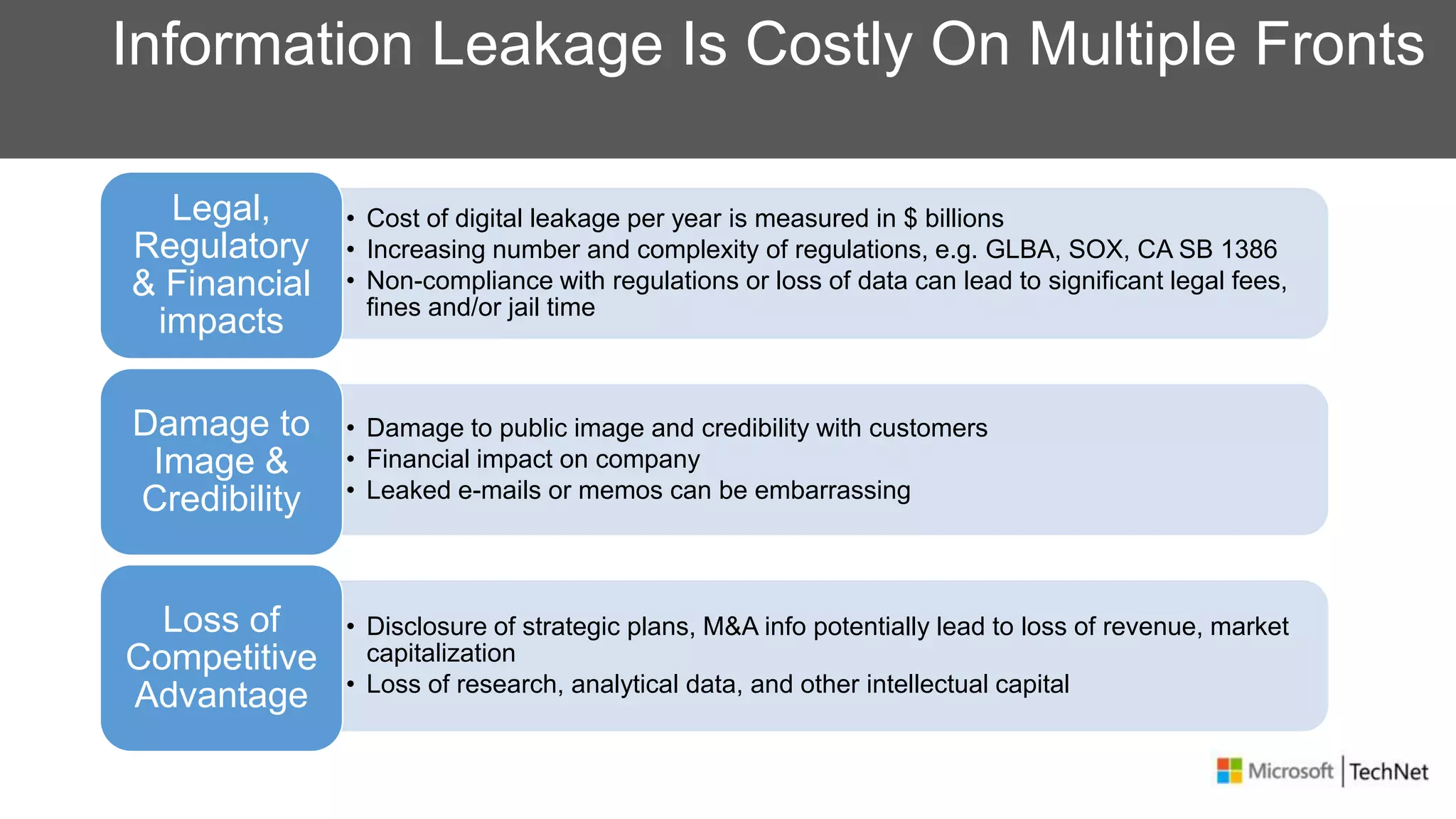
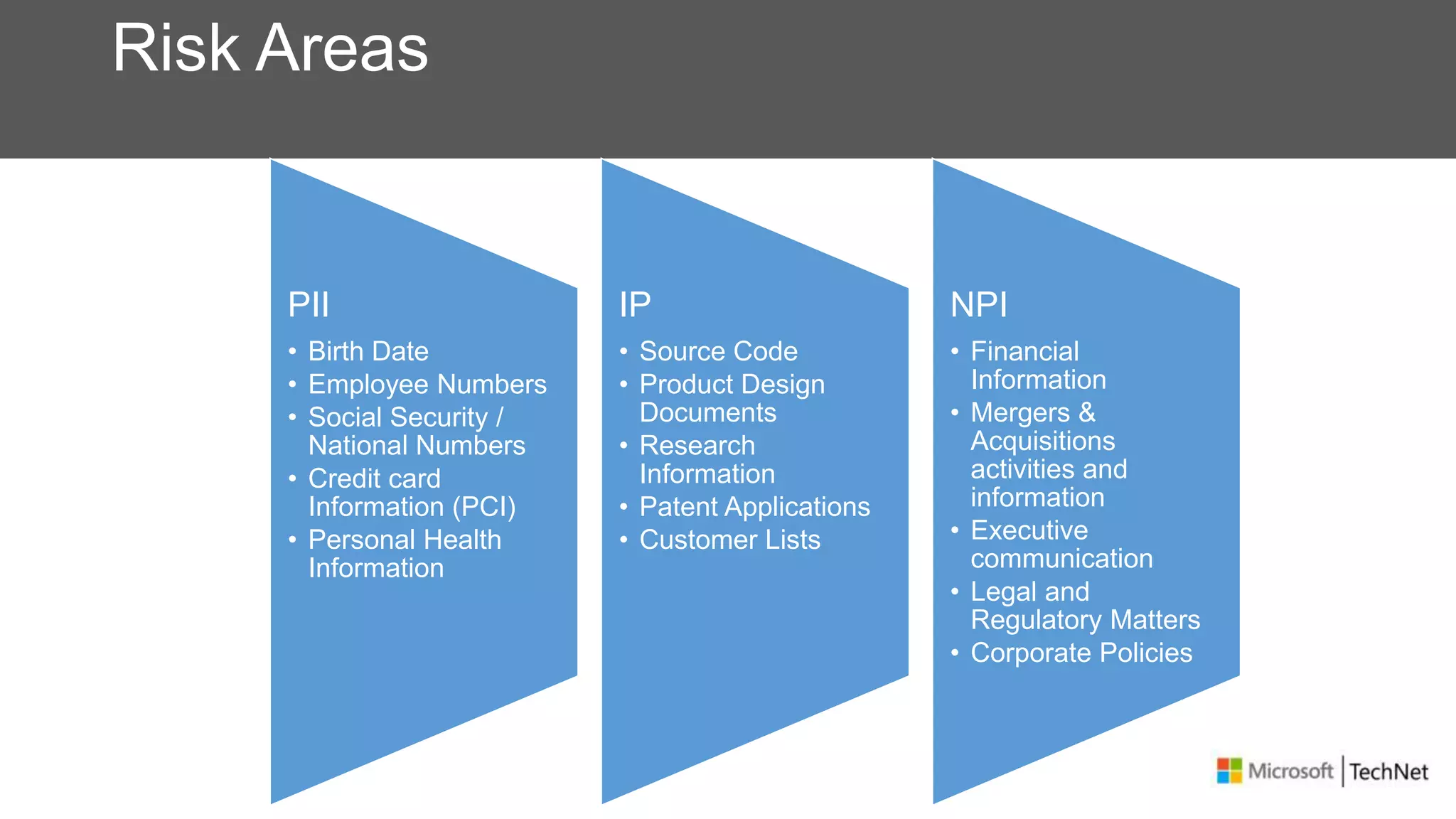
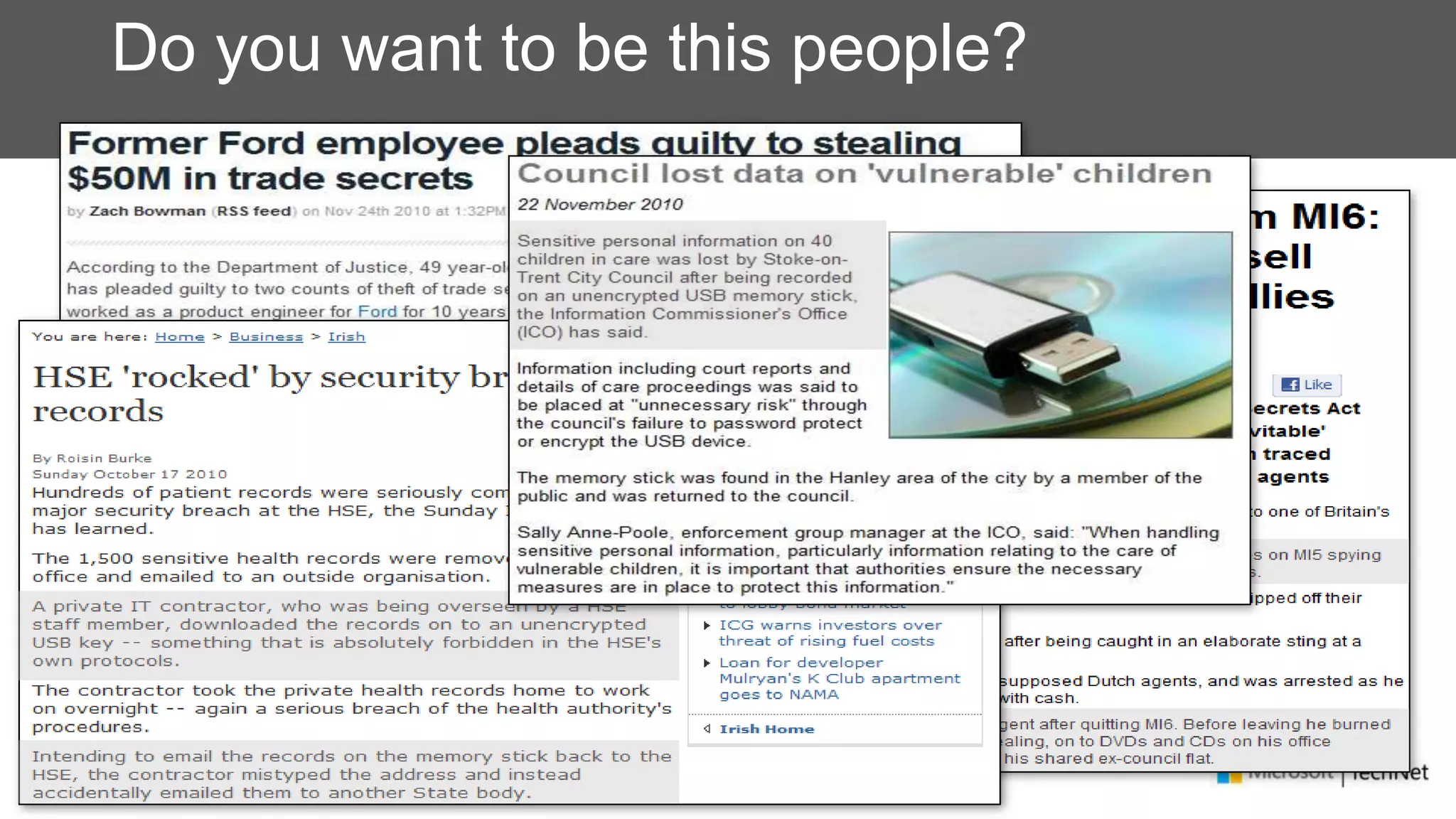
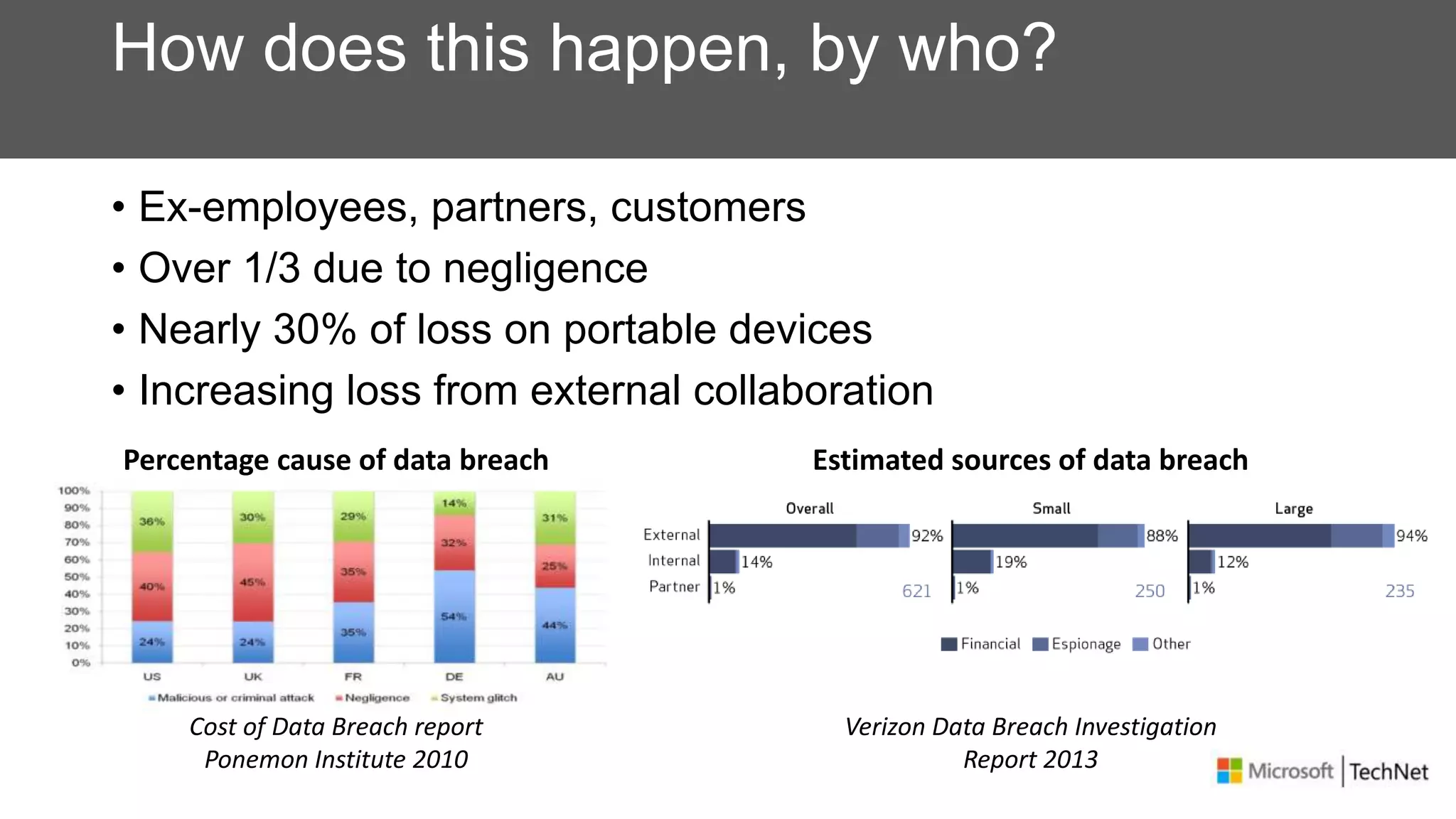
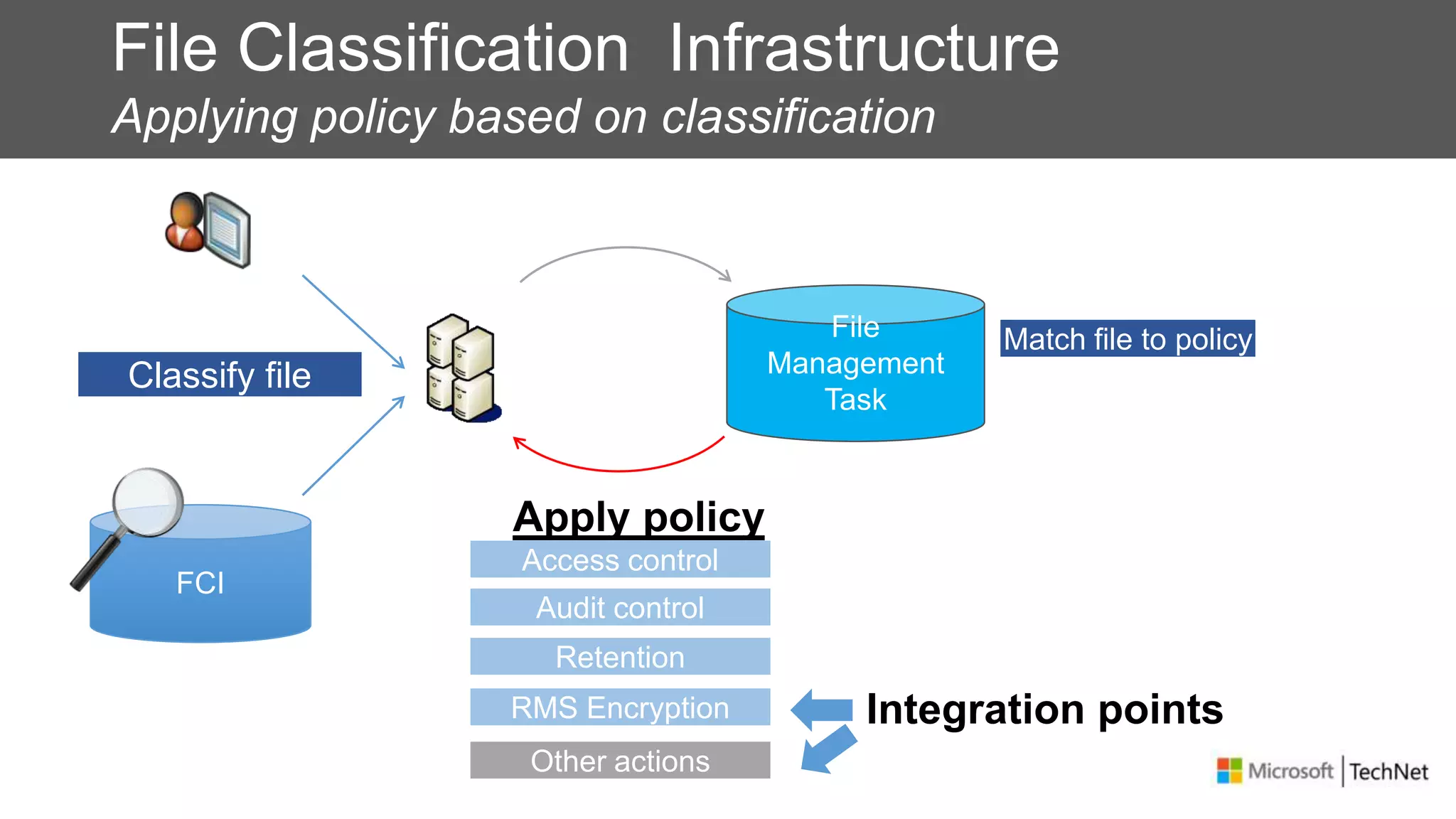
