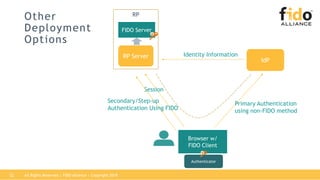
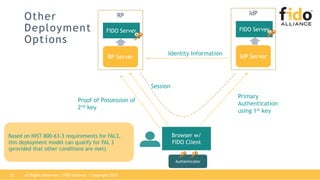
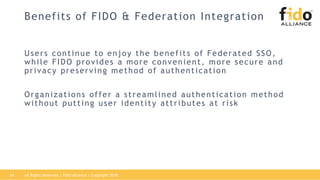
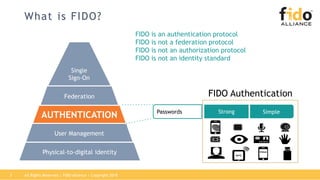
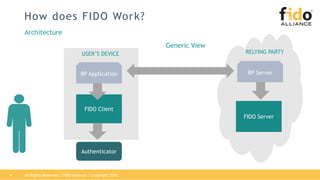
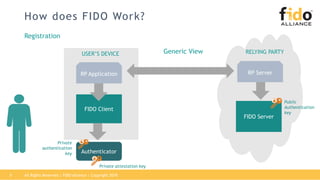
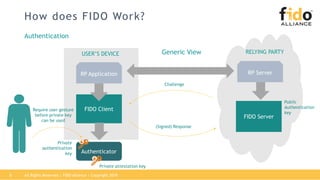
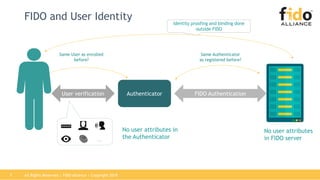
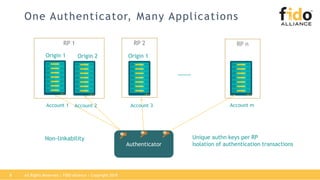
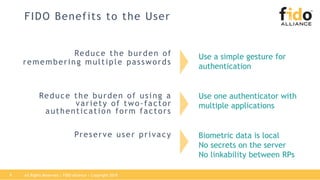
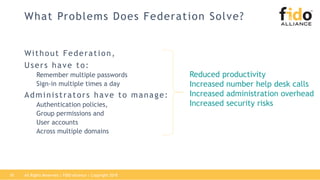
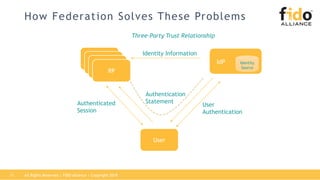
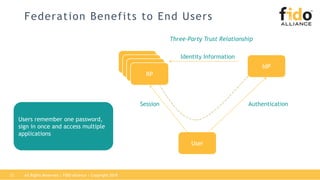
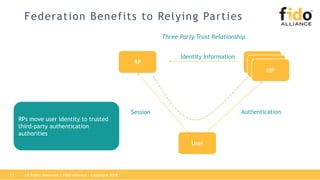
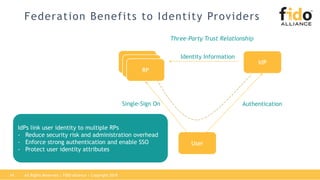
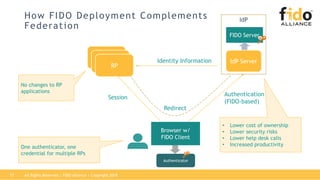
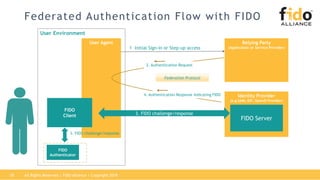
The document outlines best practices for integrating FIDO authentication with federation protocols to enhance enterprise security and user experience. It explains how FIDO serves as an efficient and user-friendly authentication method, reducing password burdens while complementing federated identity management. Additionally, the report emphasizes the benefits for organizations and users alike, including improved security, reduced help desk calls, and streamlined access to multiple applications.





![Use acr_values in OIDC for JIT
enforcement
Sample OIDC Request /Response
EndpointURI: https://tenant.server.example.com/oidc/auth
Http Parameters: {
response_type: id_token,
client_id: rp_client,
response_mode: query,
redirect_uri: https://rp.example.com/oidc-rp/,
scope: openid,
……
acr_values: phr phrh mfa
RedirectURI: https://rp.example.com/oidc-rp/
Http Parameters: {
…….
'id_token' content:
{
"auth_time":1490898779,
"exp":1490899139,
"sub":"someone@example.com",
…….
"iss":" https://tenant.server.example.com/oidc-fe",
"iat":1490898779,
"acr":“phrh",
"amr":[“hwk"]
}
}
ACR policy identifiers that can be satisfied by FIDO Authenticators are defined OpenID Connect (EAP) ACR Values specification
All Rights Reserved | FIDO Alliance | Copyright 201821](https://image.slidesharecdn.com/federationfidowebinarpresentationweb-180323183439/85/Integrating-FIDO-Authentication-Federation-Protocols-21-320.jpg)