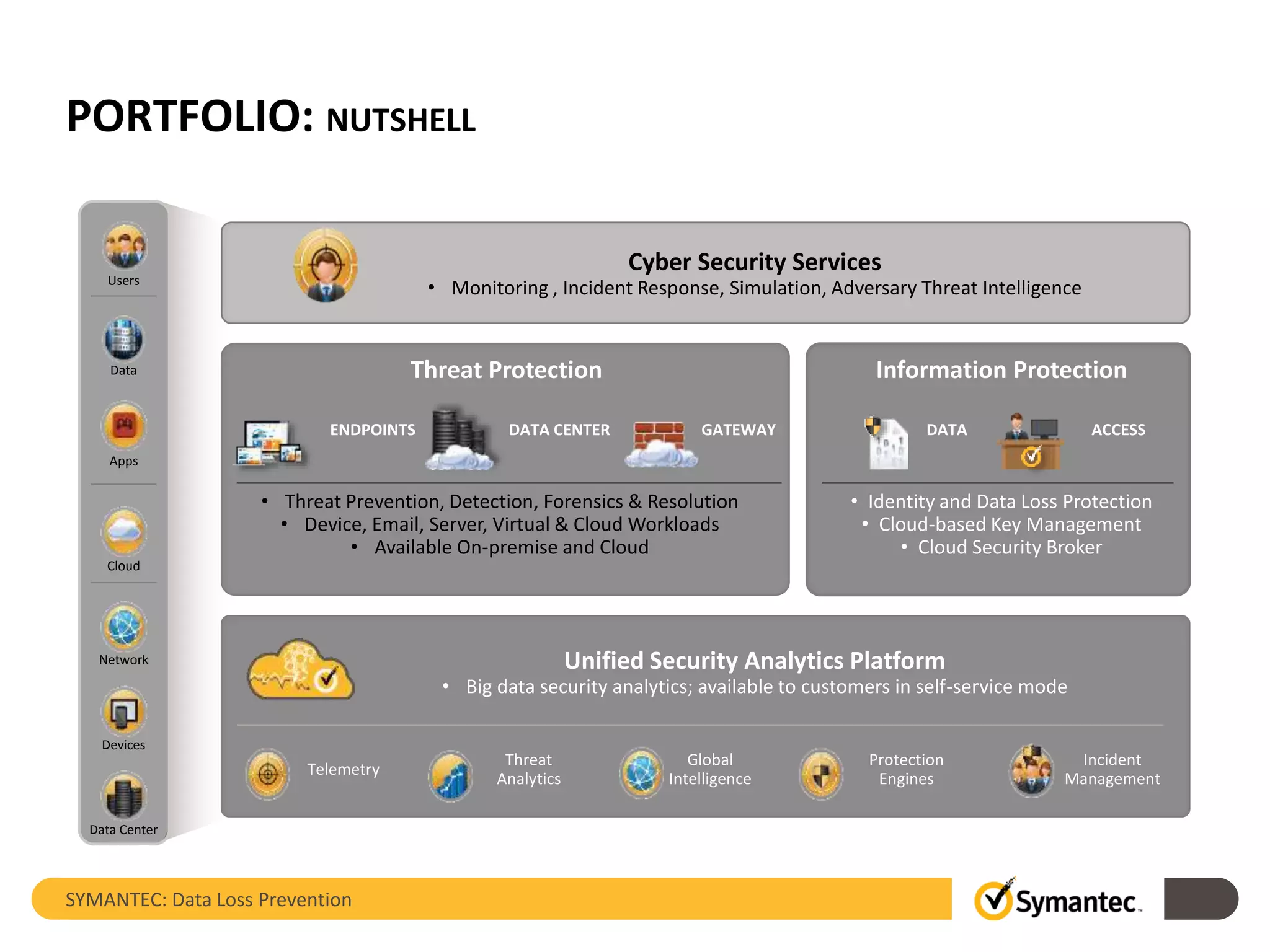
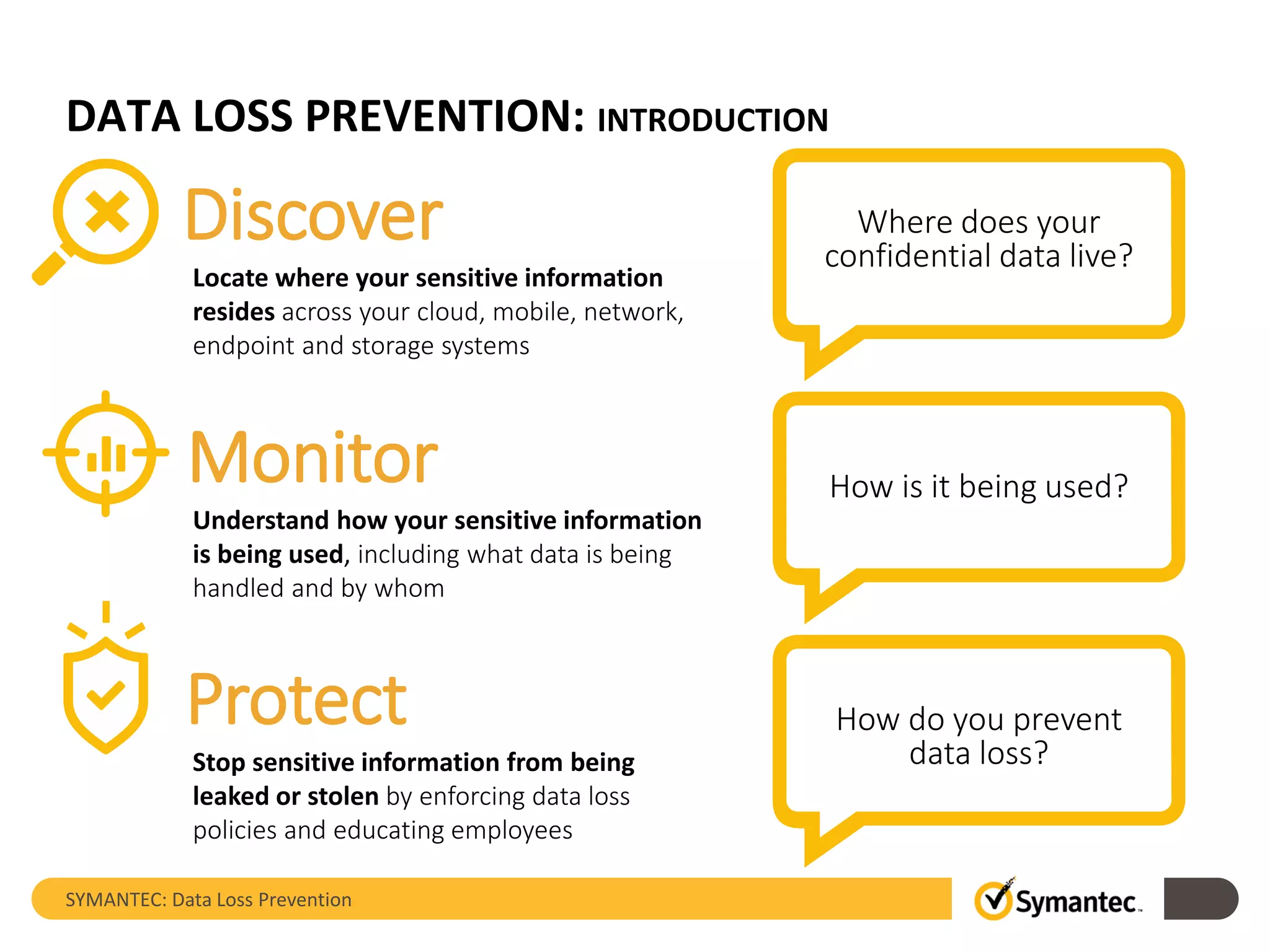
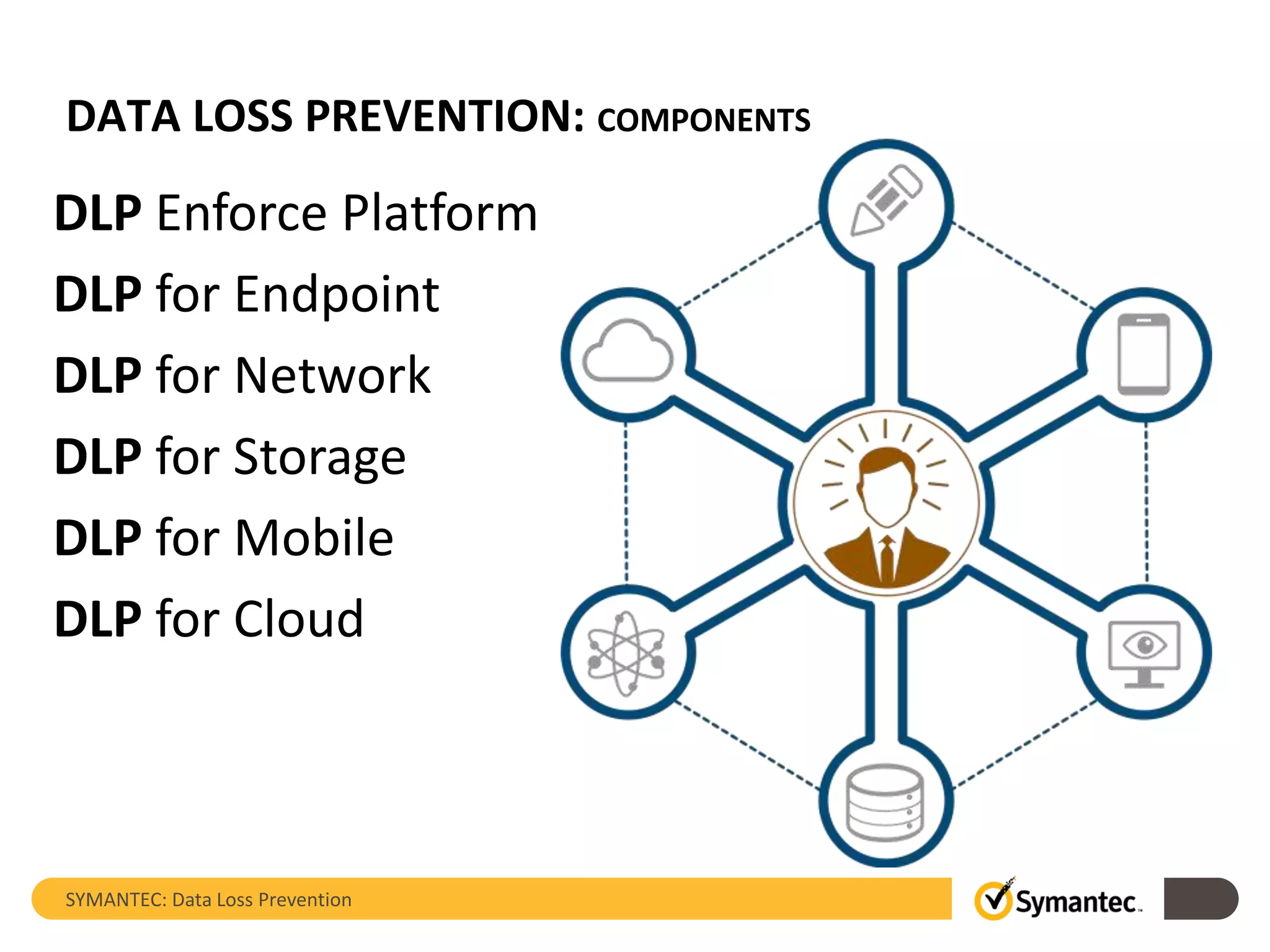
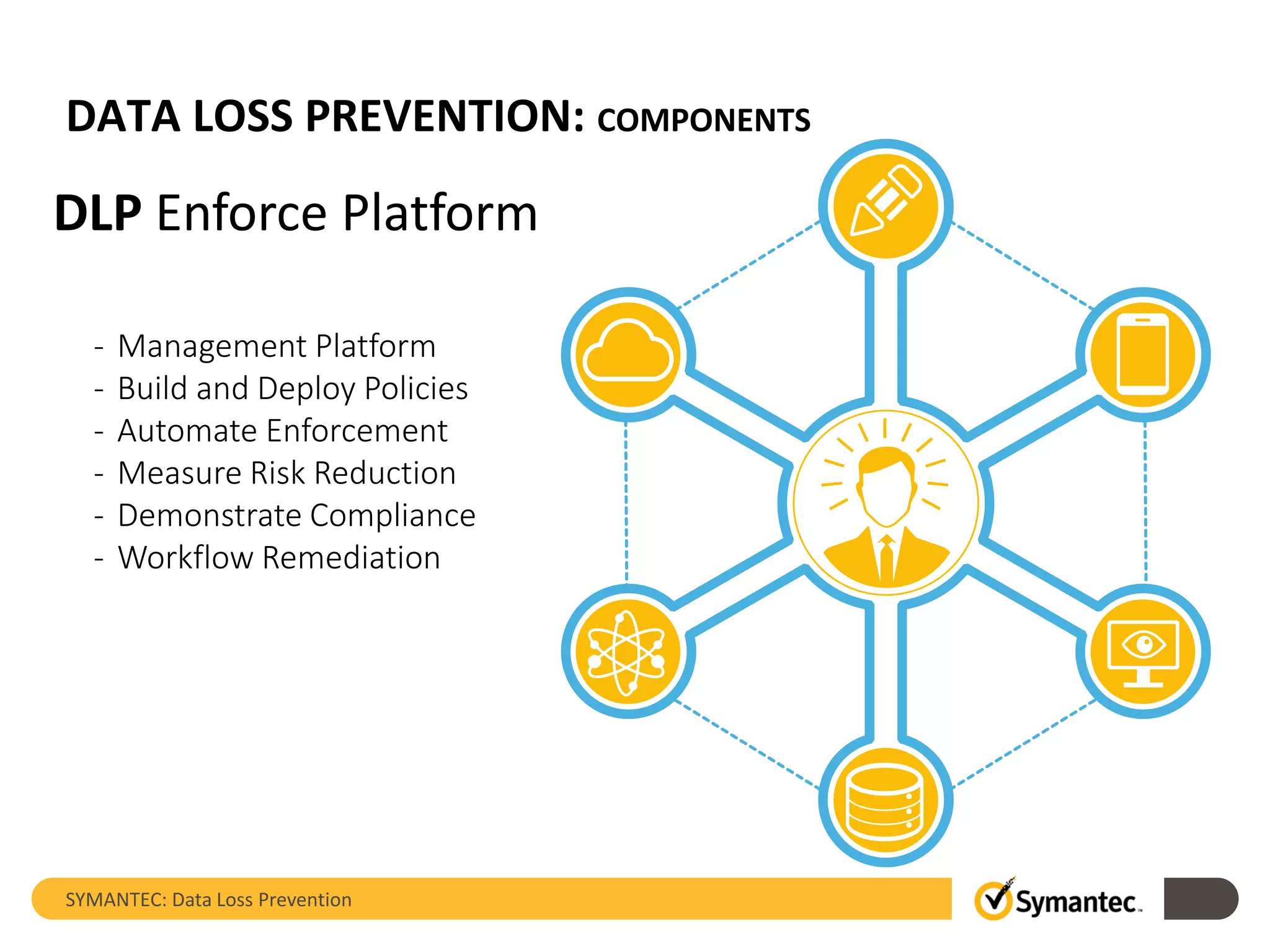