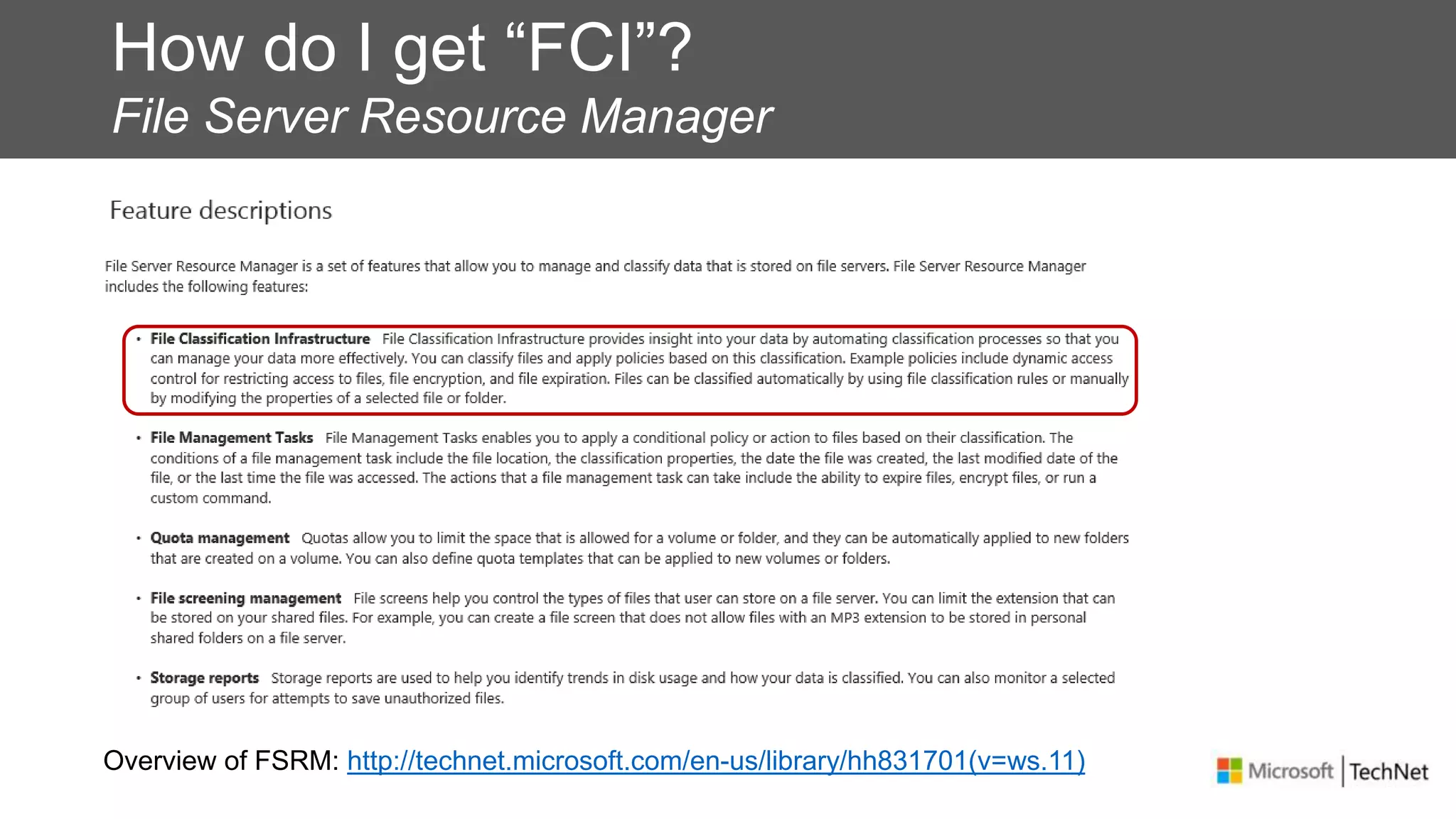
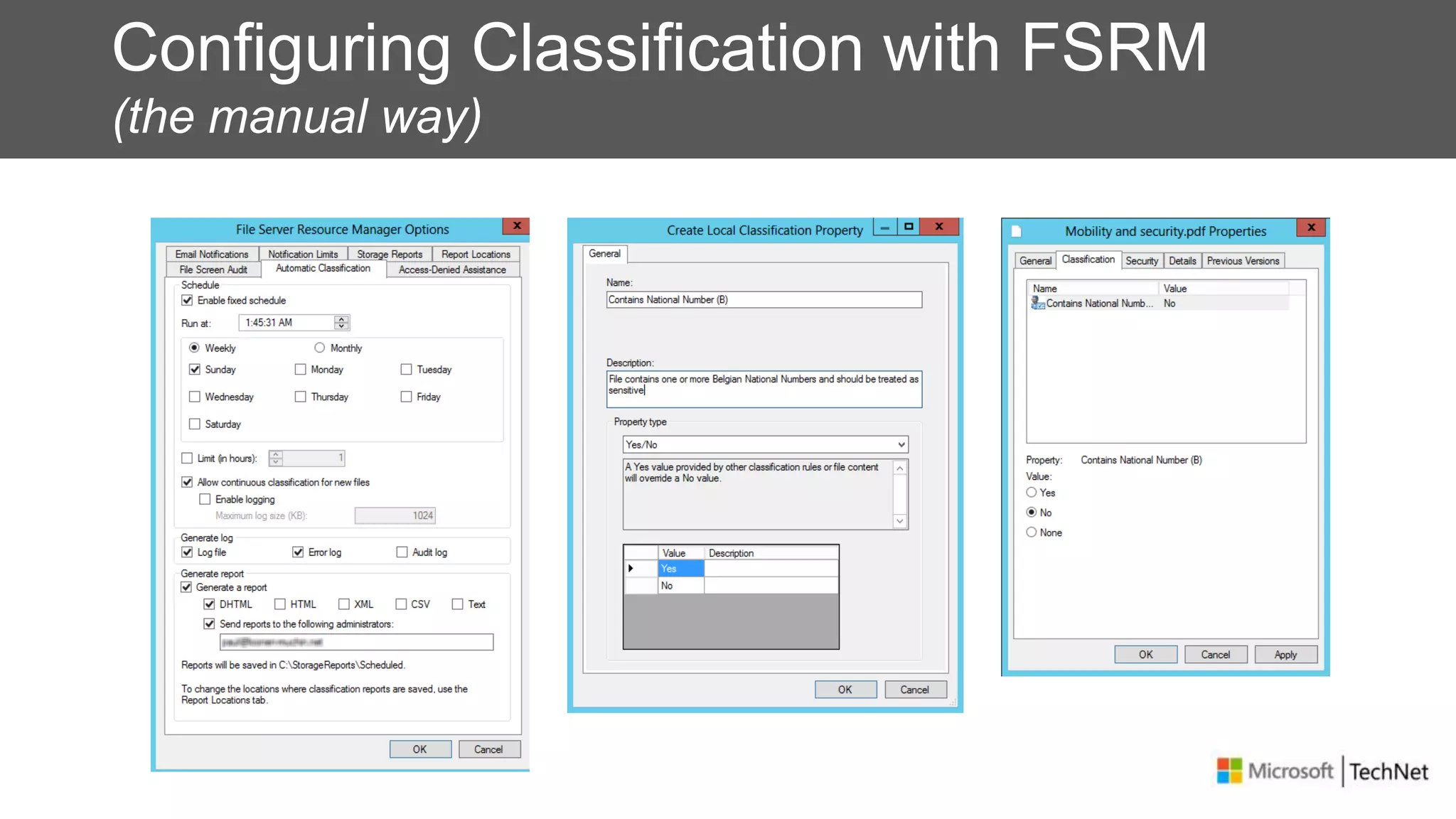
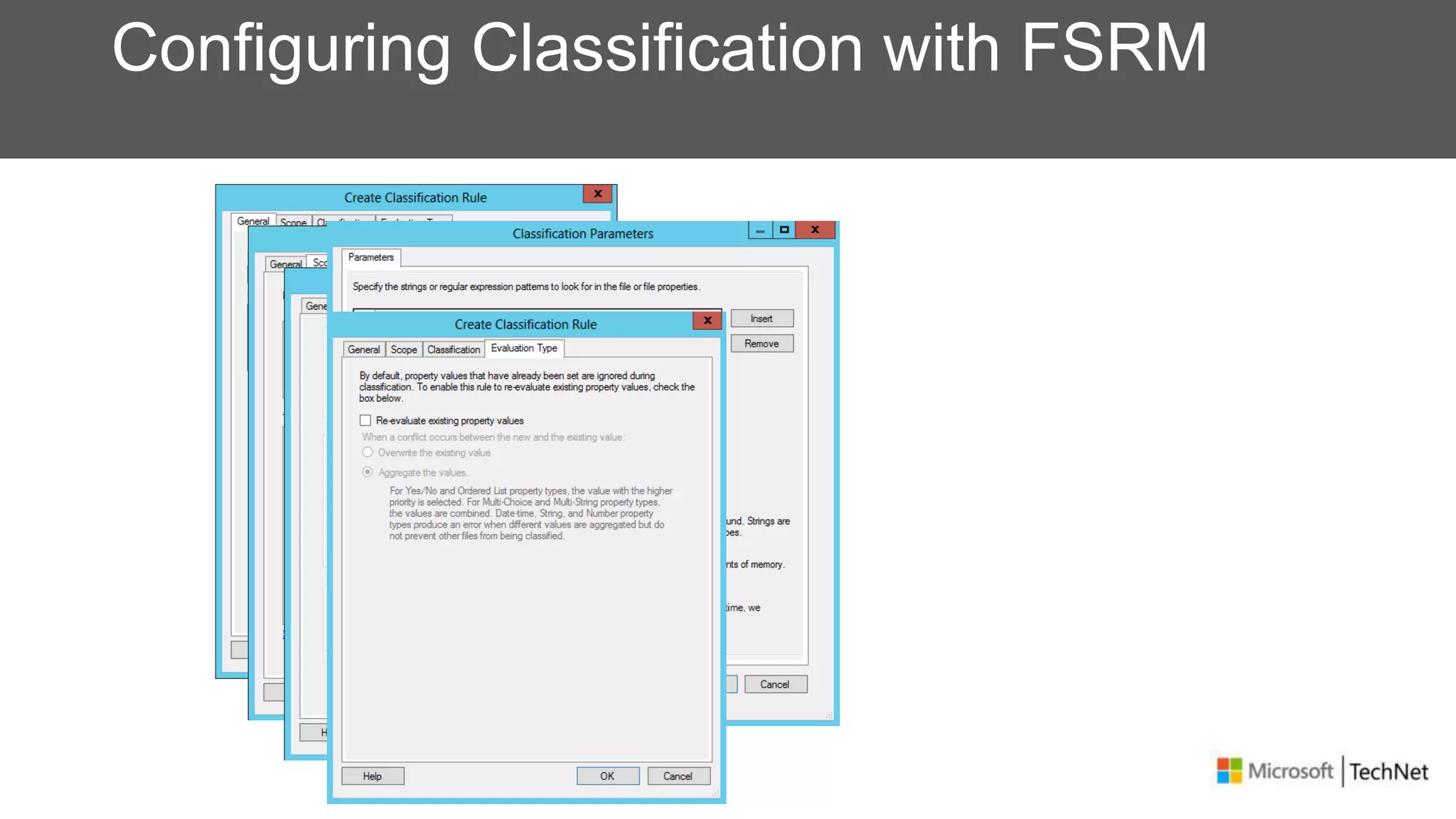
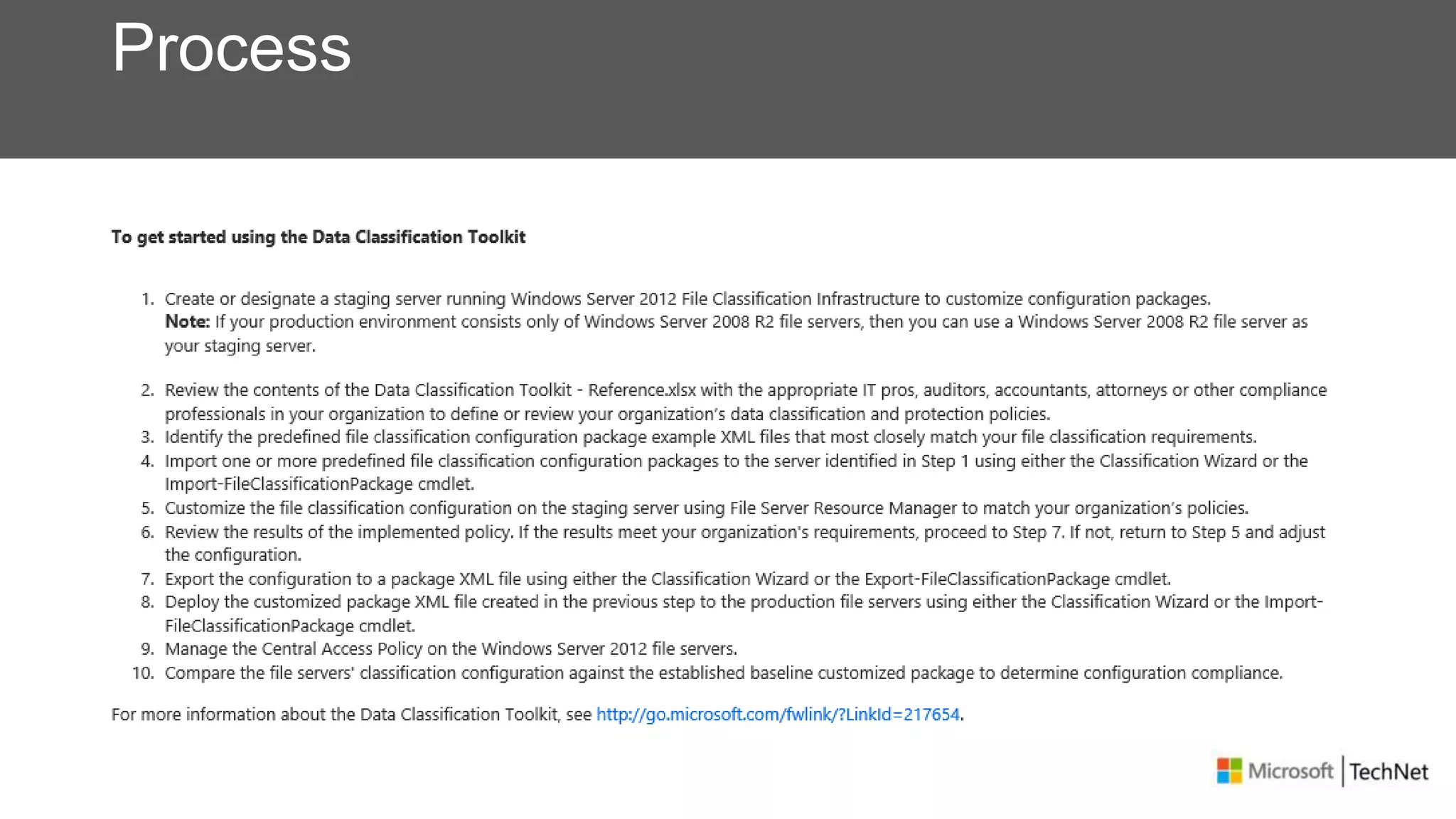
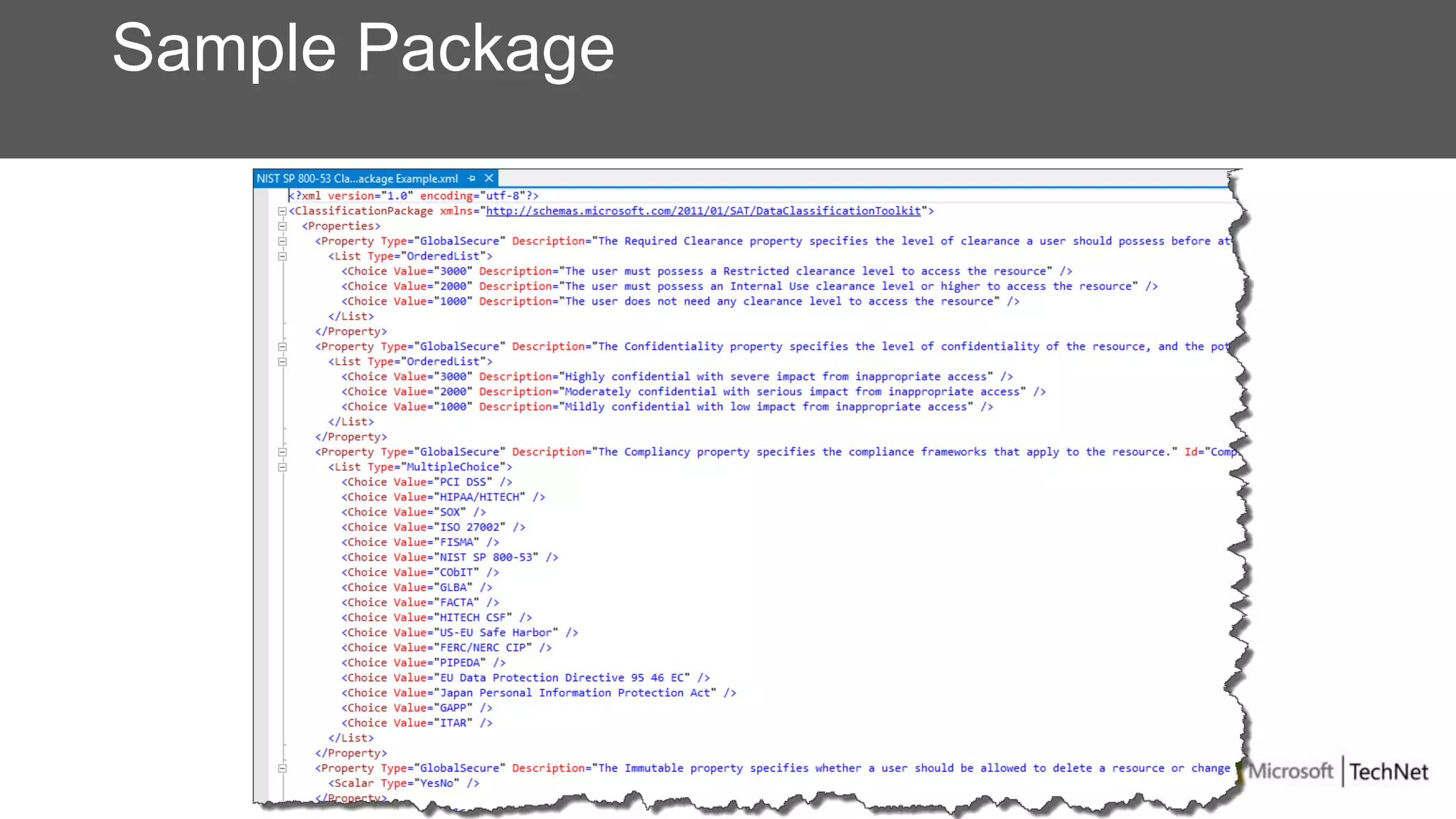
