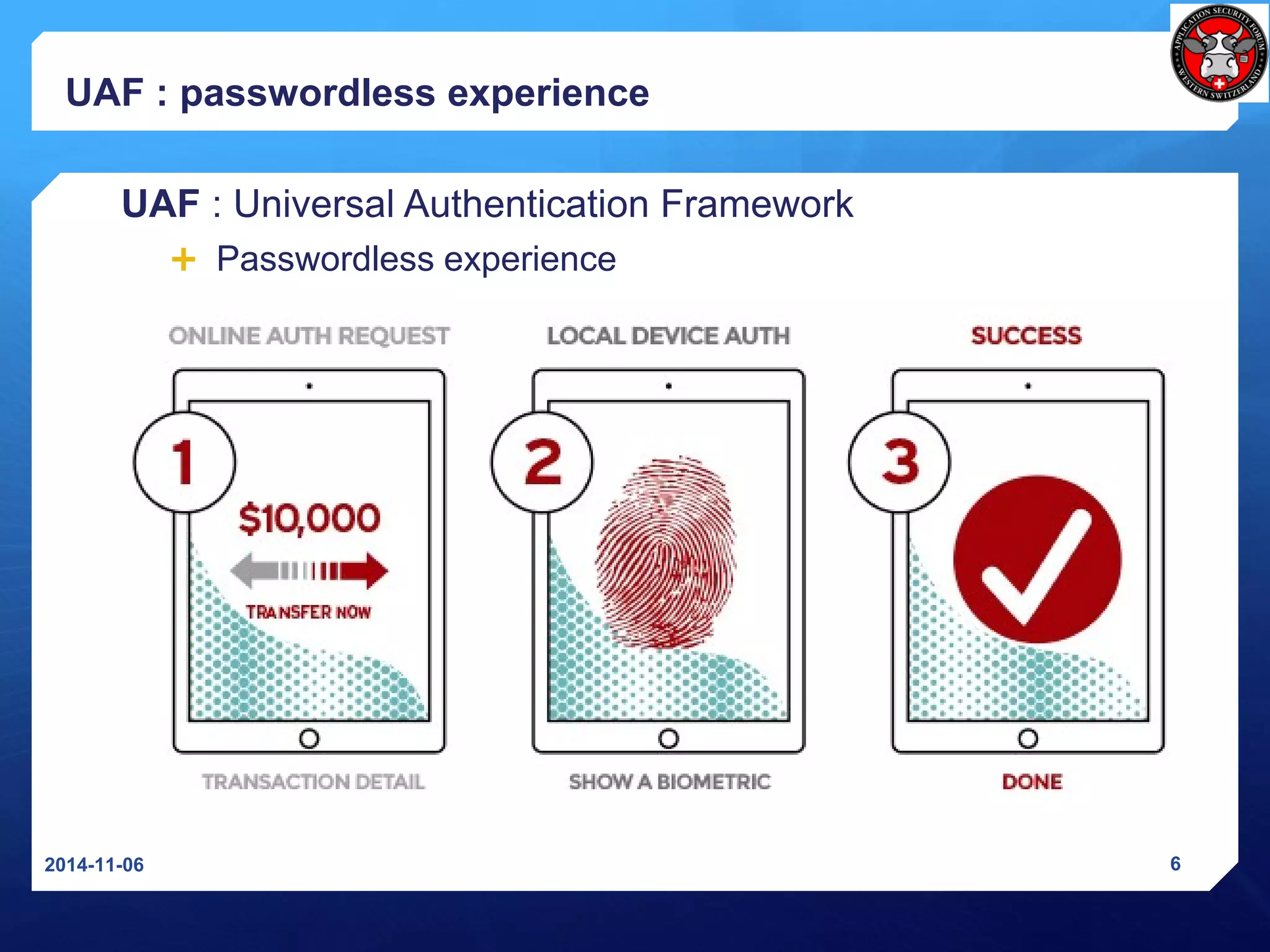
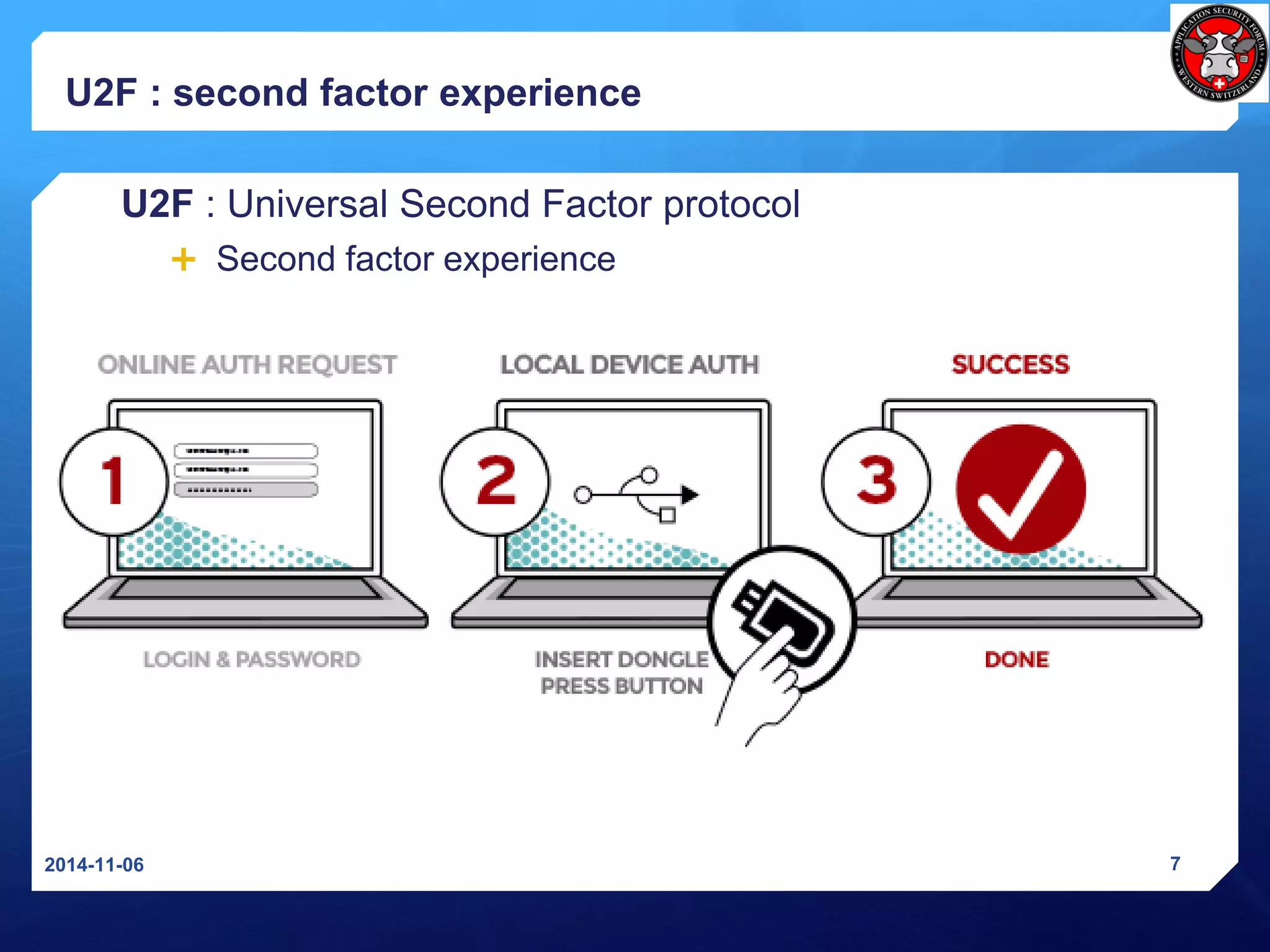
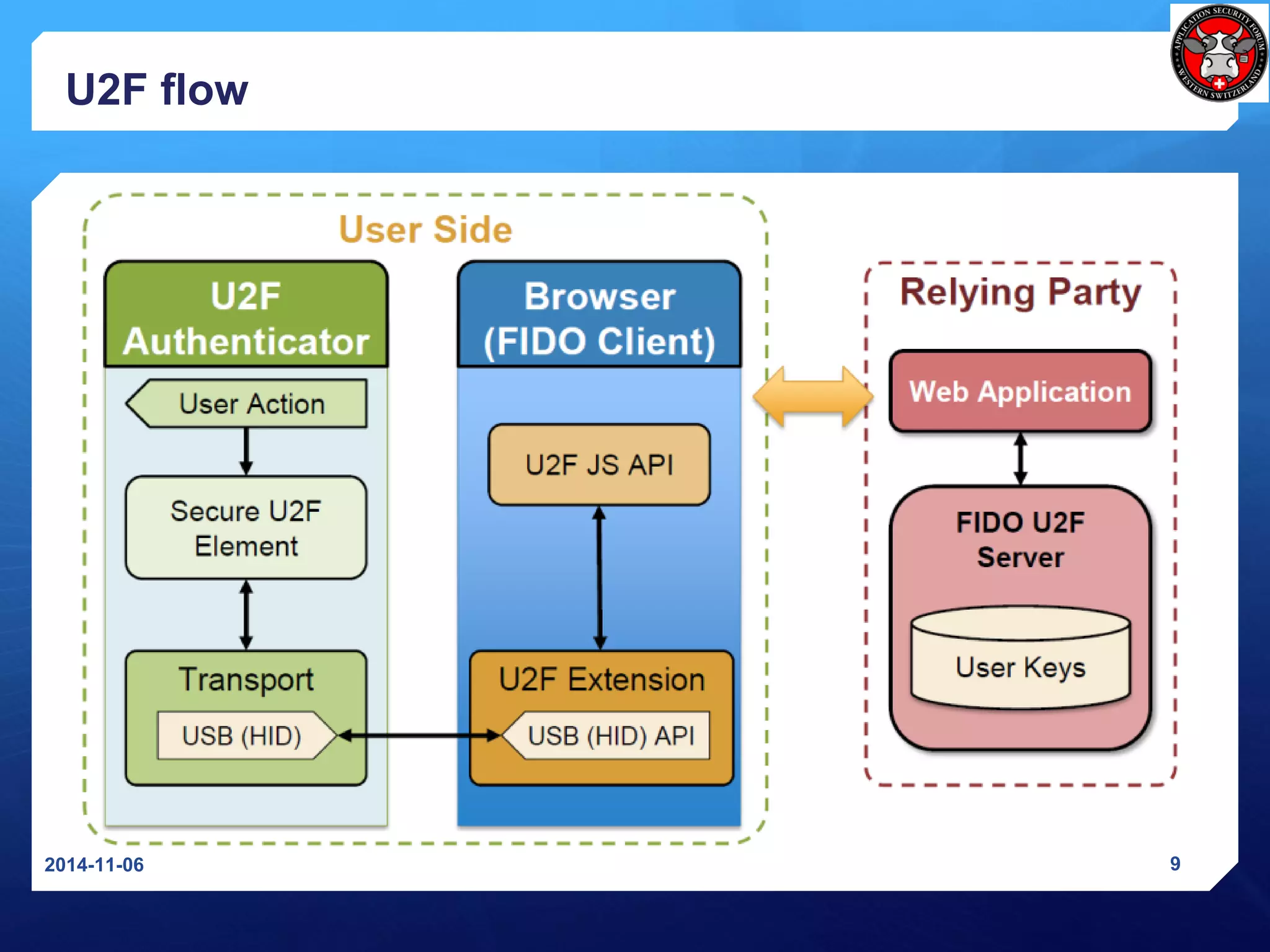
