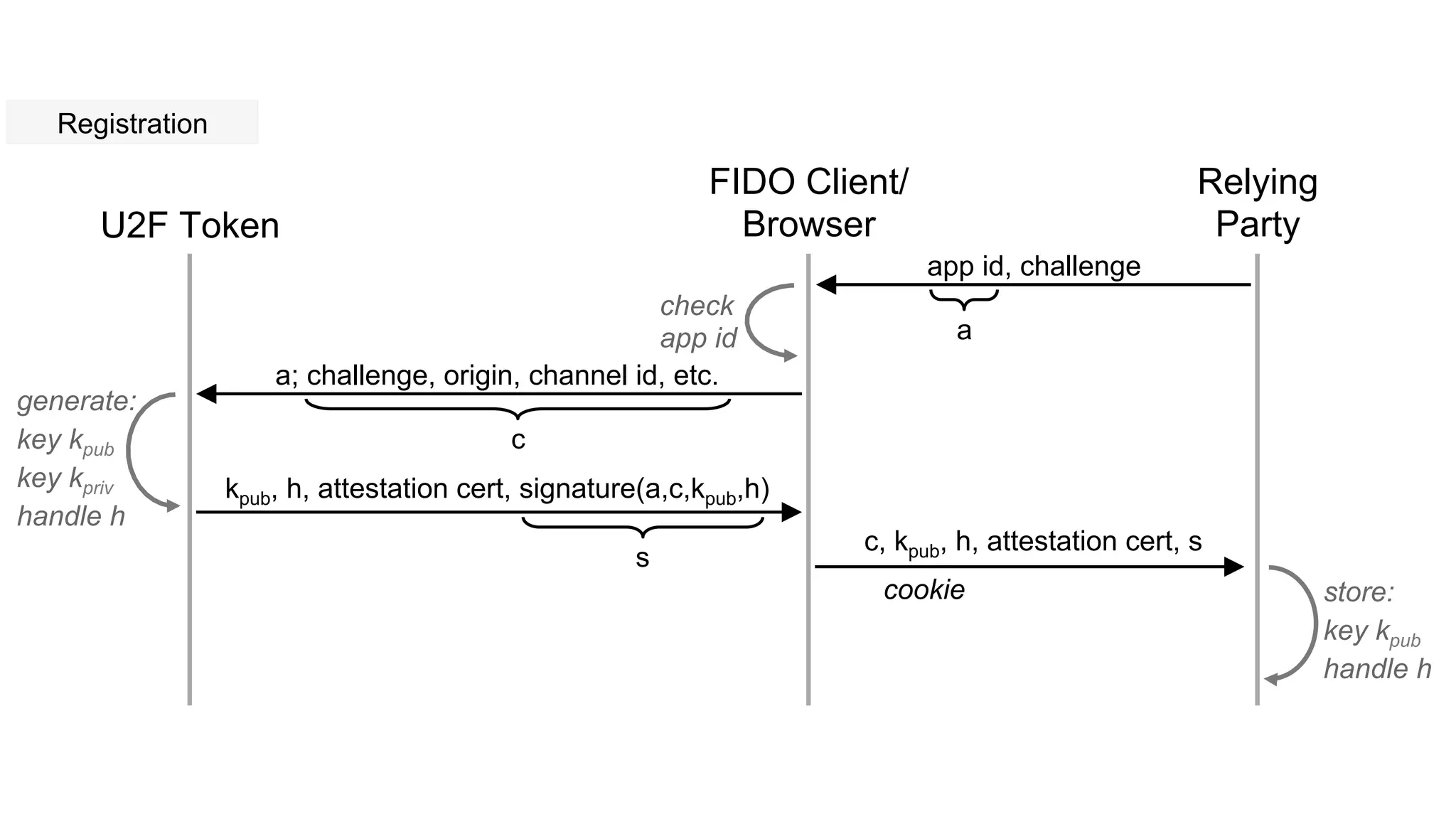
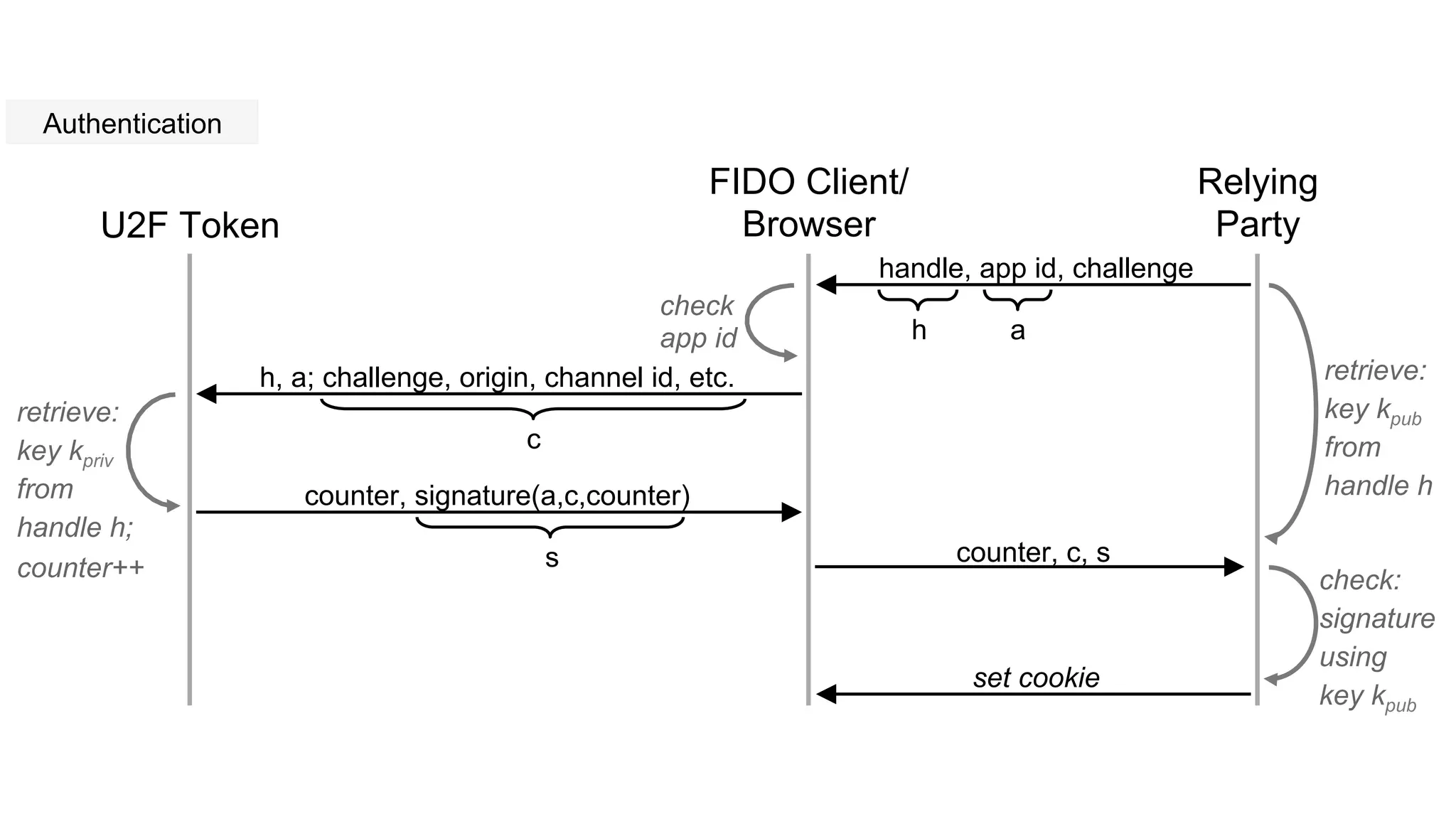
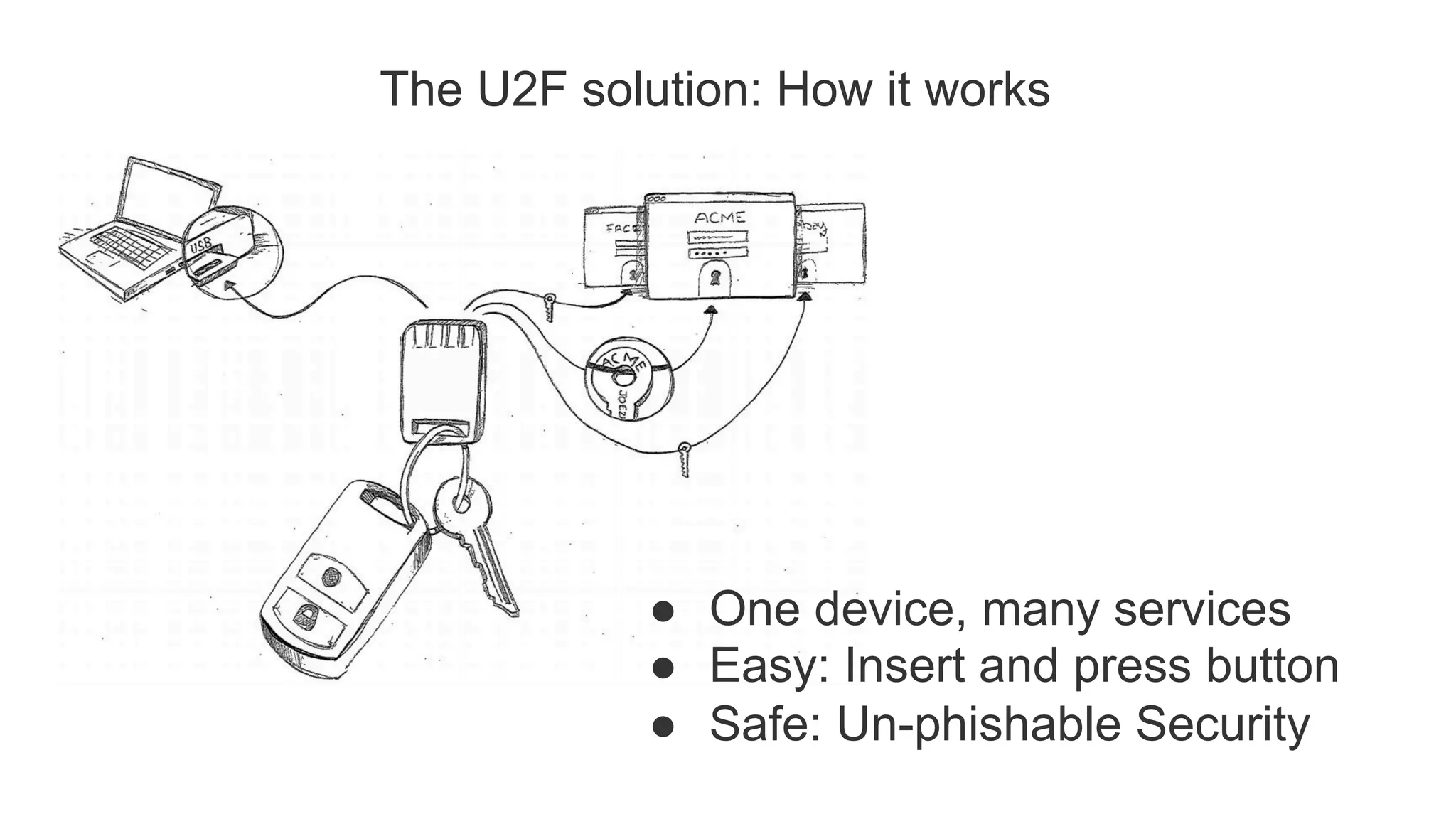
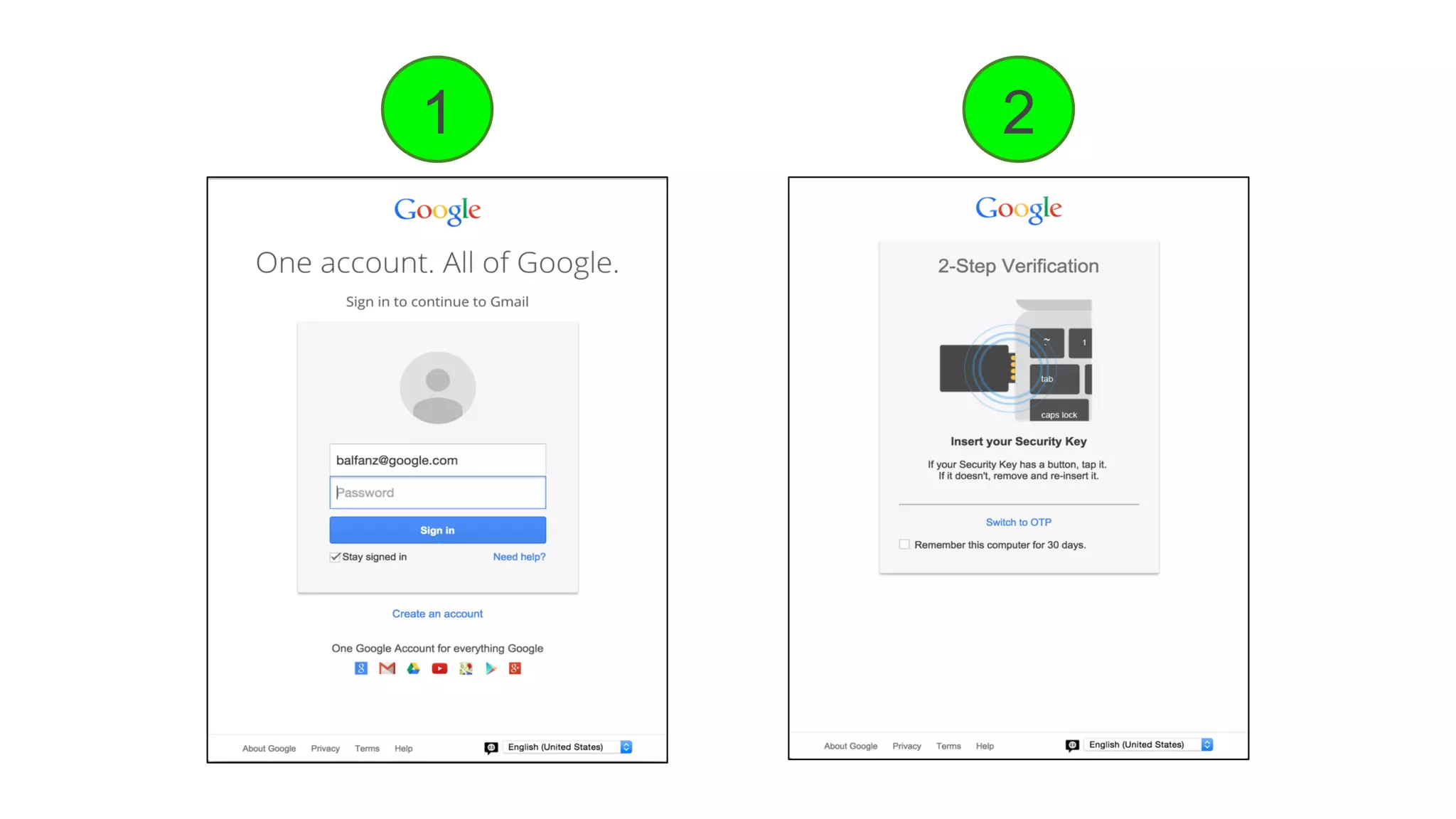
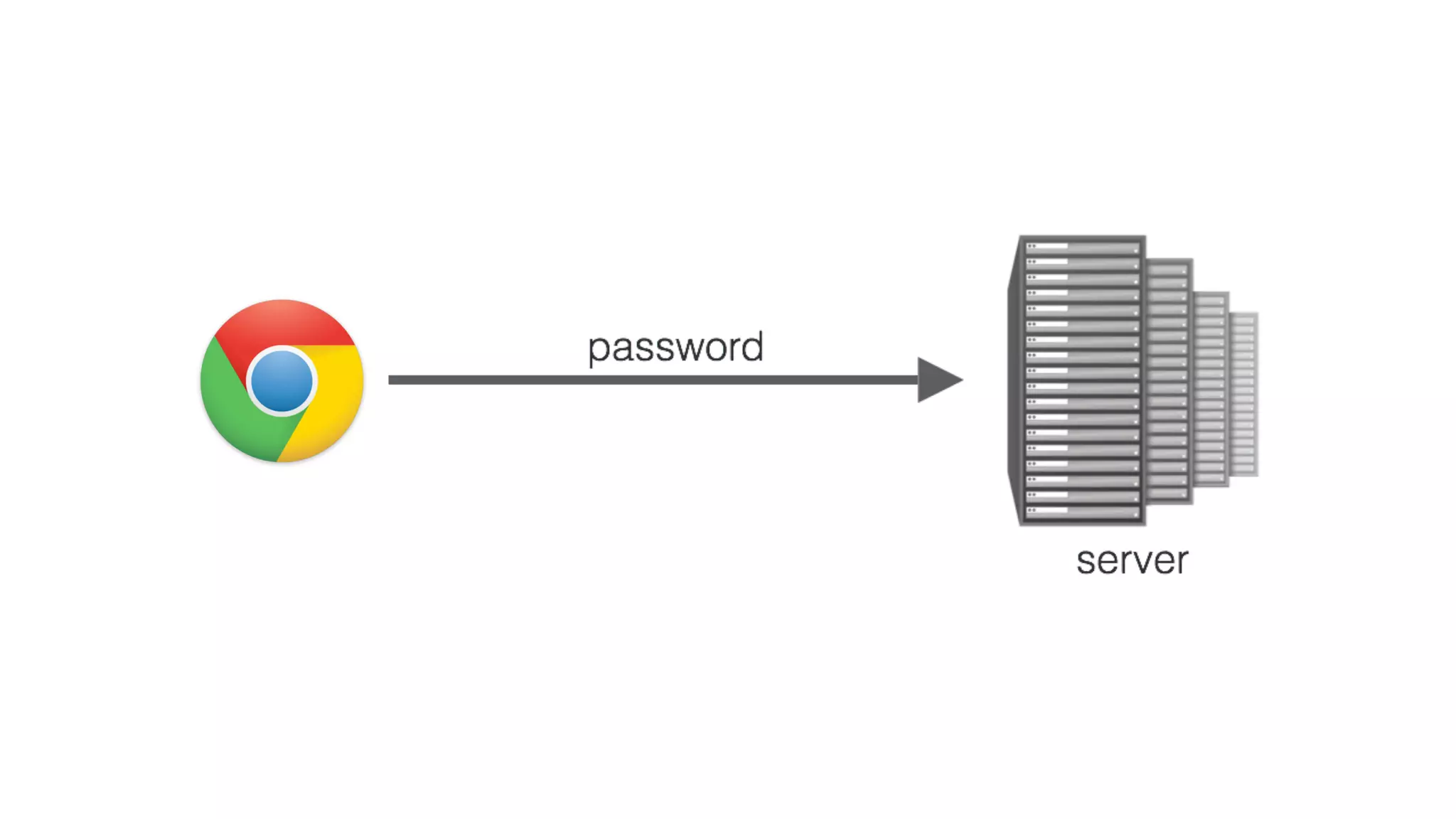
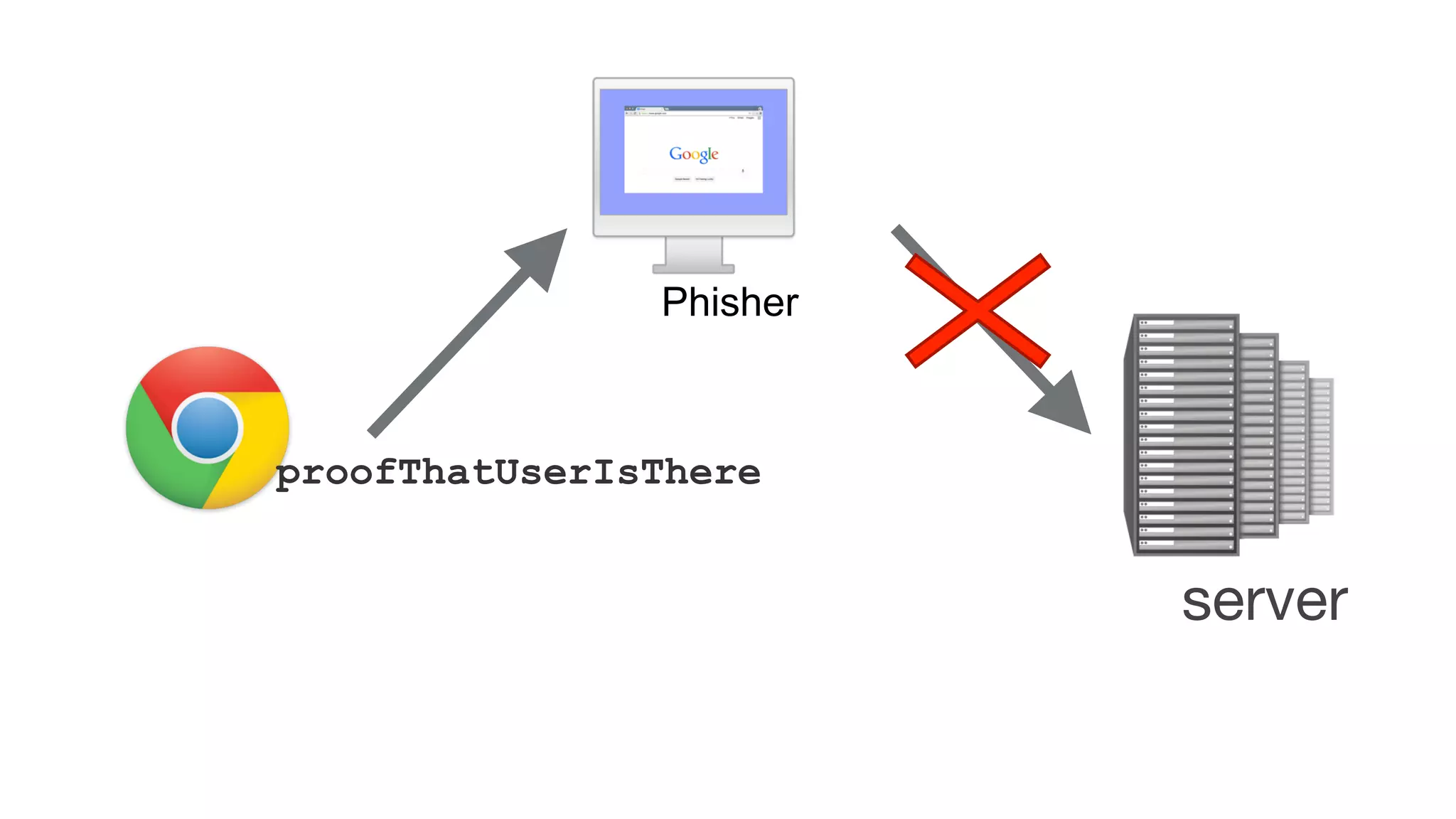
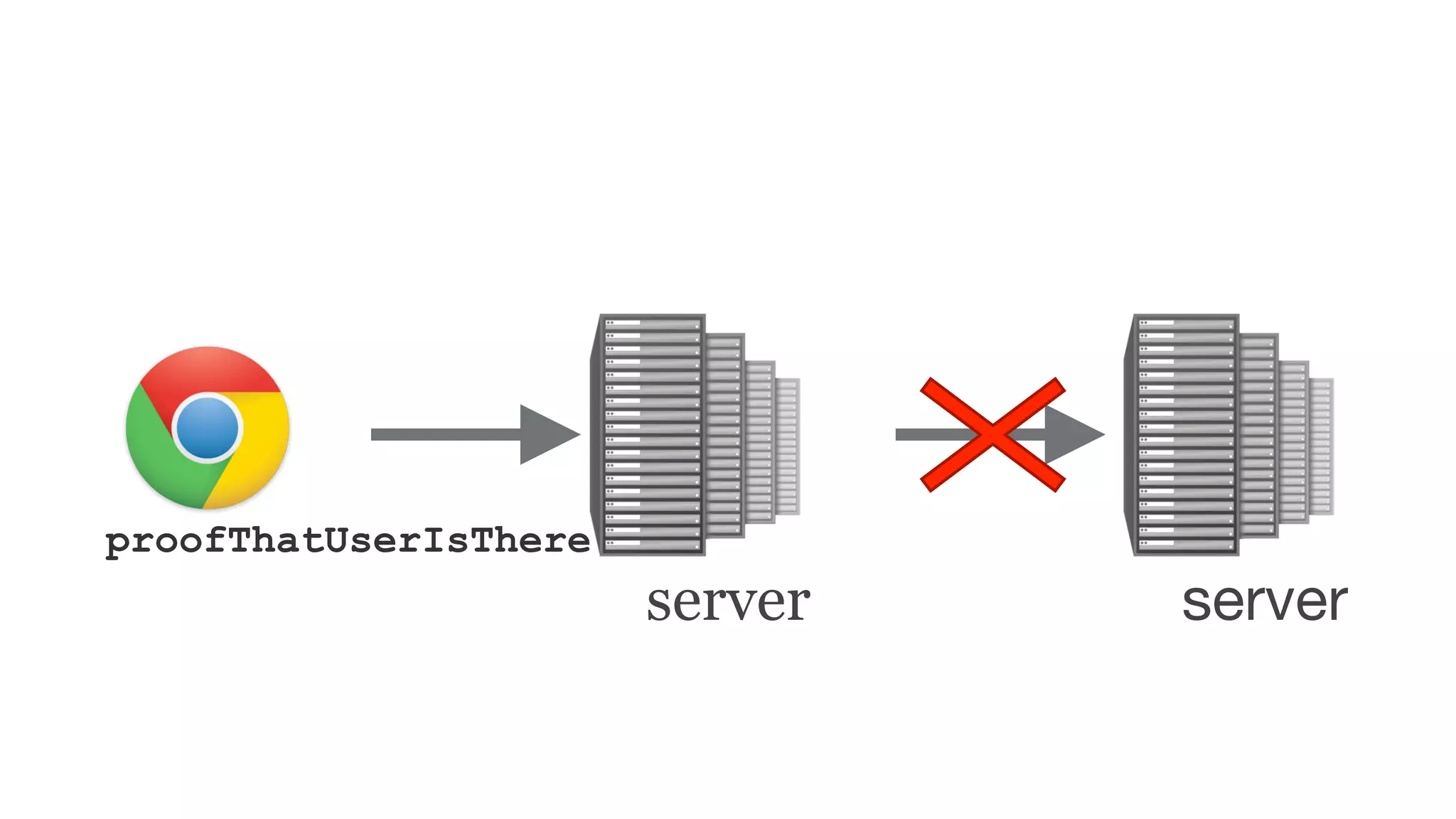
