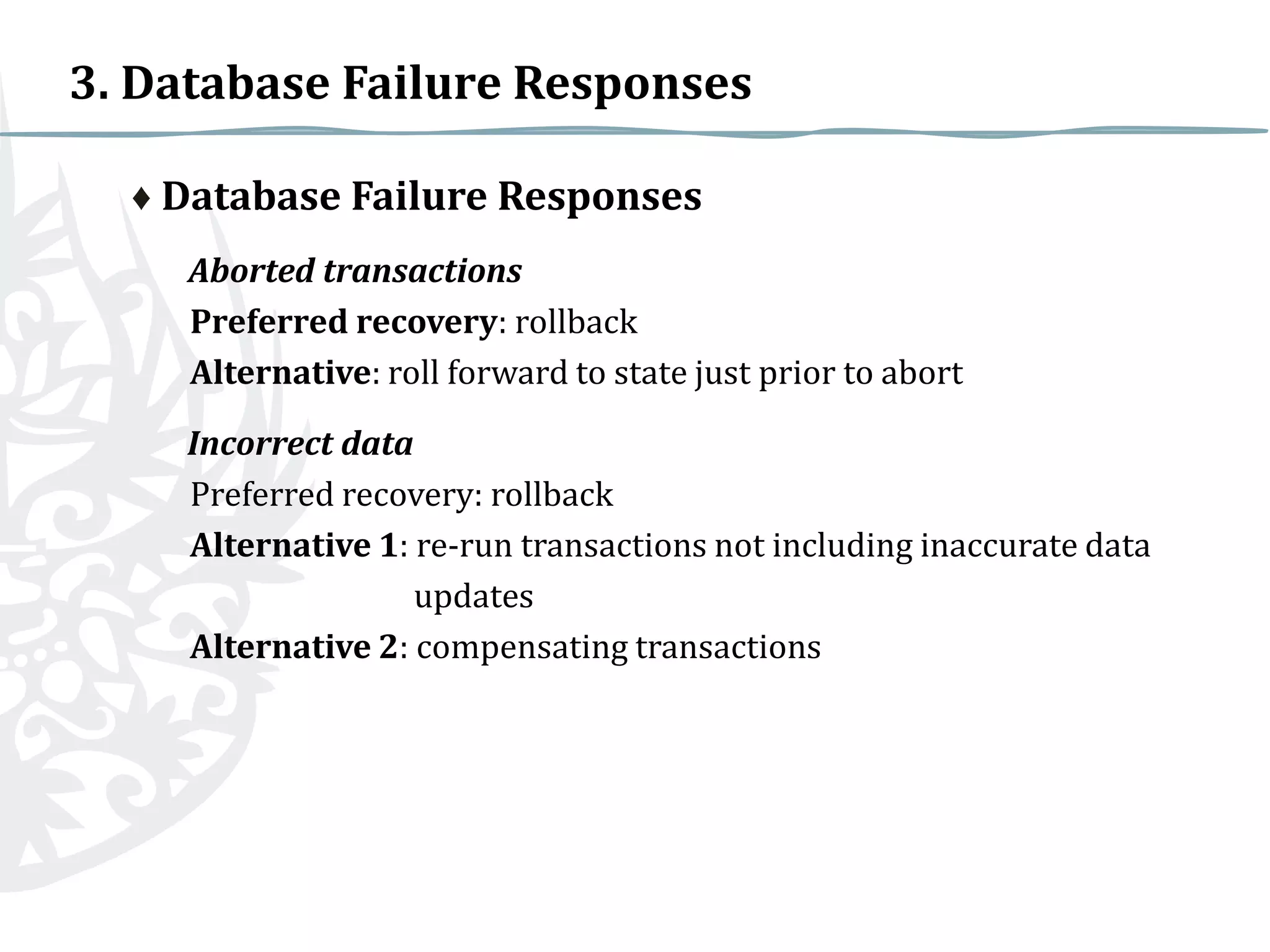
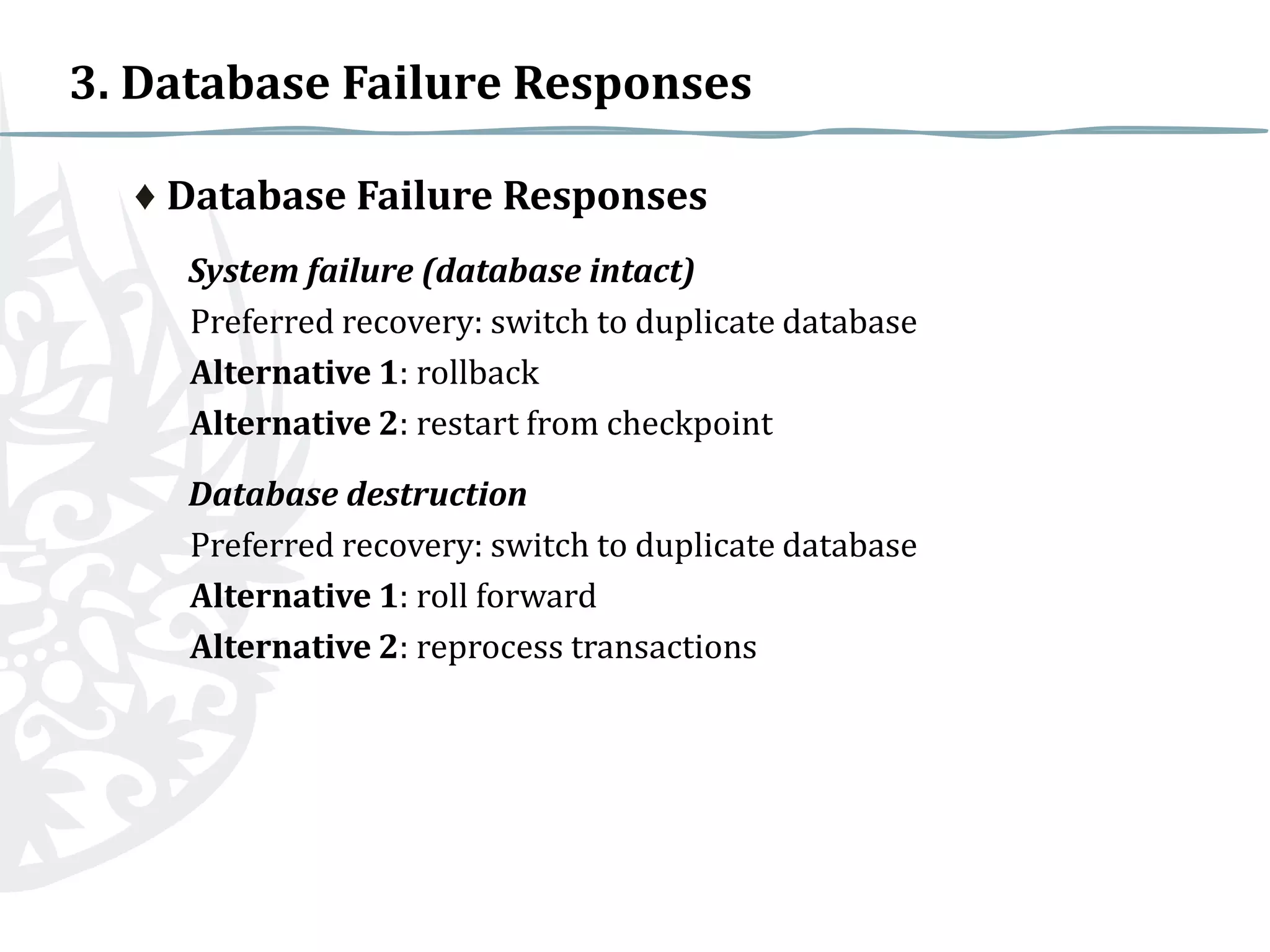
This document discusses various countermeasures for database security including authorization, authentication, backups, journalizing, encryption, RAID technology, user-defined procedures, and checkpoints. It also discusses responses to different types of database failures such as aborted transactions, incorrect data, system failures with the database intact, and total database destruction. The preferred and alternative recovery approaches are outlined for each failure scenario.