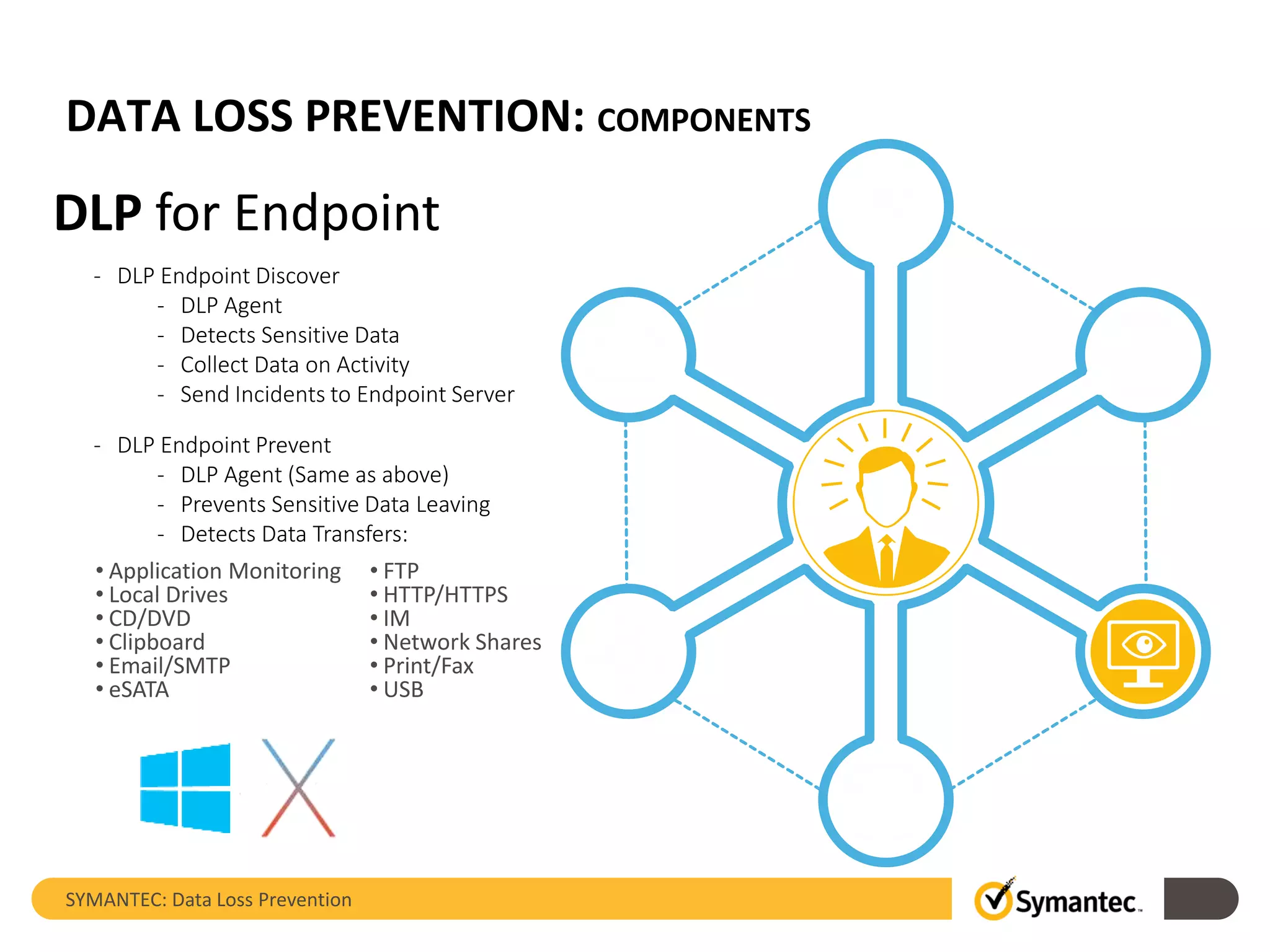
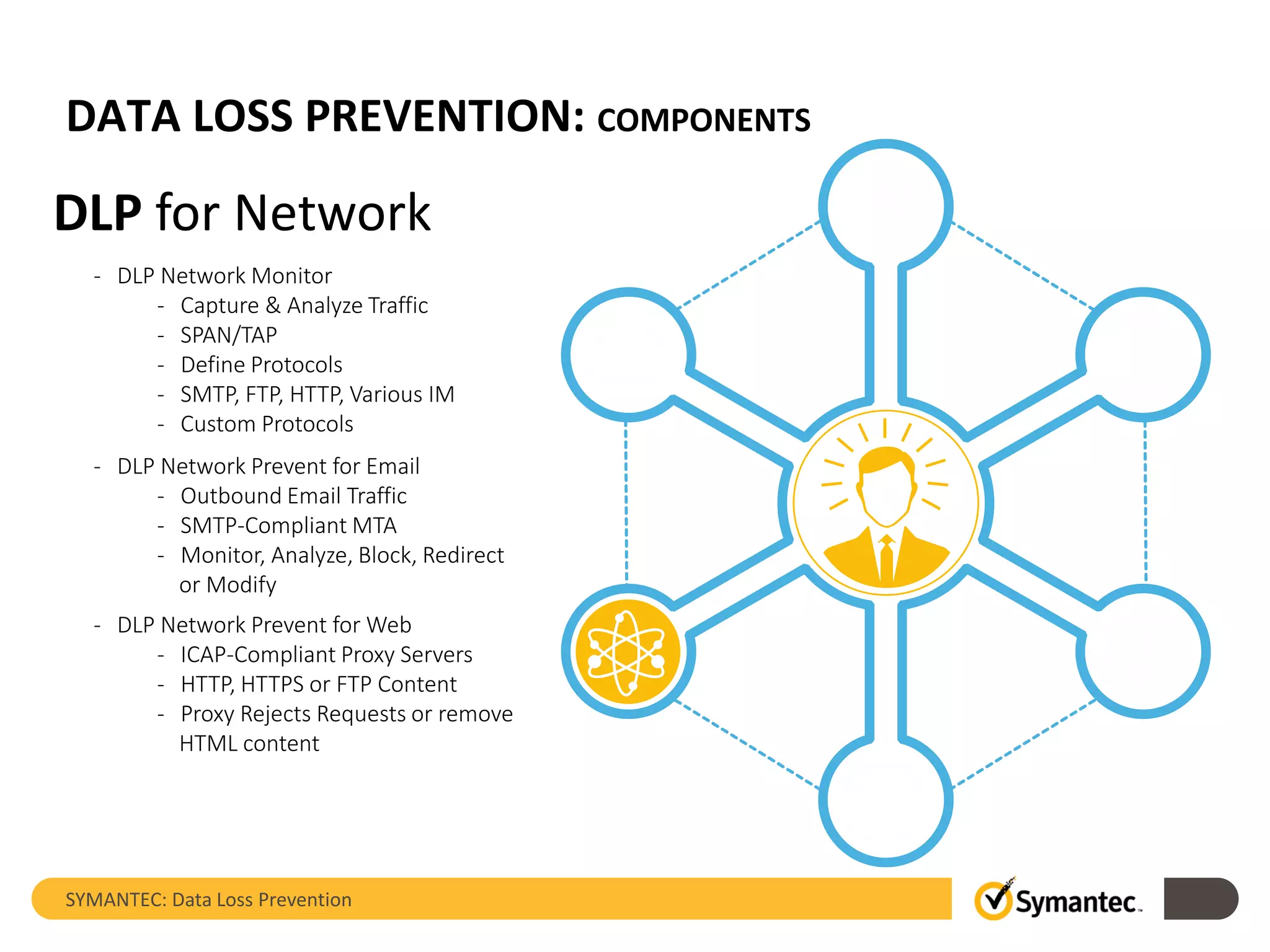
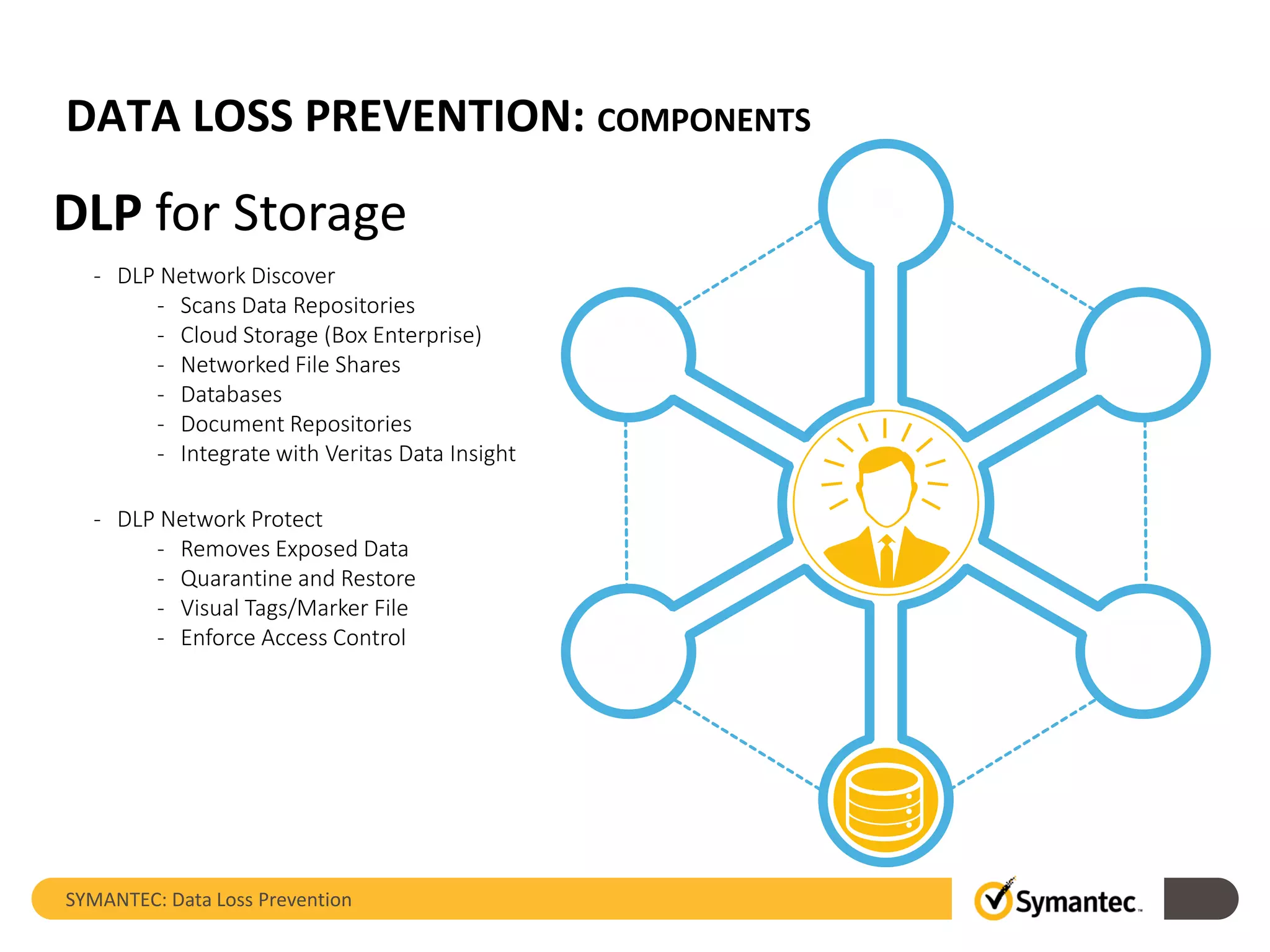
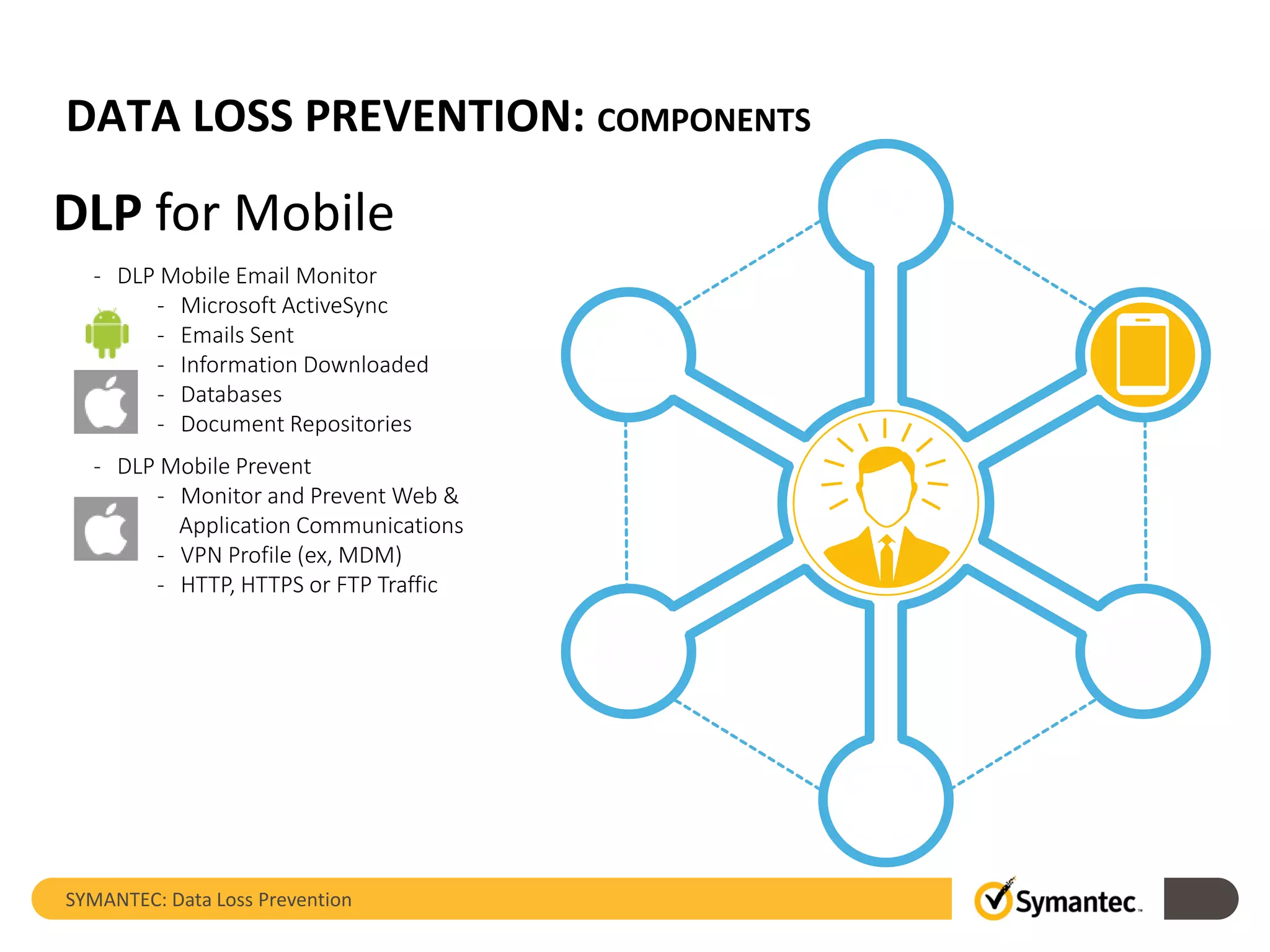
