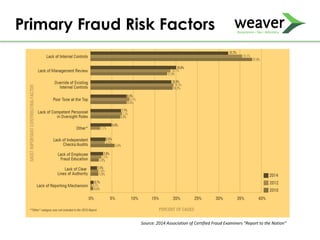
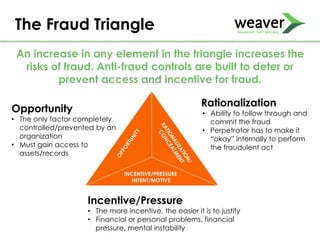
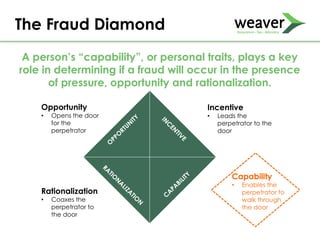
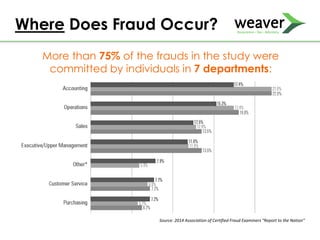
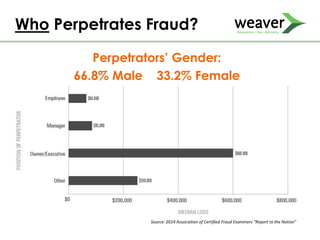
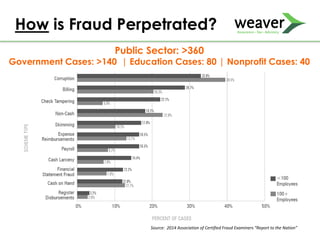
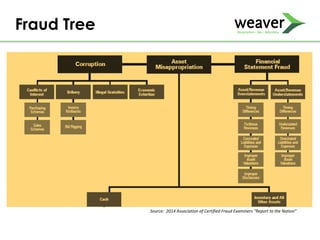
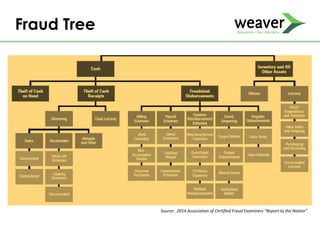
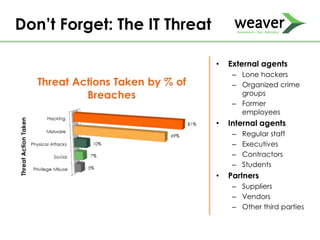
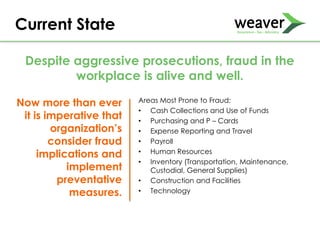
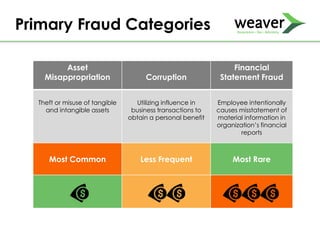
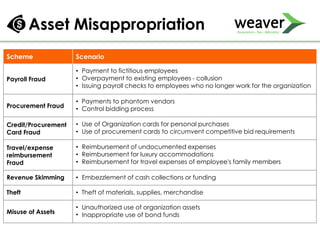
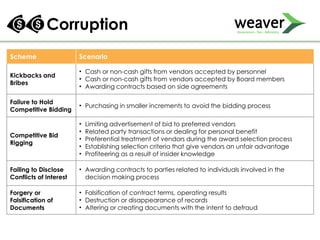
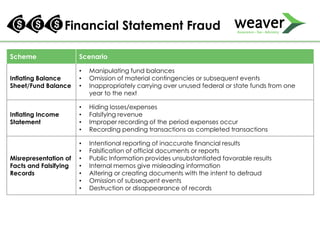
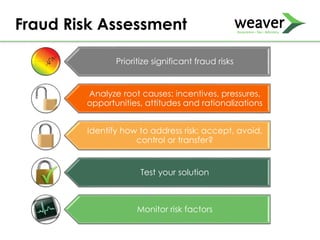
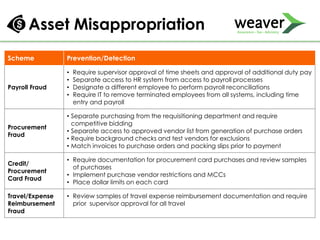
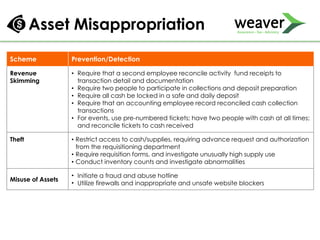
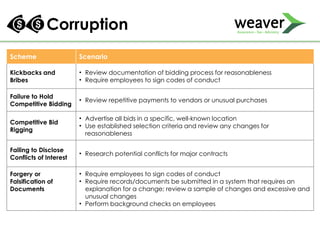
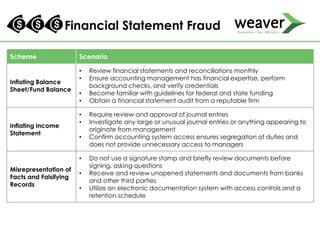
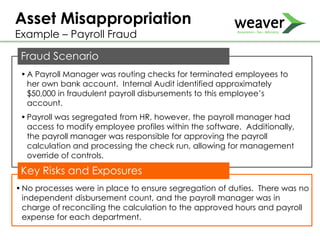
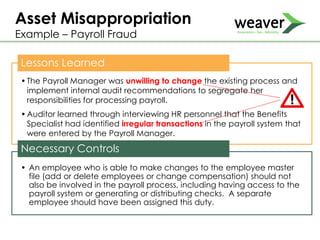
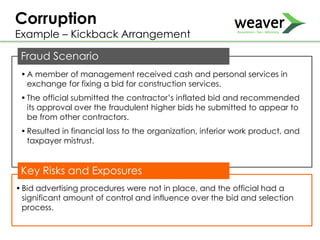
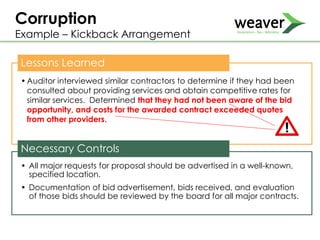
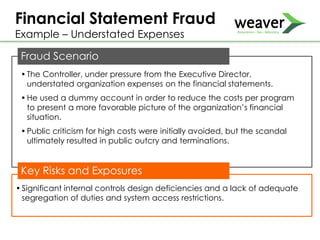
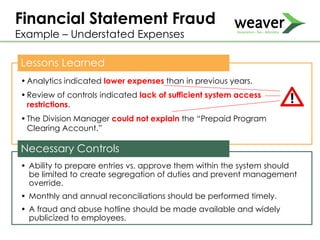
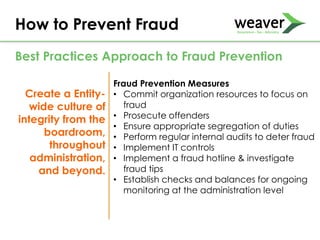
This document discusses fraud risk and prevention. It begins with defining fraud and identifying common fraud schemes such as asset misappropriation, corruption, and financial statement fraud. Examples of each scheme are provided. The document also discusses elements that contribute to fraud occurrence, like opportunity and incentives. Effective fraud prevention controls are then outlined, including segregating duties, competitive bidding processes, and fraud hotlines. The importance of fraud risk assessments and creating an organizational culture of integrity are also emphasized.