The document discusses data and database administration. It covers:
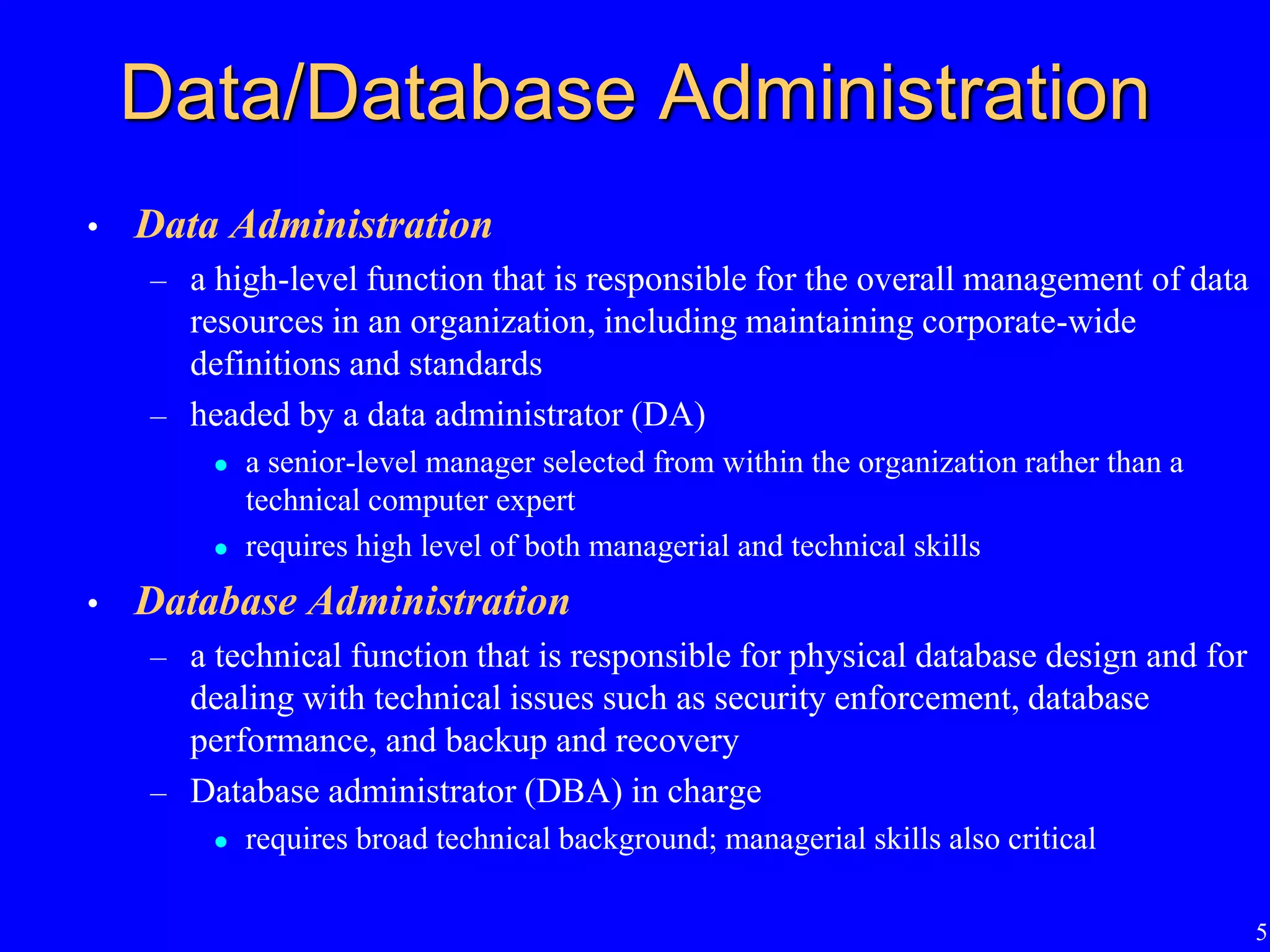
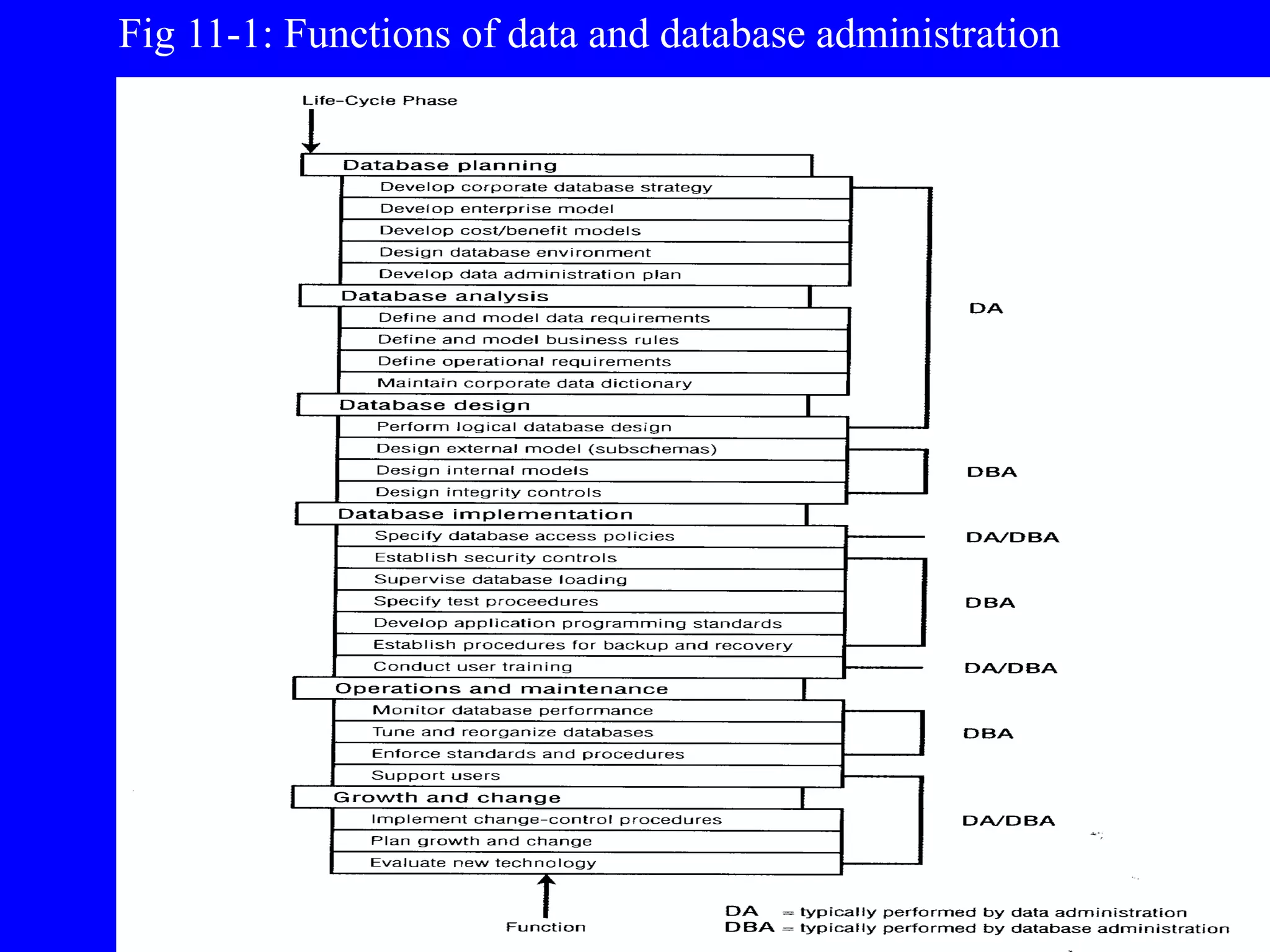
1) The functions of data administration including data policies, planning, and