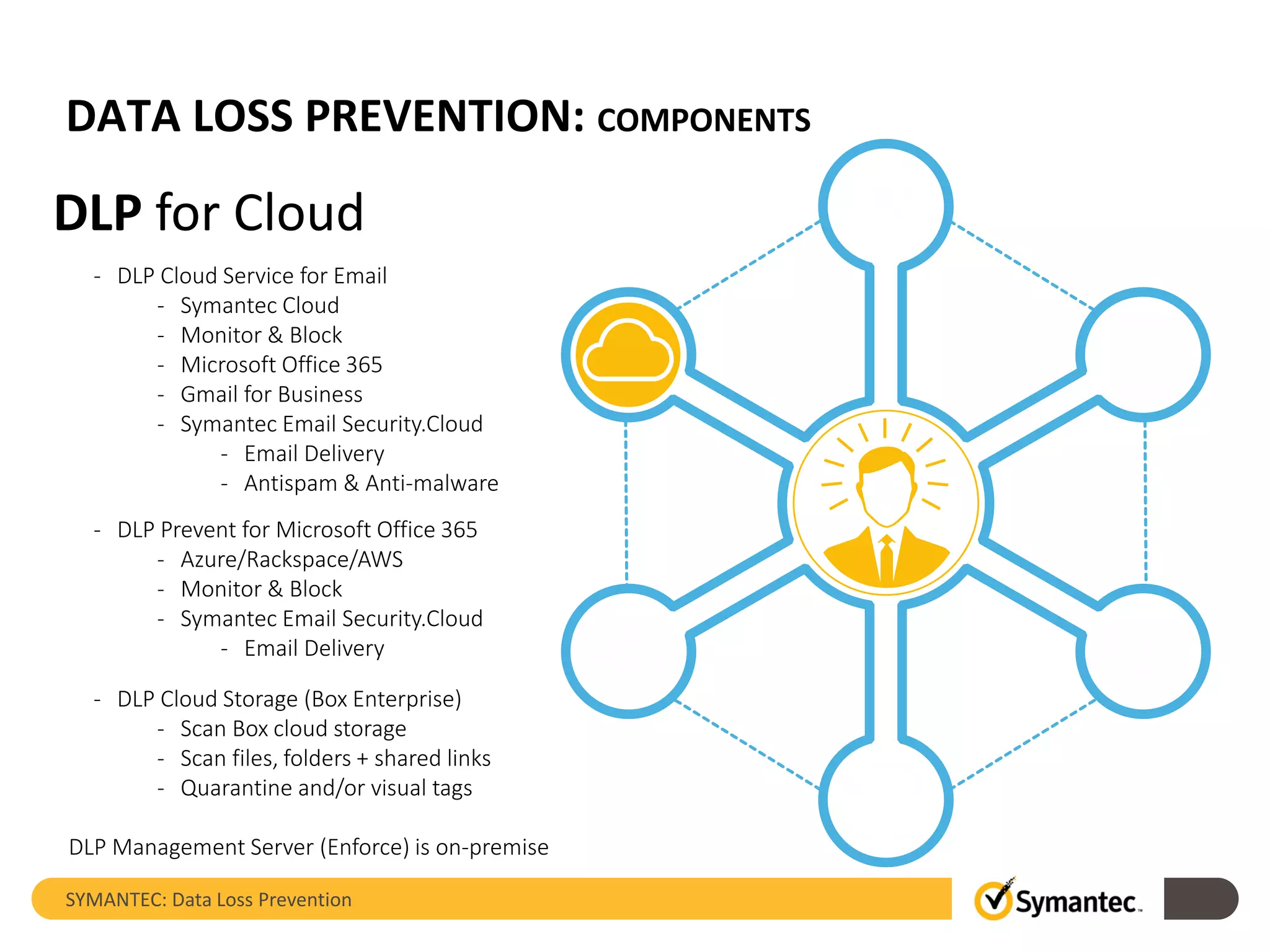
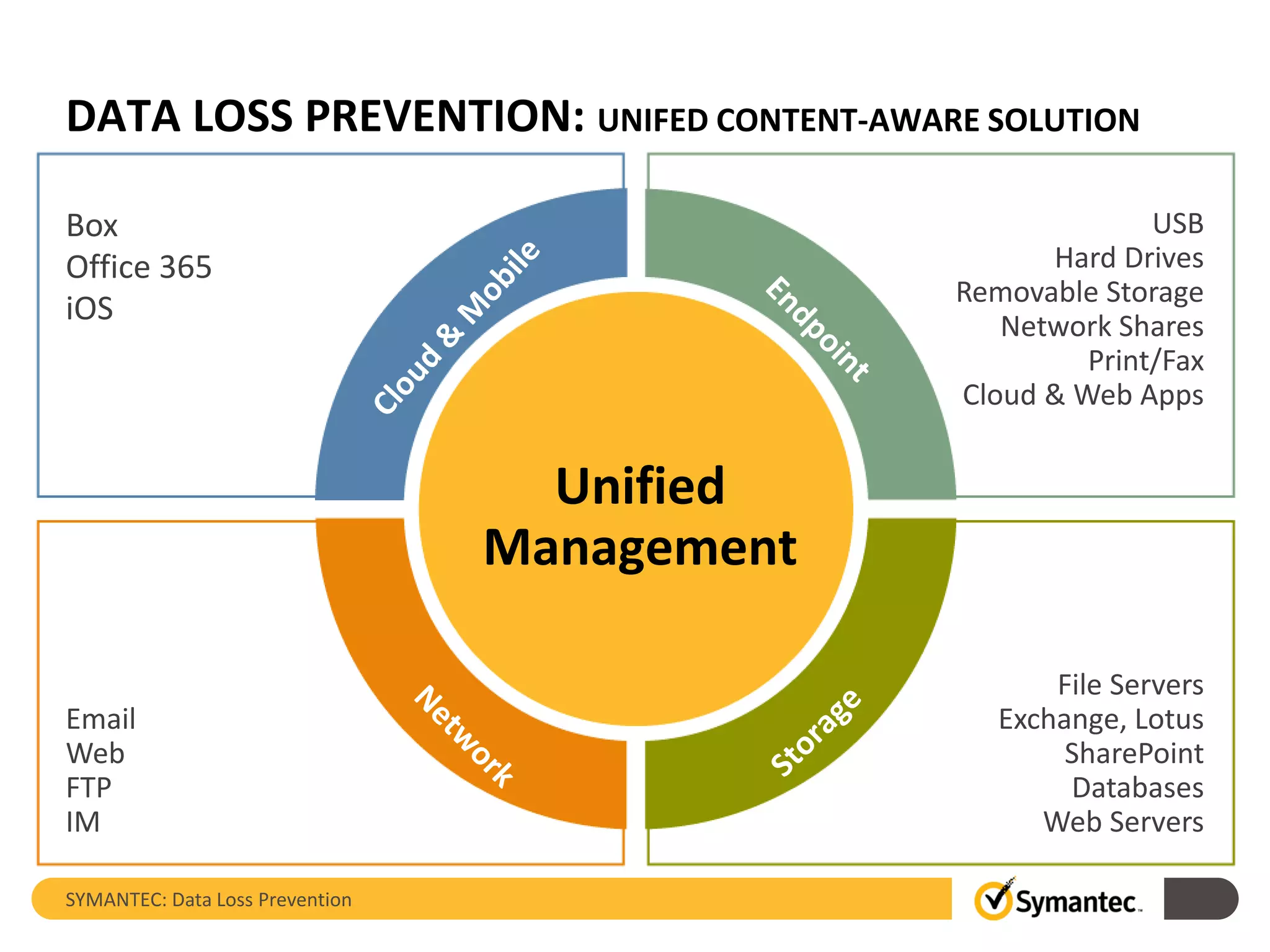
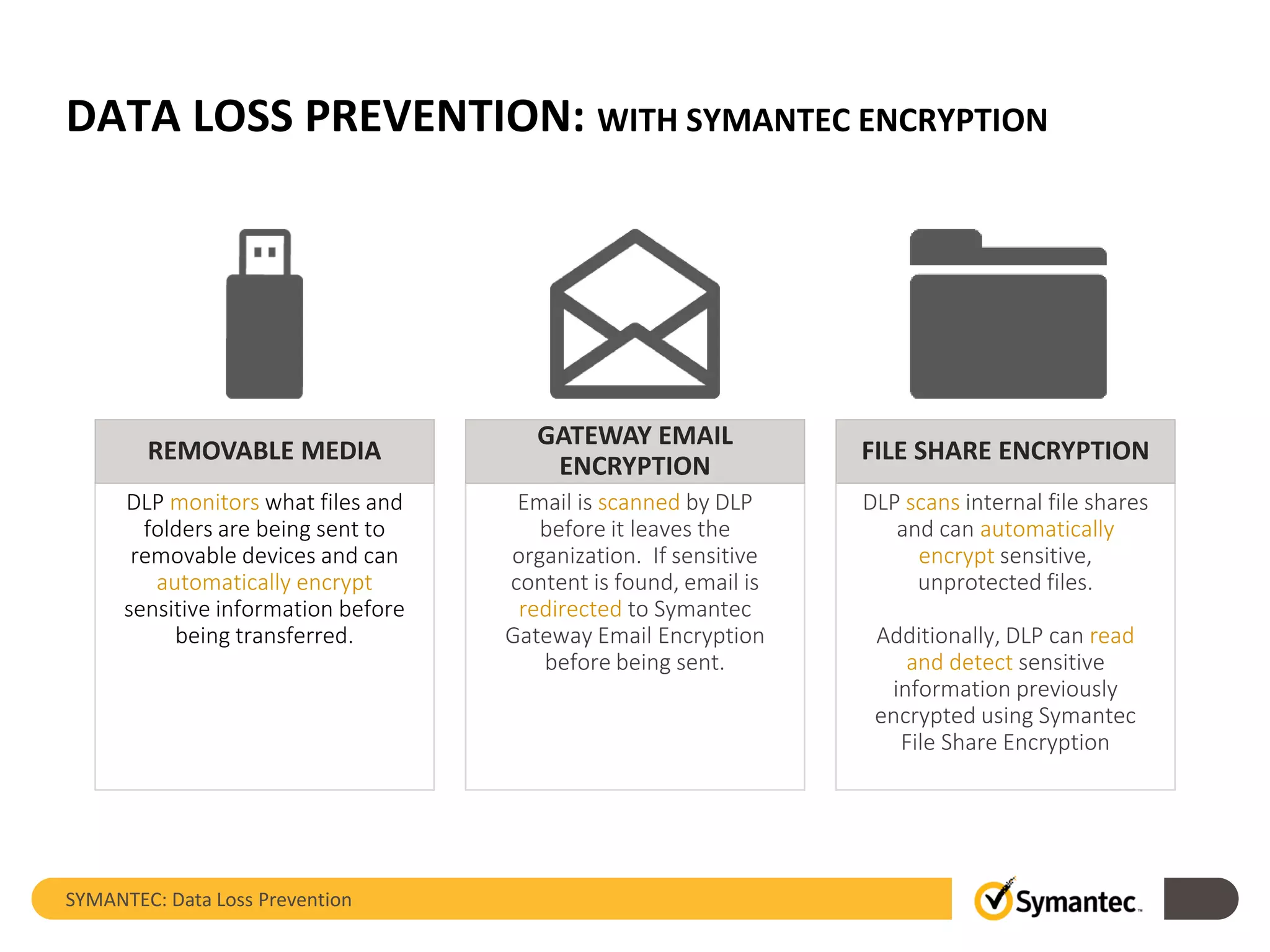
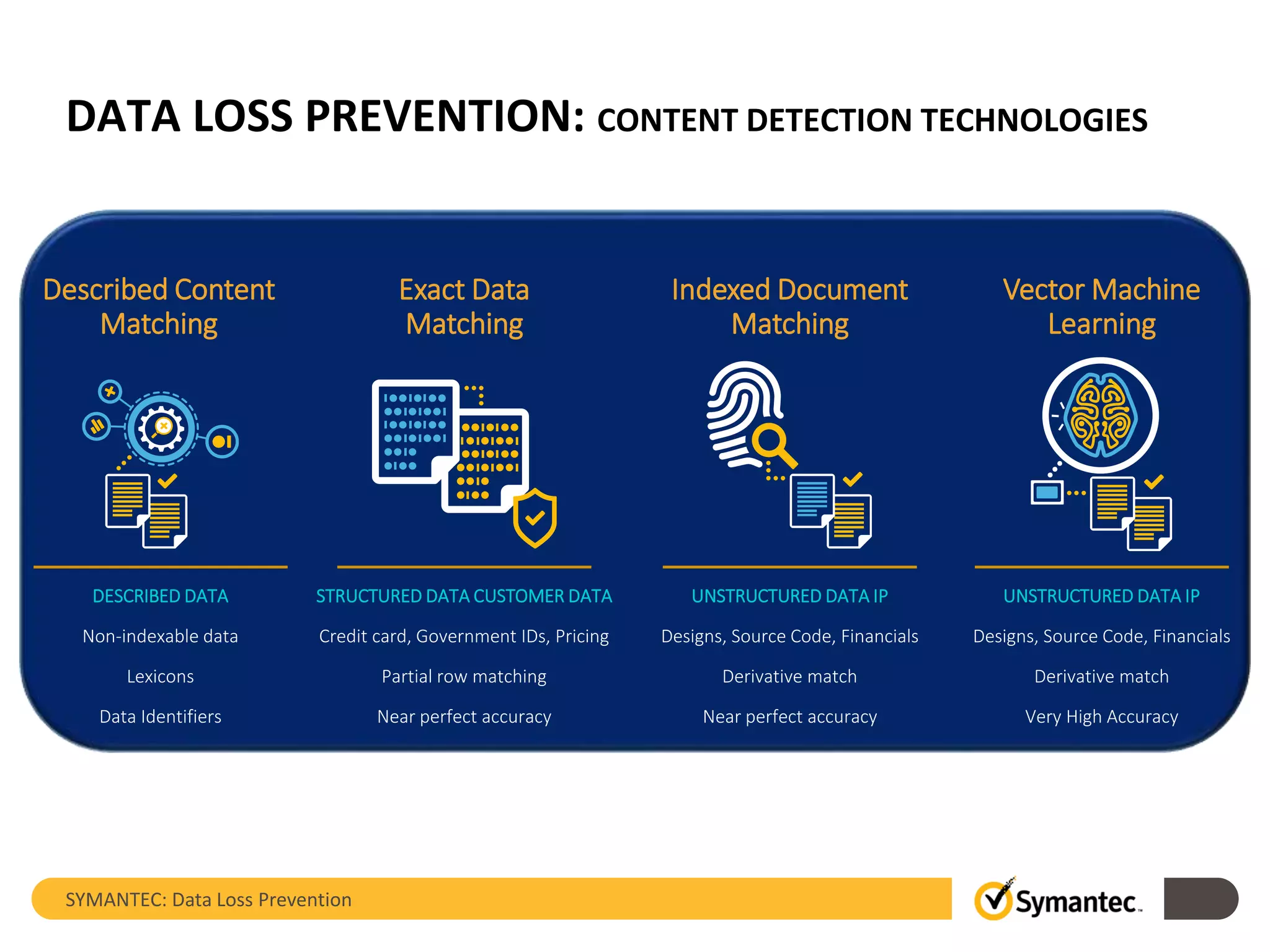
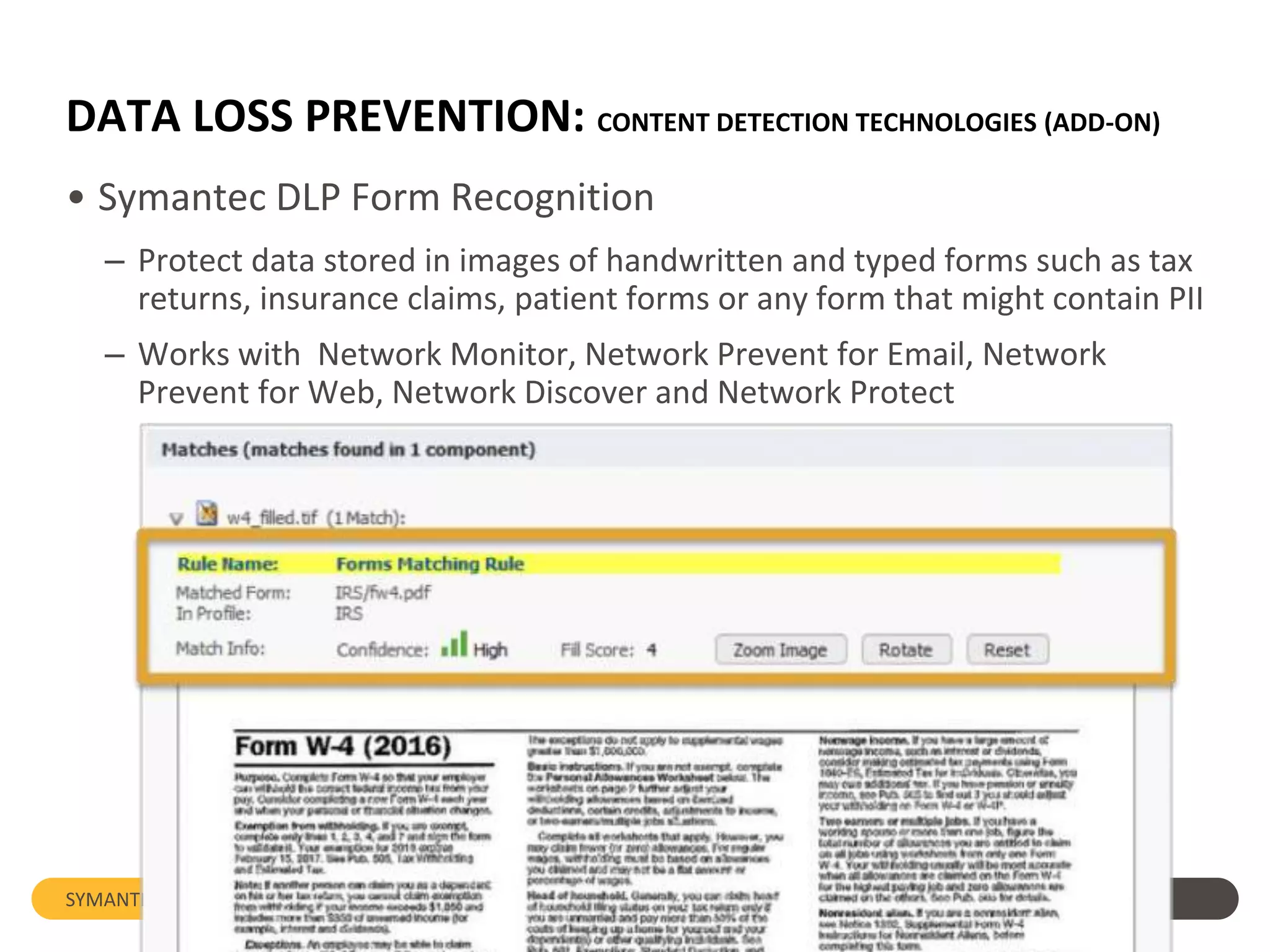
