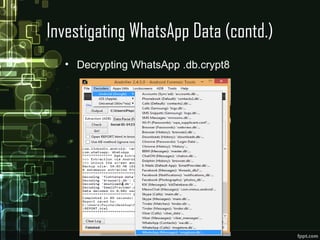
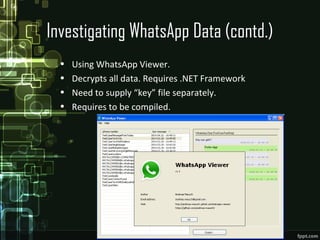
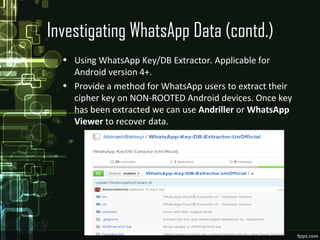
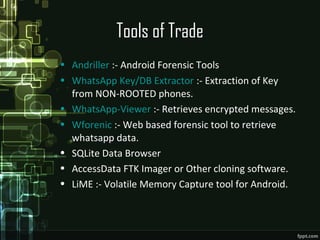
The document discusses WhatsApp forensics, detailing its significance, statistics, and security issues, particularly focusing on concerns for Indian users who make up a large portion of its user base. It outlines the methods for investigating WhatsApp data, including where to find evidence, tools required for forensics, and the principles of safeguarding personal information. The presentation emphasizes the need for awareness about security threats associated with instant messaging applications.