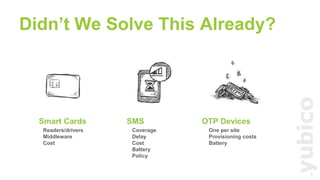
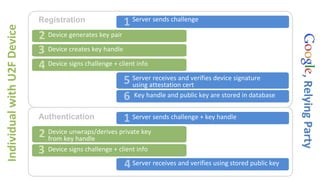
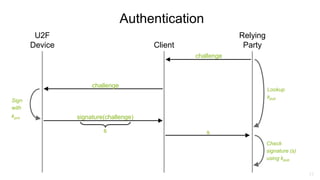
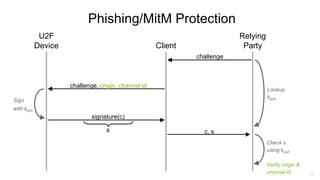
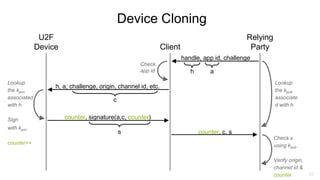
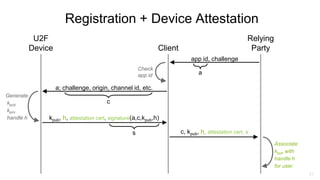
U2F (Universal 2nd Factor) is a simple, secure, and scalable 2-factor authentication standard that uses public key cryptography. It protects against phishing and man-in-the-middle attacks by requiring the insertion of a security key that signs a challenge along with the website domain and TLS channel ID. U2F addresses limitations of SMS one-time passwords and smart cards by providing a user-friendly solution that is compatible across multiple services using only a single physical security key.