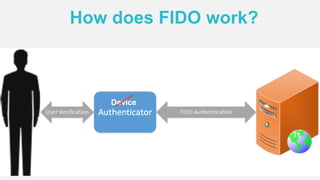
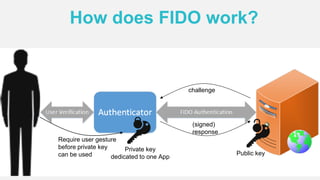
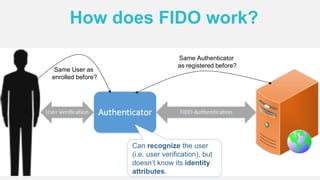
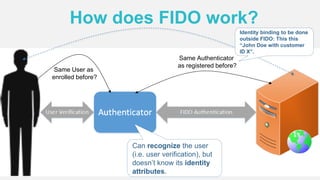
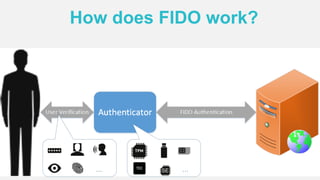
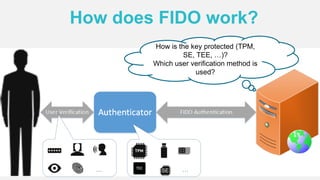
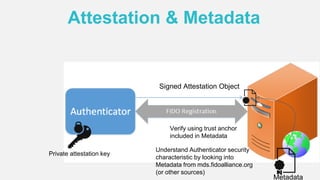
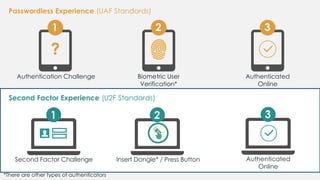
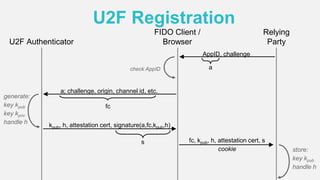
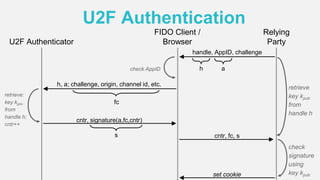
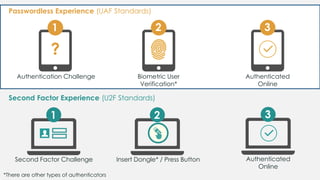
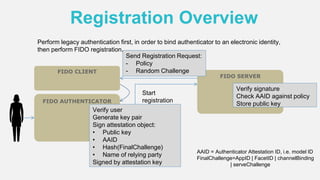
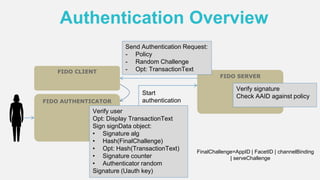
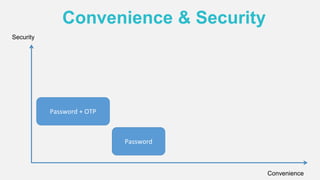
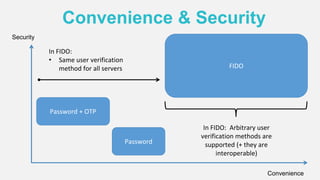
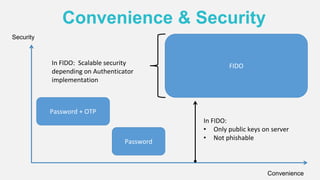
The document discusses the security of authentication, detailing various threats such as phishing and server data theft, and introduces FIDO (Fast Identity Online) as a solution. It explains how FIDO works with private and public keys for user verification, and highlights its advantages such as passwordless experiences and interoperability. The conclusion emphasizes FIDO's ability to separate user verification from authentication, supporting diverse verification methods while ensuring security and convenience.