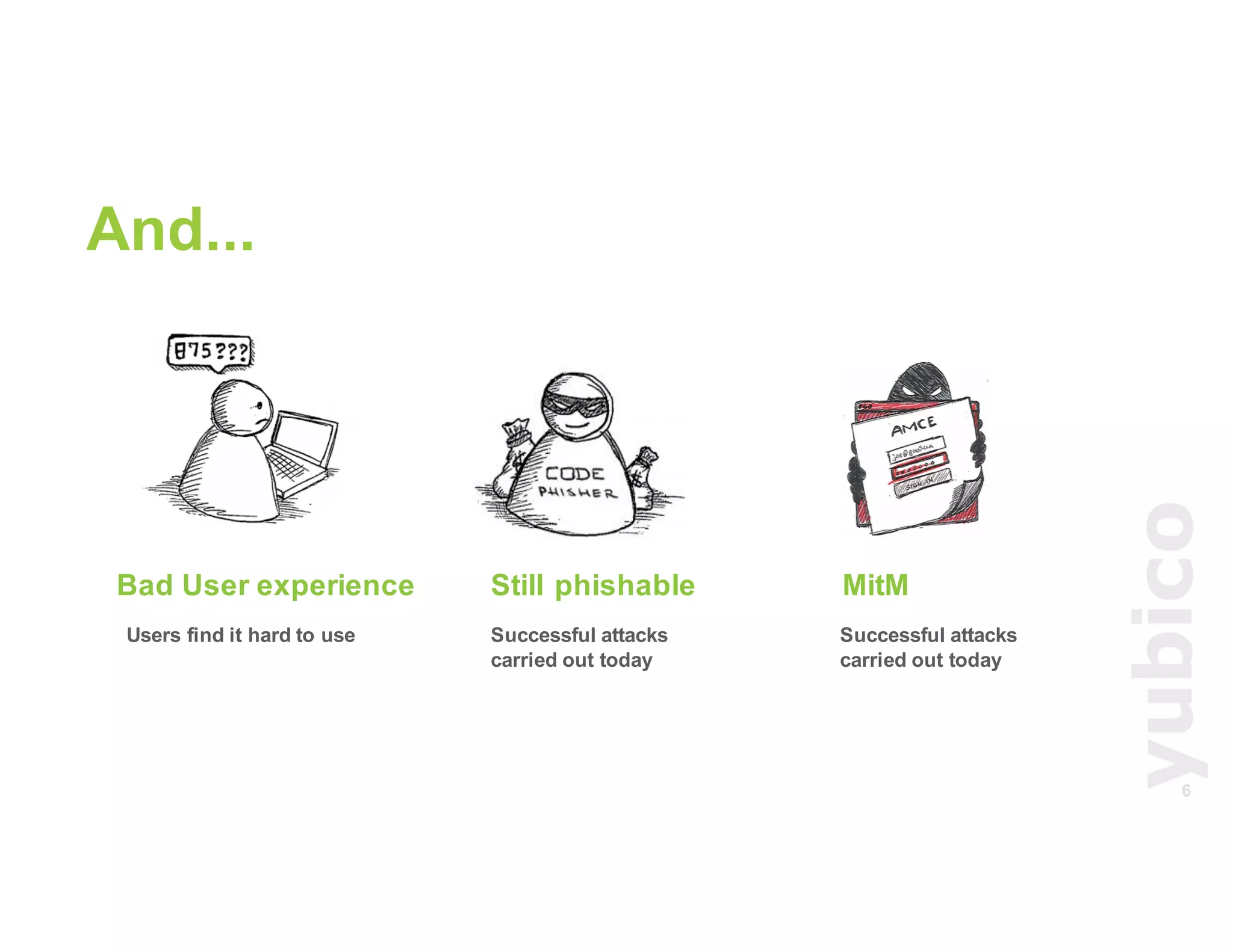
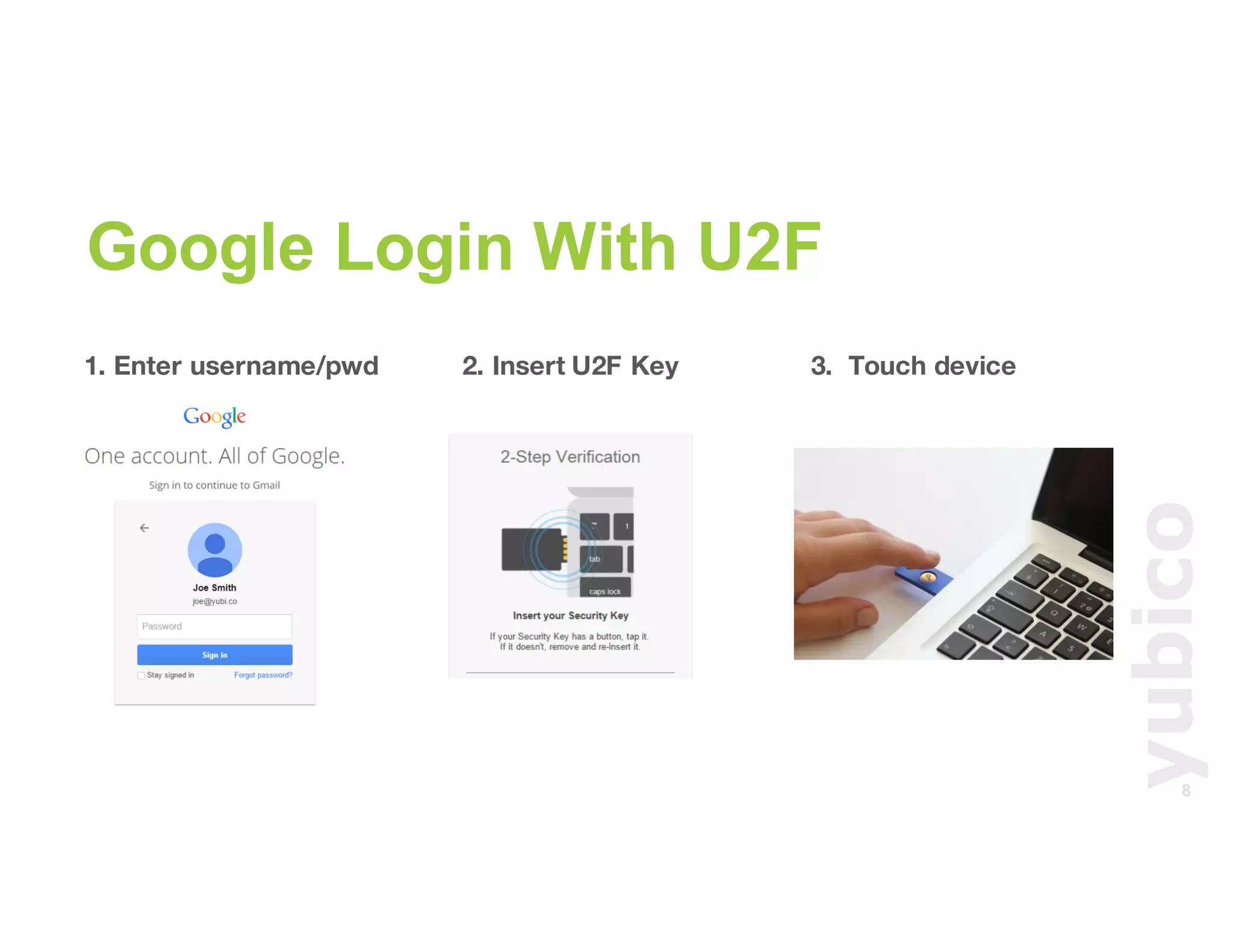
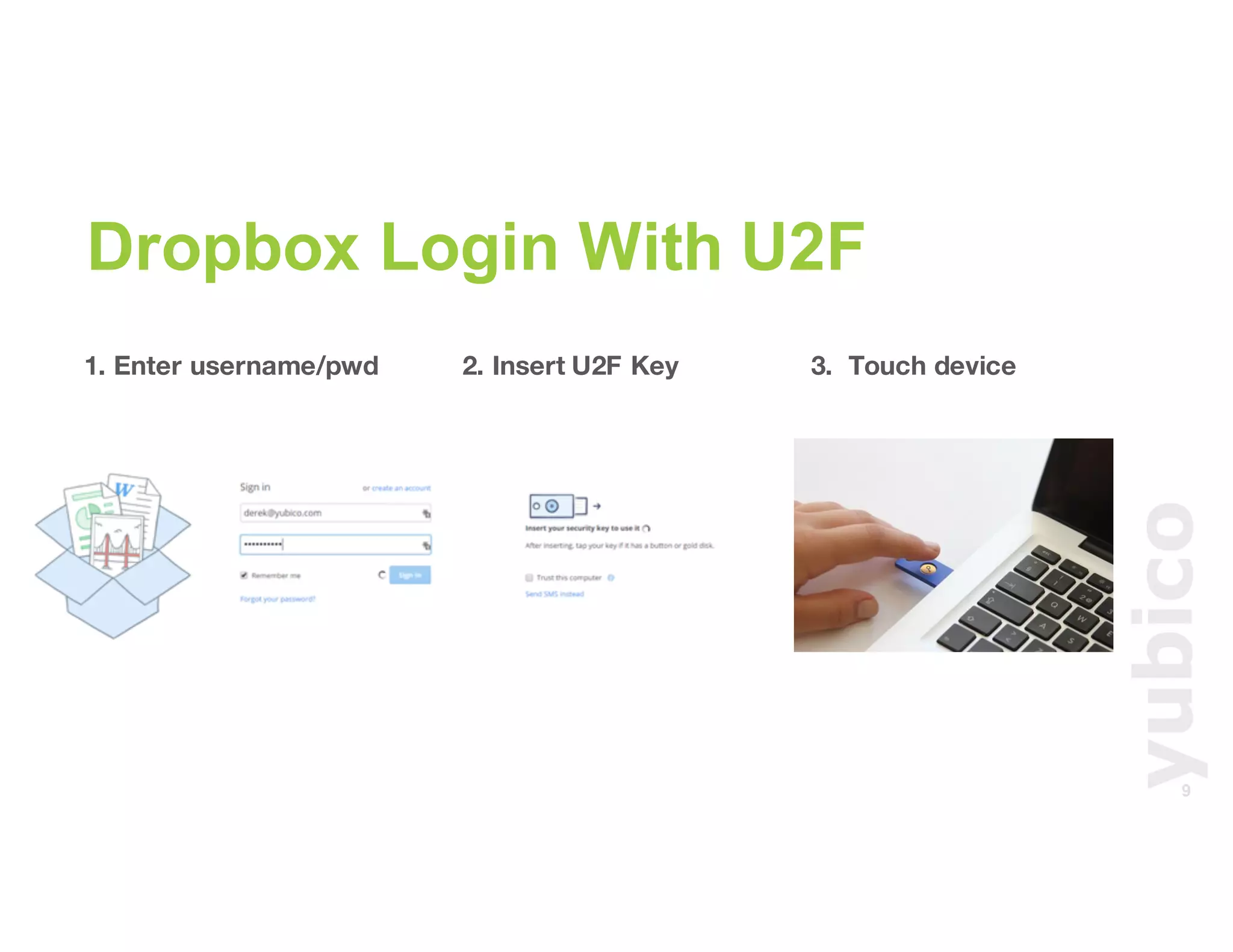
