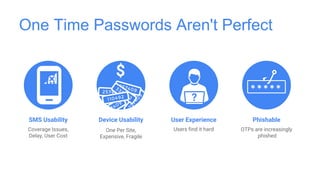
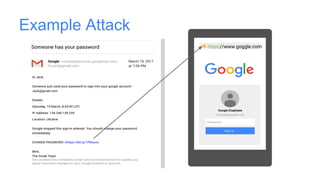
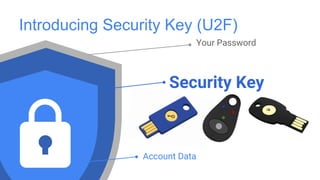
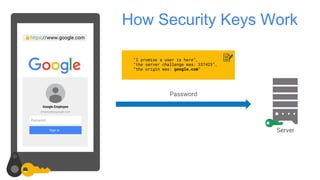
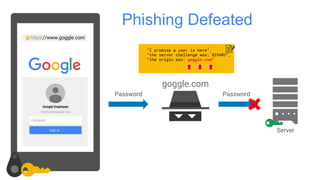
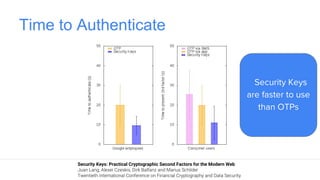
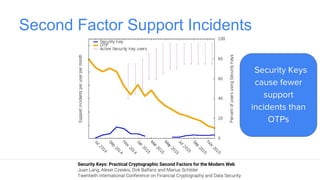
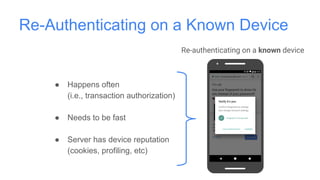
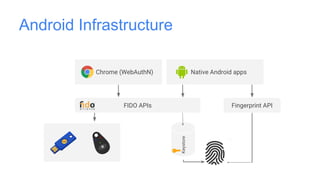
Google has deployed FIDO U2F security keys for two-factor authentication at scale within their organization. They found security keys to be faster and cause fewer support incidents than one-time passwords. Google has also made security keys available to consumers as an optional second factor for their accounts. Other companies like Dropbox, GitHub, and Facebook have also adopted FIDO security keys. Google's experience shows that security keys can provide stronger authentication that is also more usable for users and enterprises.