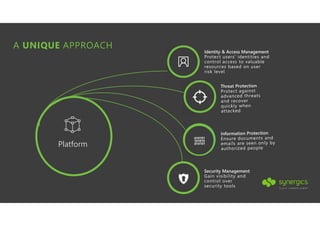
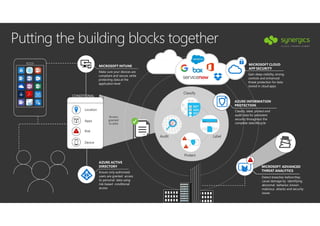
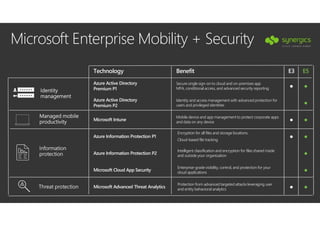
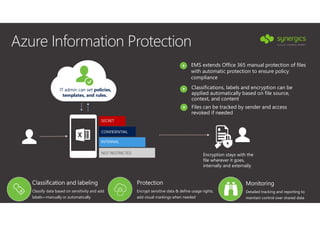
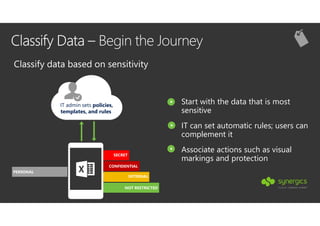
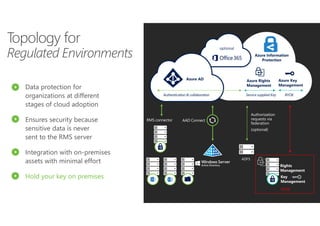
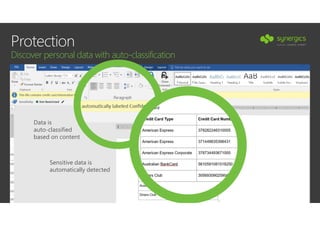
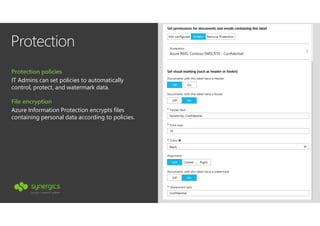
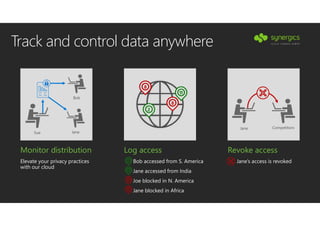
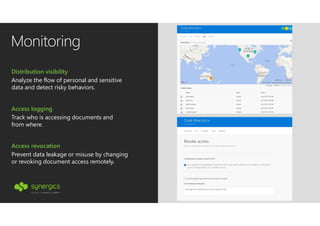
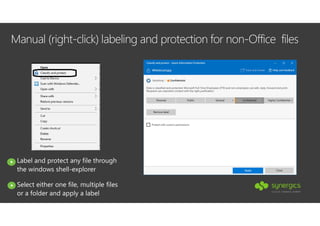
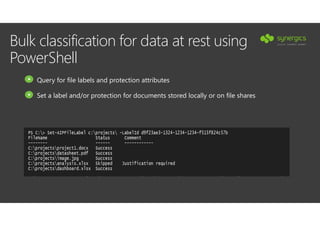
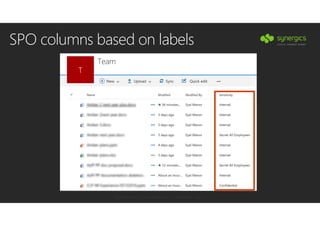
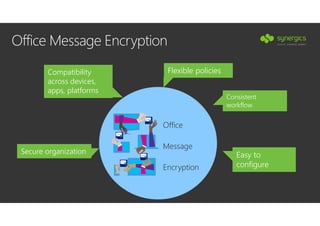
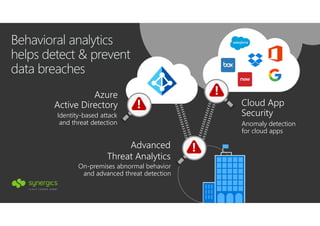
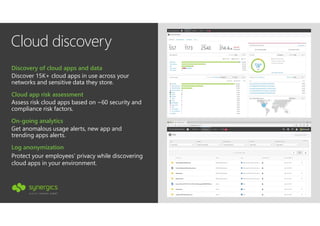
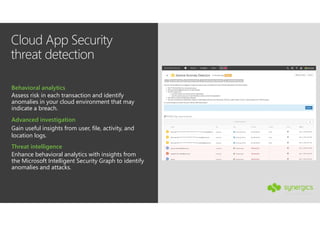
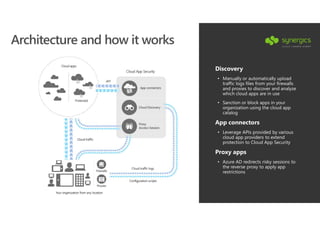
This document outlines Microsoft's security framework for Azure Information Protection, focusing on enabling productivity without compromising security. It details strategies for identity and access management, security management, and various tools like Microsoft Intune, Azure Active Directory, and Microsoft Cloud App Security for protecting sensitive data. Additionally, it covers the classification, labeling, and encryption of data, as well as threat detection and monitoring capabilities to mitigate risks associated with cloud applications.