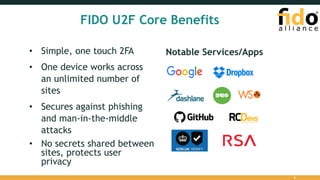
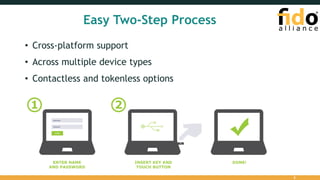
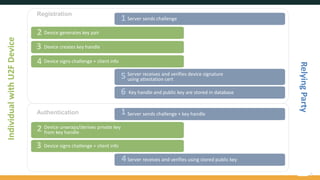
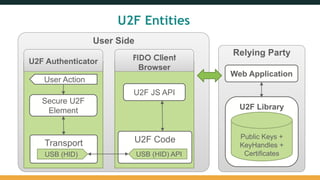
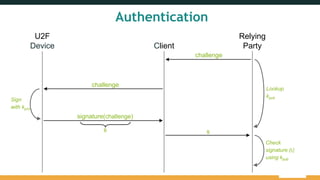
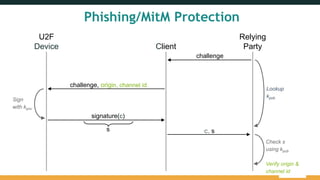
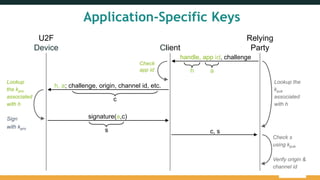
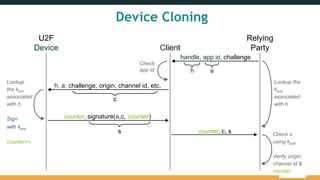
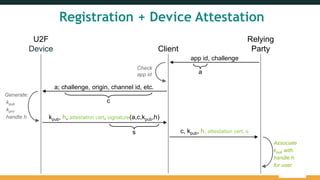
The document provides an overview of the FIDO Universal Second Factor (U2F) specifications, emphasizing its simple and secure two-factor authentication (2FA). Key benefits include cross-platform support, enhanced privacy, and protection against phishing attacks. It also details implementation procedures, performance comparisons with Google Authenticator, and mentions future developments in mobile and cross-browser support.