managing the information repository.
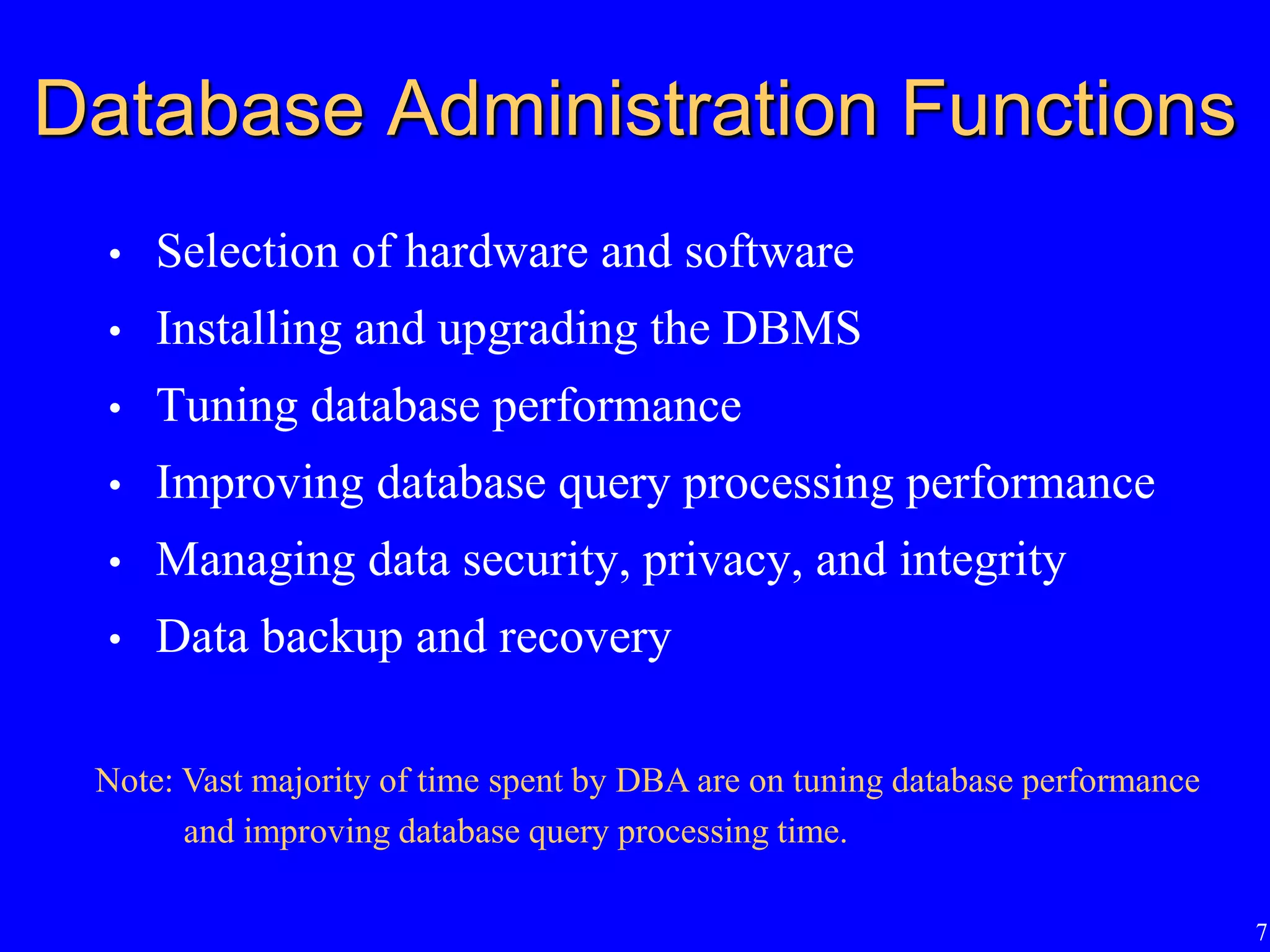
2) The functions of database administration including hardware/software selection, performance tuning, security, backups, and recovery.
