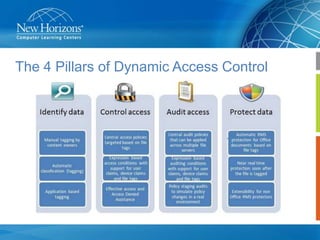
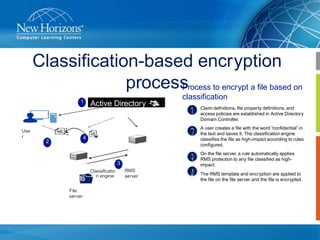
This document summarizes a presentation on Dynamic Access Control in Windows Server 2012. It introduces Dynamic Access Control and its four pillars: data classification, expression-based auditing, expression-based access conditions, and encryption. It provides examples of how data classification can automatically classify documents based on their contents. Expression-based access control allows flexible access control lists based on document classification and user attributes. Dynamic Access Control helps address challenges around data compliance, leakage, and regulatory issues by automating access control and encryption based on how data is classified.