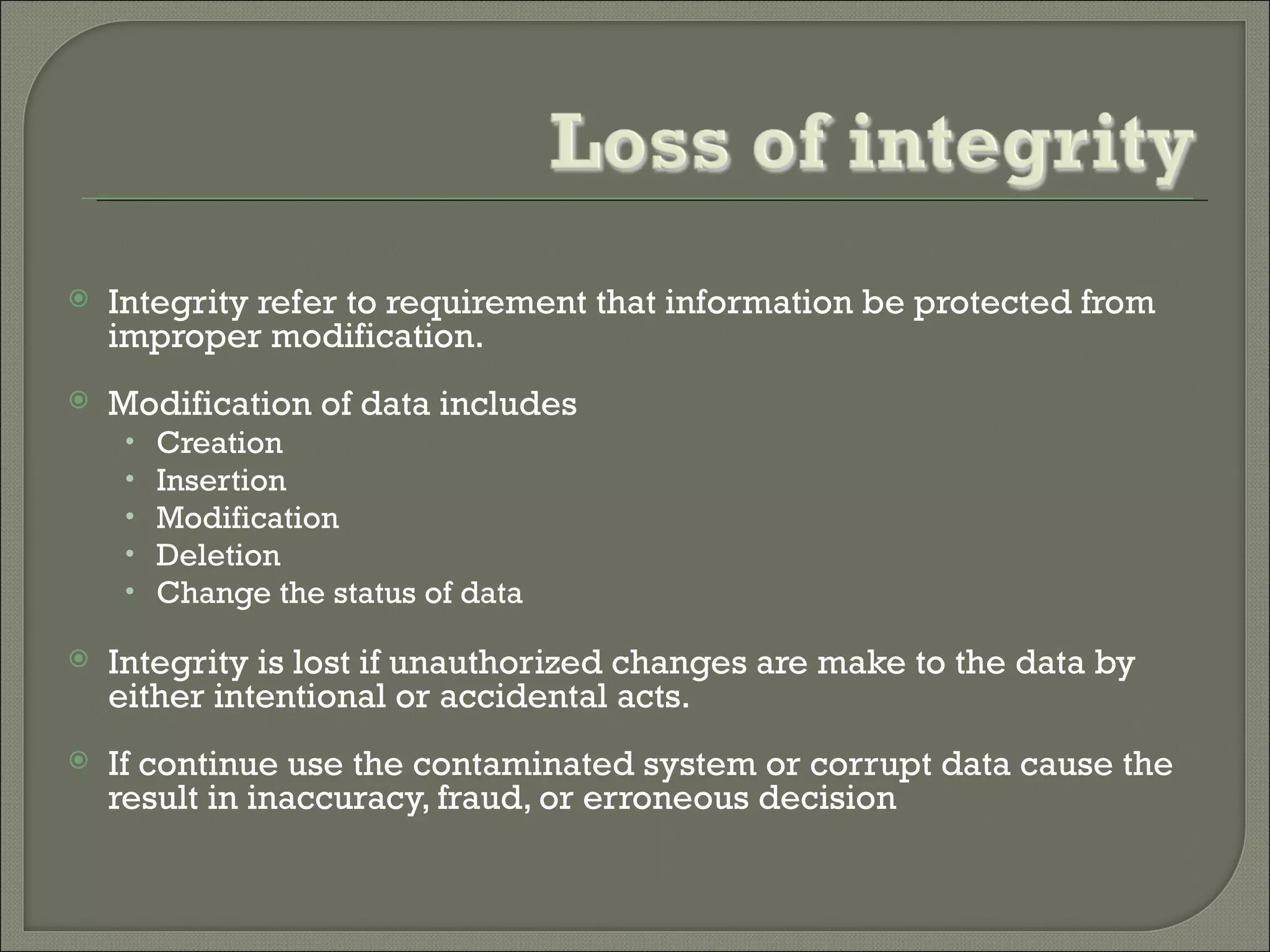
This document discusses threats to databases in e-commerce. It introduces security issues in relational databases and mechanisms for enforcing multiple security levels. It discusses types of security threats like loss of integrity, availability, and confidentiality of data. Specific threats to e-commerce databases are unauthorized access and alteration of user data or product information. The document proposes countermeasures like access control, inference control, flow control, encryption, and backups to protect databases from these threats.