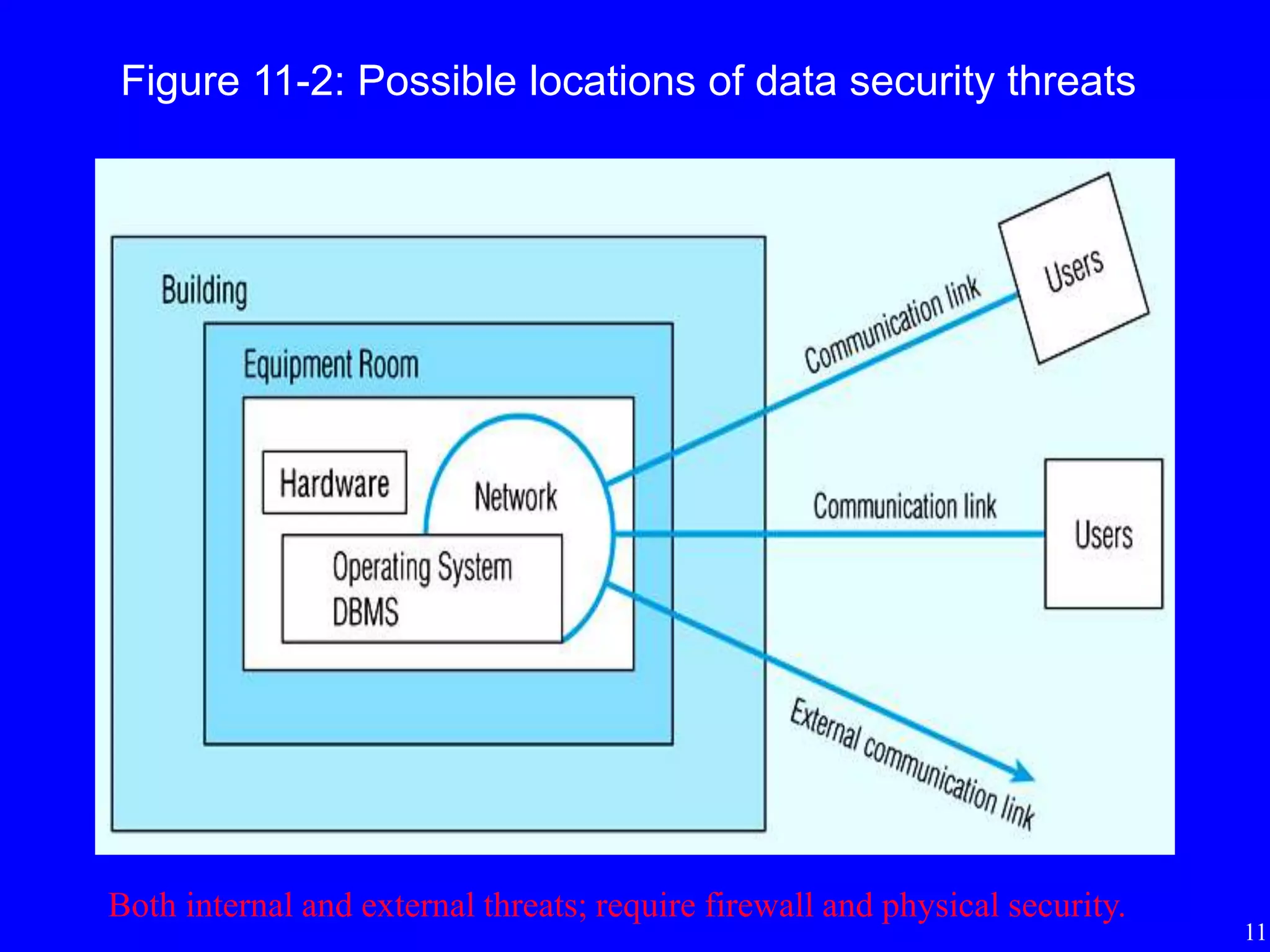
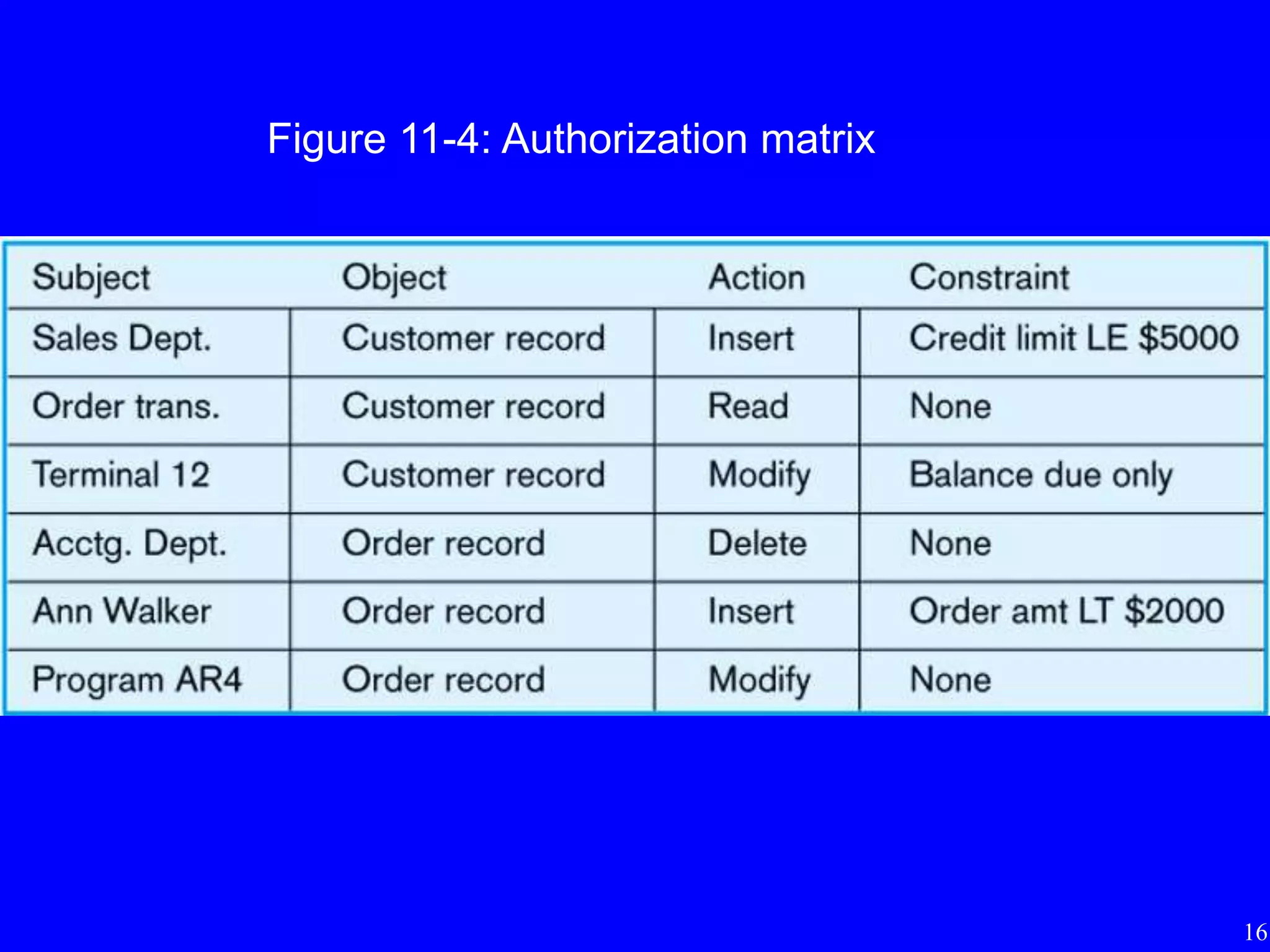