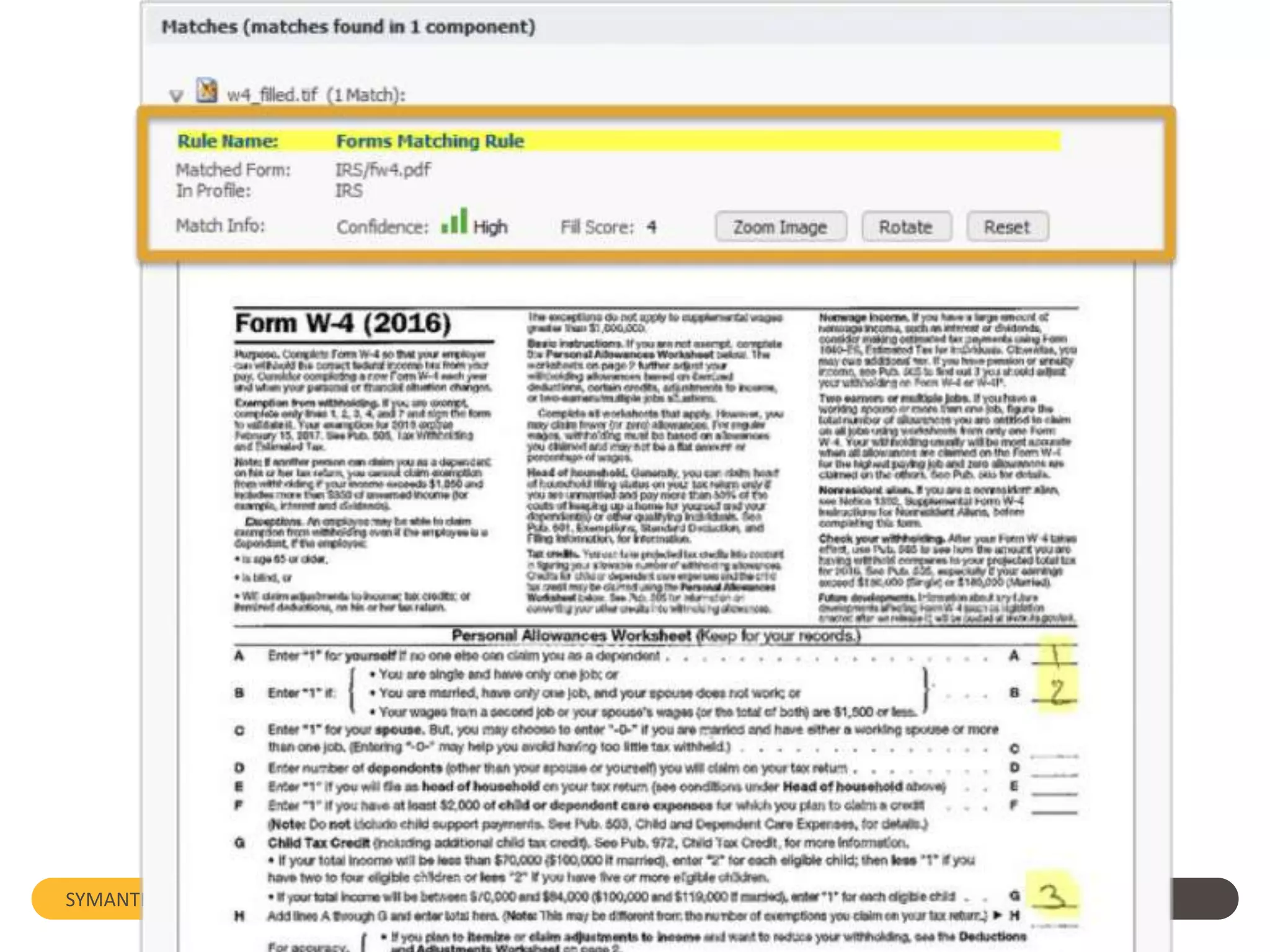
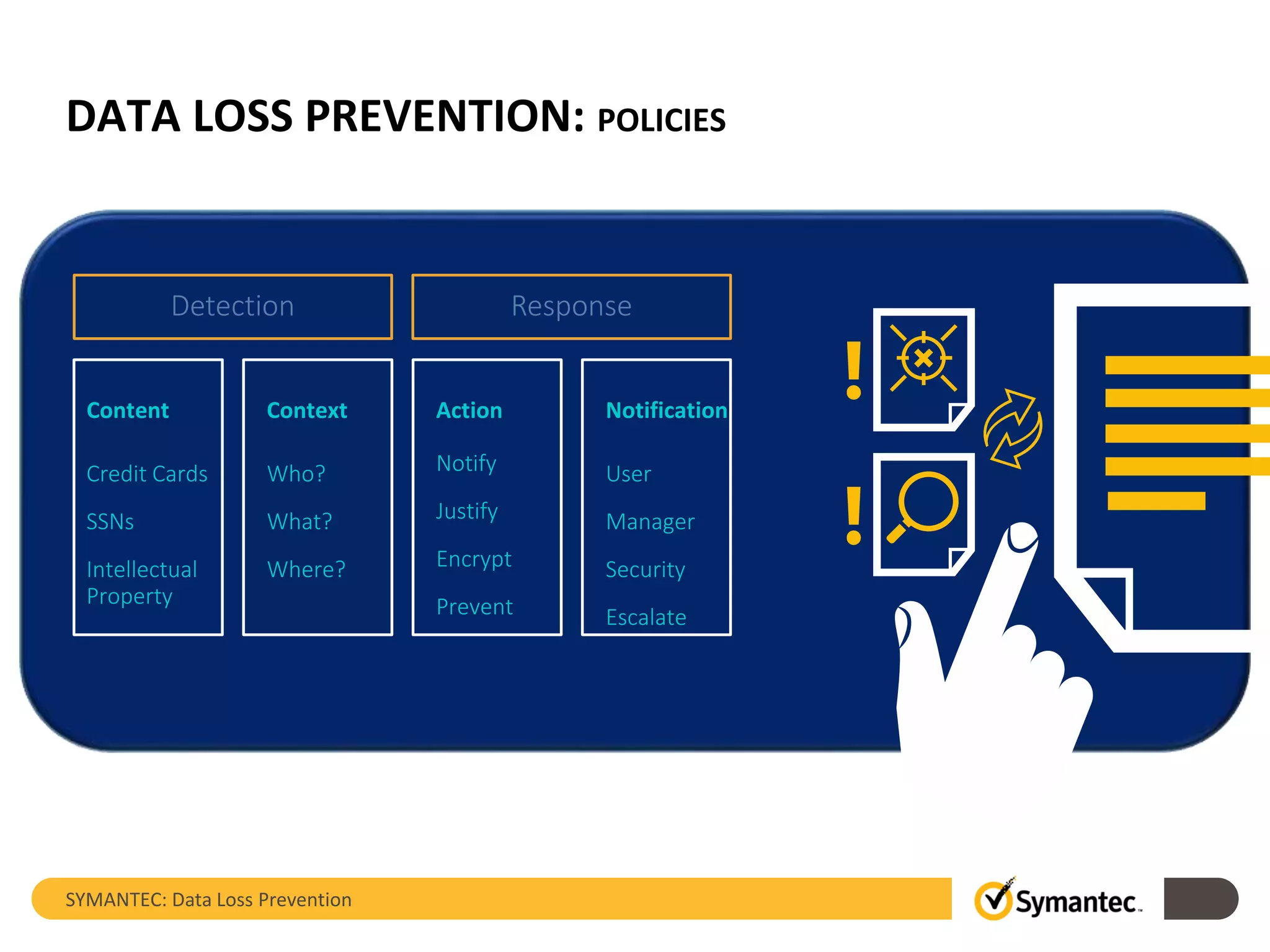
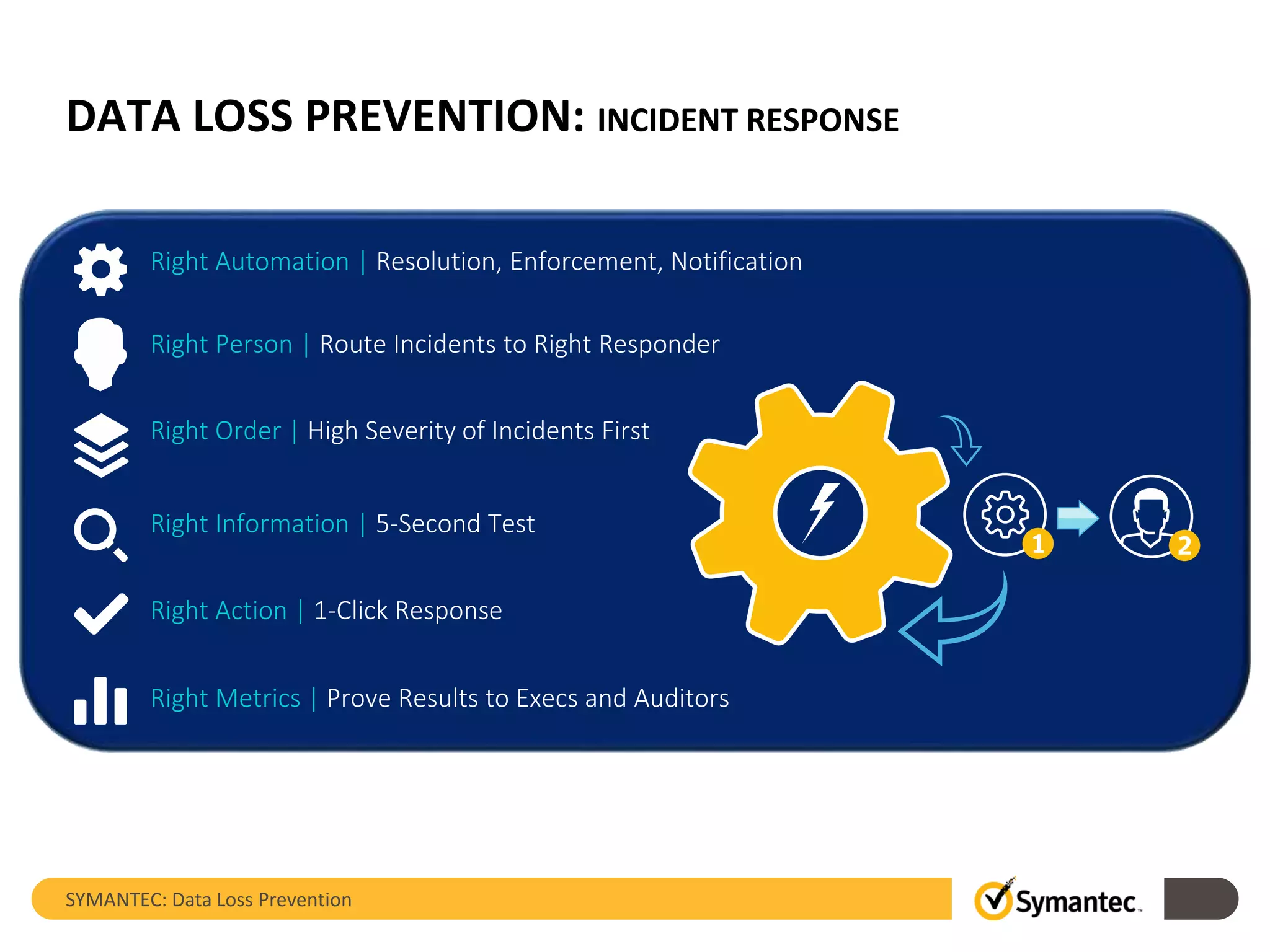
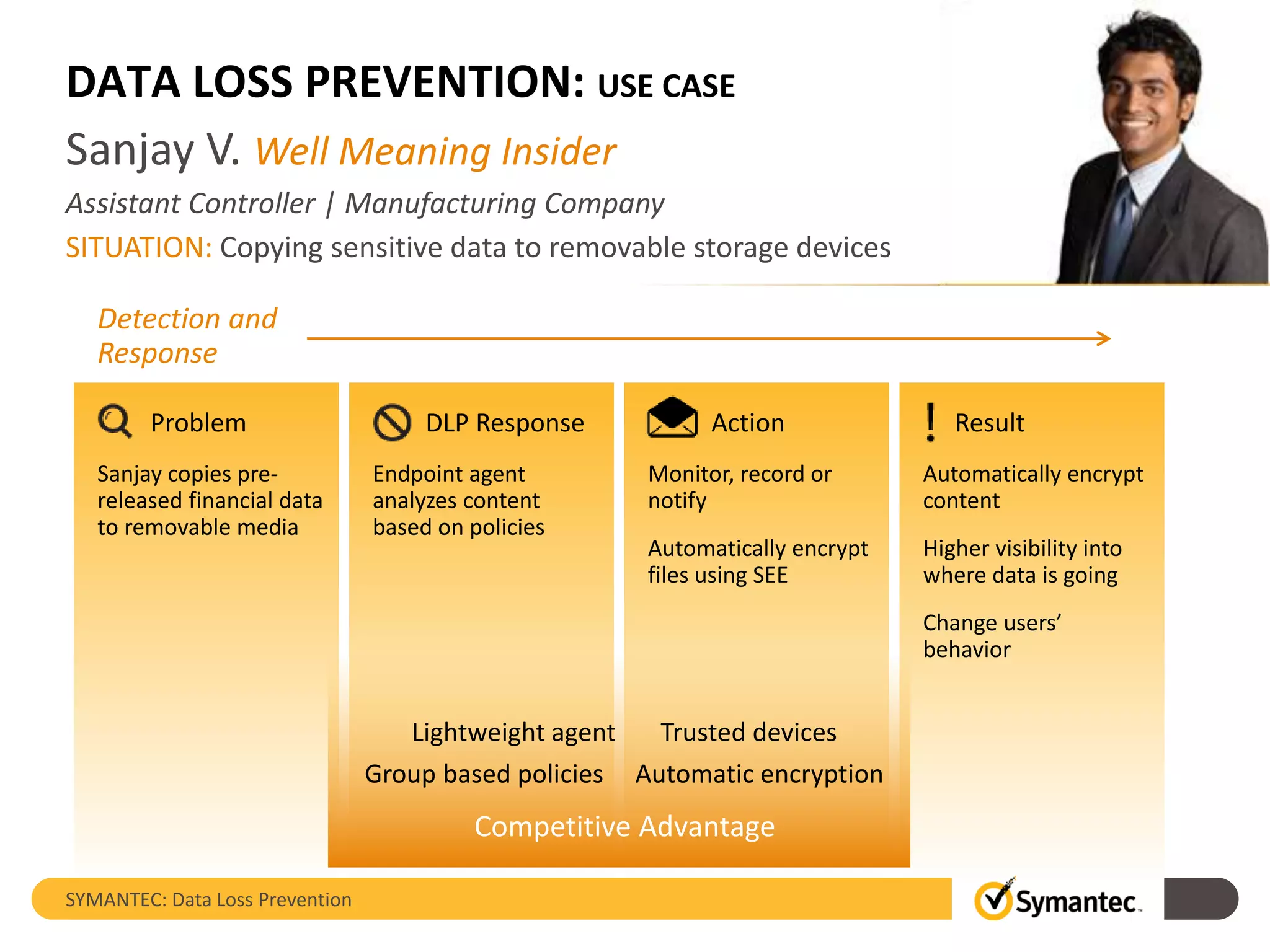