The document summarizes the FIDO U2F security standard for two-factor authentication. It describes how U2F works by having a single authentication device that can be used across multiple services. When a user wants to log in, their U2F device signs a challenge from the website to prove the user is present, with the signature verified by the website. The document outlines the U2F protocol and APIs, explaining the registration and authentication flows. It also provides guidance for websites wanting to implement U2F login and manufacturers wanting to produce U2F security keys.


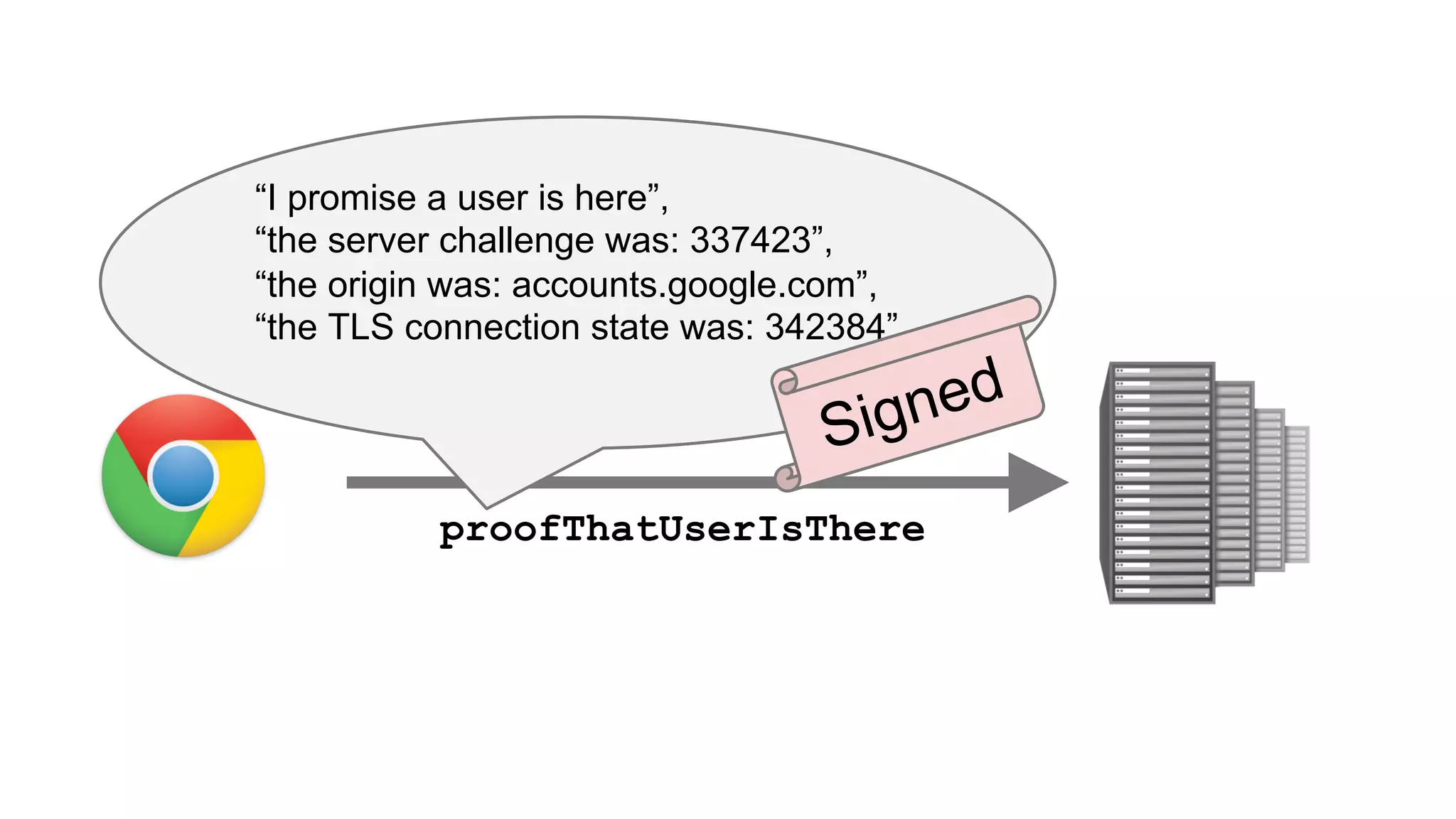
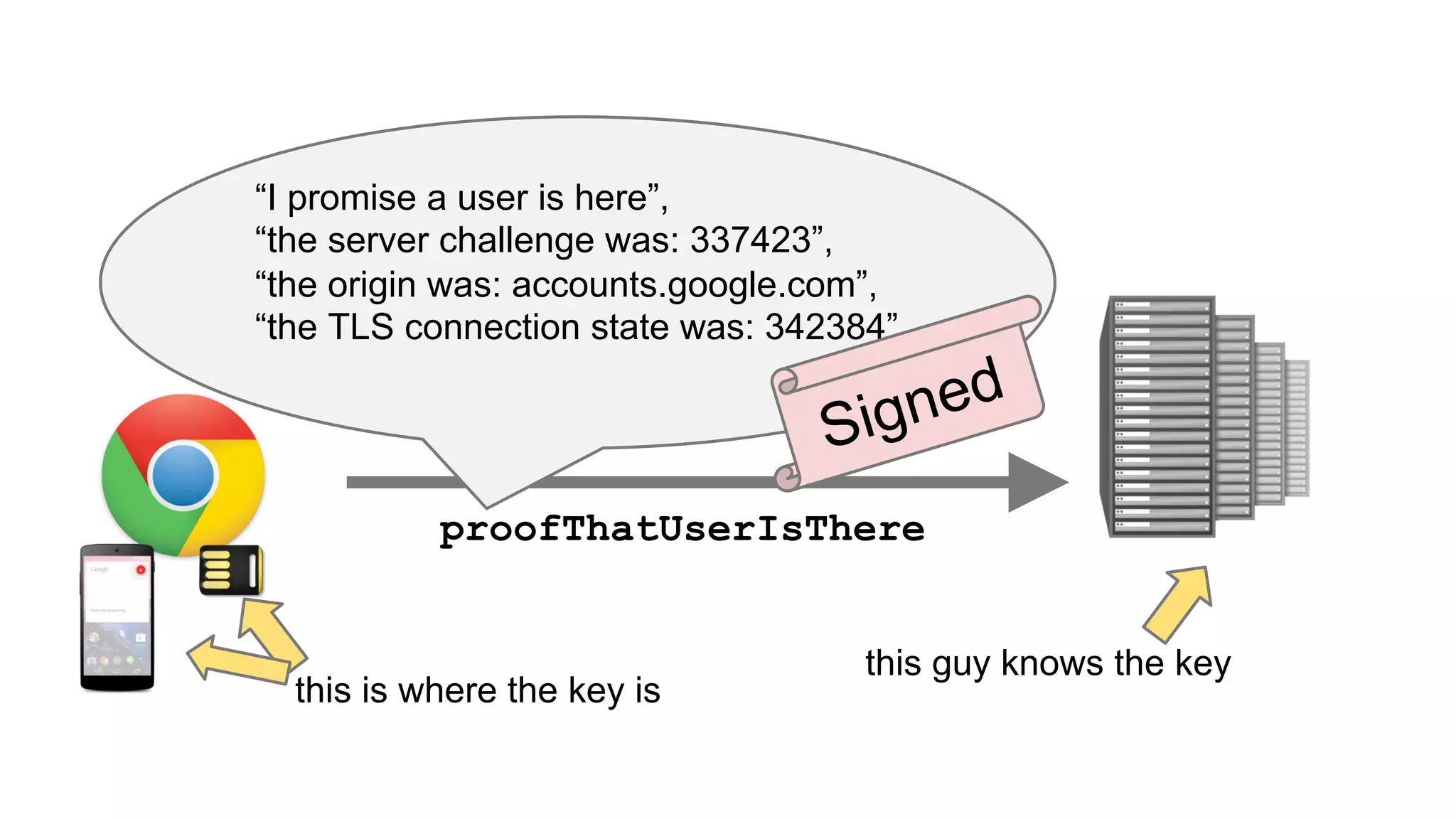
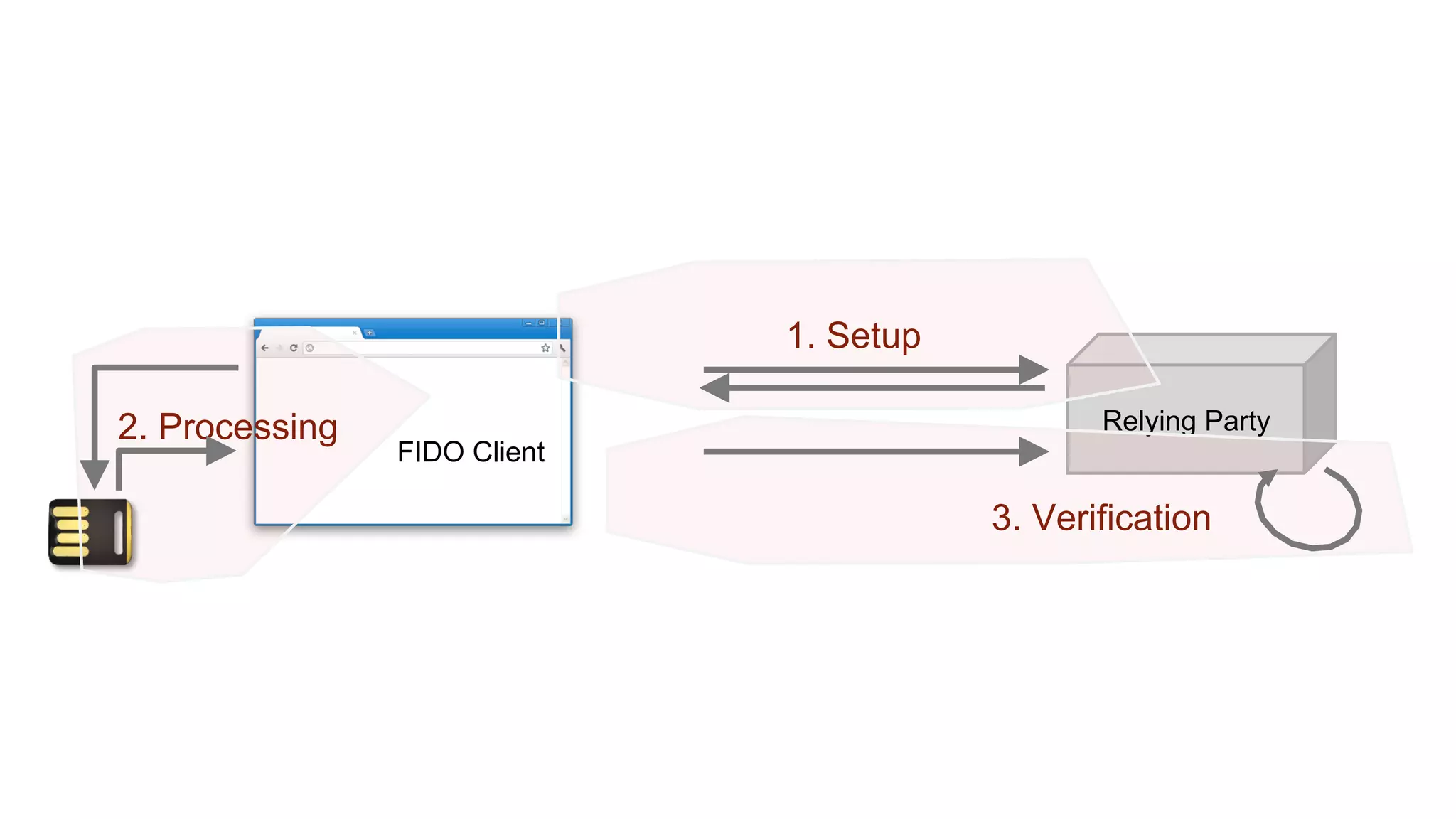
