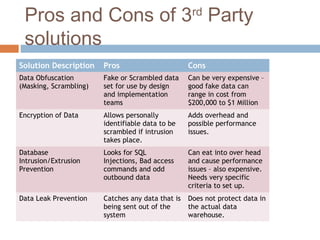
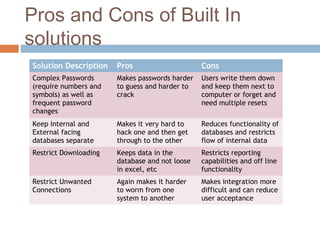
The document summarizes a seminar on database security threats, challenges, and approaches. It discusses how database security aims to protect the confidentiality, integrity, and availability of data. It outlines several challenges to database security like complex access control policies, security for large distributed databases, and privacy-preserving techniques. The document also discusses approaches to database security including encryption, digital signatures, role-based access control policies, and both built-in database protections and third-party security solutions.






![New Data Security Concerns
Data quality and completeness.
–Is the data complete and correct with respect
to the external world? Is the data up-to-date?
Data Provenance, Ownership and IPR
[intellectual property rights].
–From which information sources are the data
in a database coming from?](https://image.slidesharecdn.com/dstca-151004130710-lva1-app6891/85/Dstca-8-320.jpg)
![Large Data Volumes
“It is estimated that the amount of information
in the world is doubling every 20 months, and
the size and number of databases are
increasing even faster” [ Rakesh Agrawal ,
VLDB Conf.].](https://image.slidesharecdn.com/dstca-151004130710-lva1-app6891/85/Dstca-9-320.jpg)

![On- Demand Business
“An on-demand business is an enterprise
whose business processes are integrated end-
to-end across the company and key partners,
suppliers and customers so it can respond
with speed to any customer demand, market
opportunity or external threat” [Nelson Mattos,
VLDB Conf.].](https://image.slidesharecdn.com/dstca-151004130710-lva1-app6891/85/Dstca-14-320.jpg)



![Database Security Challenges
6.Security for GIS and spatial databases
Techniques for access control and integrity
specifically tailored to spatial data and GIS
[Geographic information system].
7.Data security in pervasive computing
environments
8. Integration of DB access control systems
with trust negotiation systems and identity
management schemes](https://image.slidesharecdn.com/dstca-151004130710-lva1-app6891/85/Dstca-19-320.jpg)