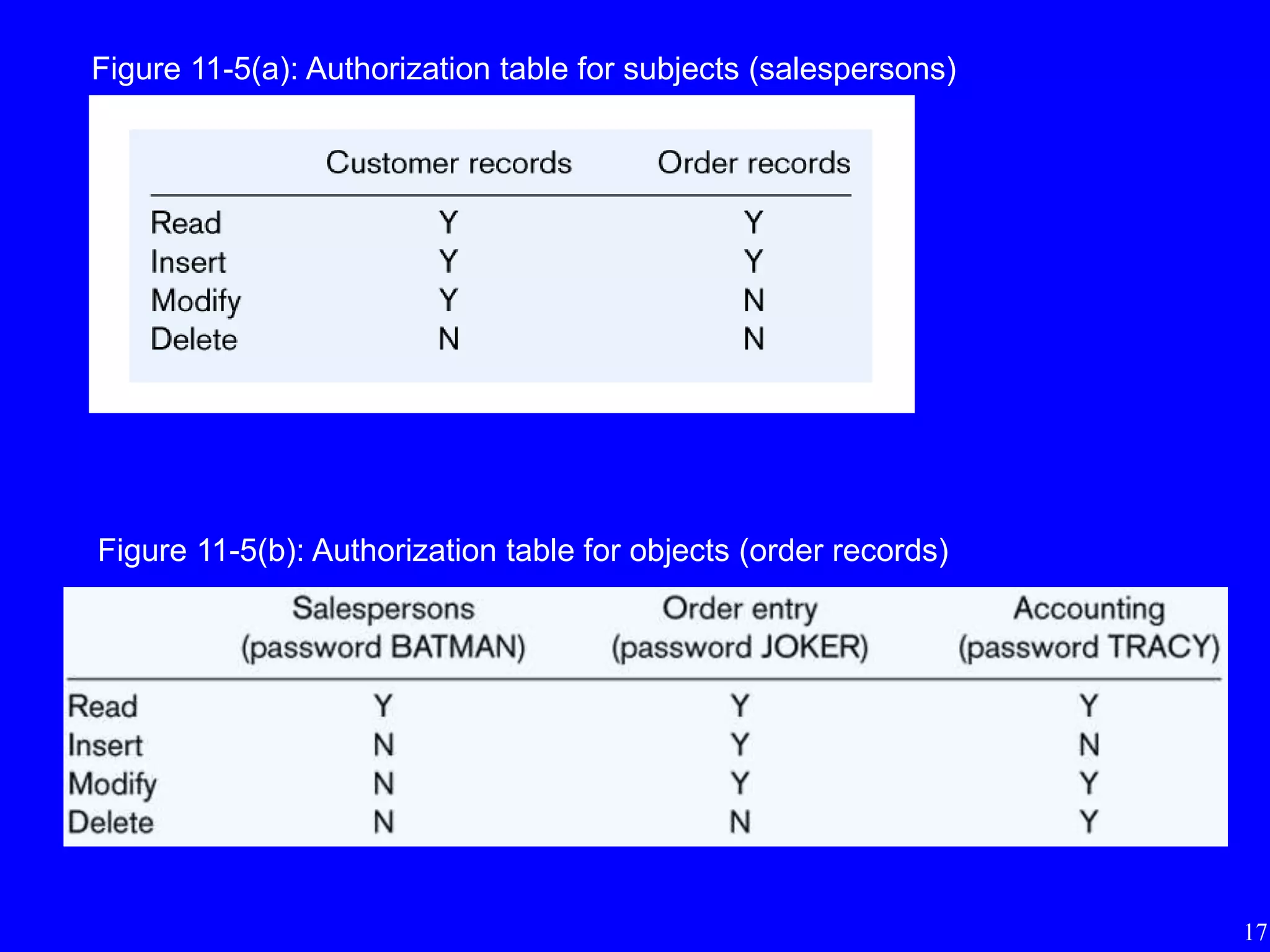
3) Techniques for managing data security including views, integrity