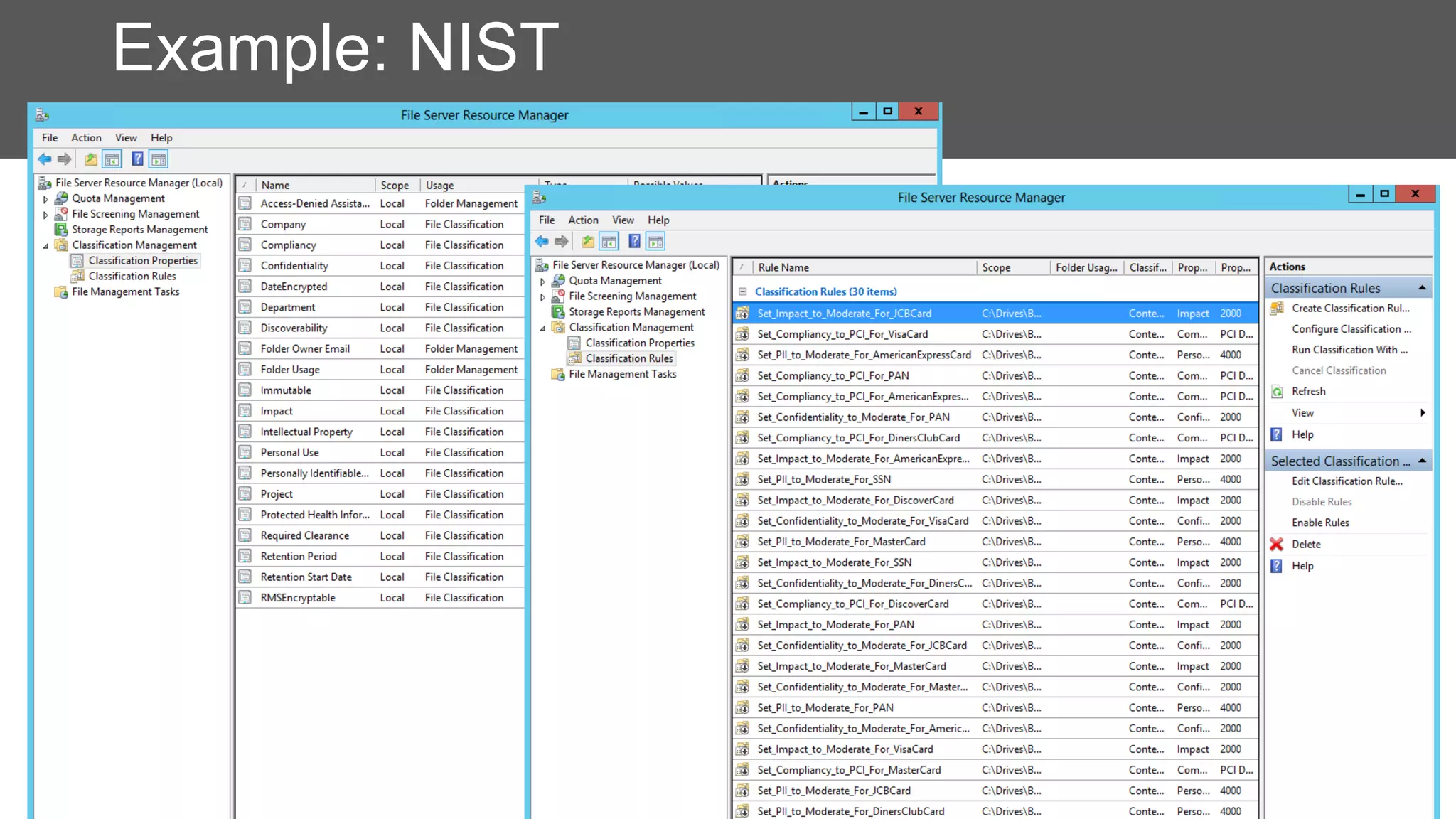
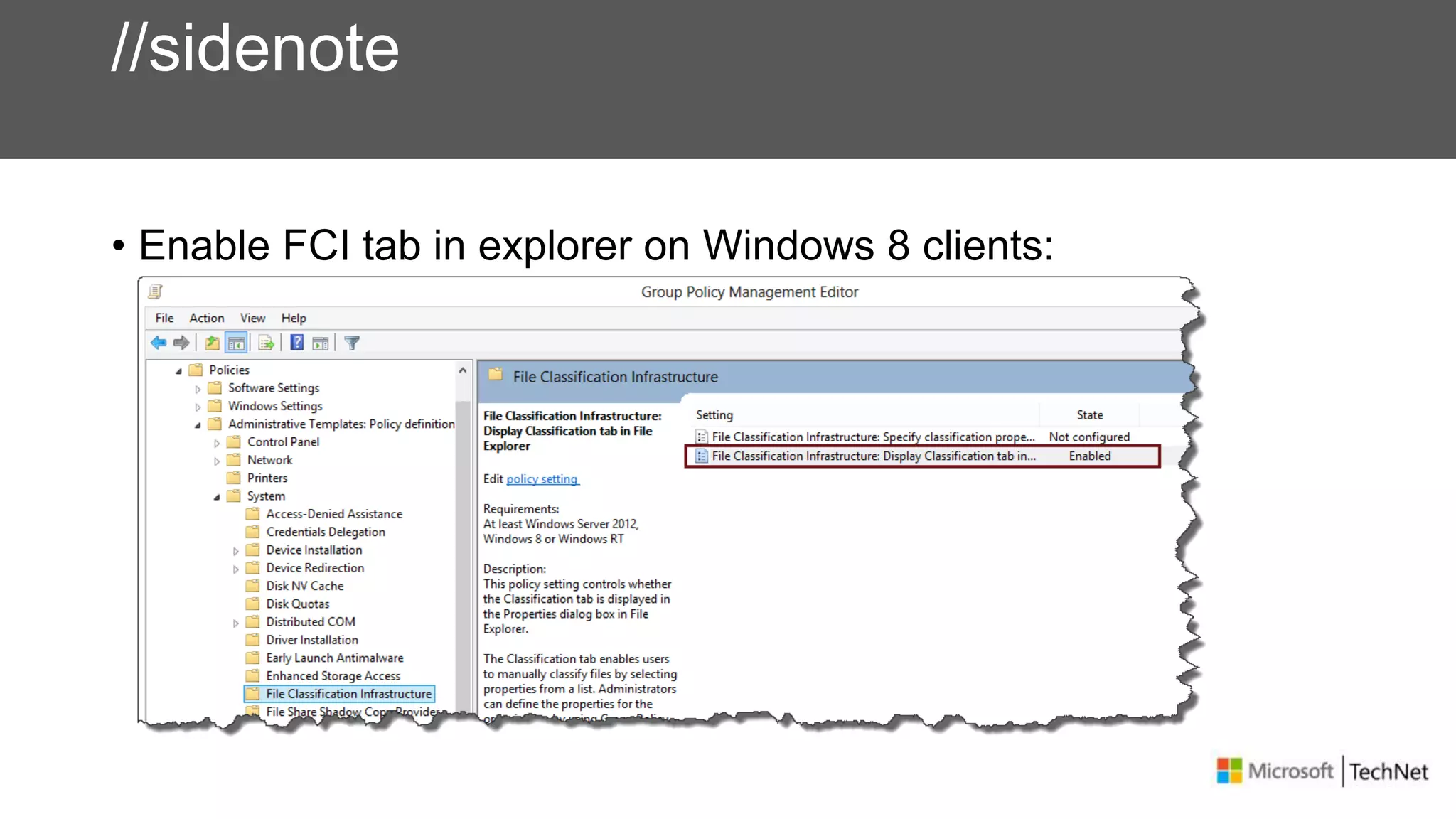
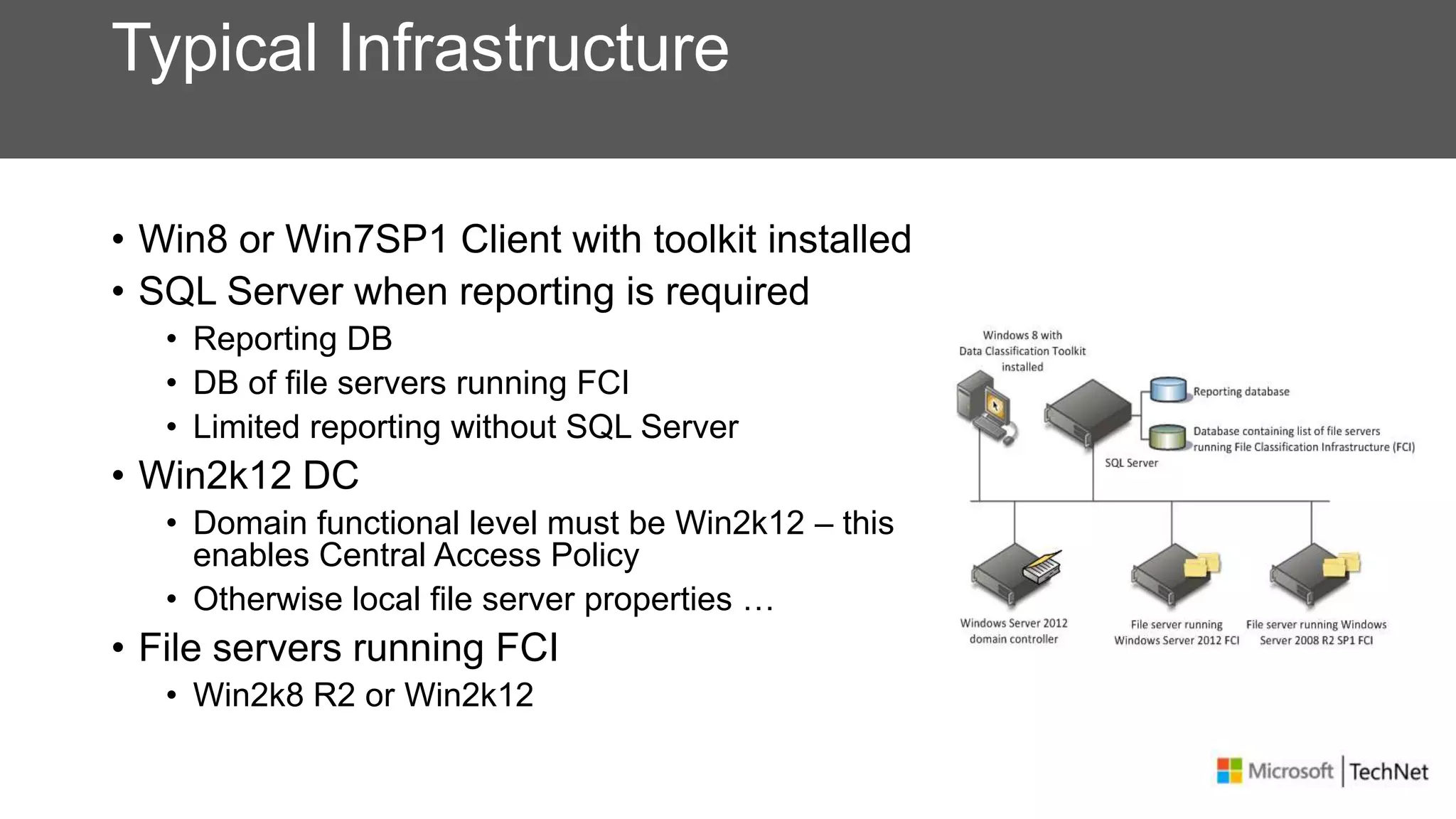
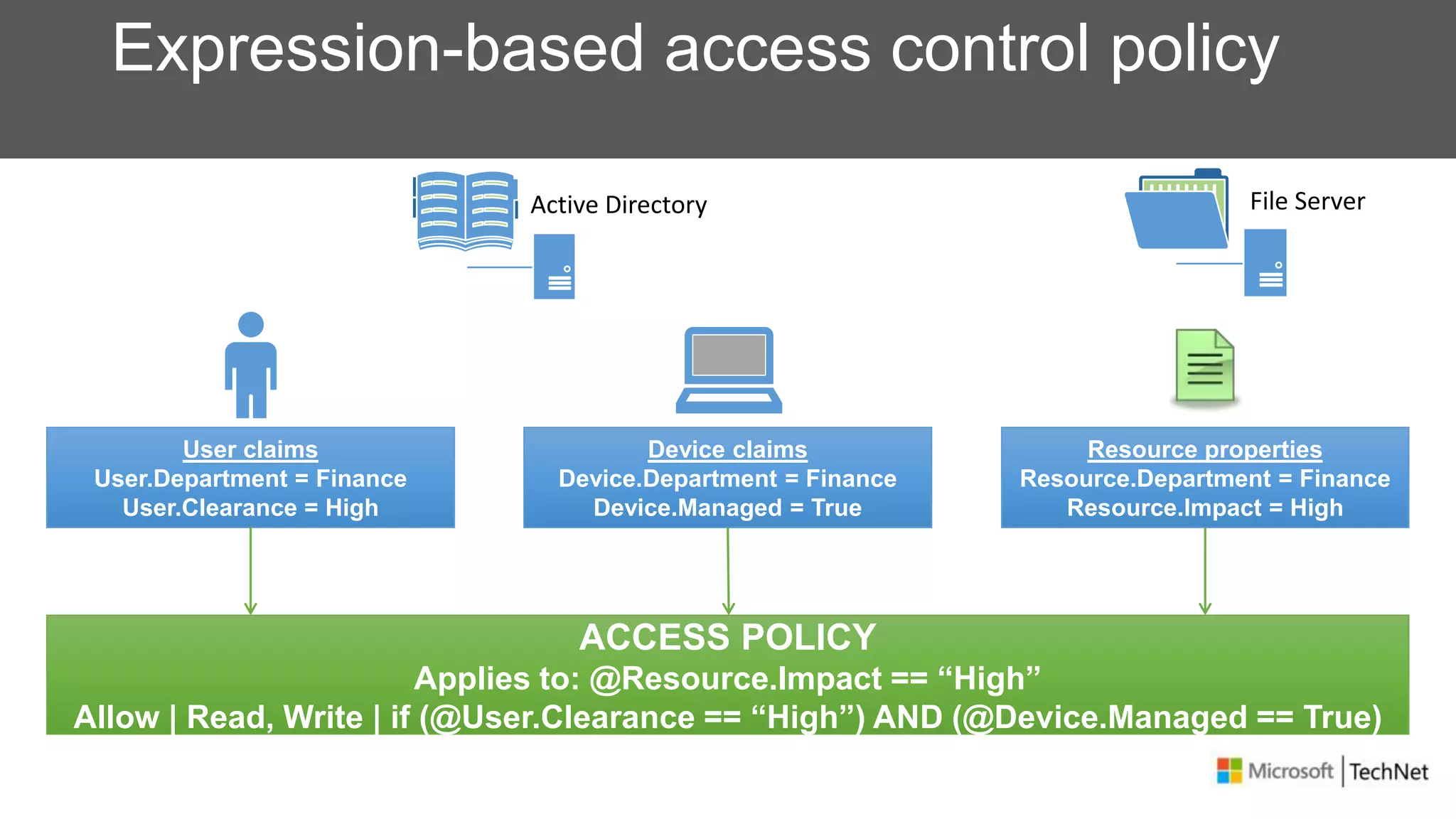
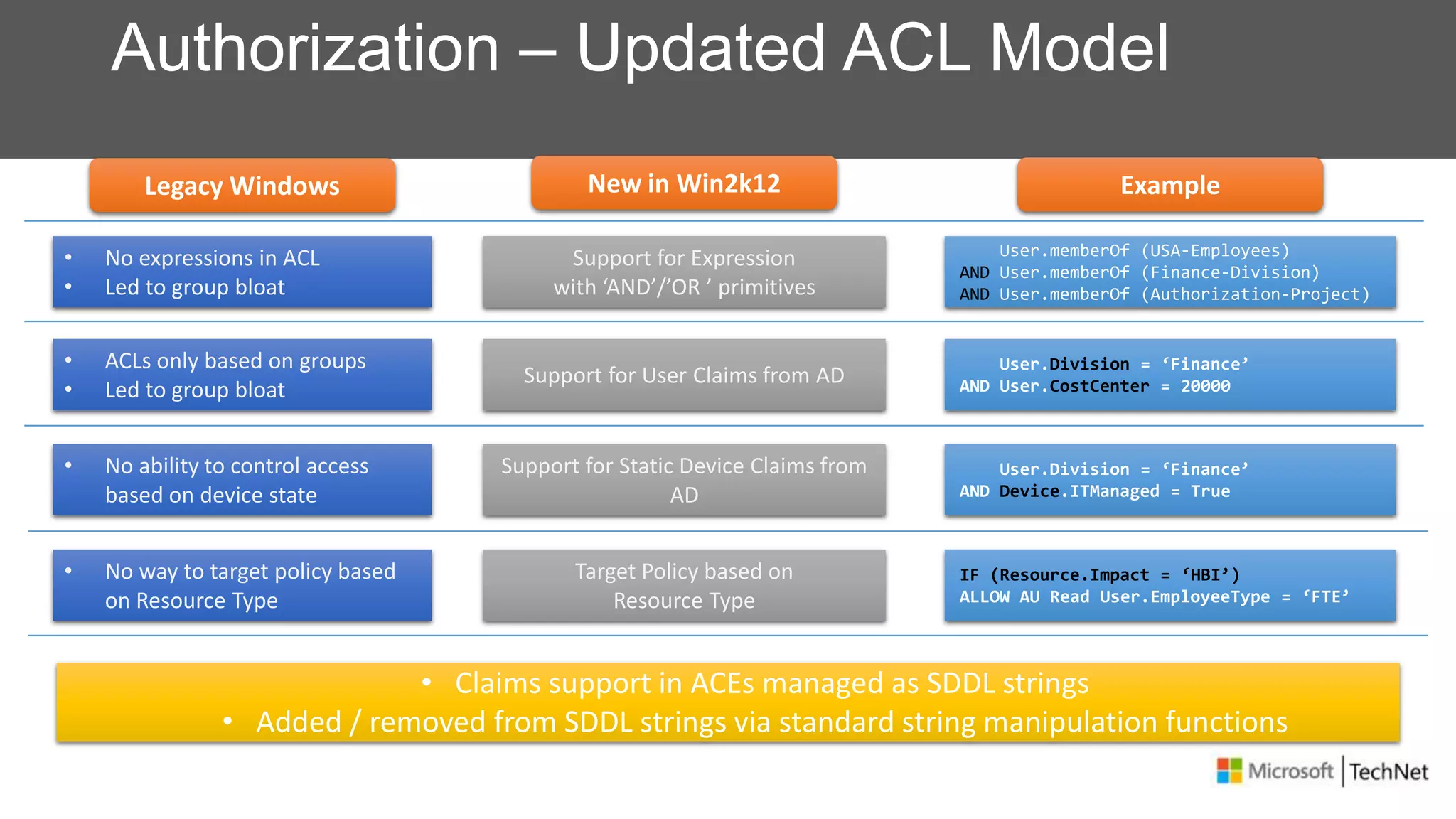
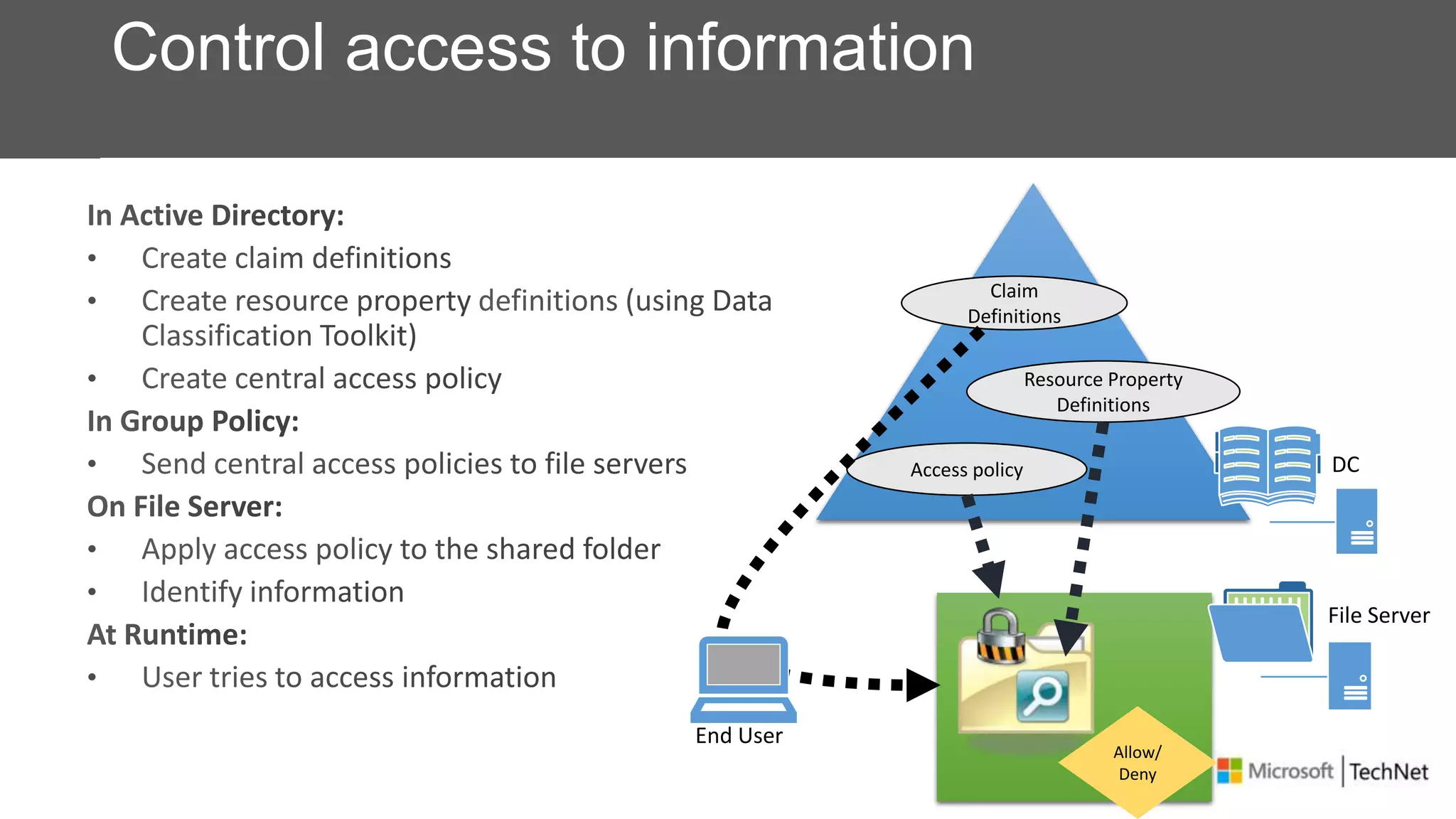
