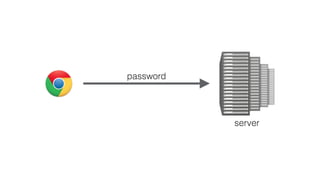
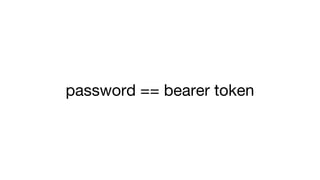
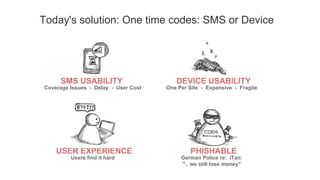
The document outlines the Universal 2nd Factor (U2F) authentication protocol developed by Google, emphasizing its security against phishing through the use of a single device for multiple services and unique public key cryptography. It describes how U2F works, including device registration, key generation, and user verification processes. Additionally, it discusses implementation considerations for servers and service providers, as well as future developments in compatibility with various platforms and token types.

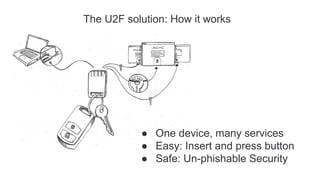









![User Presence API
u2f.register({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};](https://image.slidesharecdn.com/u2f-fido-balfanz-16x9-140806083406-phpapp02/85/CIS14-An-Overview-of-FIDO-s-Universal-2nd-Factor-U2F-Specification-17-320.jpg)
![u2f..handleRegistrationRequest({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};
User Presence API{
"typ":"register",
"challenge":"KSDJsdASAS-AIS_AsS",
"cid_pubkey": {
"kty":"EC",
"crv":"P-256",
"x":"HzQwlfXX7Q4S5MtCRMzPO9tOyWjBqRl4tJ8",
"y":"XVguGFLIZx1fXg375hi4-7-BxhMljw42Ht4"
},
"origin":"https://accounts.google.com"
}](https://image.slidesharecdn.com/u2f-fido-balfanz-16x9-140806083406-phpapp02/85/CIS14-An-Overview-of-FIDO-s-Universal-2nd-Factor-U2F-Specification-18-320.jpg)
![User Presence API
u2f.sign({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’,
‘key_handle’: ‘JkjhdsfkjSDFKJ_ld-sadsAJDKLSAD’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};](https://image.slidesharecdn.com/u2f-fido-balfanz-16x9-140806083406-phpapp02/85/CIS14-An-Overview-of-FIDO-s-Universal-2nd-Factor-U2F-Specification-19-320.jpg)
![User Presence API
u2f.sign({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’,
‘key_handle’: ‘JkjhdsfkjSDFKJ_ld-sadsAJDKLSAD’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};
{
"typ":"authenticate",
"challenge":"KSDJsdASAS-AIS_AsS",
"cid_pubkey": {
"kty":"EC",
"crv":"P-256",
"x":"HzQwlfXX7Q4S5MtCRMzPO9tOyWjBqRl4tJ8",
"y":"XVguGFLIZx1fXg375hi4-7-BxhMljw42Ht4"
},
"origin":"https://accounts.google.com"
}](https://image.slidesharecdn.com/u2f-fido-balfanz-16x9-140806083406-phpapp02/85/CIS14-An-Overview-of-FIDO-s-Universal-2nd-Factor-U2F-Specification-20-320.jpg)