controls, authorization rules, encryption, and authentication.
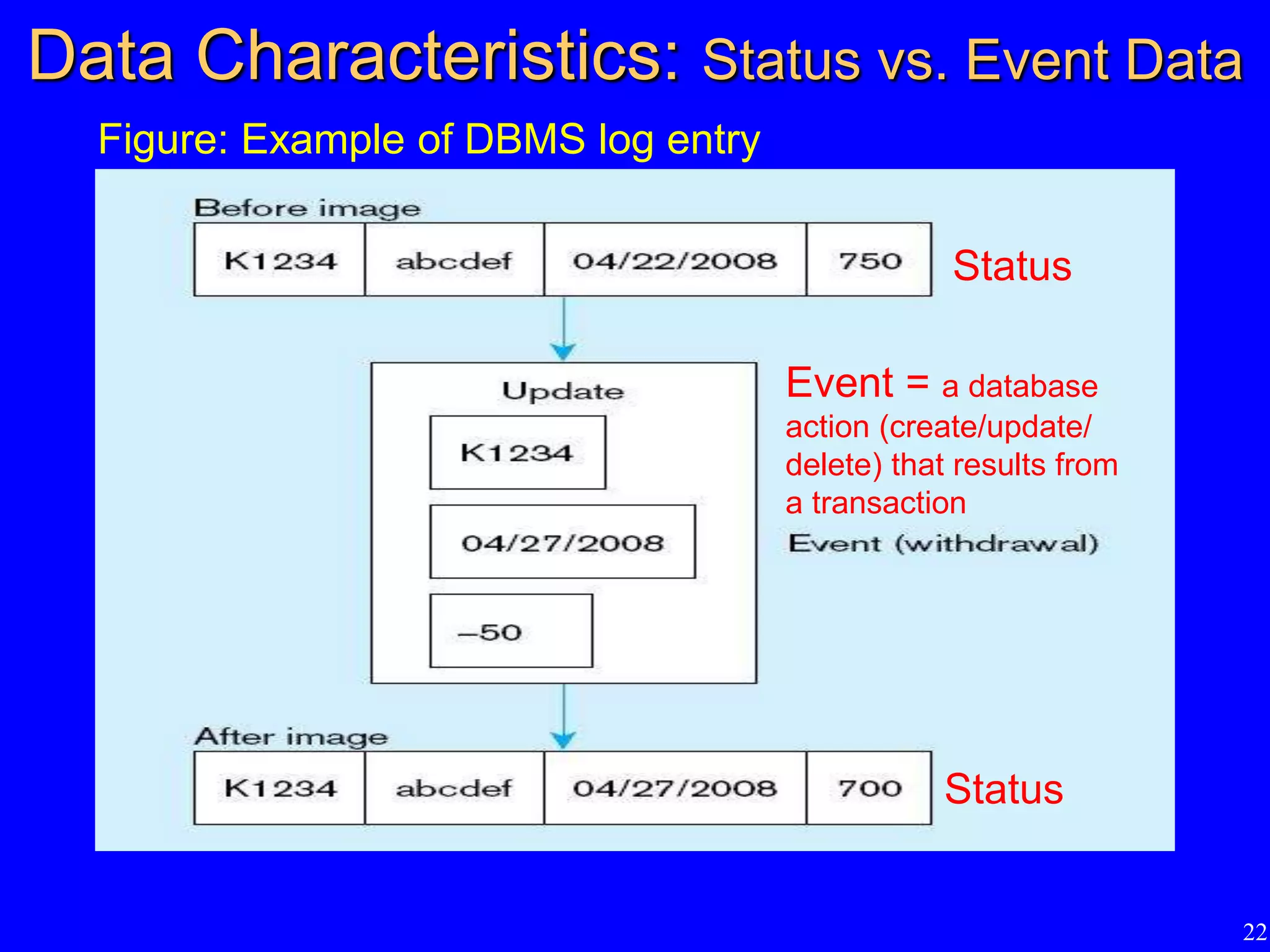