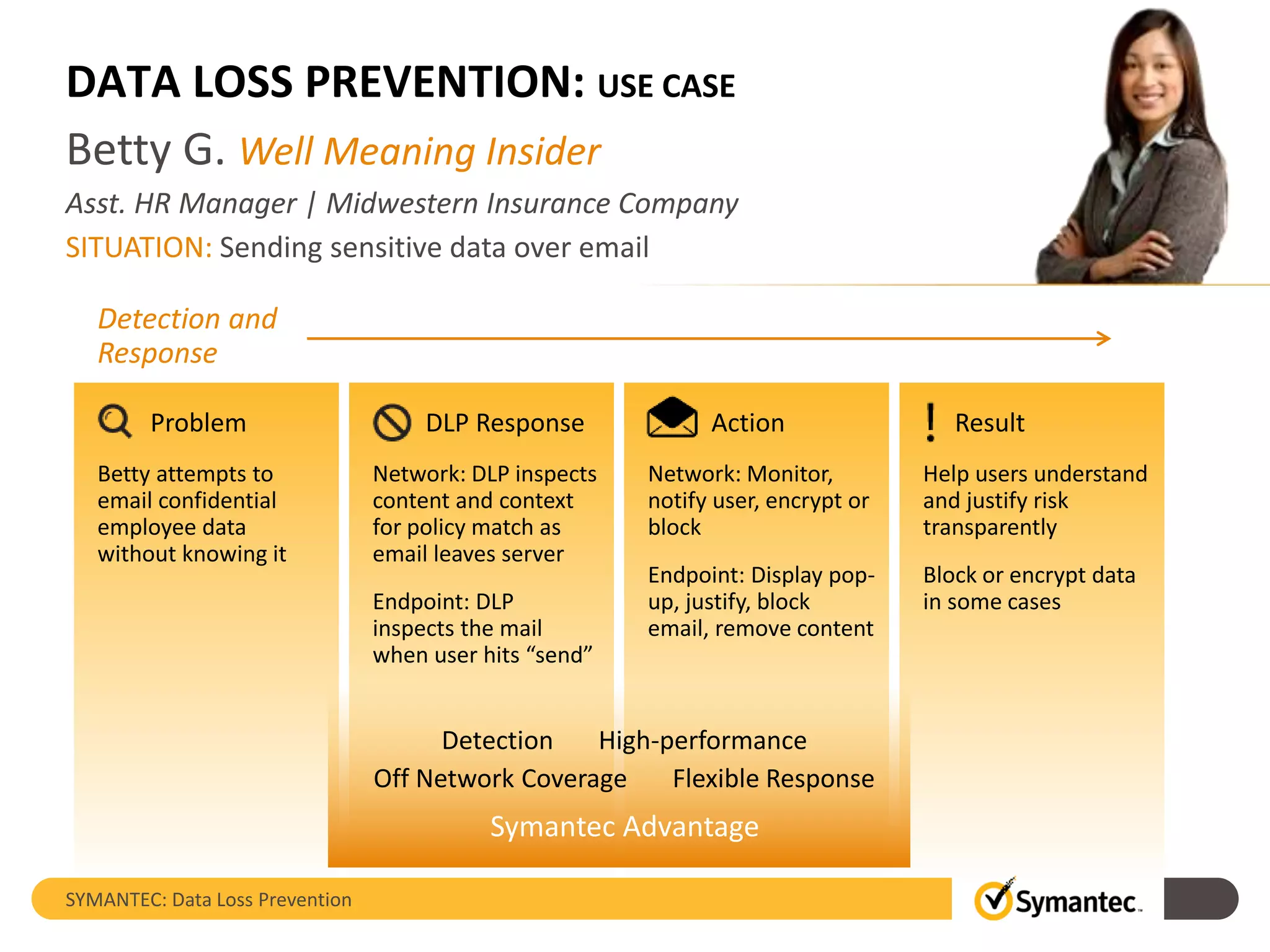
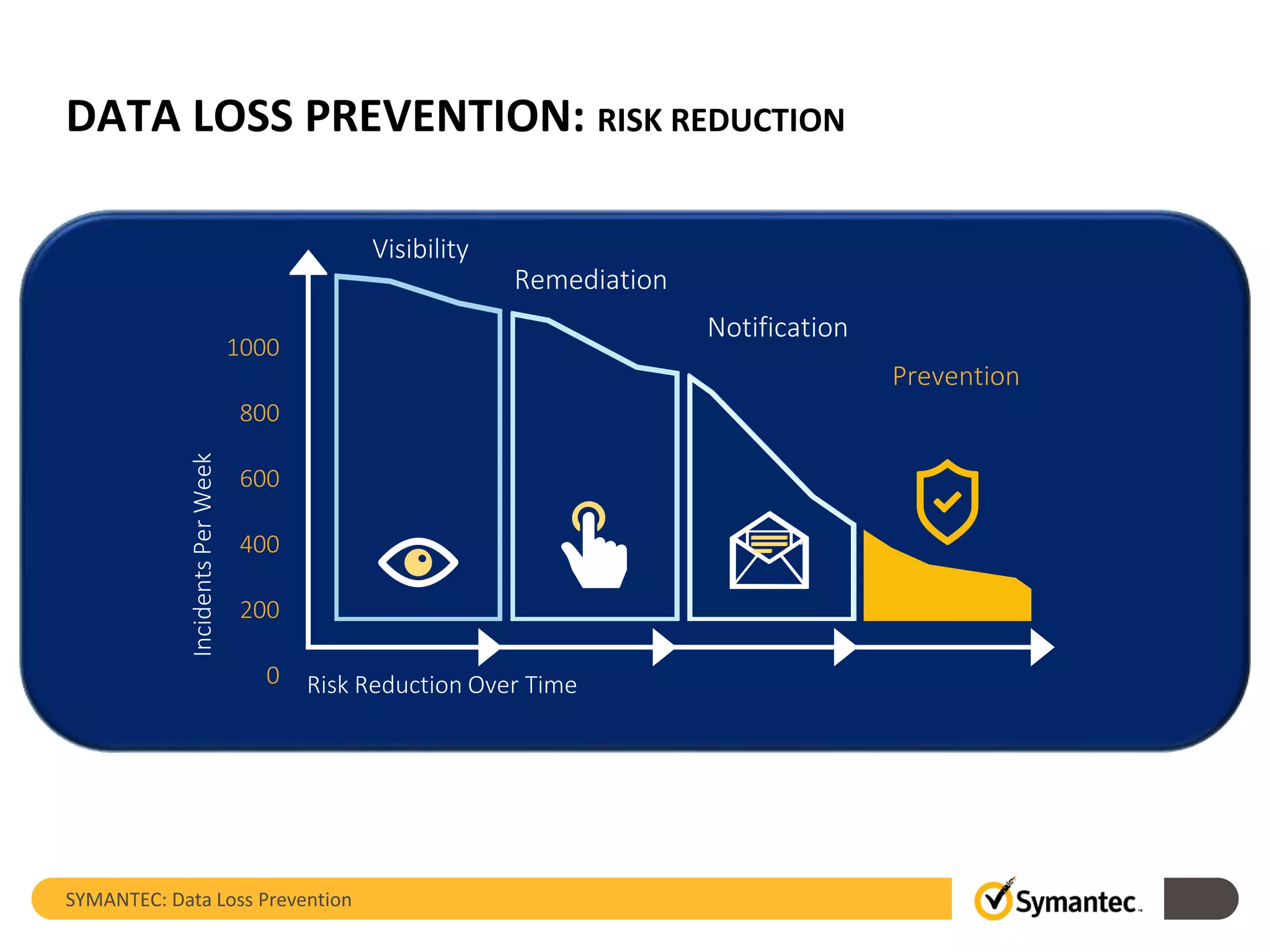
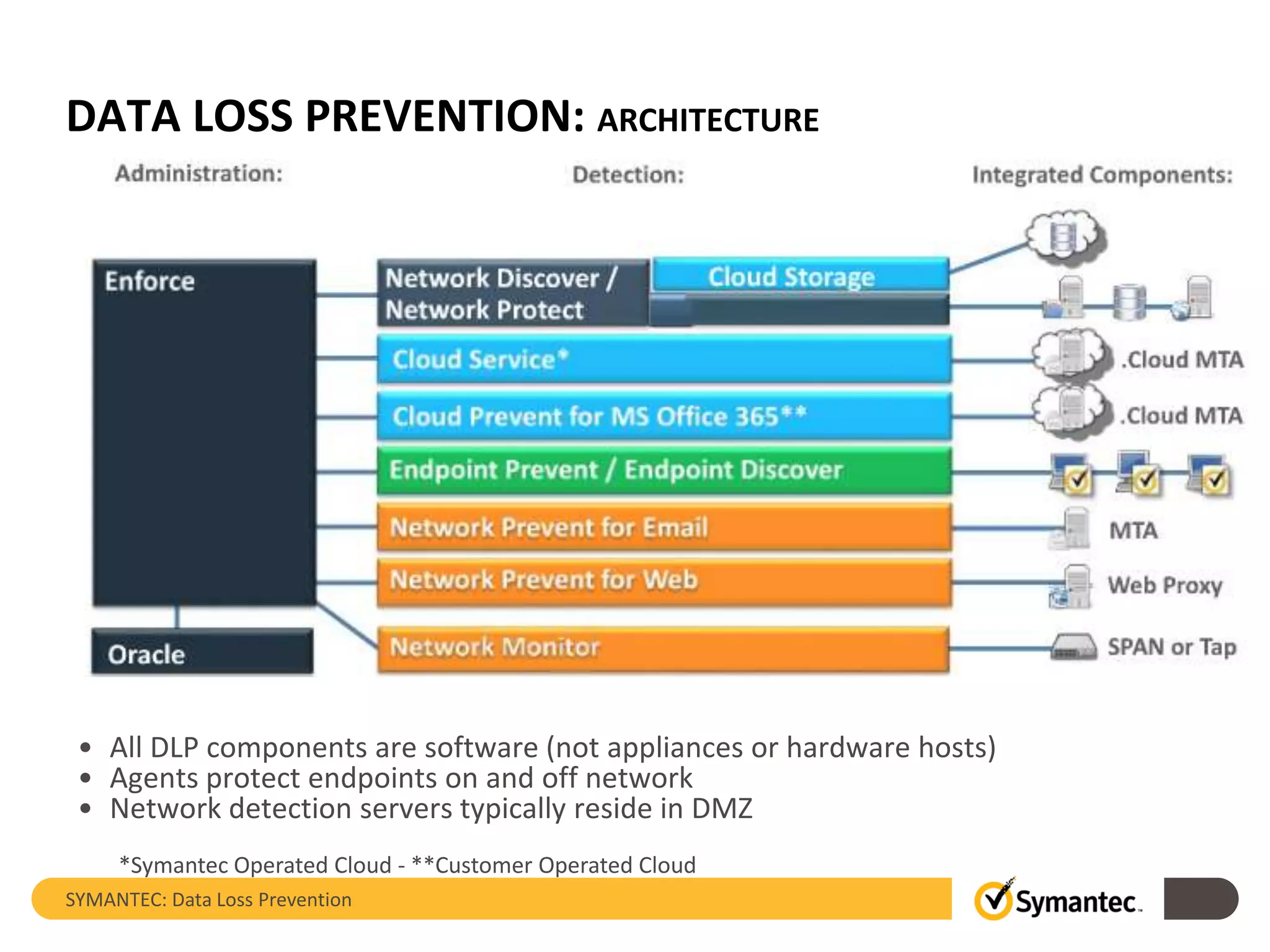
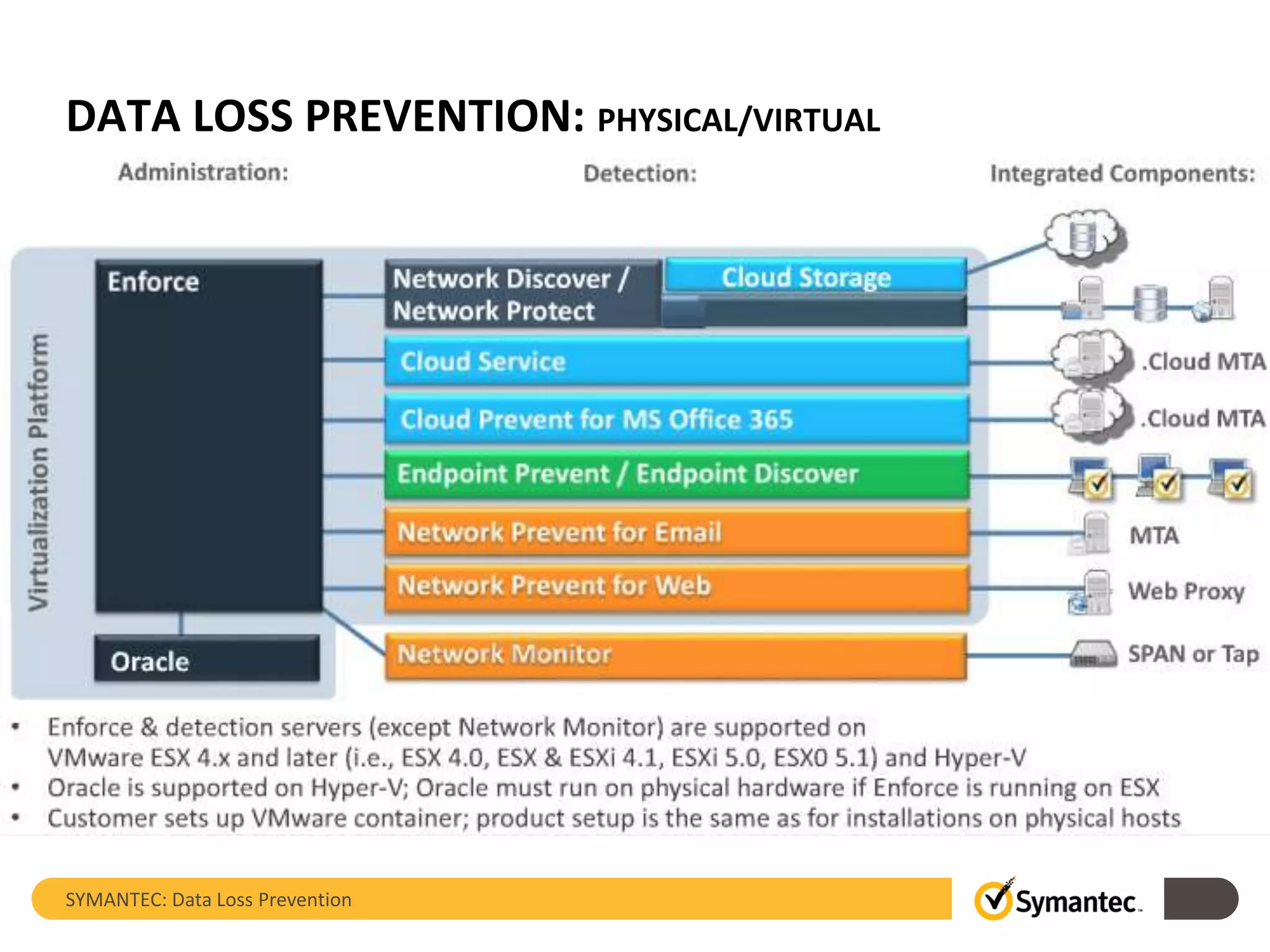
