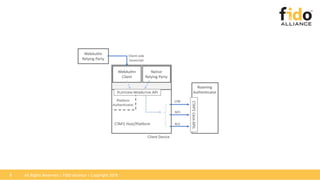
The document outlines the FIDO2 and WebAuthn standards for strong authentication, detailing the two main specifications: CTAP2, which facilitates communication between client devices and authenticators, and WebAuthn, which serves as the web API for authentication. It also highlights the roles of various entities such as relying parties, clients, platform and roaming authenticators, and interoperability with previous standards like U2F and CTAP1. Furthermore, it discusses Microsoft's implementation and plans for WebAuthn in their services and products.