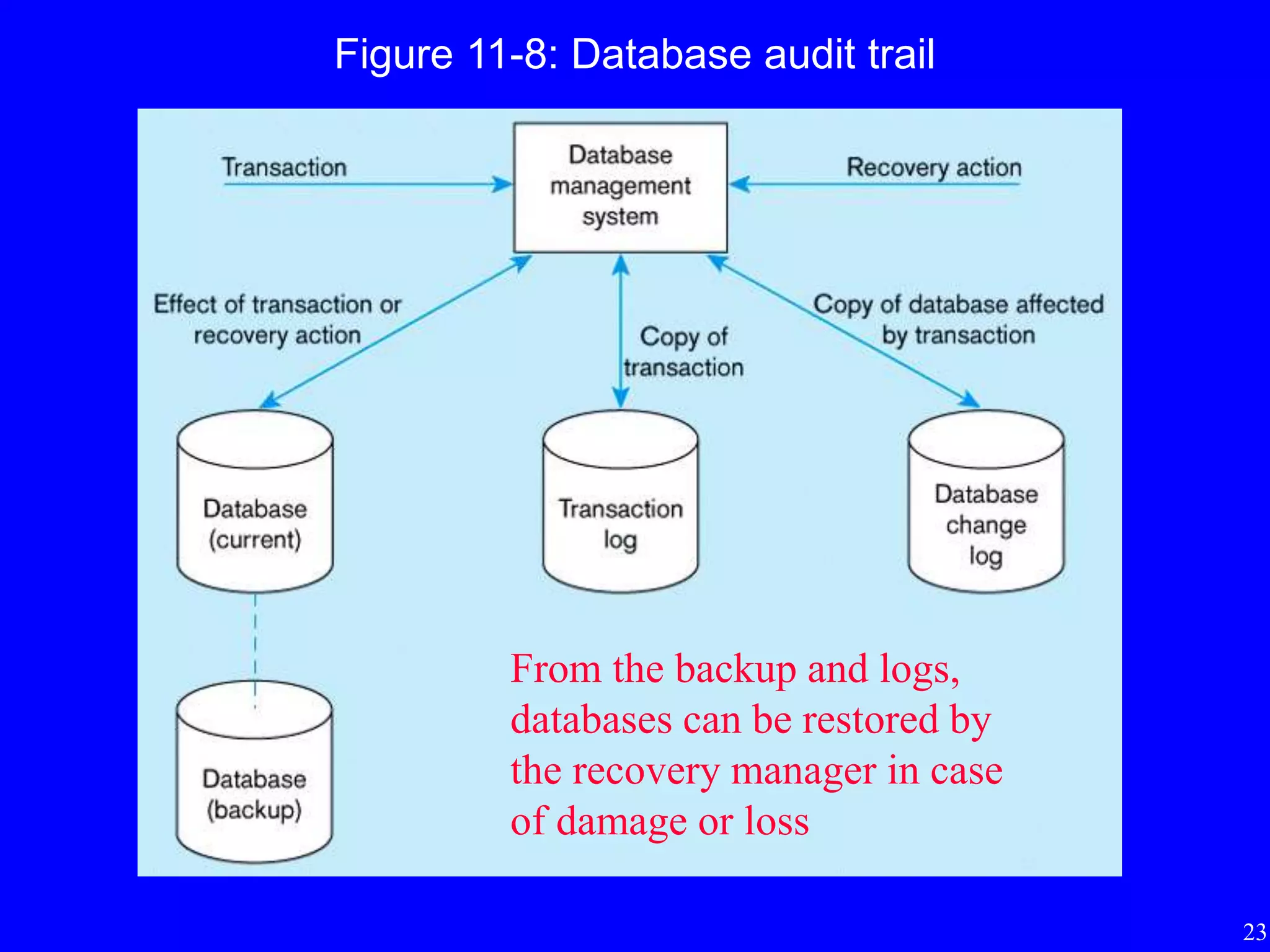
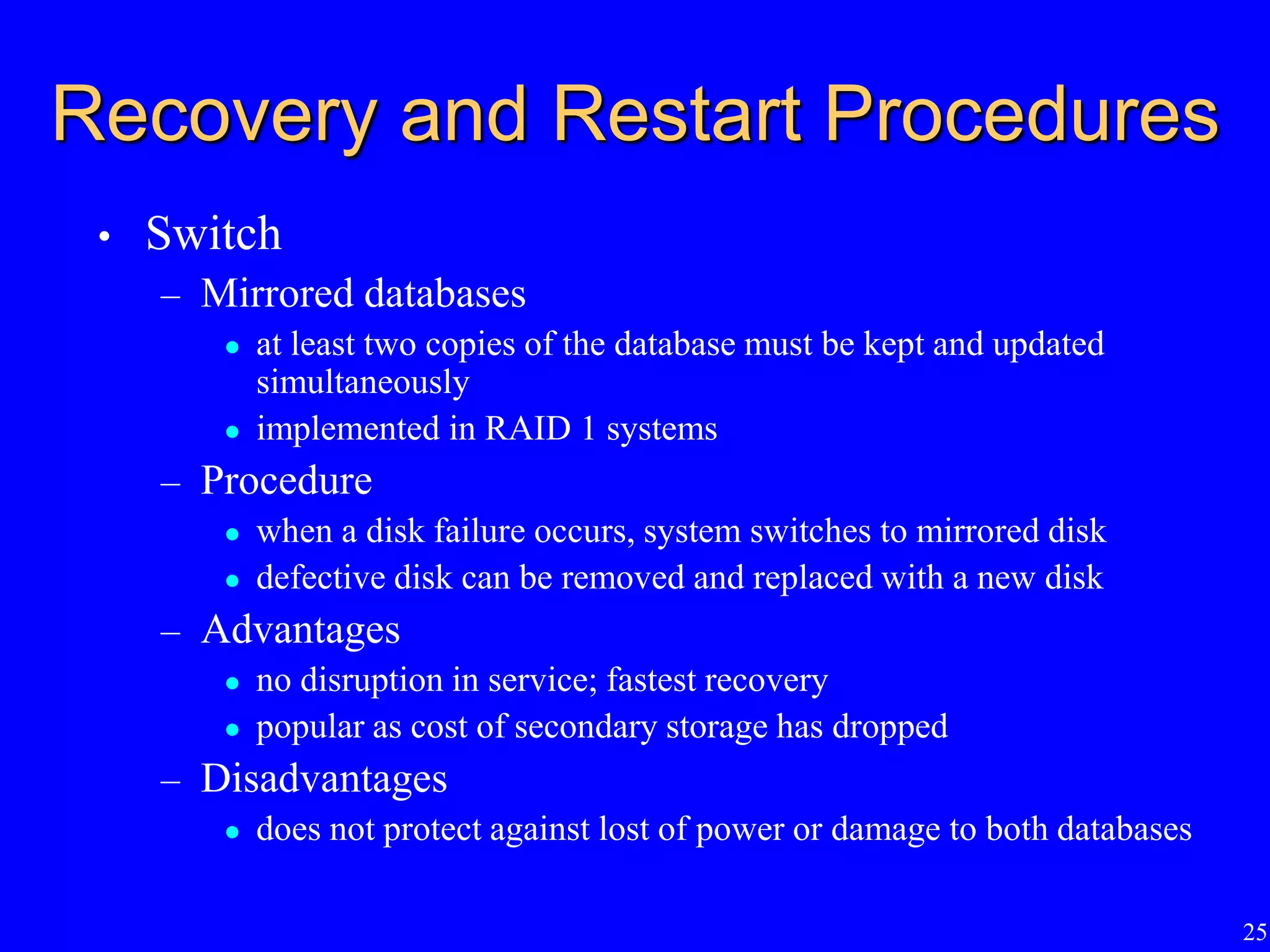
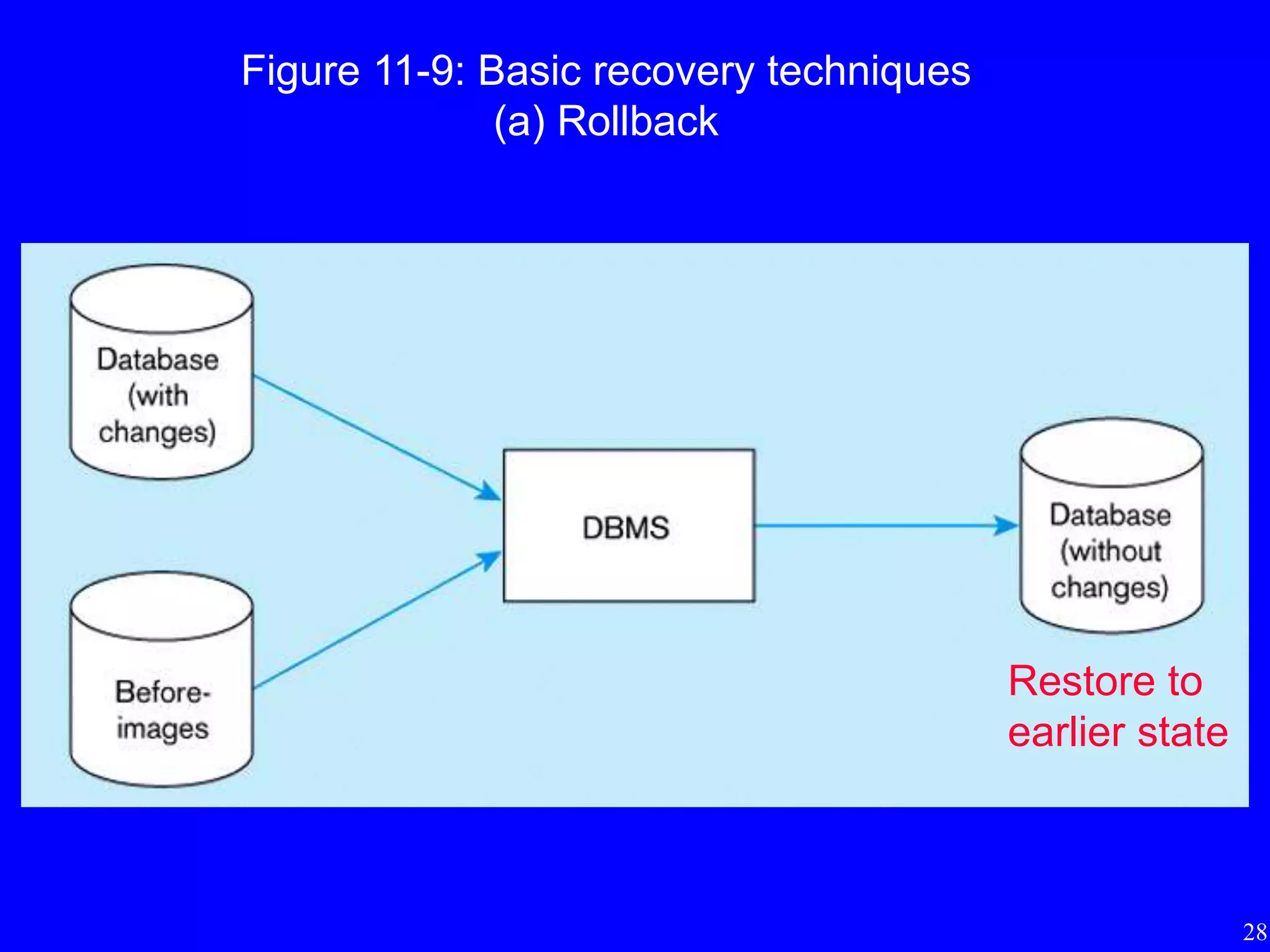