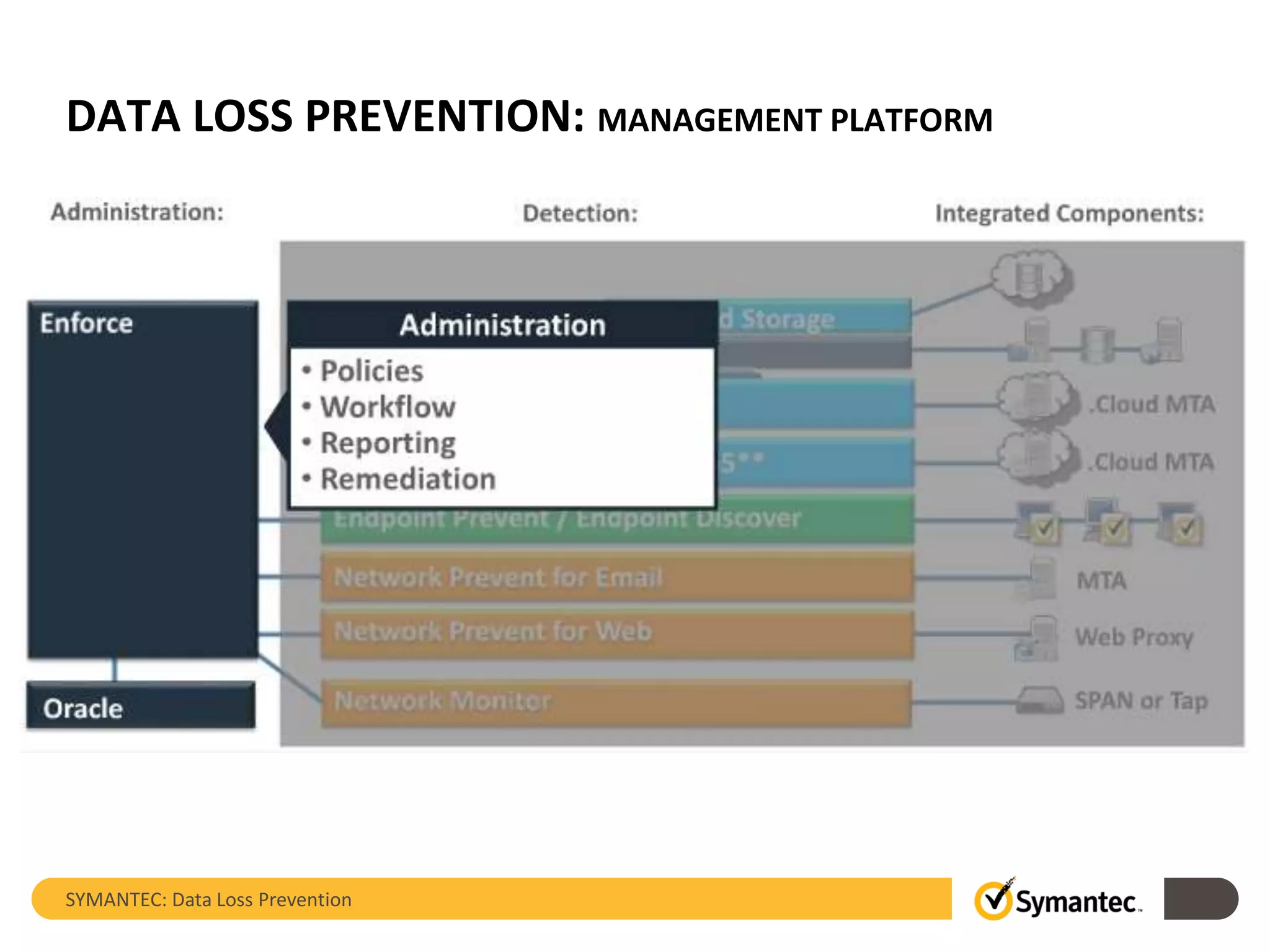
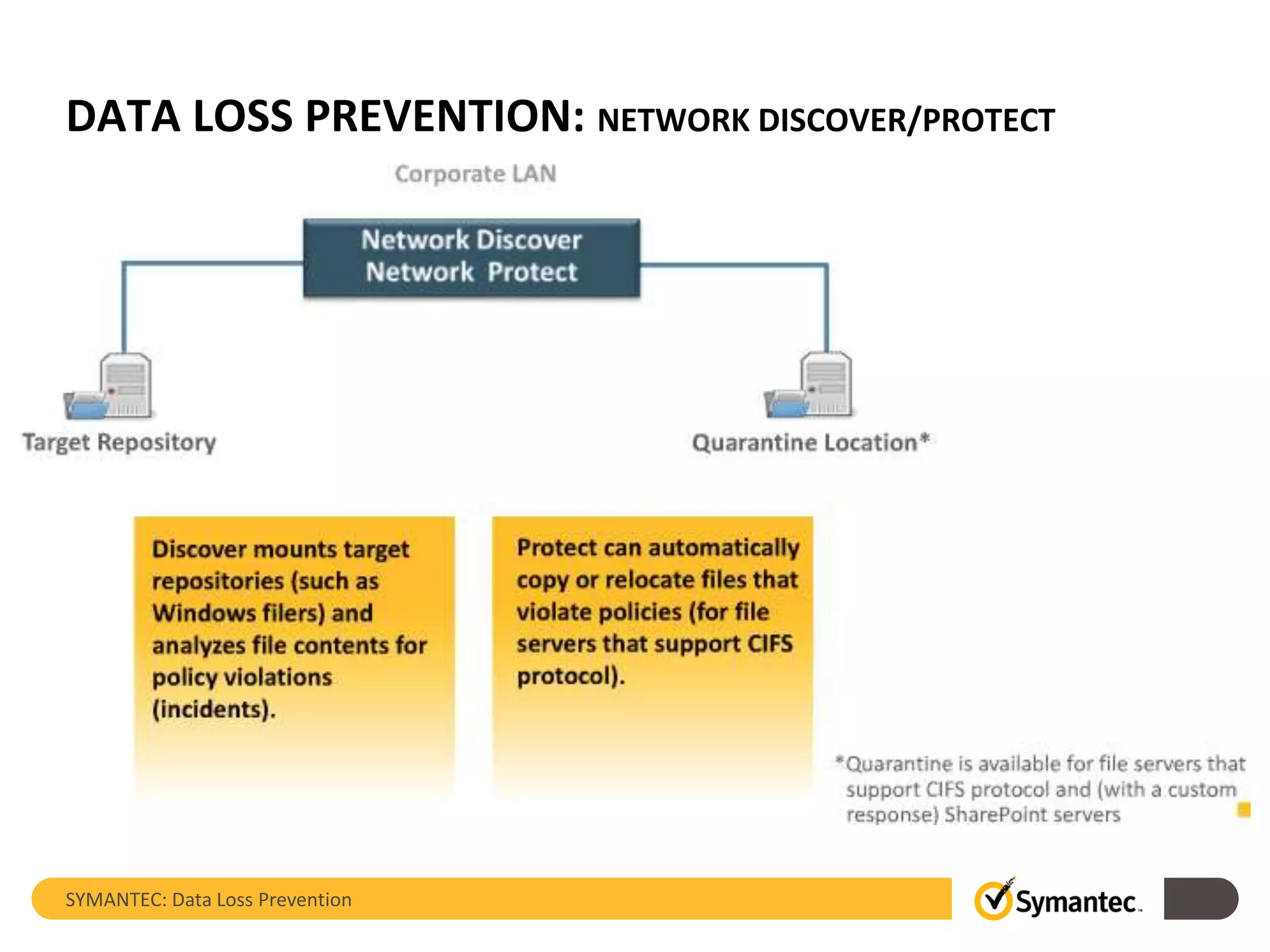
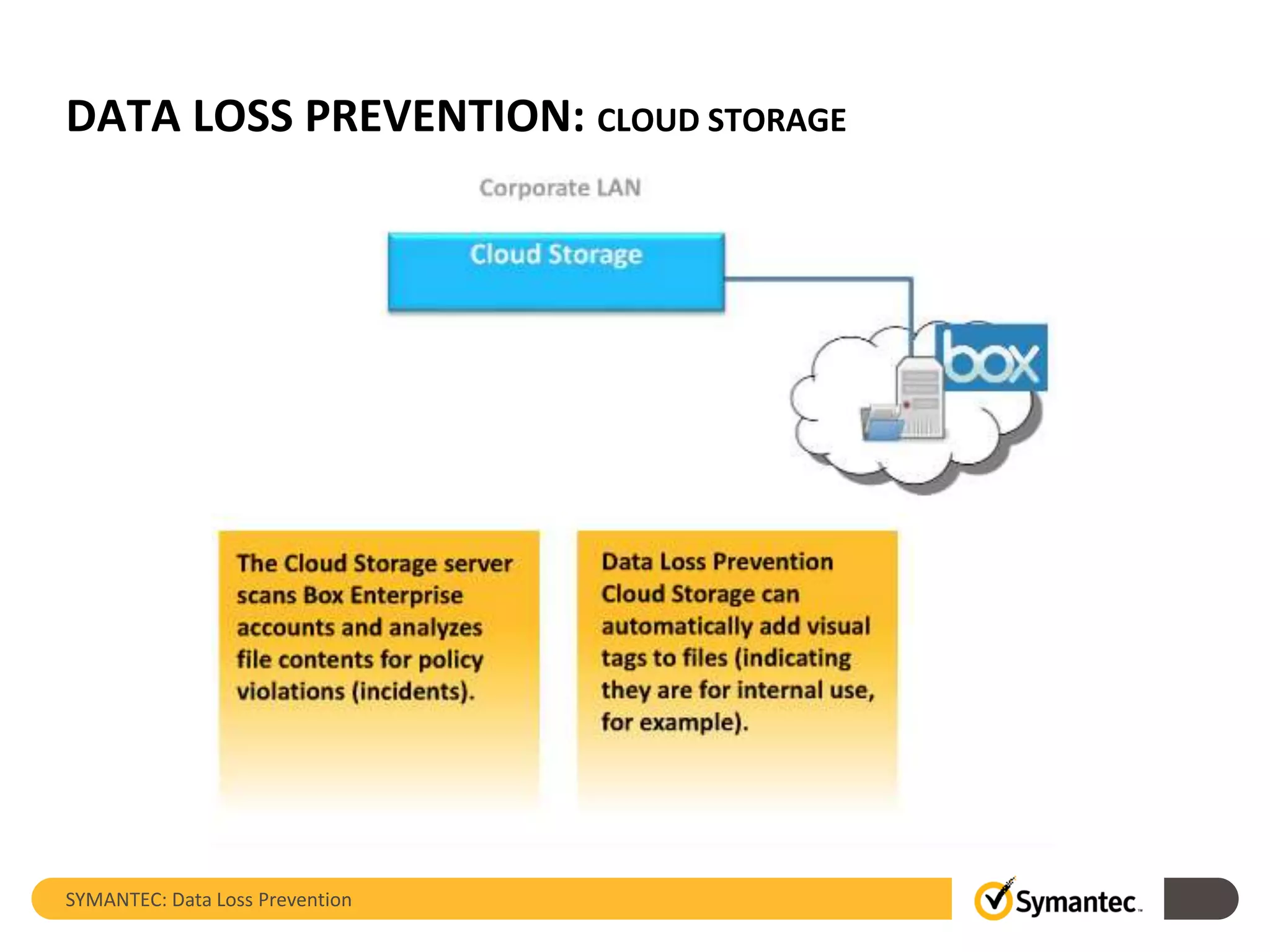
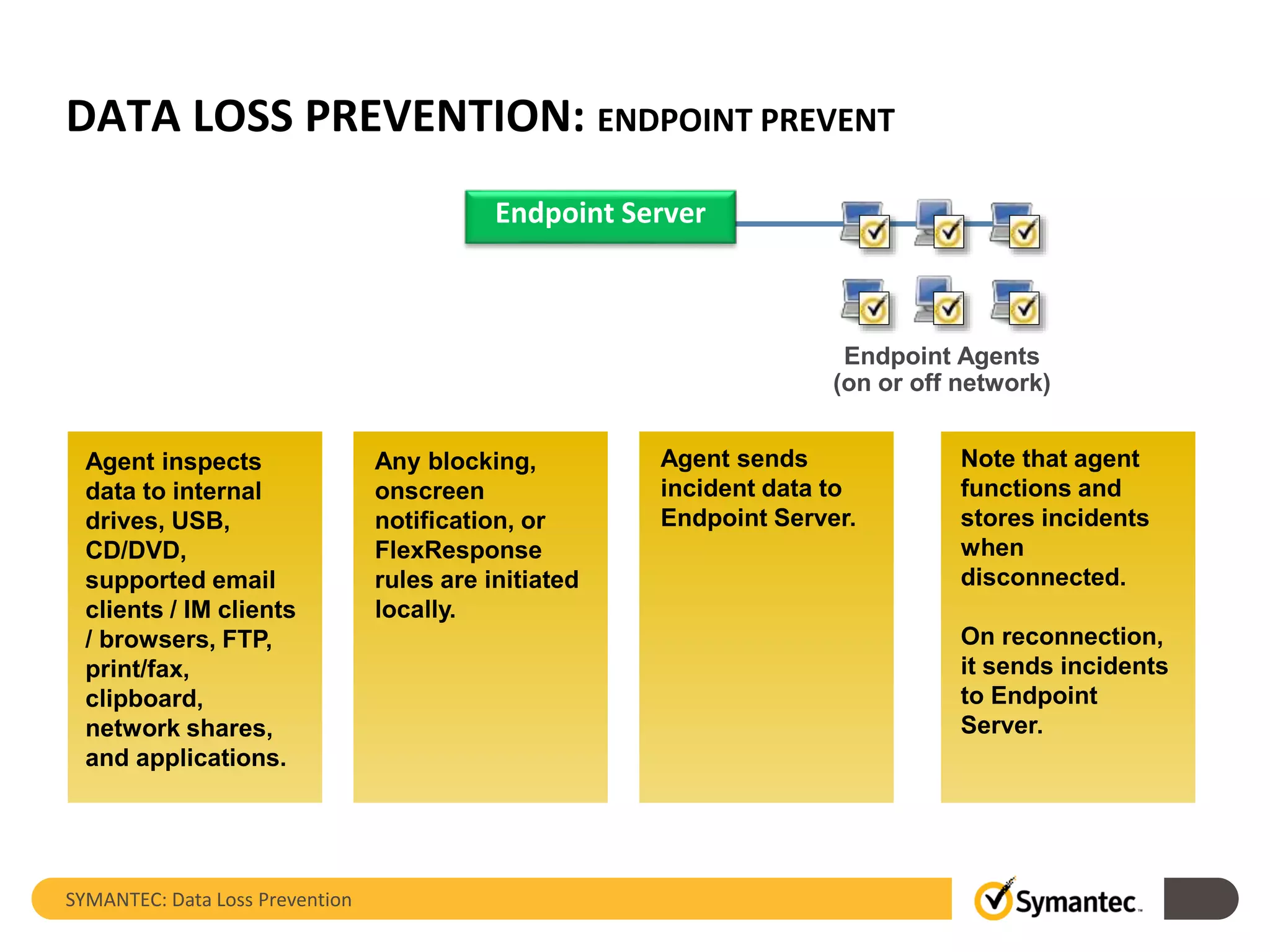