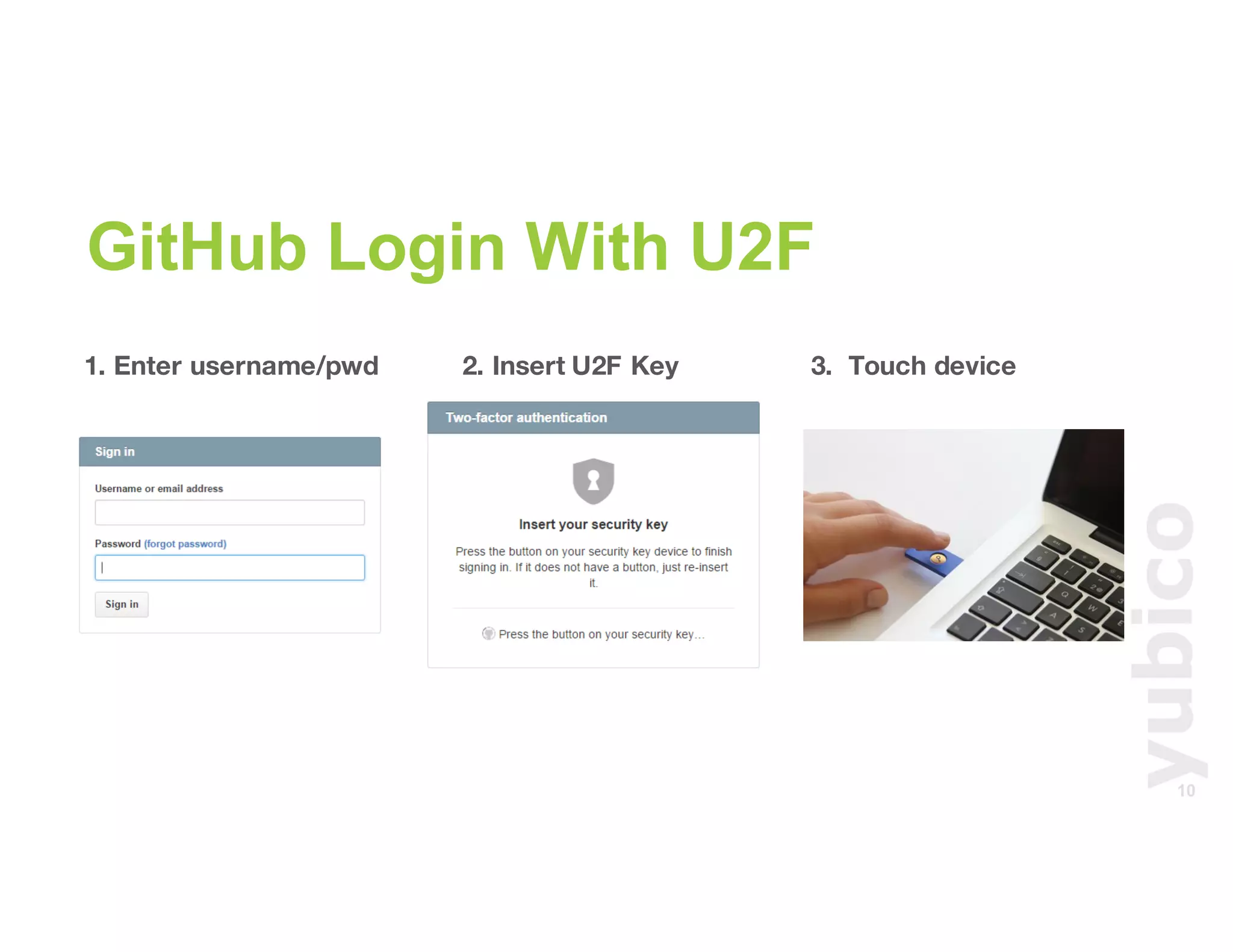
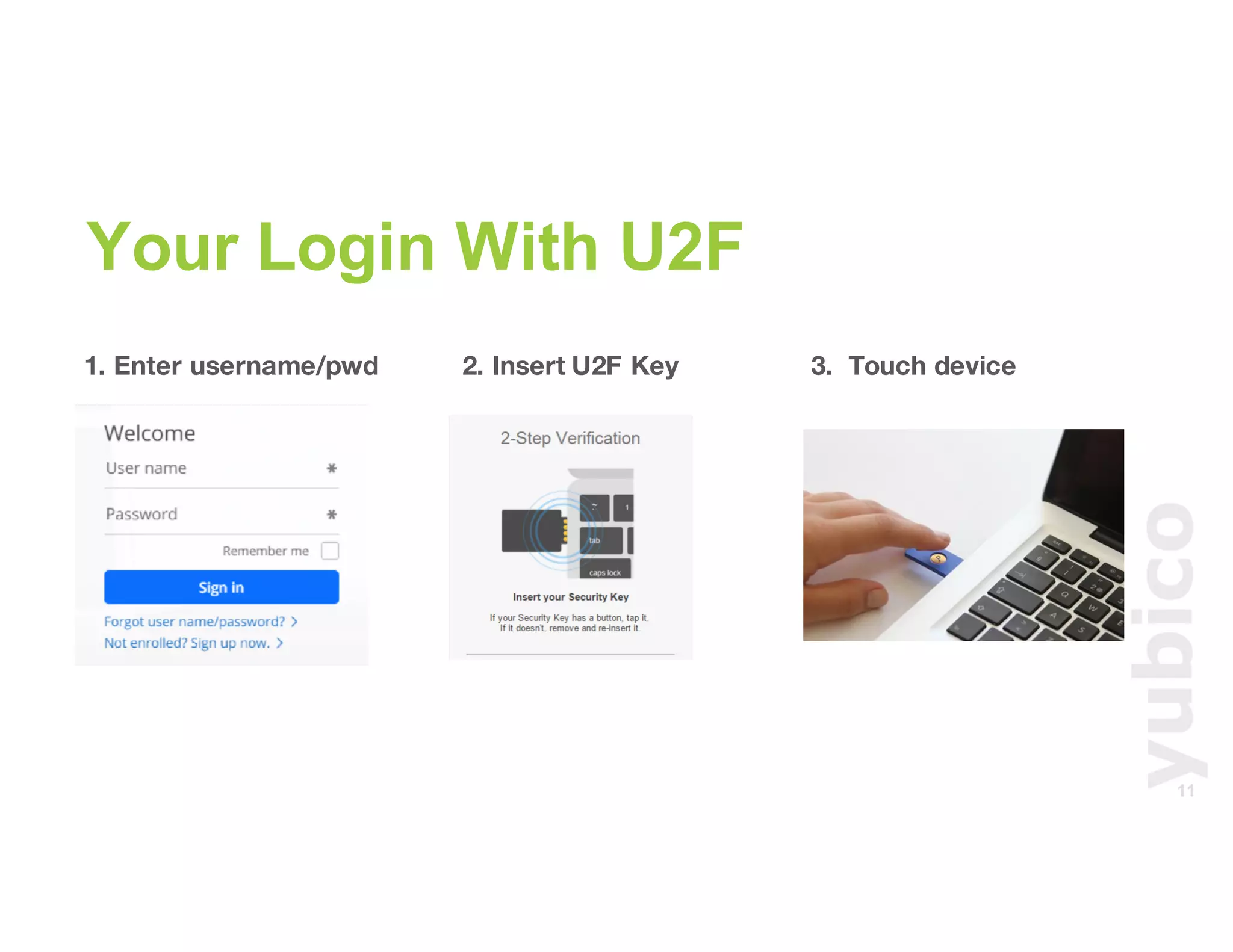
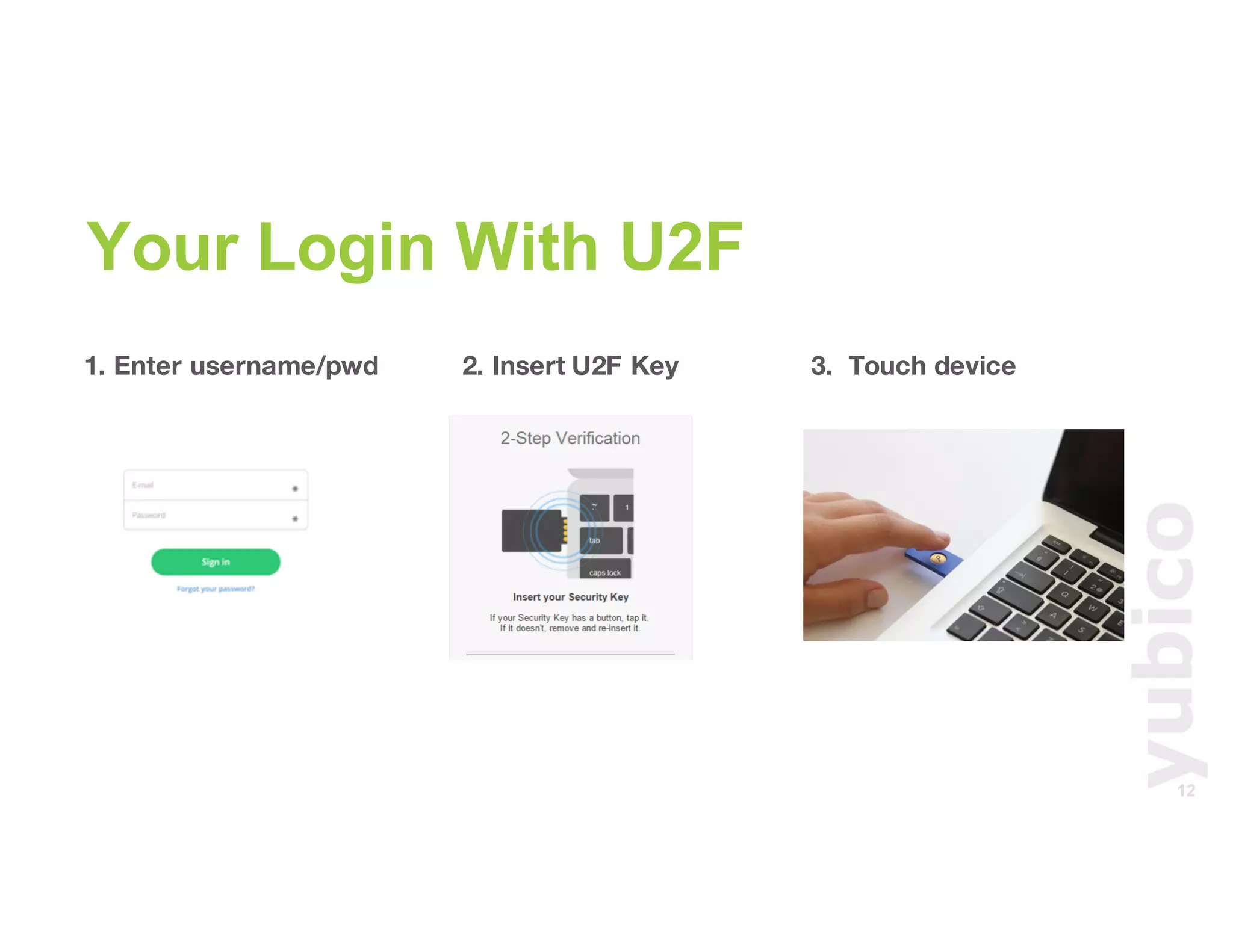