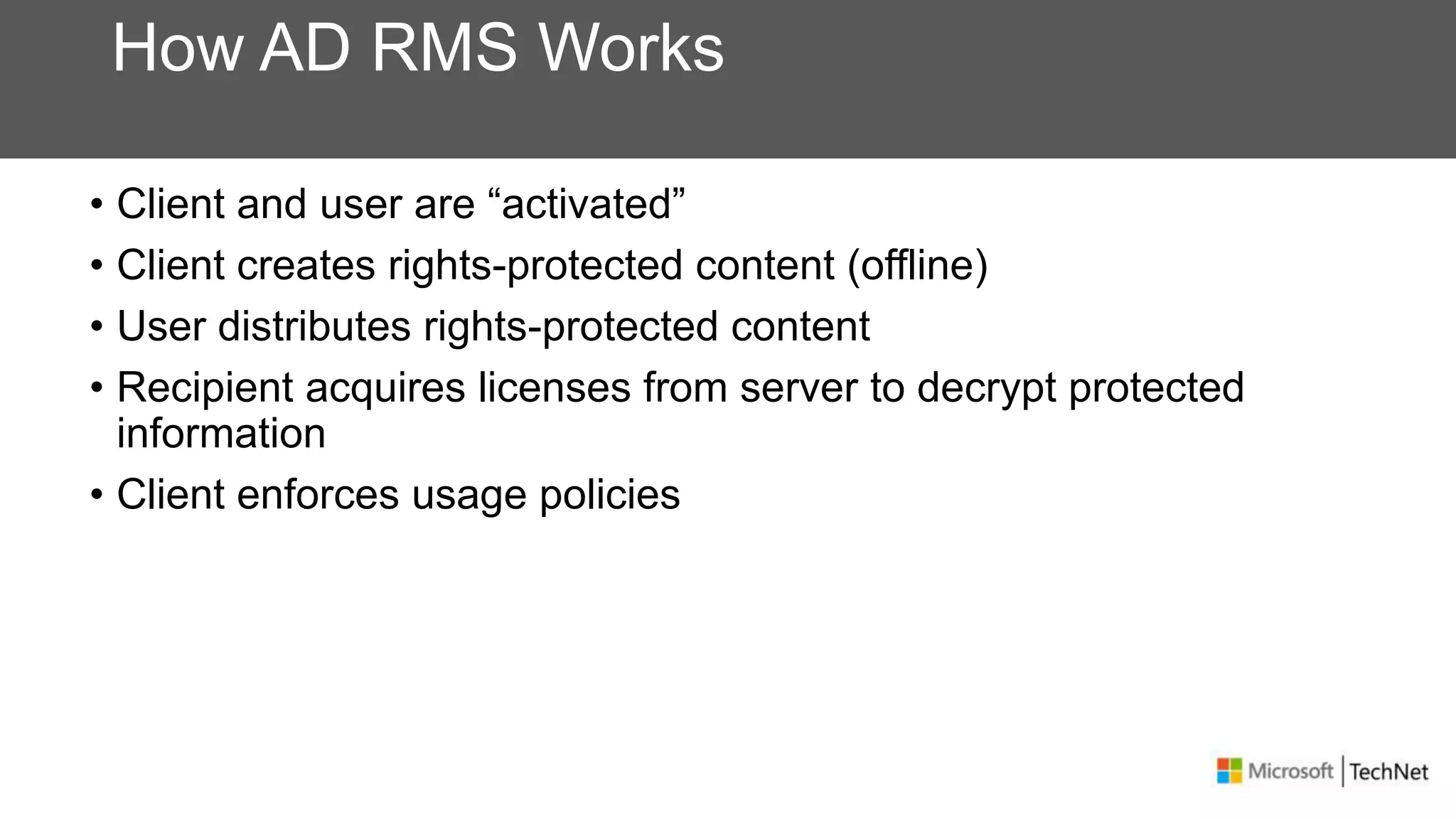
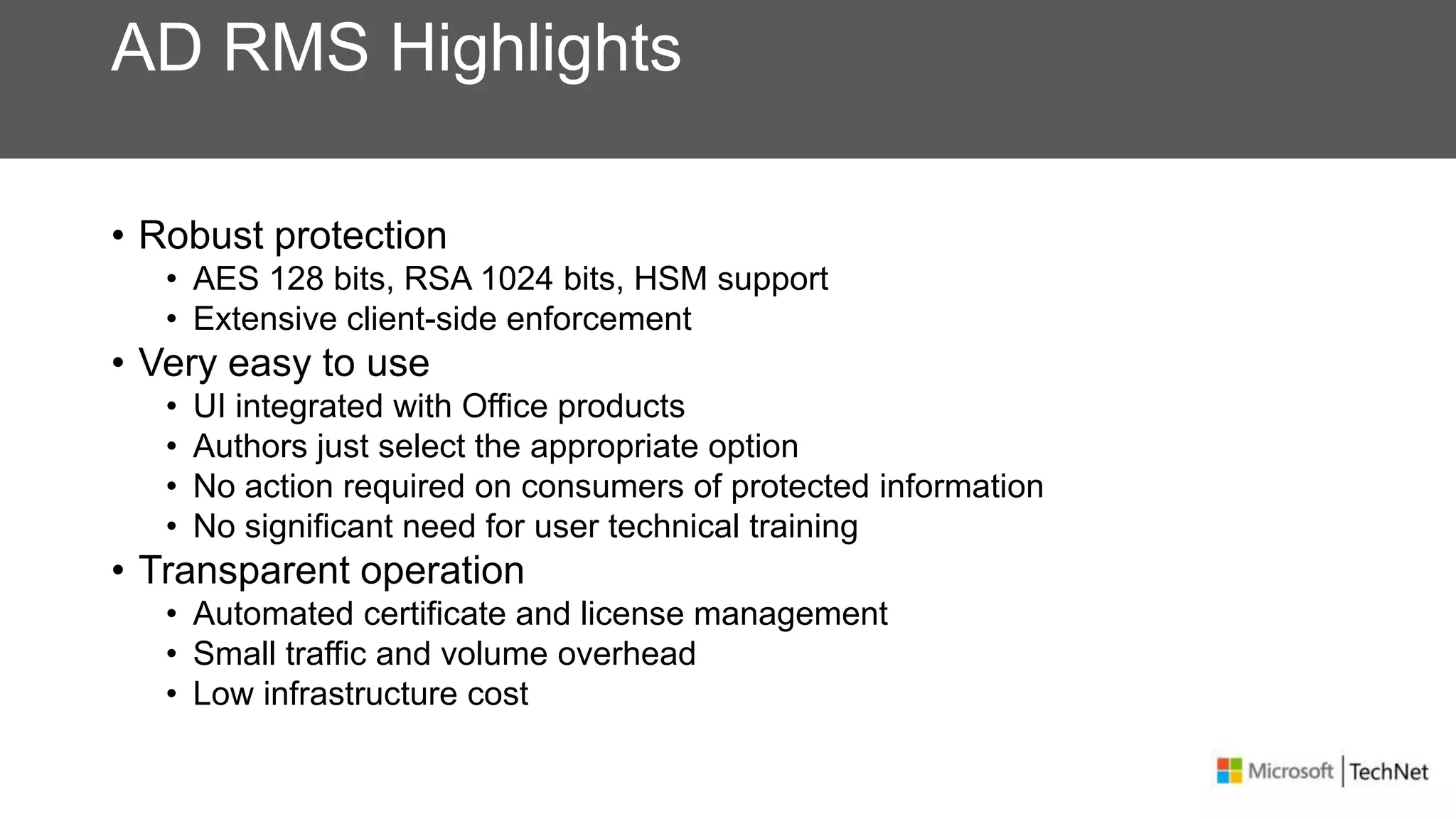
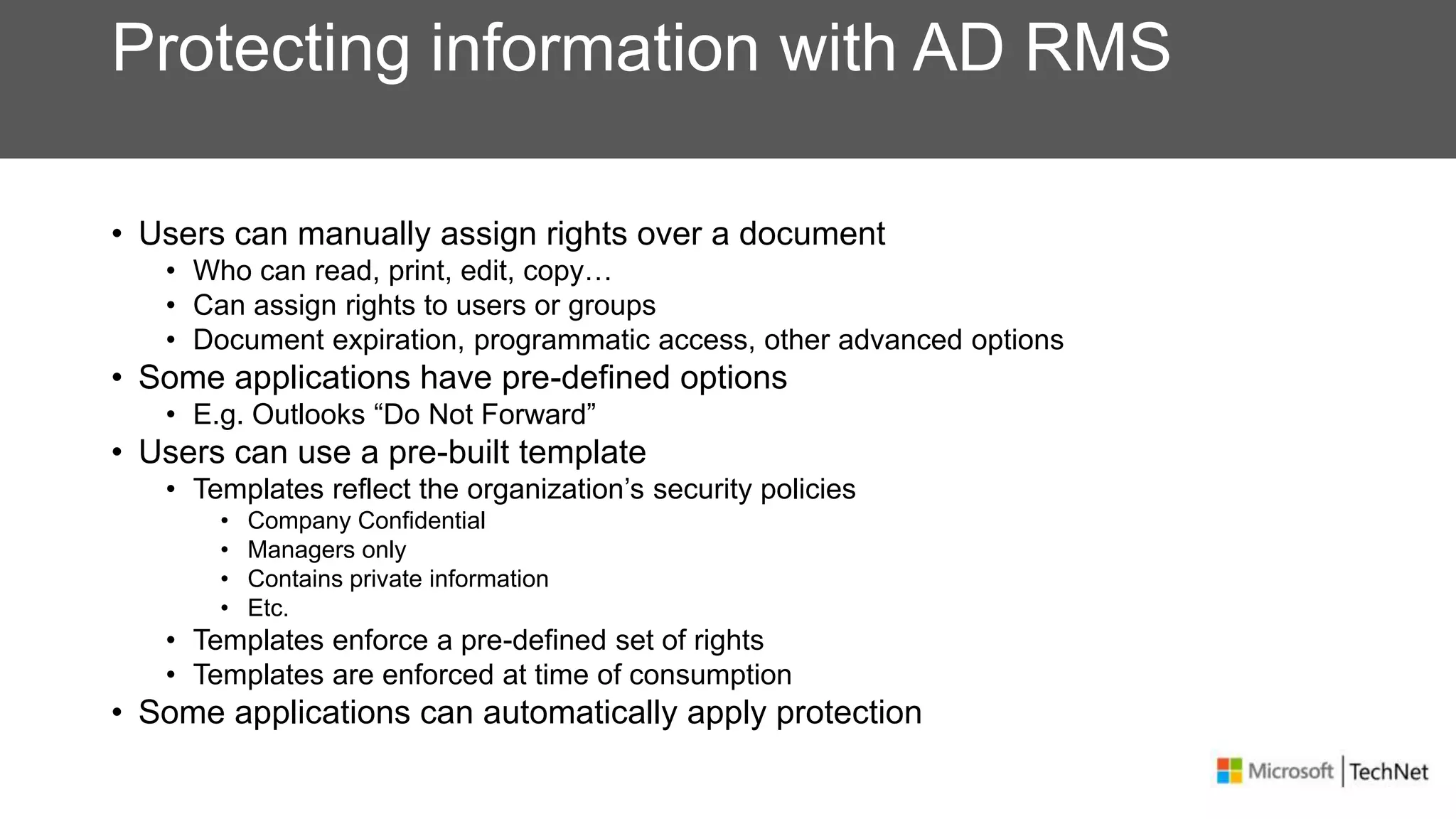
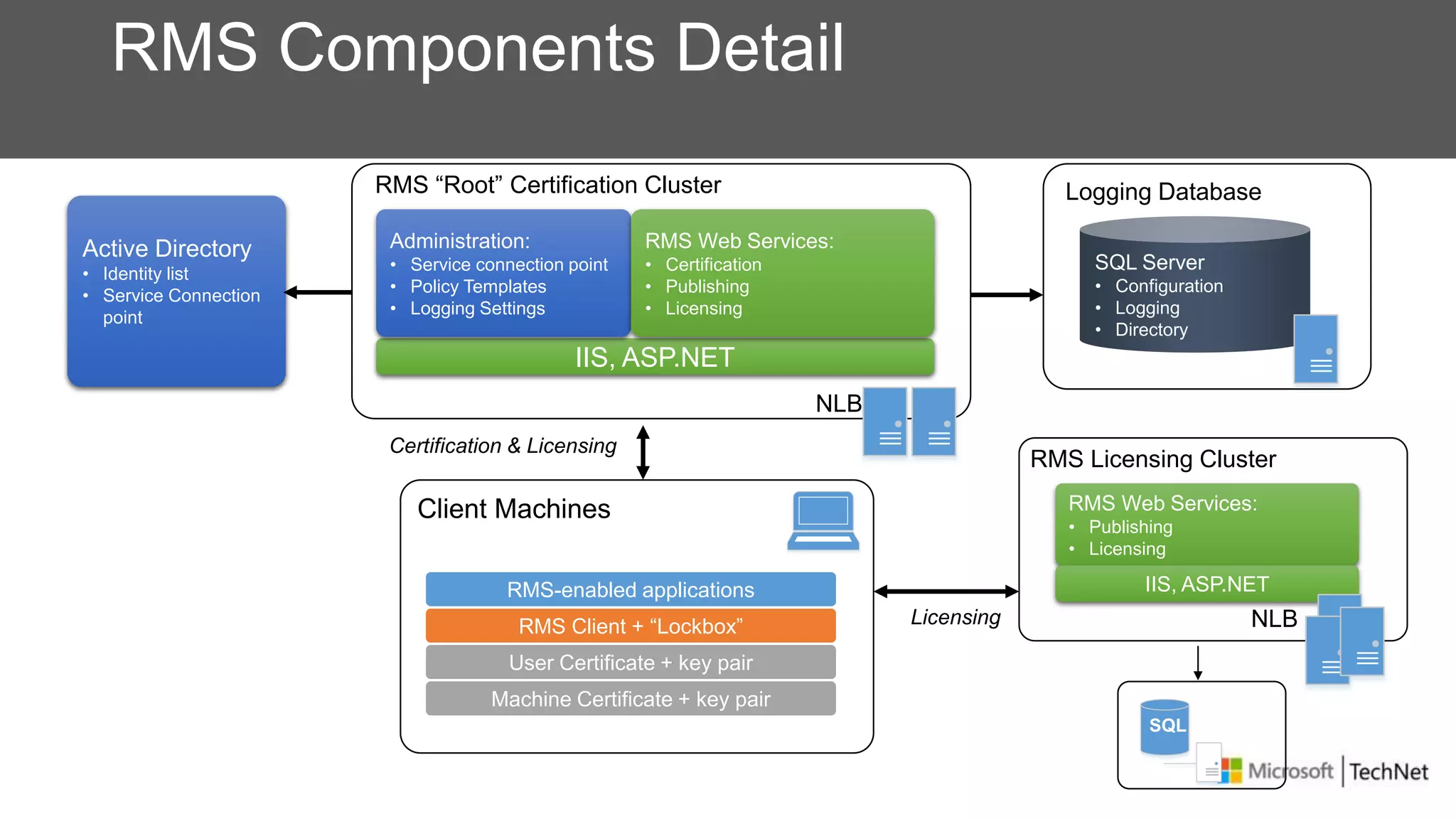
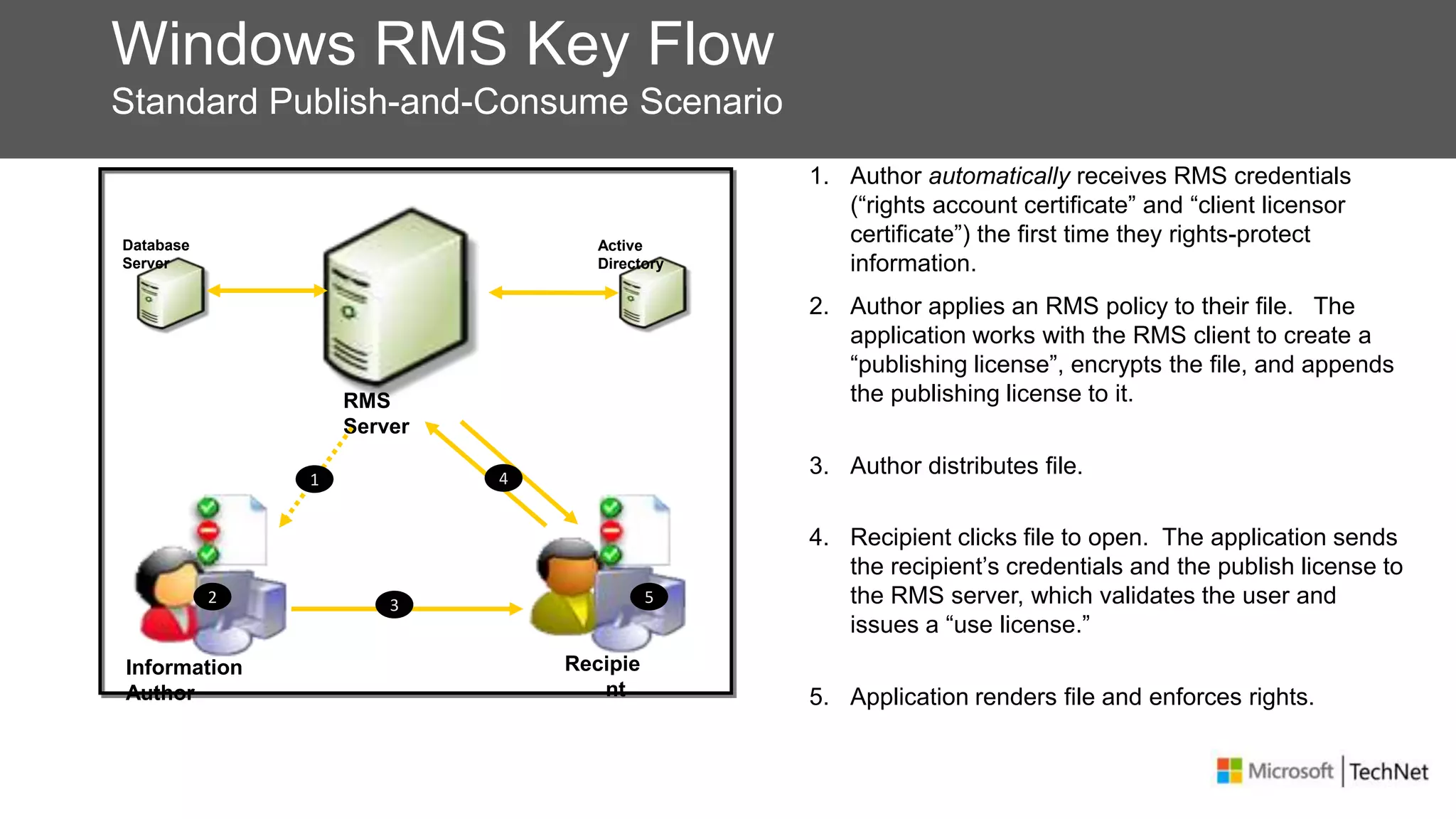