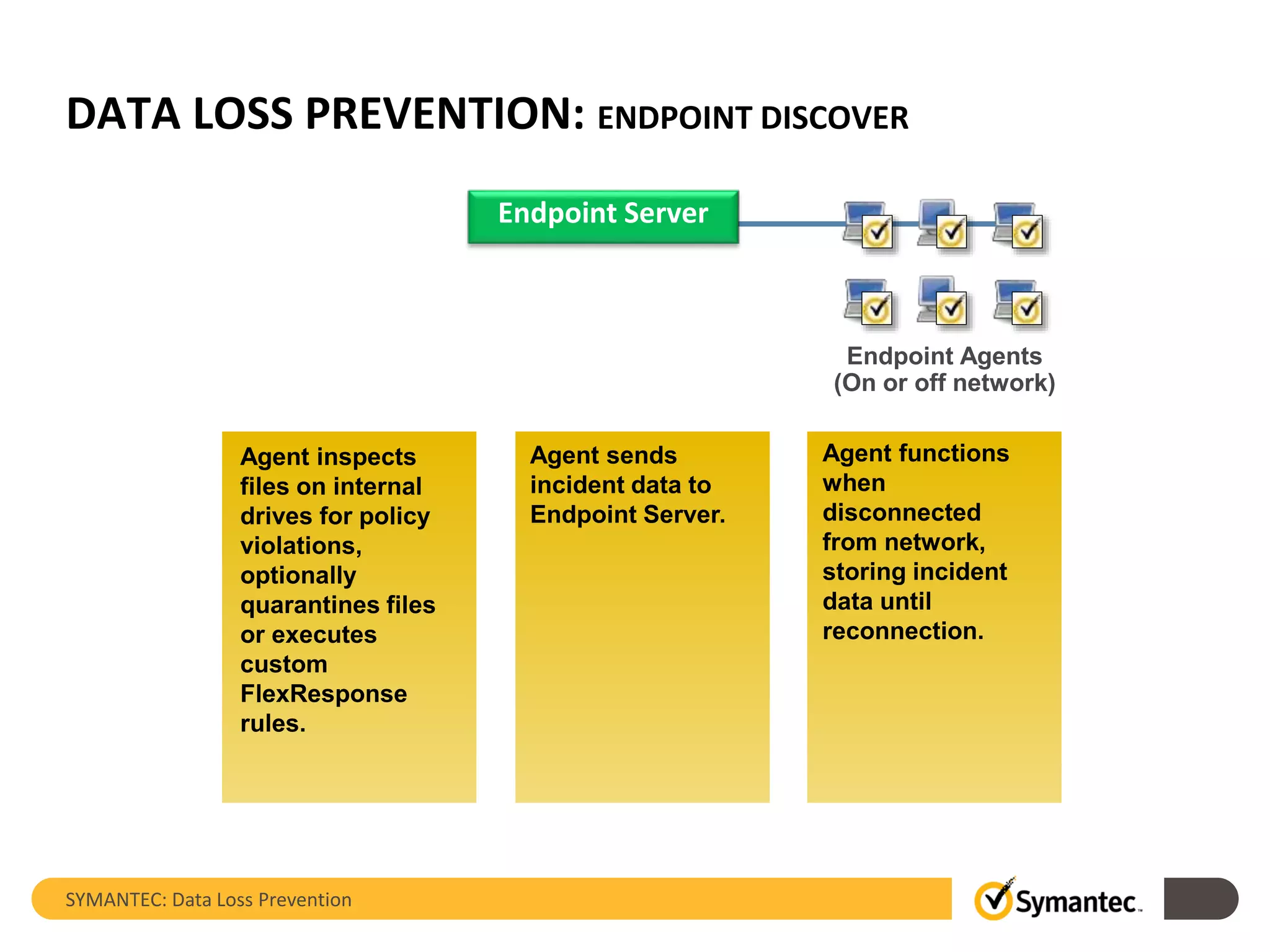
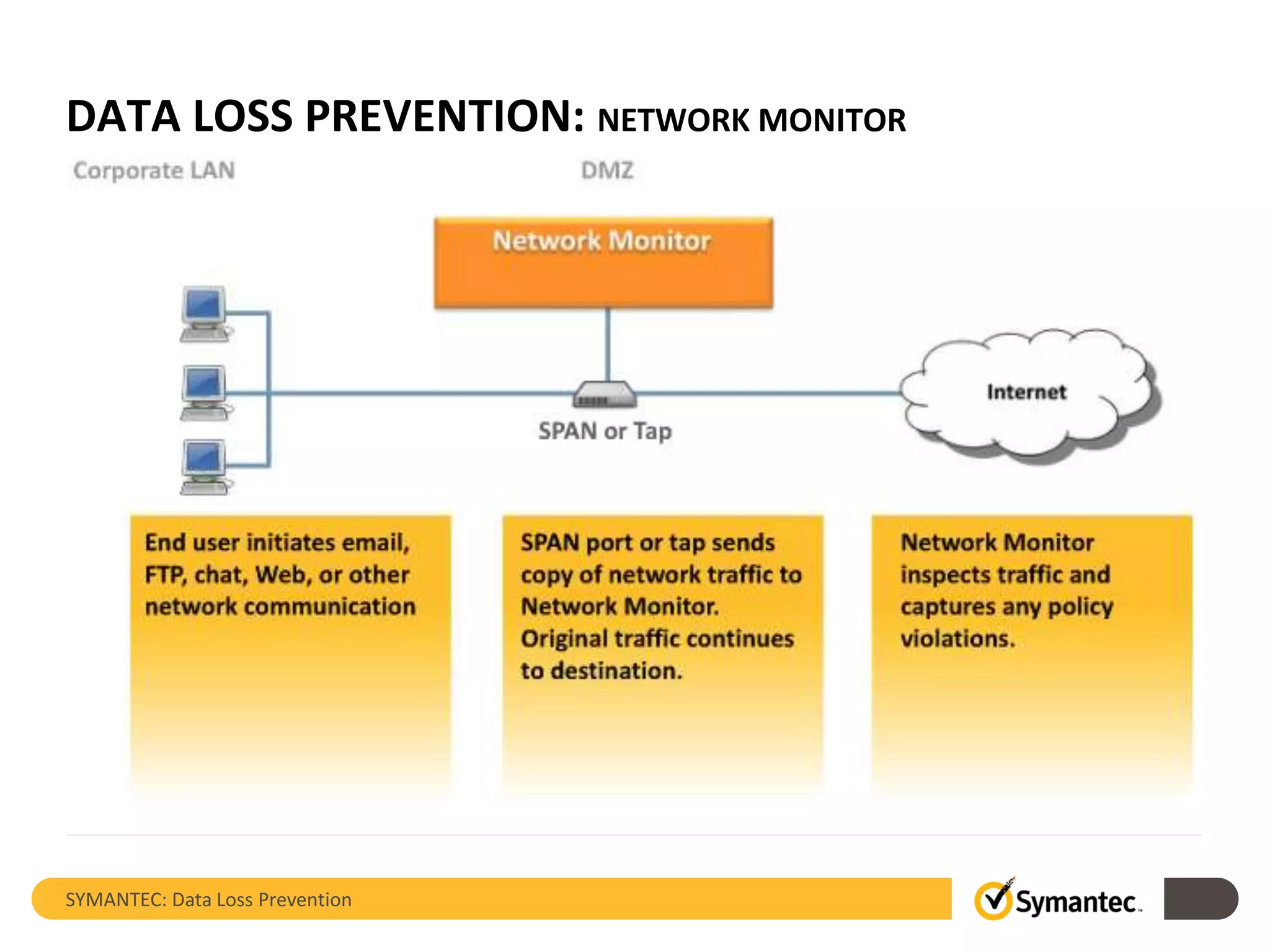
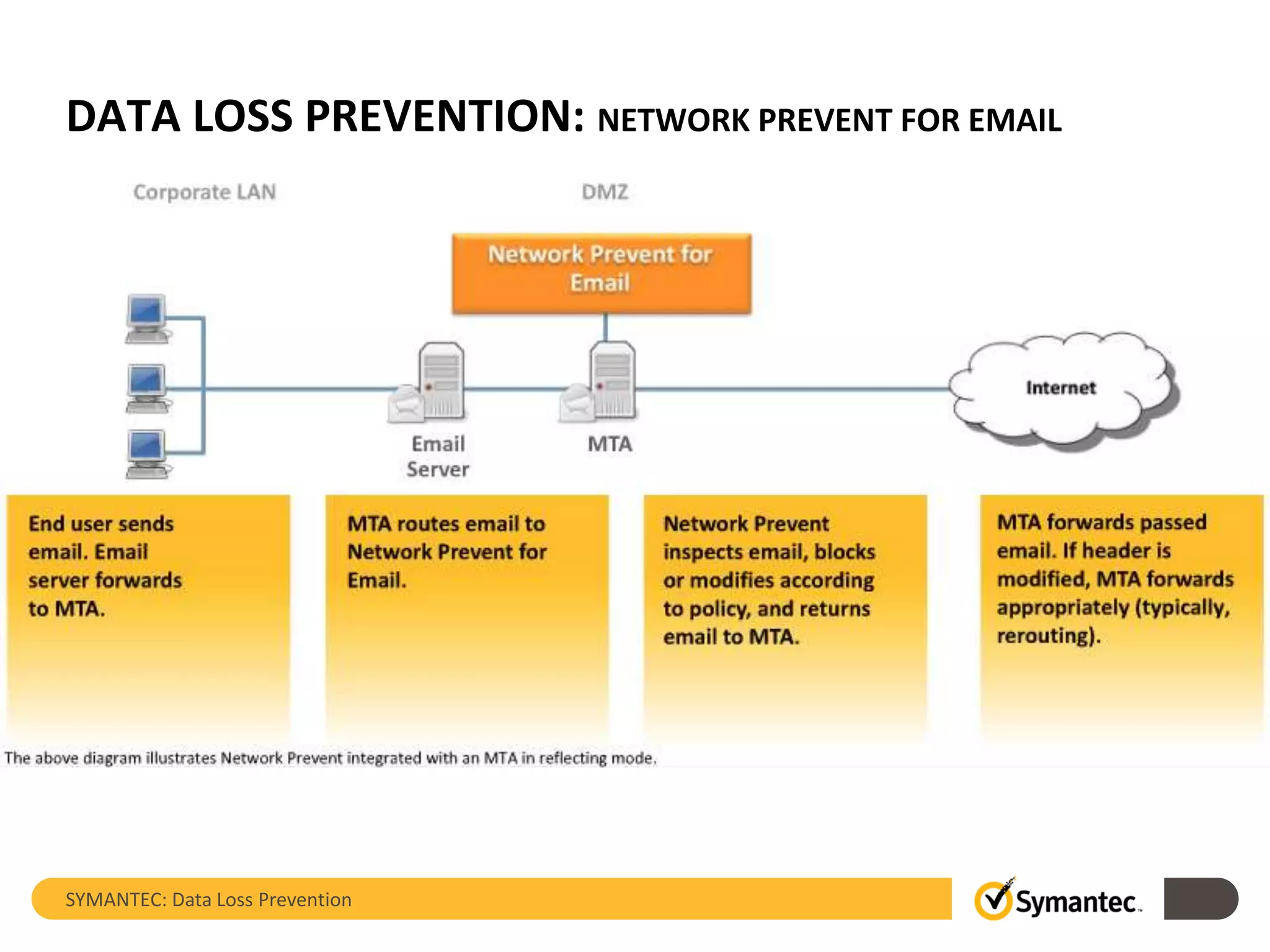
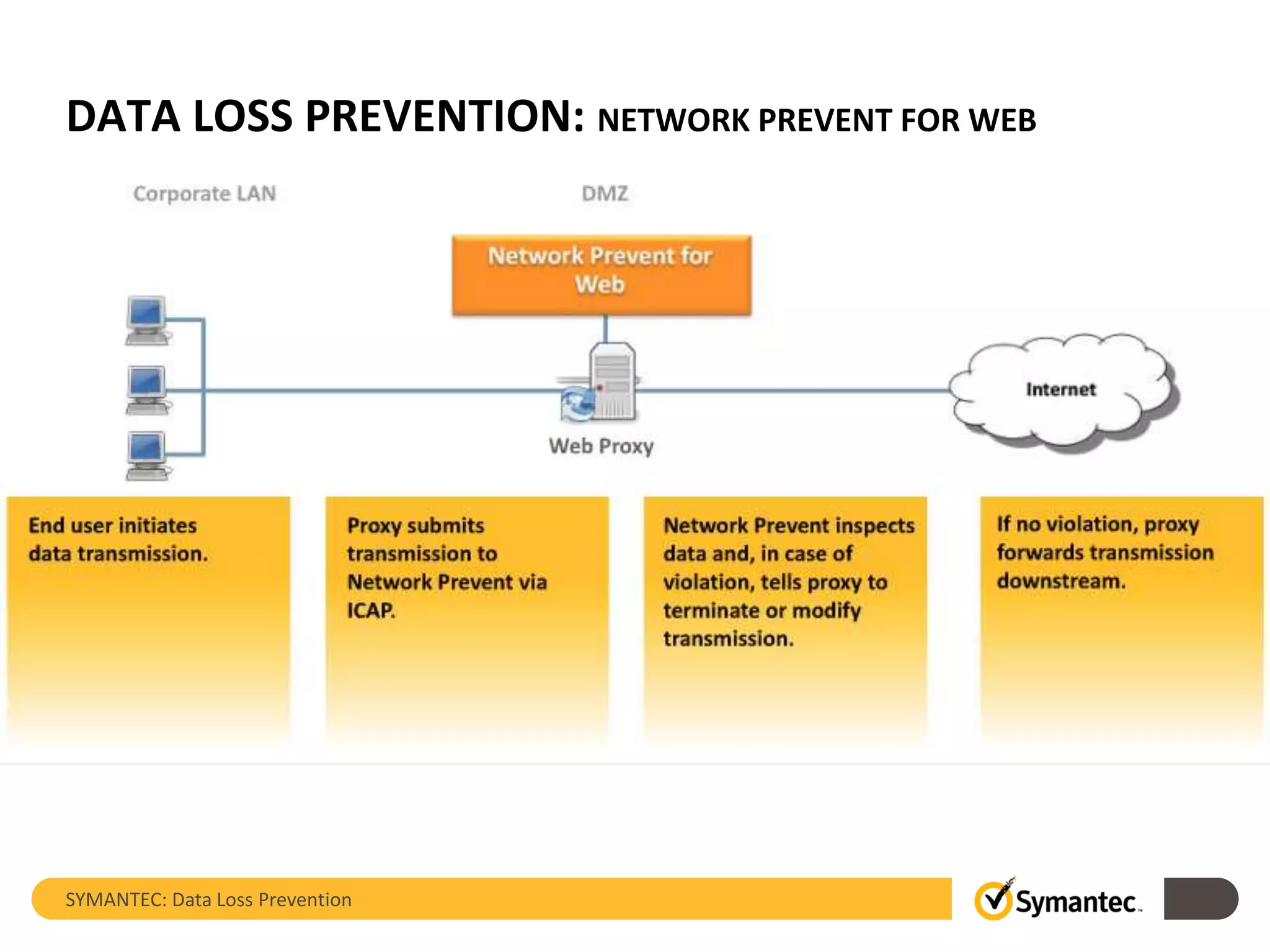
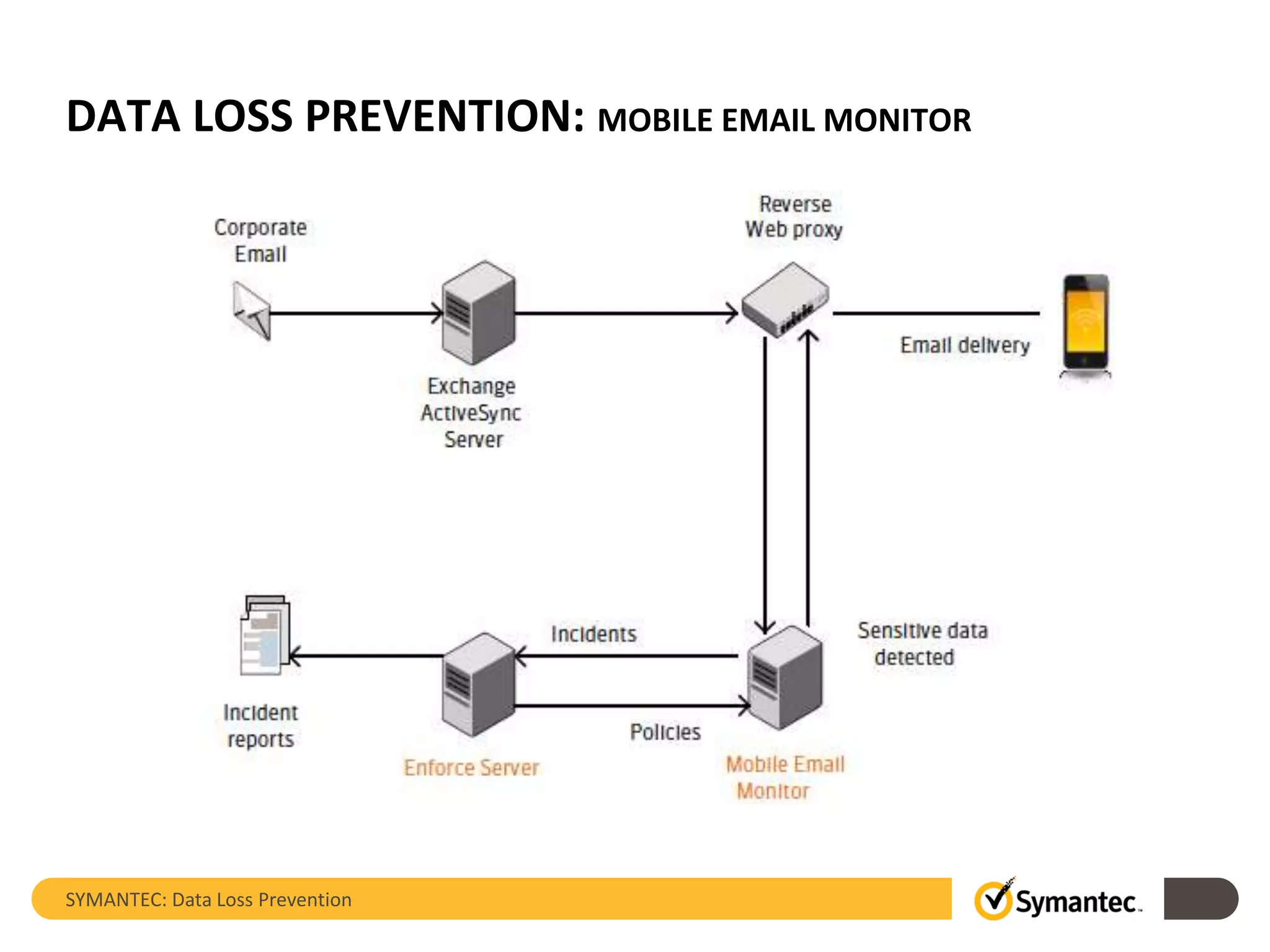