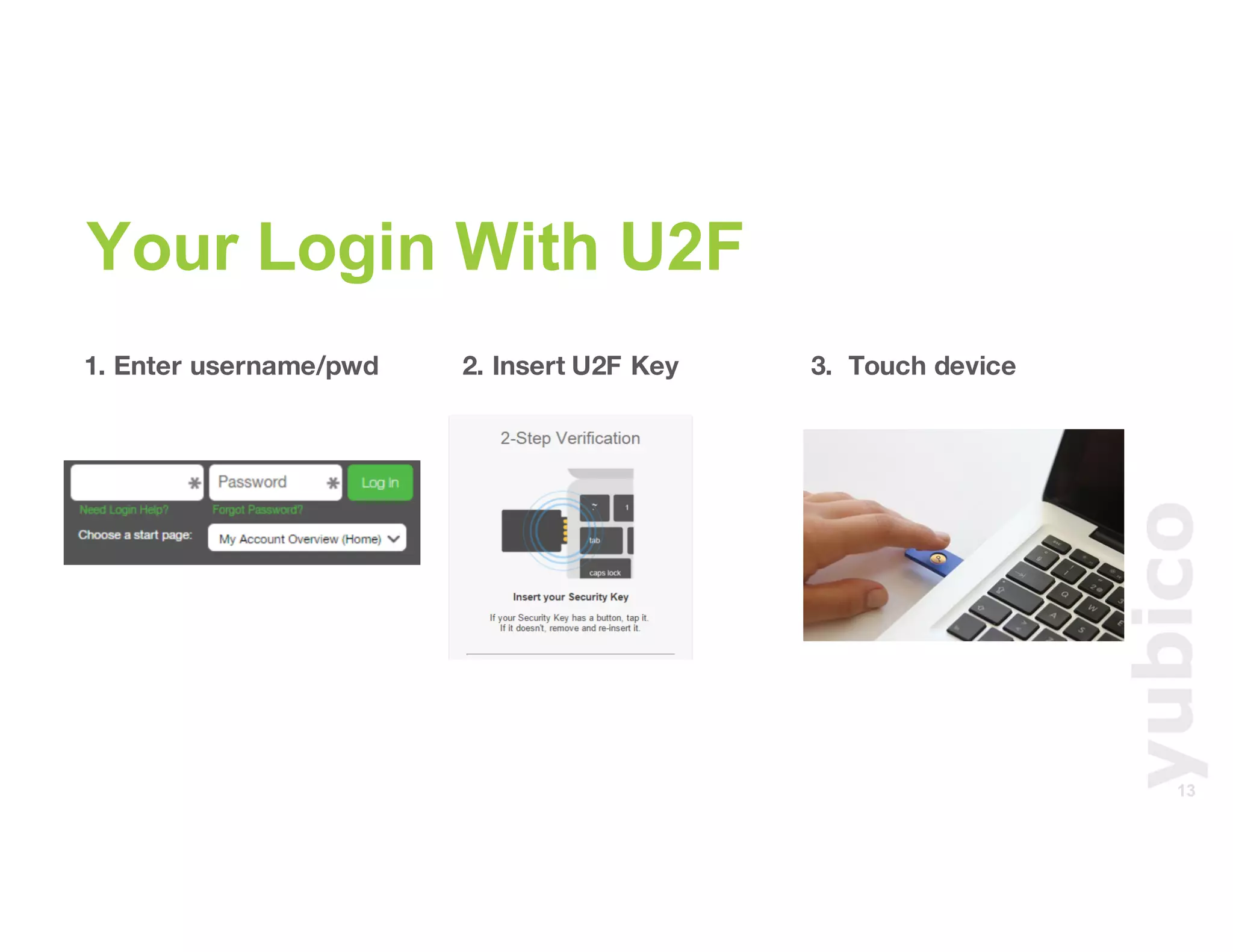
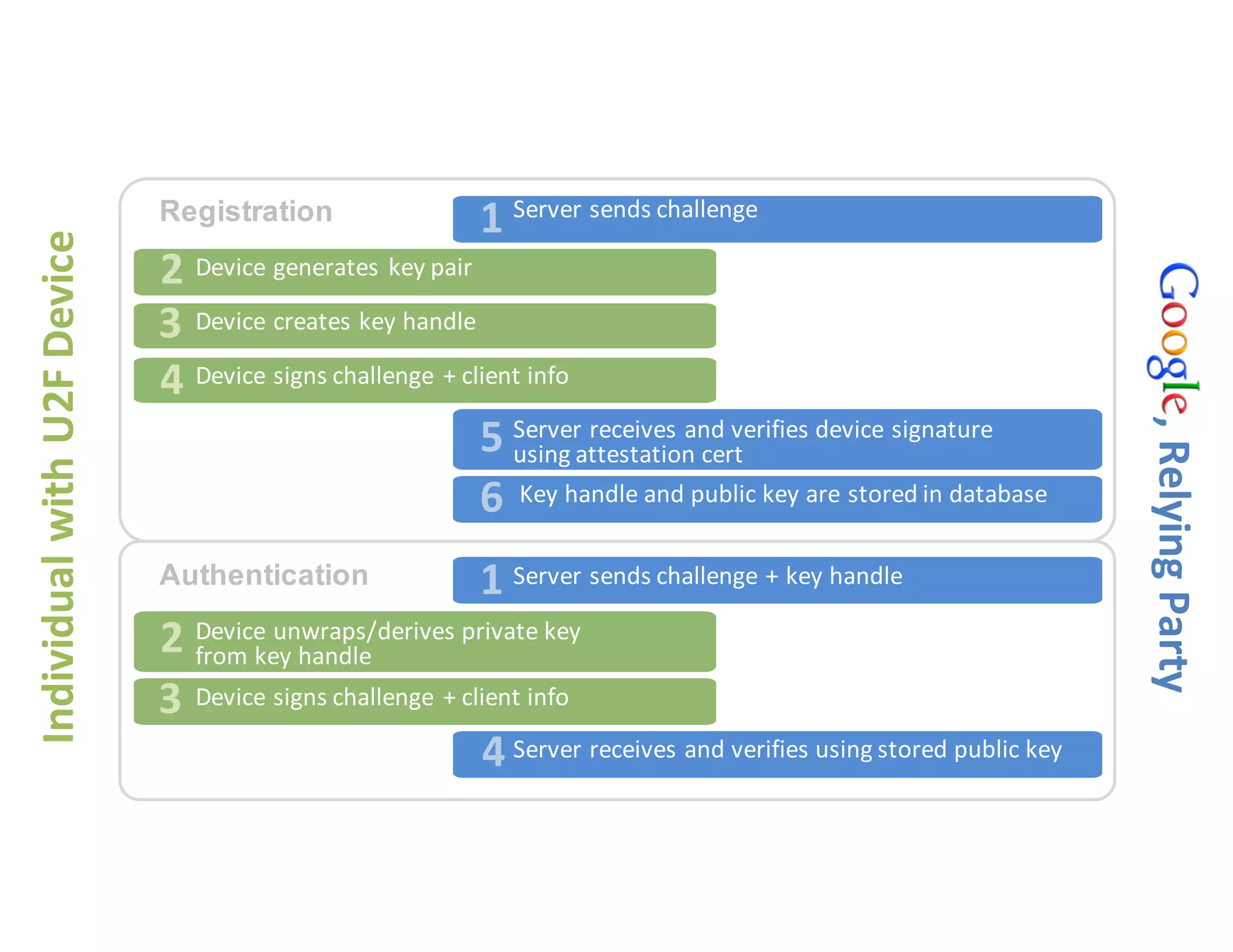
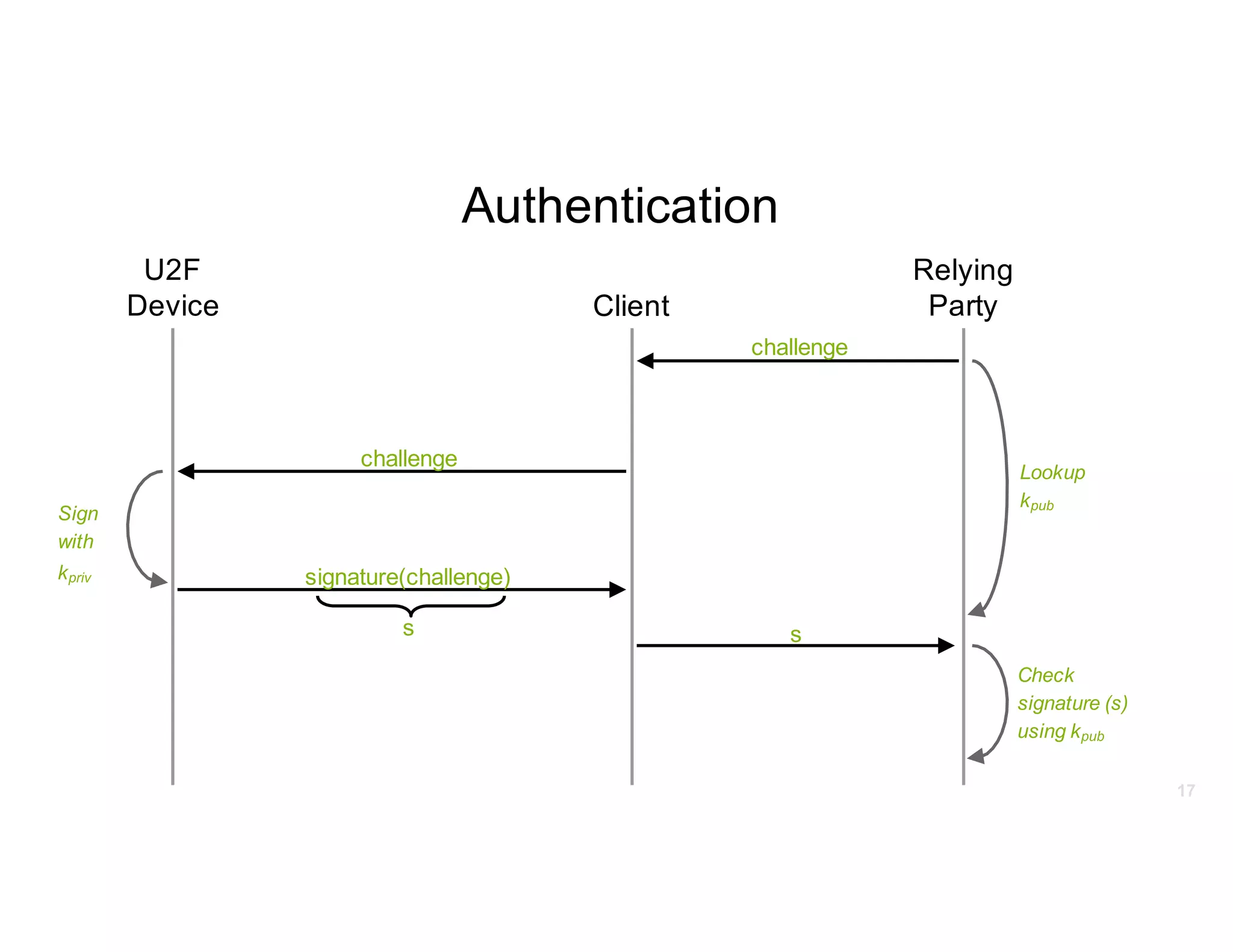
