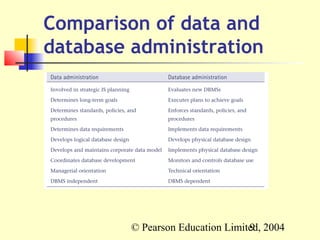
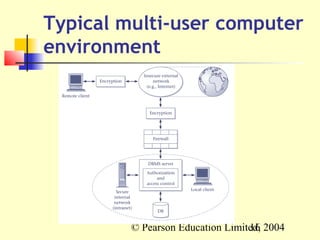
This document discusses database administration and security. It defines the roles of data administrator and database administrator, and their respective responsibilities in managing corporate data and databases. The document outlines threats to database security, such as hacking and hardware failure, and countermeasures like authorization, backups, and RAID technology to improve reliability. Maintaining database security is important to prevent issues like data theft, fraud, and loss of integrity or availability.