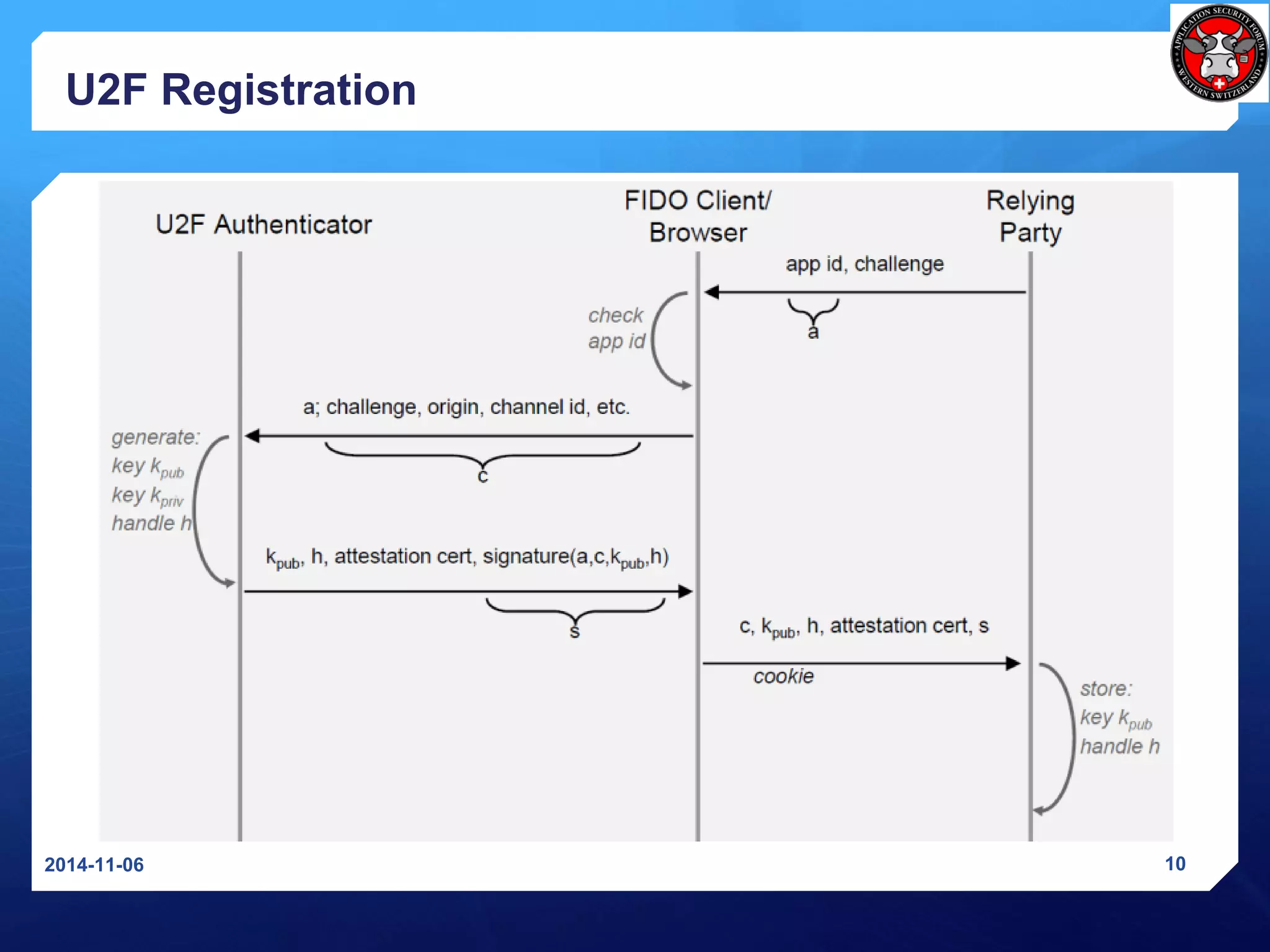
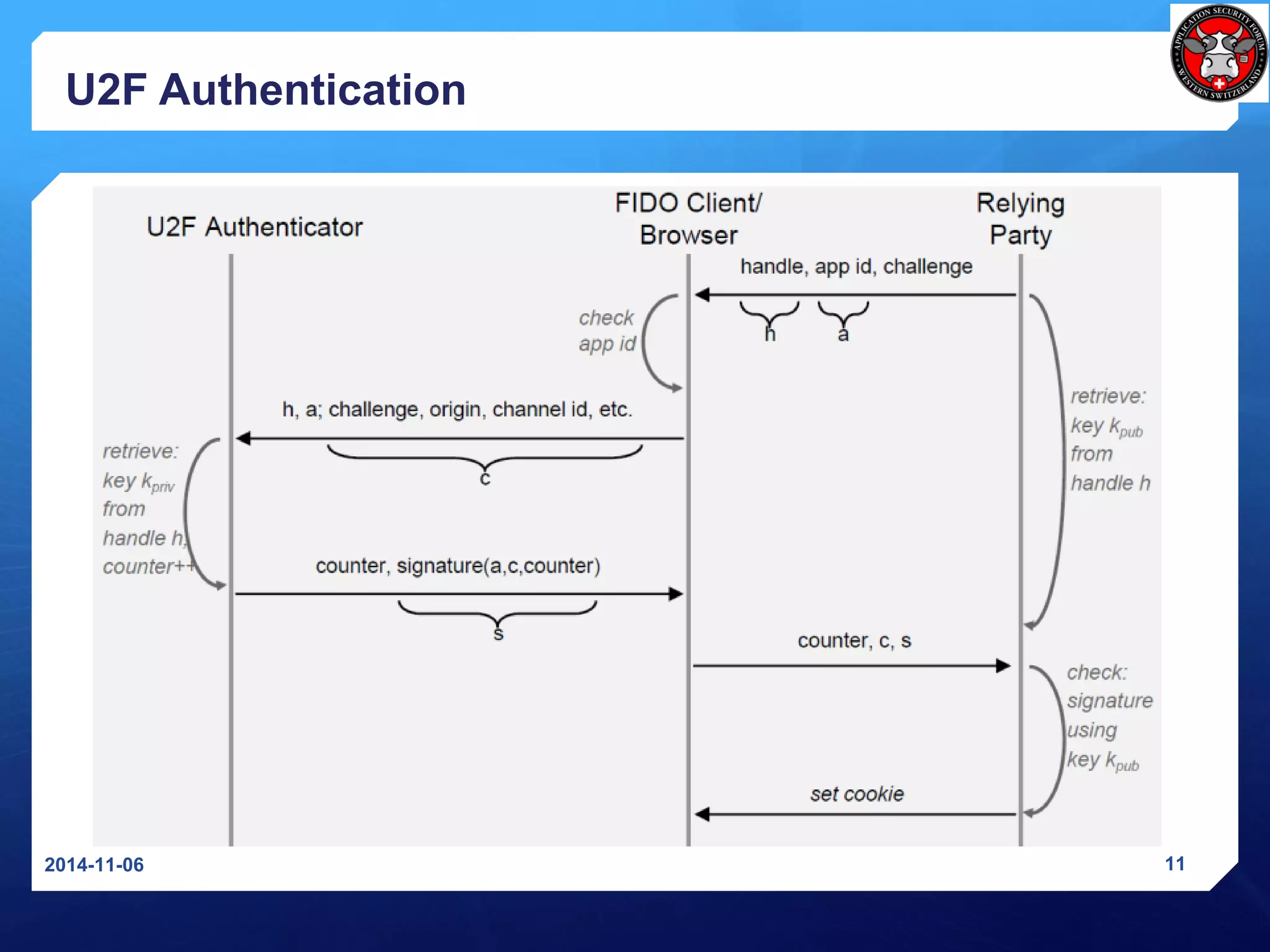
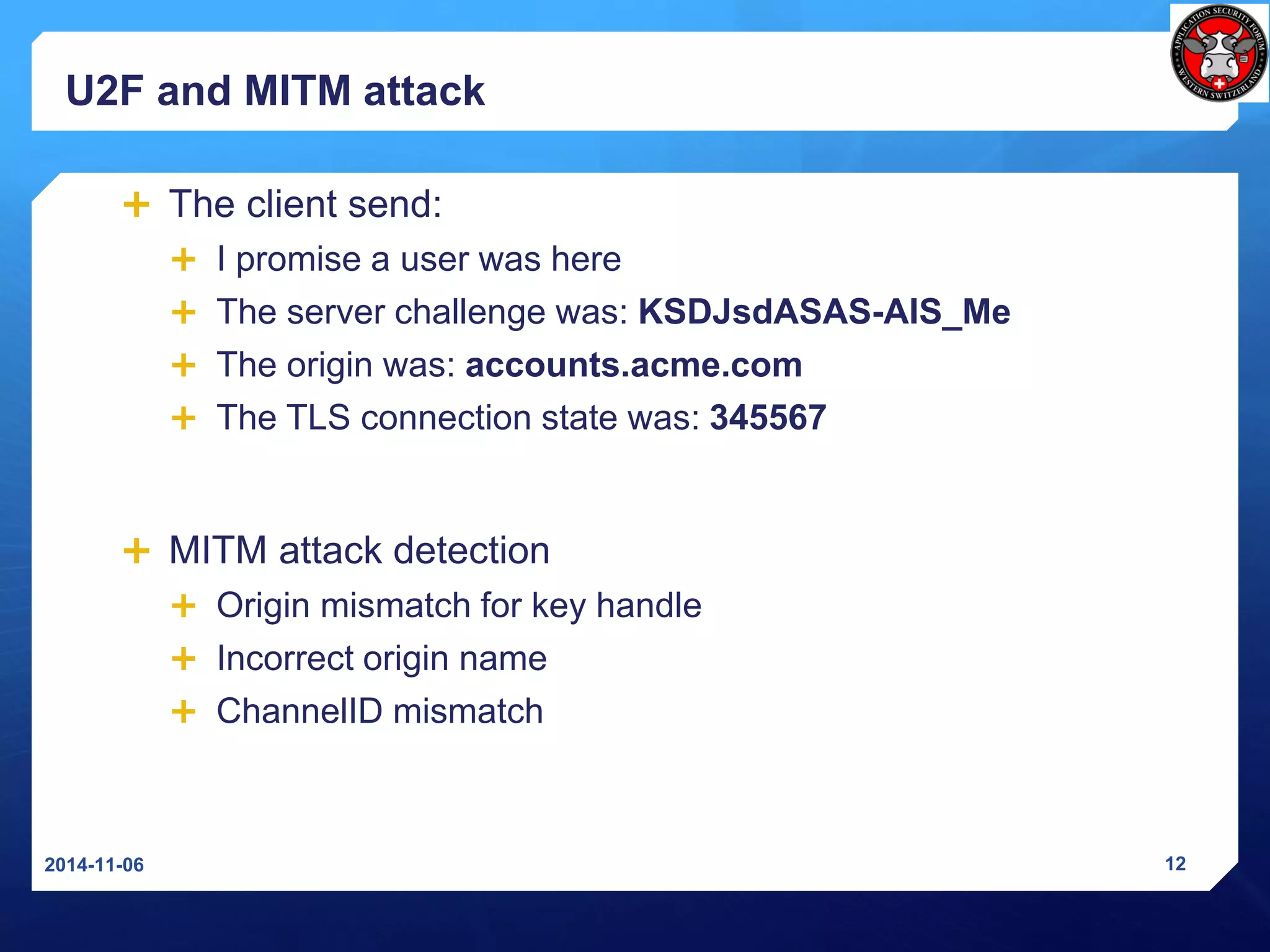
The document discusses Universal 2nd Factor (U2F) and Universal Authentication Framework (UAF) protocols developed by the FIDO Alliance to enable strong, passwordless authentication. It provides an overview of the FIDO Alliance and its goal of developing open authentication standards. It then describes the U2F protocol, which provides a second factor of authentication, and the UAF protocol, which enables passwordless authentication. It also summarizes the U2F registration and authentication flows and how U2F prevents man-in-the-middle attacks.