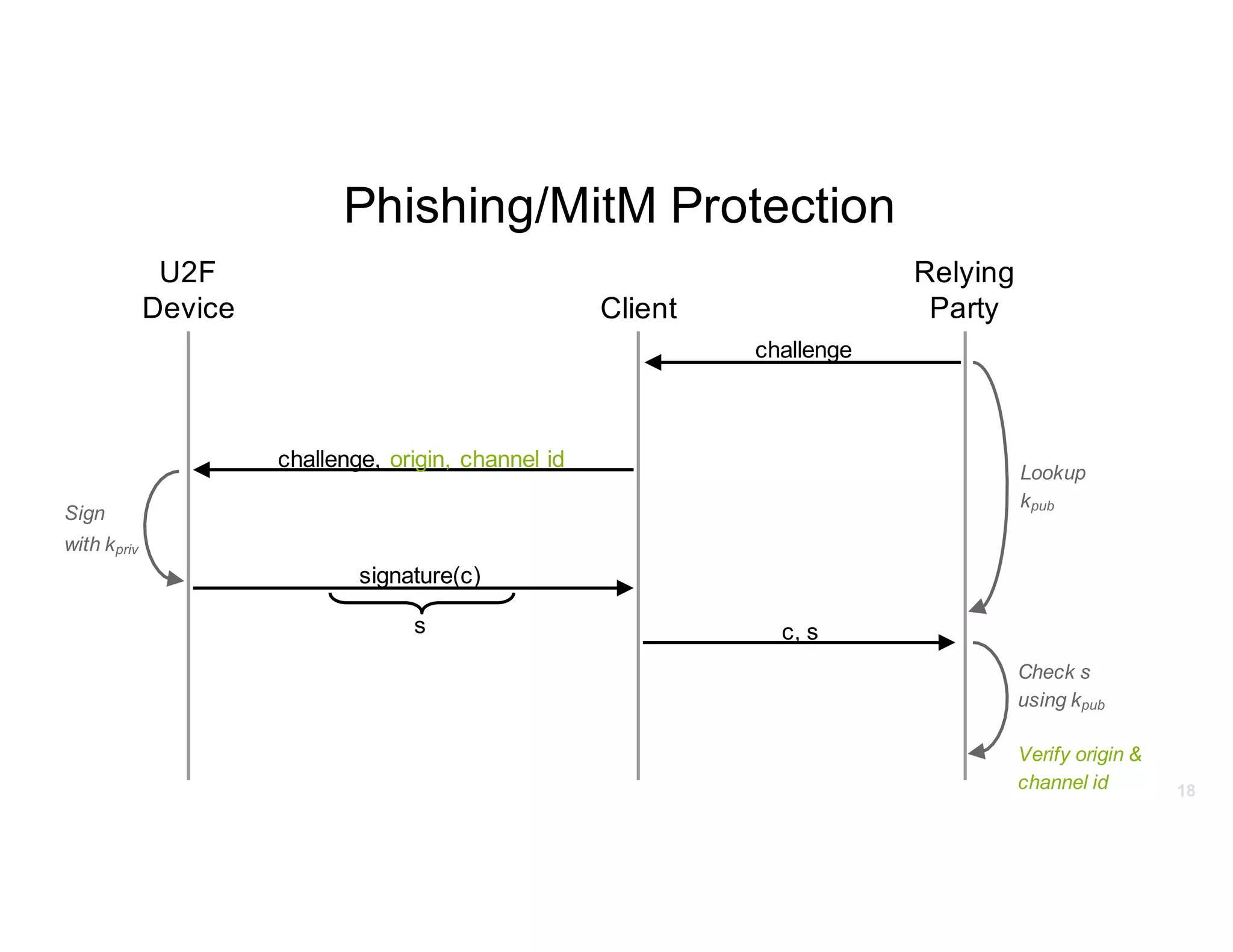
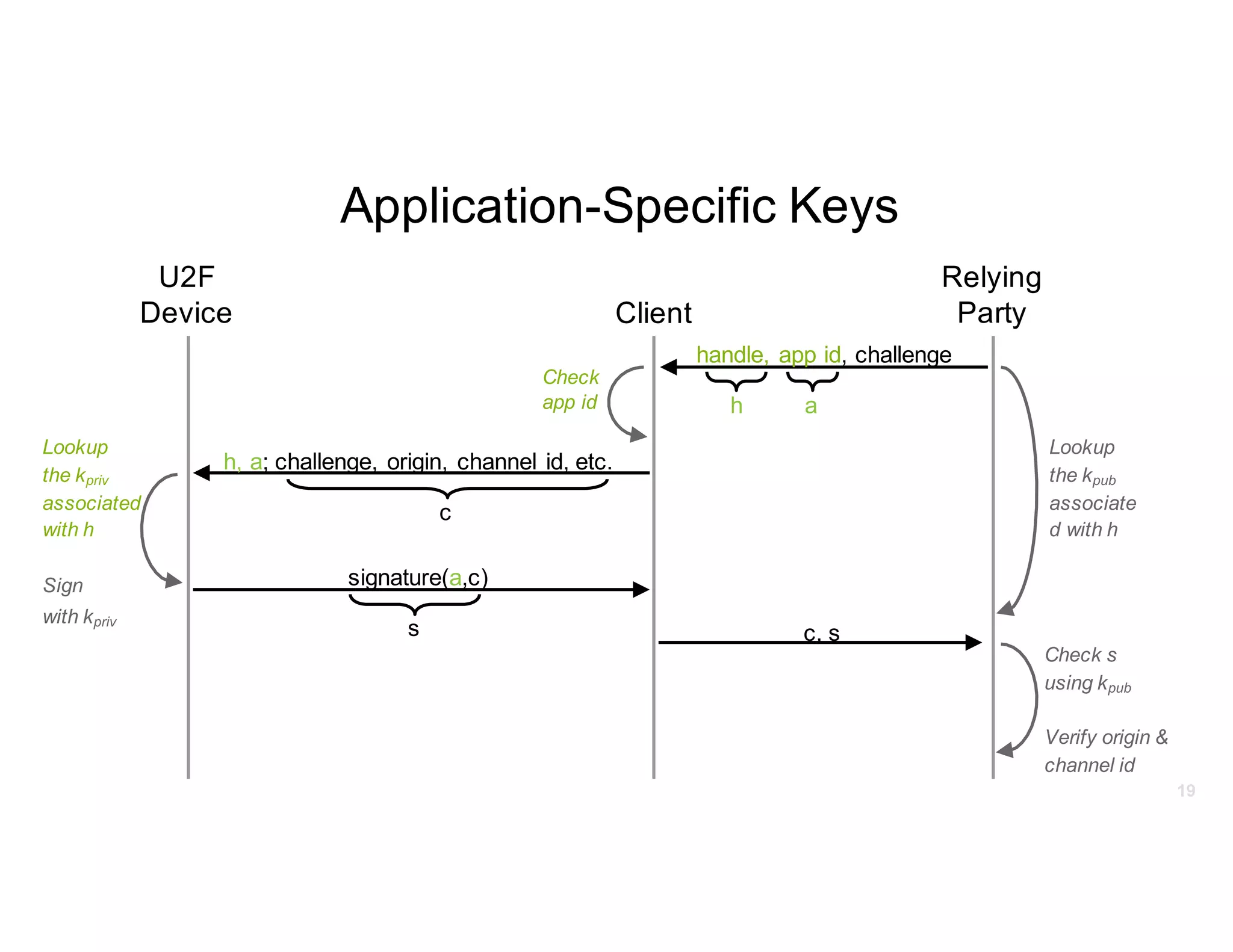
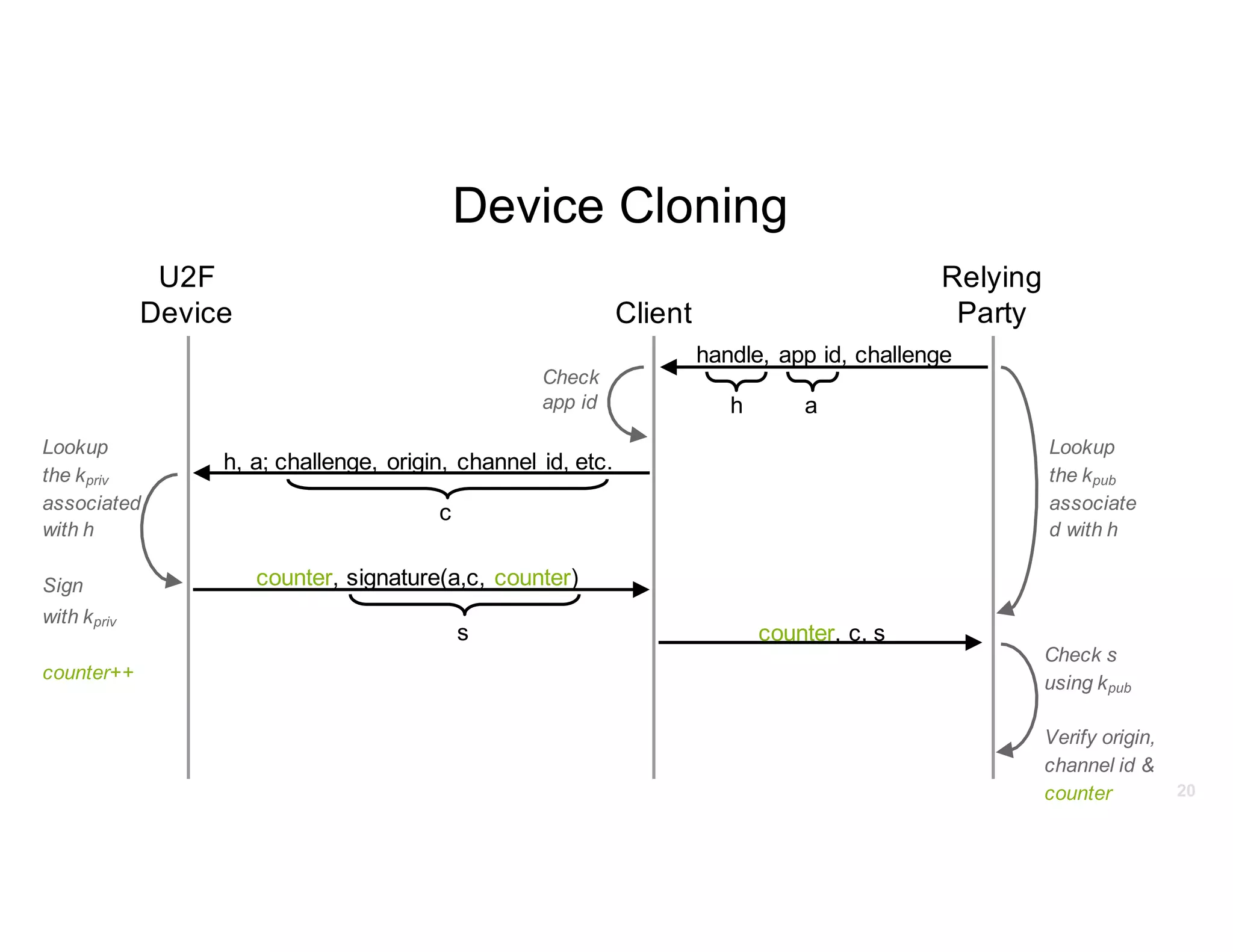
