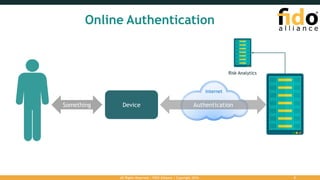
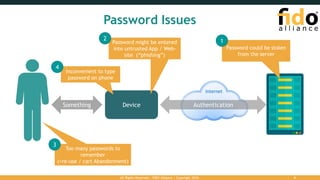
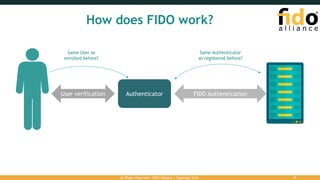
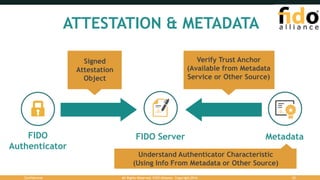
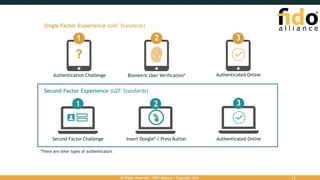
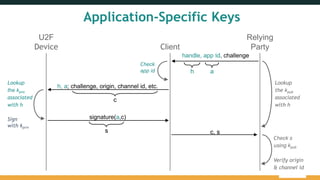
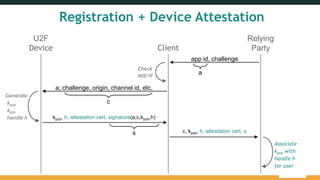
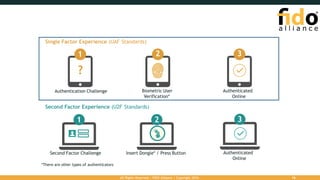
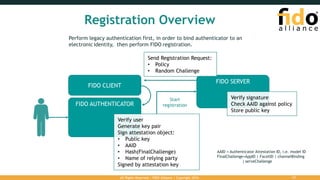
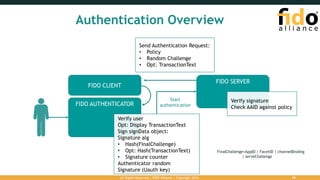
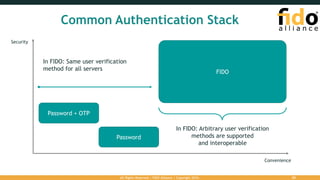
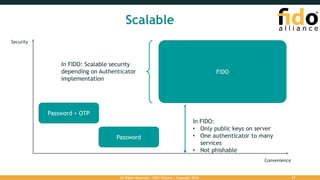
The document outlines the FIDO (Fast Identity Online) authentication framework, highlighting security vulnerabilities associated with traditional password systems and demonstrating how FIDO addresses these issues through user verification methods and public key cryptography. It explains the process of FIDO registration and authentication, emphasizing the need for a user gesture and the secure management of cryptographic keys. The conclusion stresses FIDO's capability to provide scalable convenience and security while supporting diverse user verification methods.