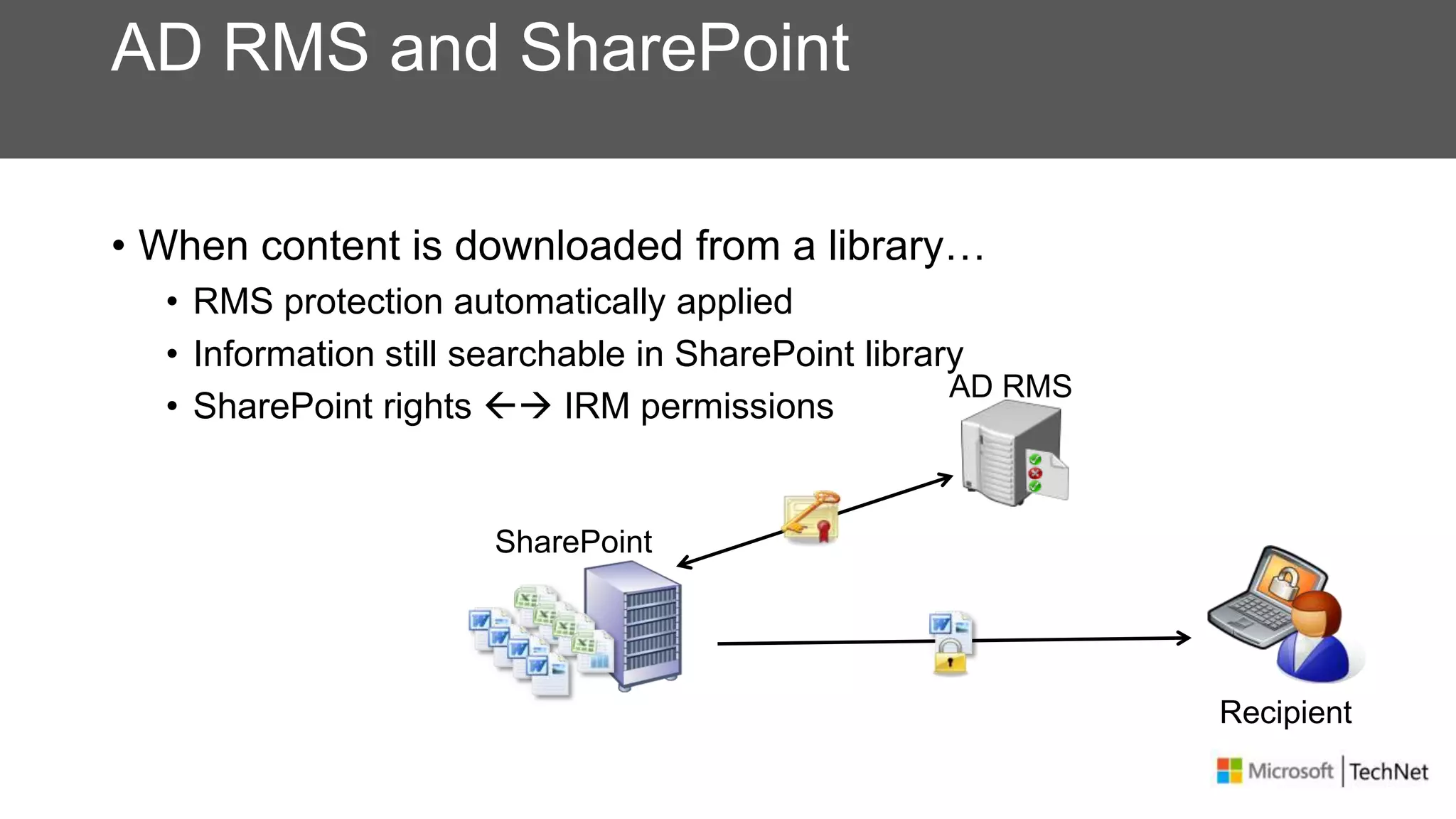
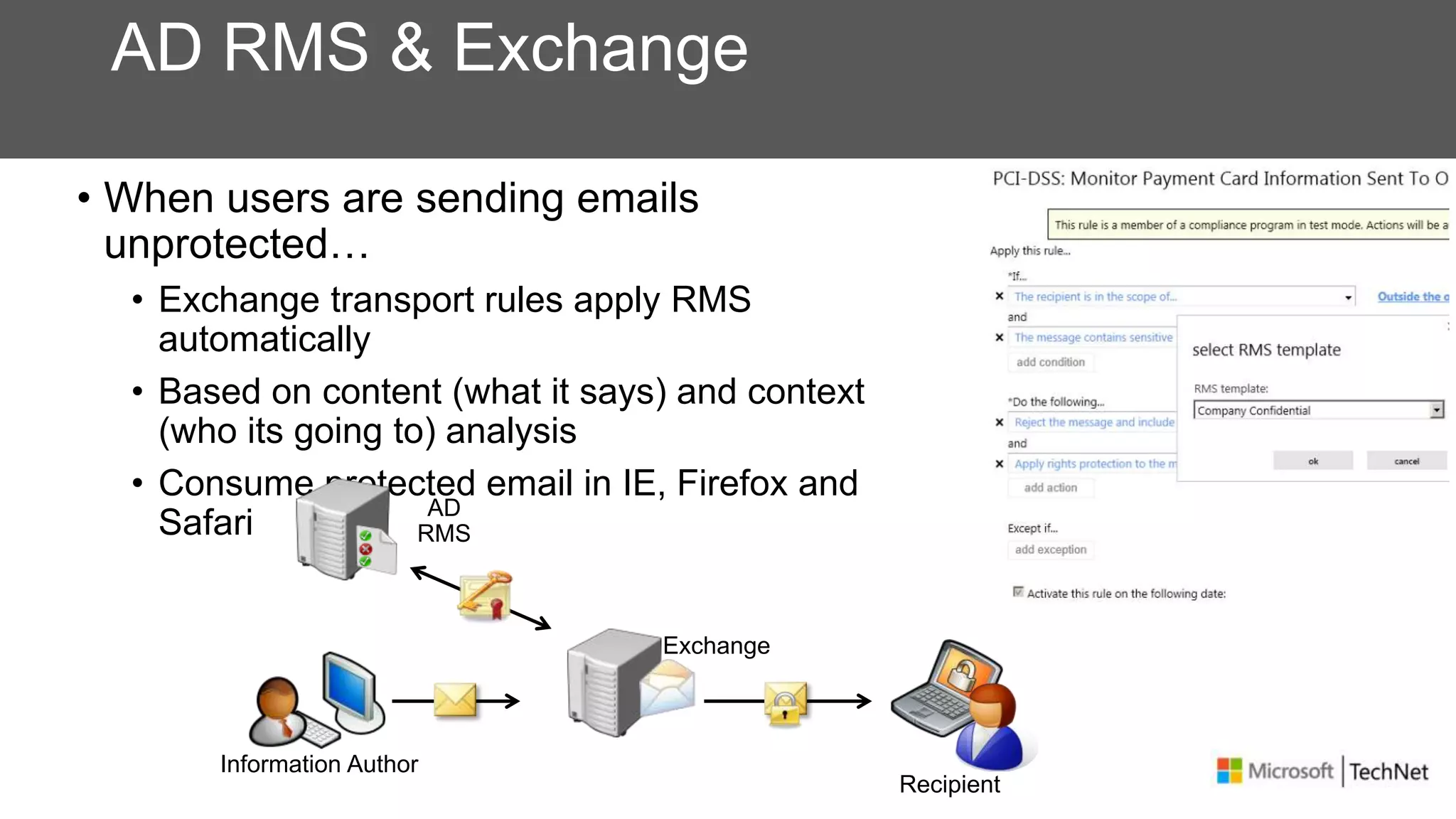
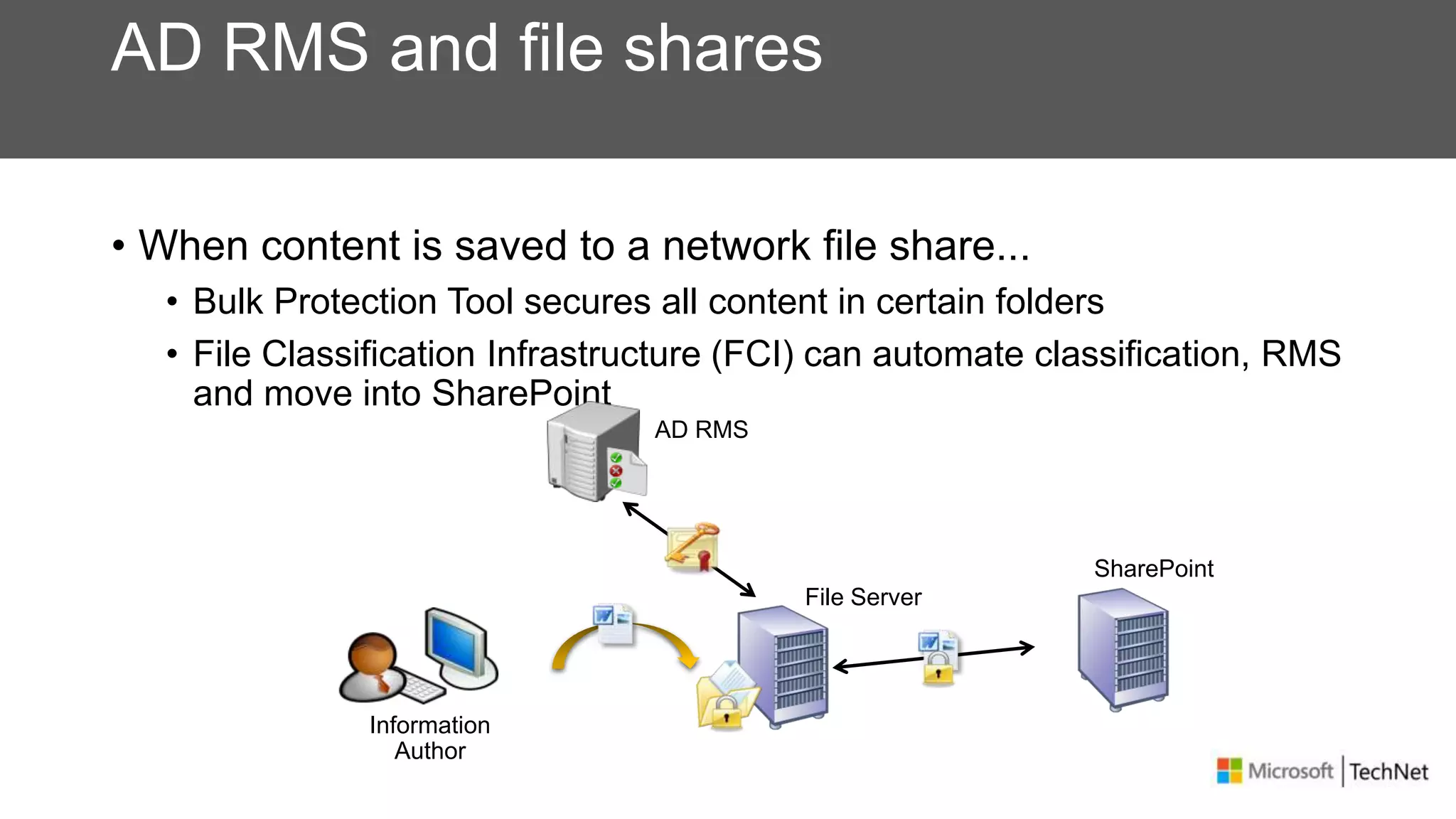
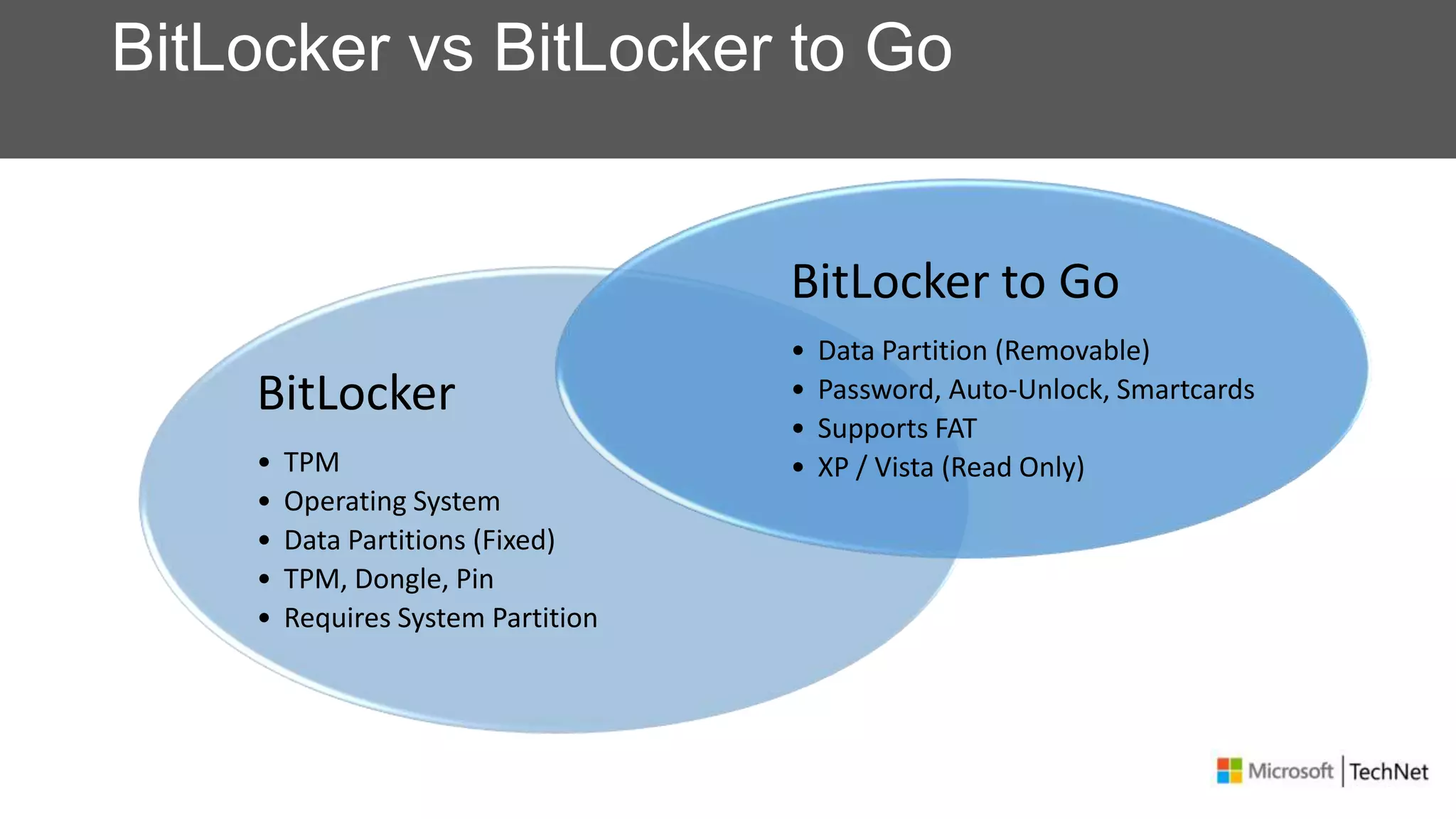
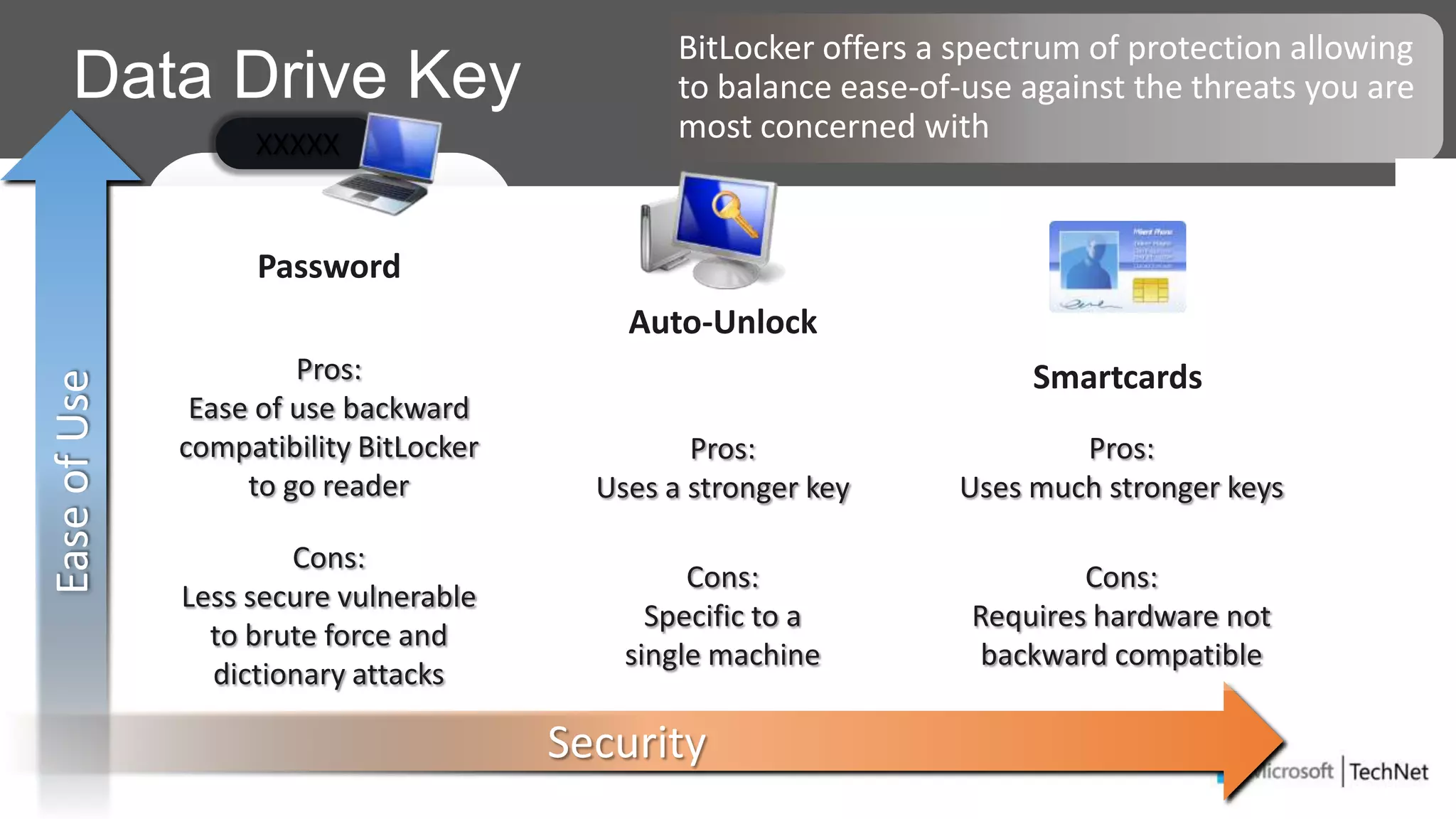