![User Presence API
u2f.register({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};](https://image.slidesharecdn.com/fidou2fin10minutescis2015-150622164512-lva1-app6891/75/Fido-u2-f-in-10-minutes-cis-2015-11-2048.jpg)
![u2f..handleRegistrationRequest({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};
User Presence API{
"typ":"register",
"challenge":"KSDJsdASAS-AIS_AsS",
"cid_pubkey": {
"kty":"EC",
"crv":"P-256",
"x":"HzQwlfXX7Q4S5MtCRMzPO9tOyWjBqRl4tJ8",
"y":"XVguGFLIZx1fXg375hi4-7-BxhMljw42Ht4"
},
"origin":"https://accounts.google.com"
}](https://image.slidesharecdn.com/fidou2fin10minutescis2015-150622164512-lva1-app6891/75/Fido-u2-f-in-10-minutes-cis-2015-12-2048.jpg)
![User Presence API
u2f.sign({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’,
‘key_handle’: ‘JkjhdsfkjSDFKJ_ld-sadsAJDKLSAD’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};](https://image.slidesharecdn.com/fidou2fin10minutescis2015-150622164512-lva1-app6891/75/Fido-u2-f-in-10-minutes-cis-2015-13-2048.jpg)
![User Presence API
u2f.sign({
‘challenge’: ‘KSDJsdASAS-AIS_AsS’,
‘app_id’: ‘https://www.google.com/facets.json’,
‘key_handle’: ‘JkjhdsfkjSDFKJ_ld-sadsAJDKLSAD’
}, callback);
callback = function(response) {
sendToServer(
response[‘clientData’],
response[‘tokenData’]);
};
{
"typ":"authenticate",
"challenge":"KSDJsdASAS-AIS_AsS",
"cid_pubkey": {
"kty":"EC",
"crv":"P-256",
"x":"HzQwlfXX7Q4S5MtCRMzPO9tOyWjBqRl4tJ8",
"y":"XVguGFLIZx1fXg375hi4-7-BxhMljw42Ht4"
},
"origin":"https://accounts.google.com"
}](https://image.slidesharecdn.com/fidou2fin10minutescis2015-150622164512-lva1-app6891/75/Fido-u2-f-in-10-minutes-cis-2015-14-2048.jpg)