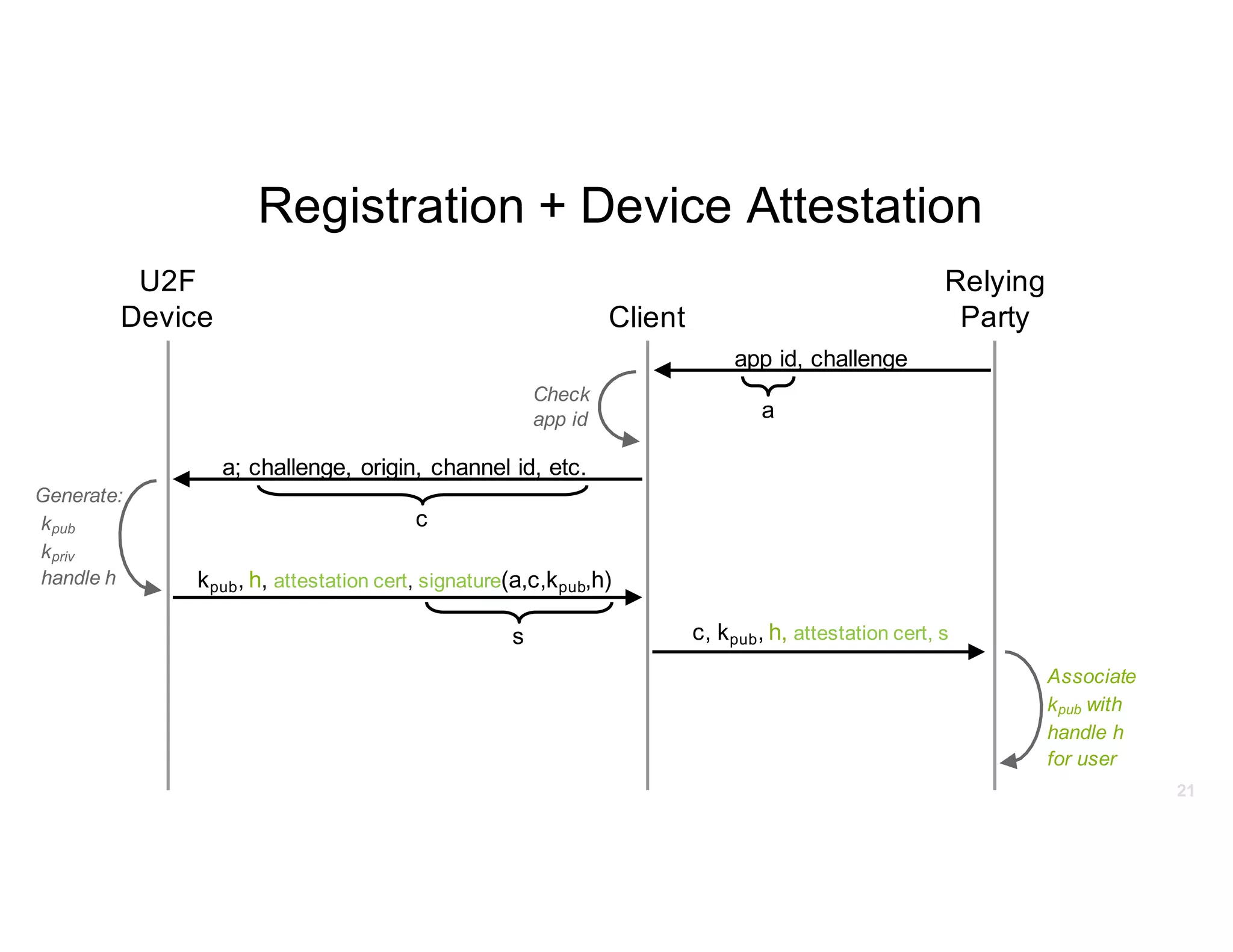
The document discusses Universal 2nd Factor (U2F) technology, which enhances security through a simple, secure, and scalable two-factor authentication mechanism using public key cryptography. It outlines the U2F authentication process and highlights its advantages, including protection against phishing and secure device registration. The document also addresses user experience issues and provides resources for implementation.