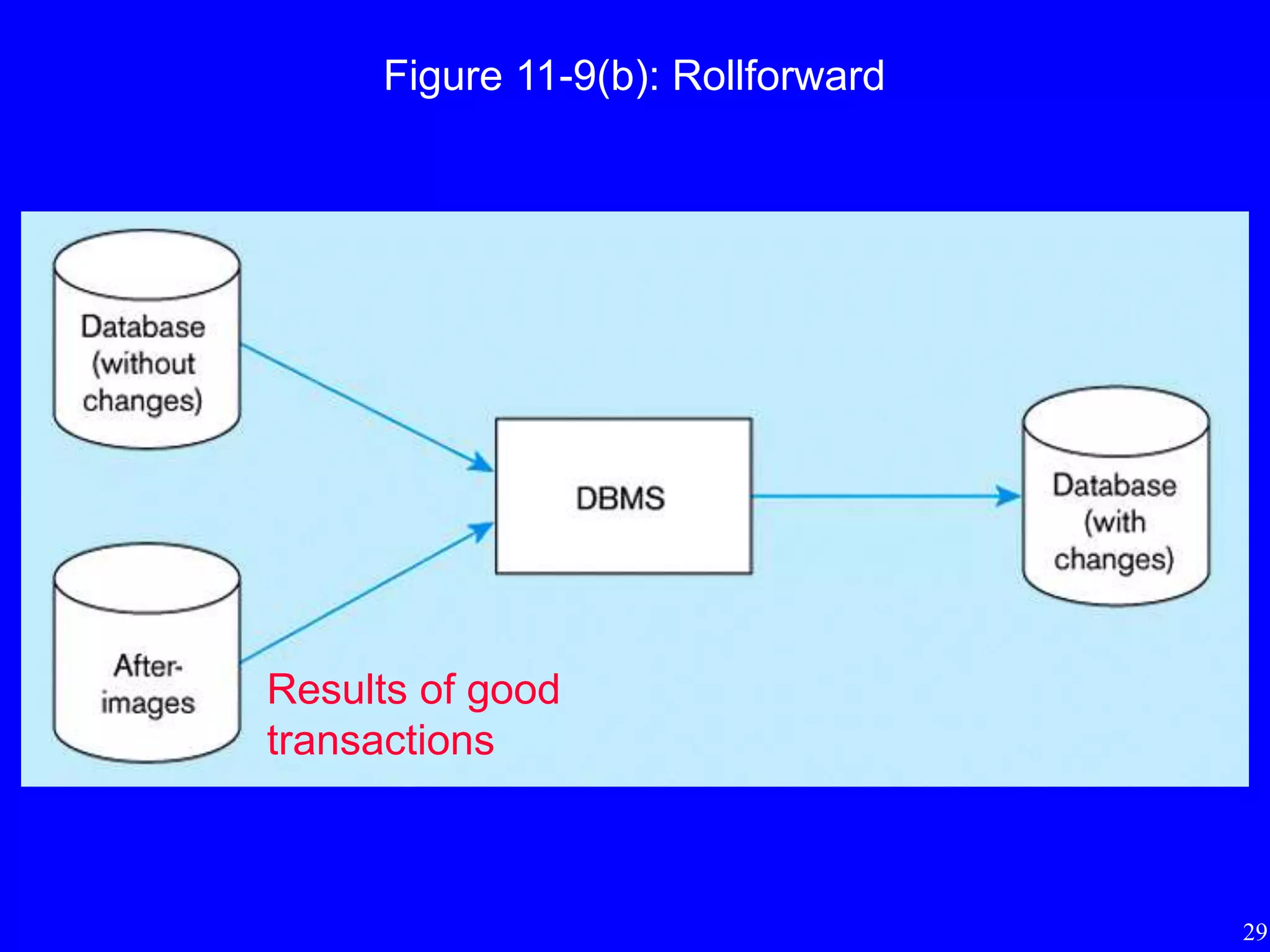
4) The importance of regularly backing up databases and using journaling facilities to facilitate recovery in case of data loss or damage.