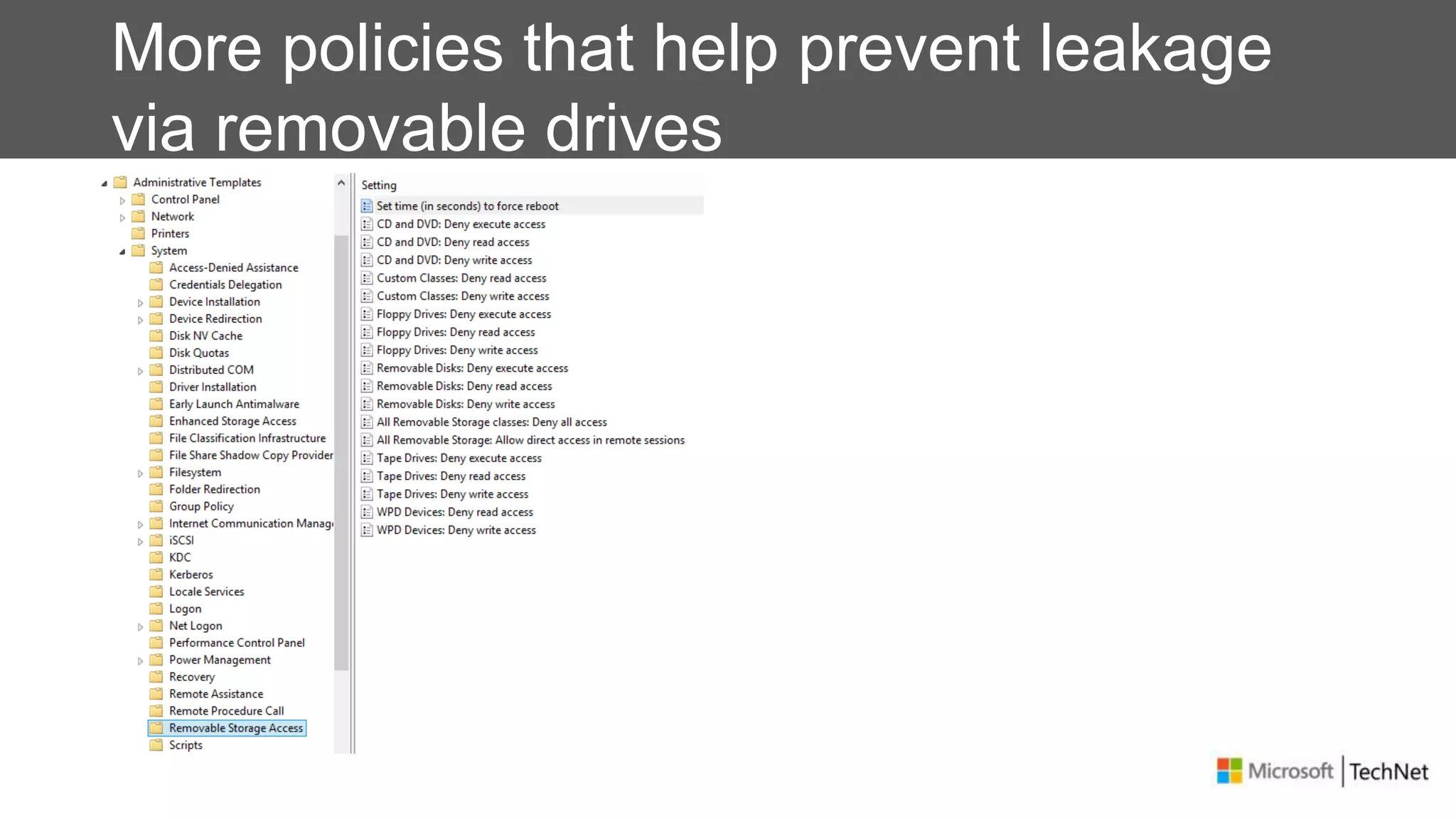
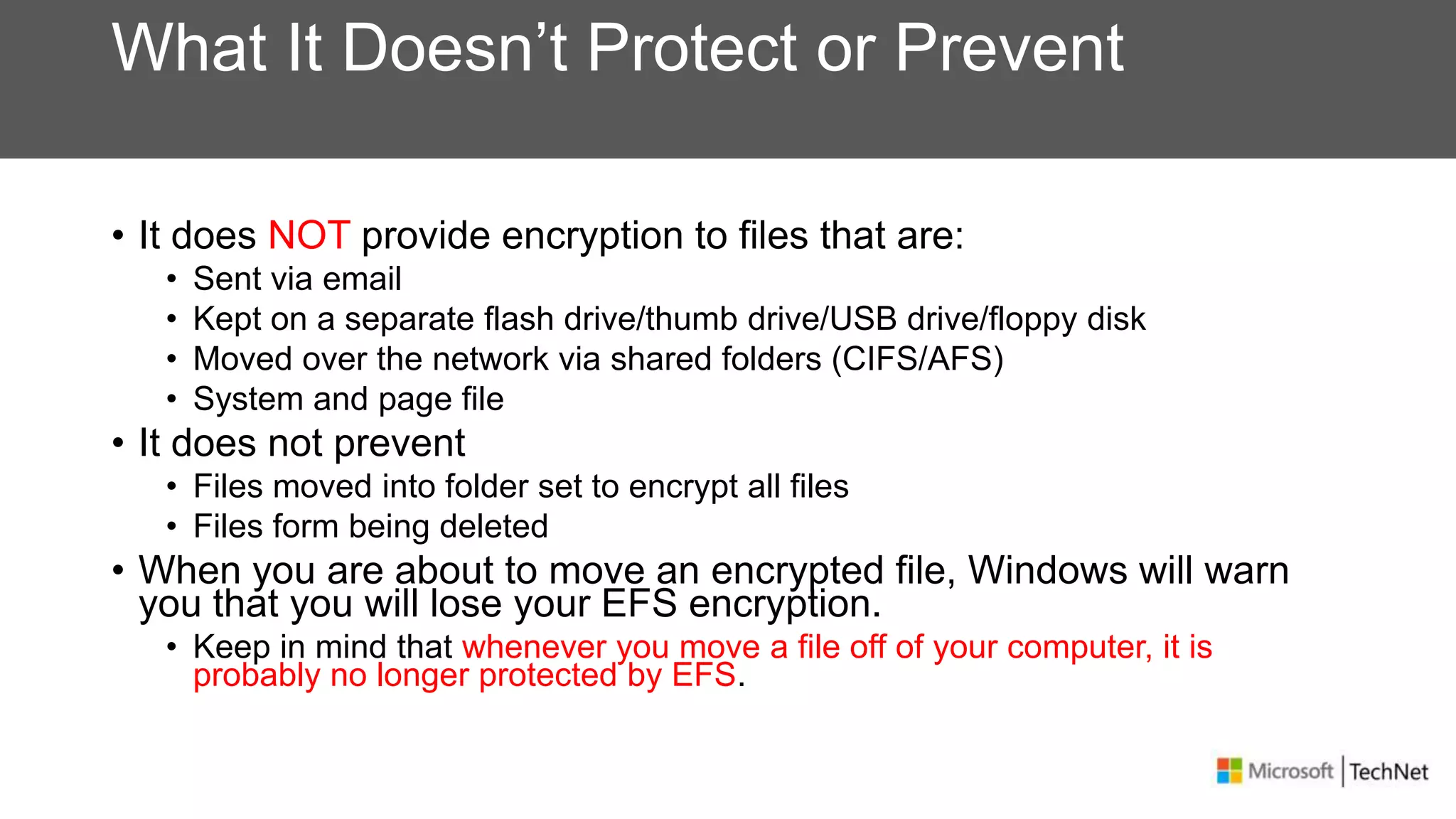
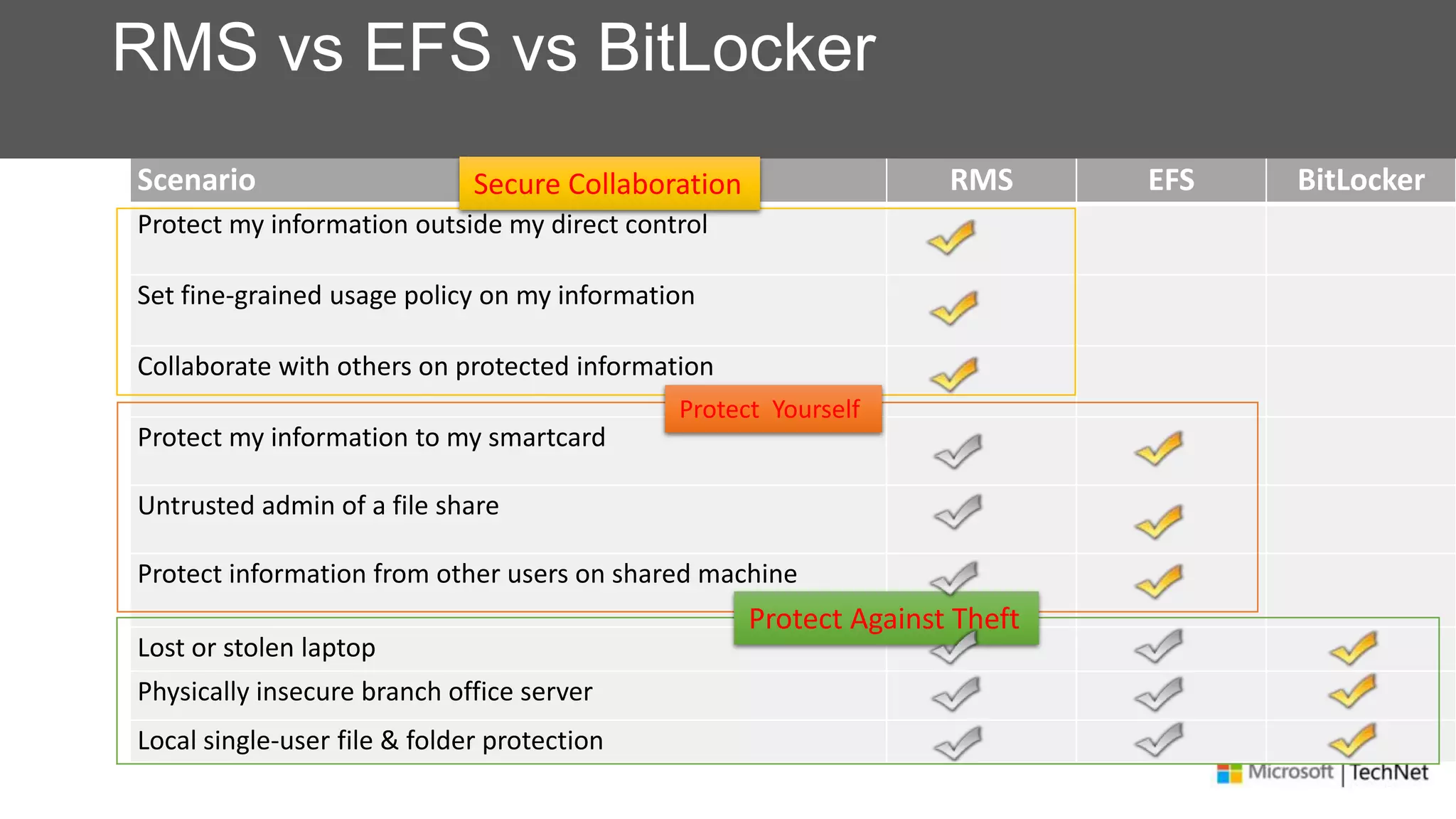
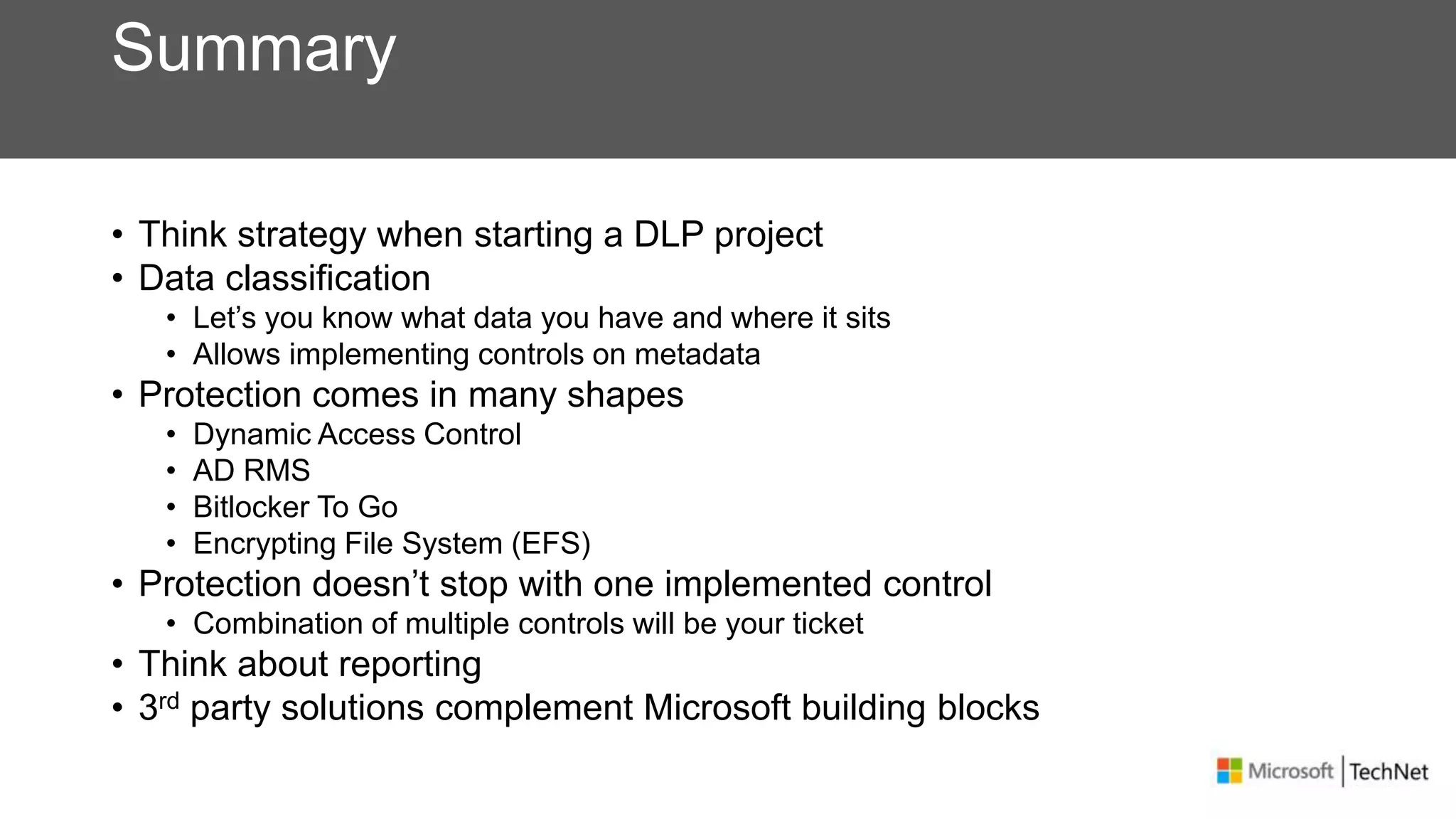
RMS, EFS, and BitLocker are Microsoft data protection technologies that can help prevent data leakage. RMS allows users to apply usage policies to files and encrypts files to control access. EFS transparently encrypts files stored locally on a computer. BitLocker encrypts fixed and removable drives to protect data at rest. The technologies provide different levels of protection and have varying capabilities for controlling access to data inside and outside an organization.