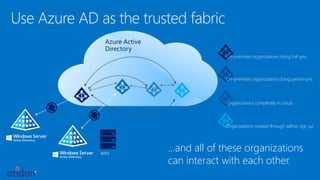
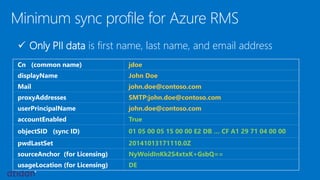
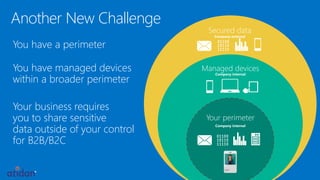
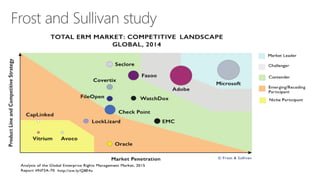
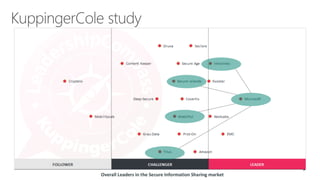
The document discusses the importance of data protection through rights management and compliance, highlighting the need for organizations to secure sensitive information against leaks and cyber attacks. It presents Azure Rights Management as a solution that enables encrypted data sharing among various partners while maintaining user control and security. The document emphasizes the necessity for organizations to take immediate action in protecting their information through both small and scalable measures.









![aEZQAR]ibr{qU
@M]BXNoHp9nMD
AtnBfrfC;jx+T
g@XL2,Jzu
()&(*7812(*:
Use Rights +
Rights management 101
Secret cola formula
Water
Sugar
Brown #16
Protect Unprotect
Usage rights and symmetric
key stored in file as ‘license’
Each file is protected by
a unique AES symmetric
License protected
by customer-owned
RSA key
Water
Sugar
Brown #16](https://image.slidesharecdn.com/microsoftazurerightsmanagement-presentedbyatidan-151028011804-lva1-app6892/85/Microsoft-Azure-Rights-Management-13-320.jpg)
![Local processing on PCs/devices
Apps protected with
RMS enforce rights
SDK
Apps use the SDK to
communicate with the
RMS service/servers
File content is never sent
to the RMS server/service.
aEZQAR]ibr{q
U@M]BXNoHp9n
MDAtnBfrfC;j
x+Tg@XL2,Jzu
()&(*7812(*:
Use Rights
+
Use Rights
+
Azure RMS
never sees the
file content, only
the license.](https://image.slidesharecdn.com/microsoftazurerightsmanagement-presentedbyatidan-151028011804-lva1-app6892/85/Microsoft-Azure-Rights-Management-14-320.jpg)