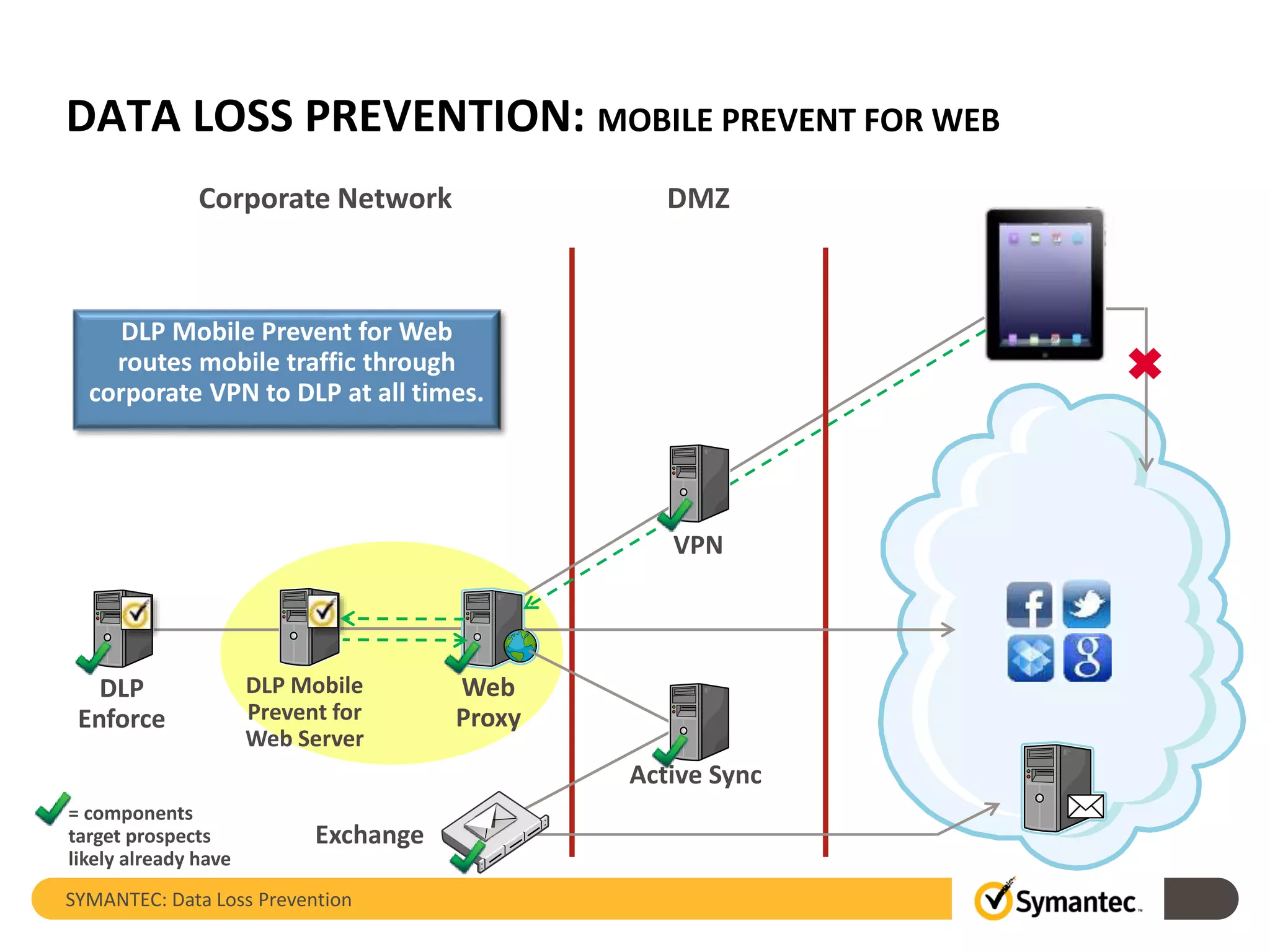
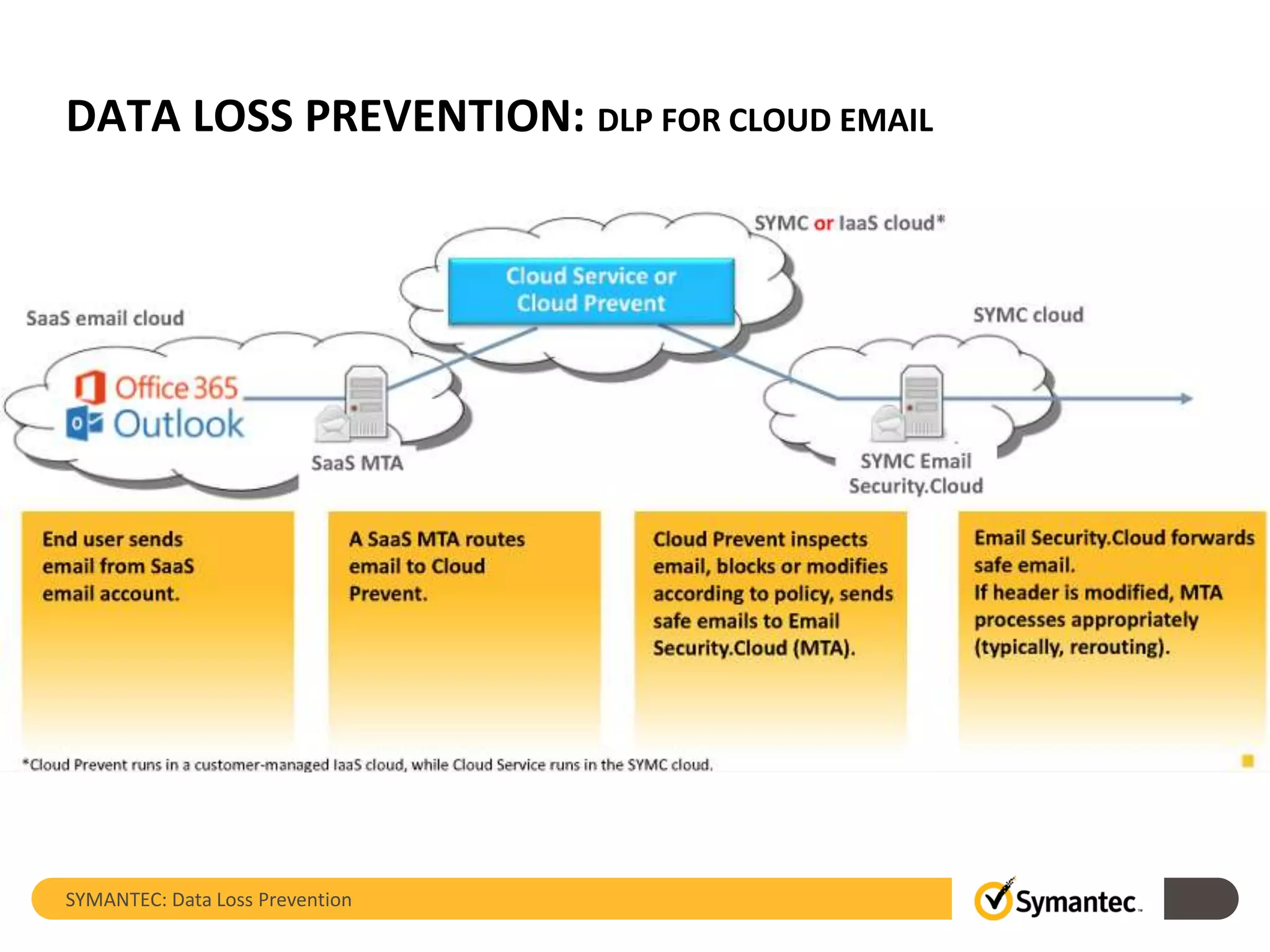
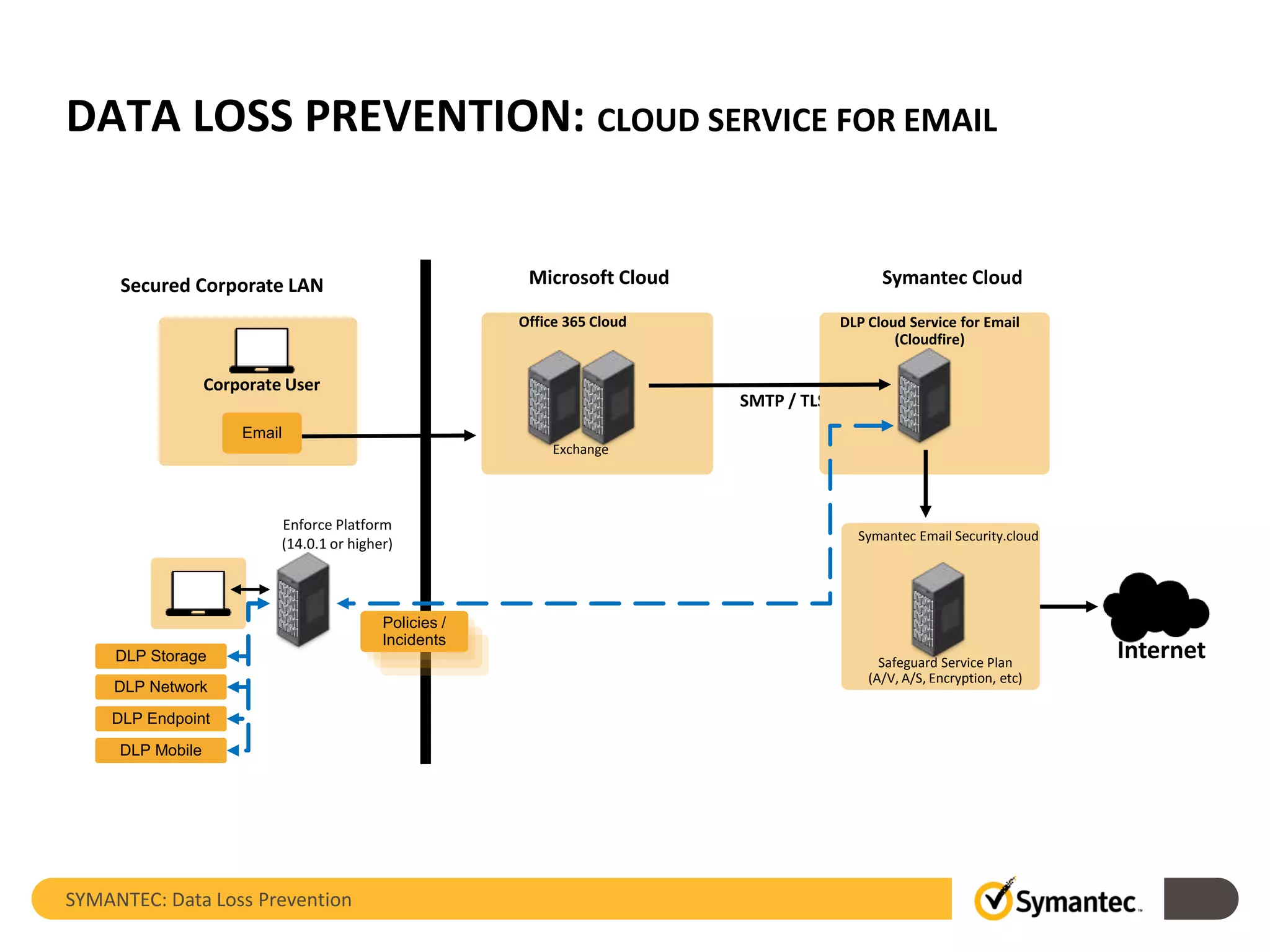
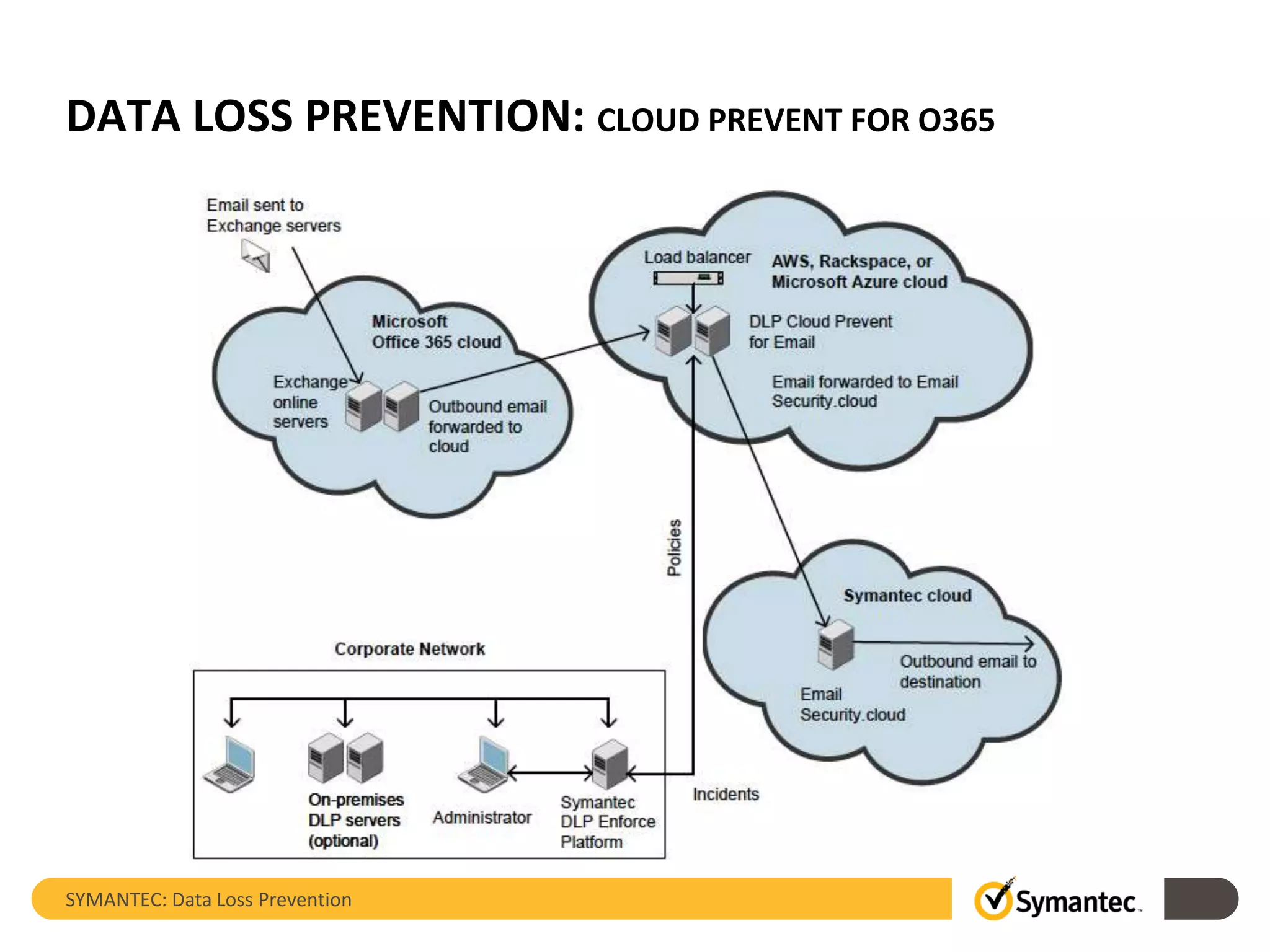
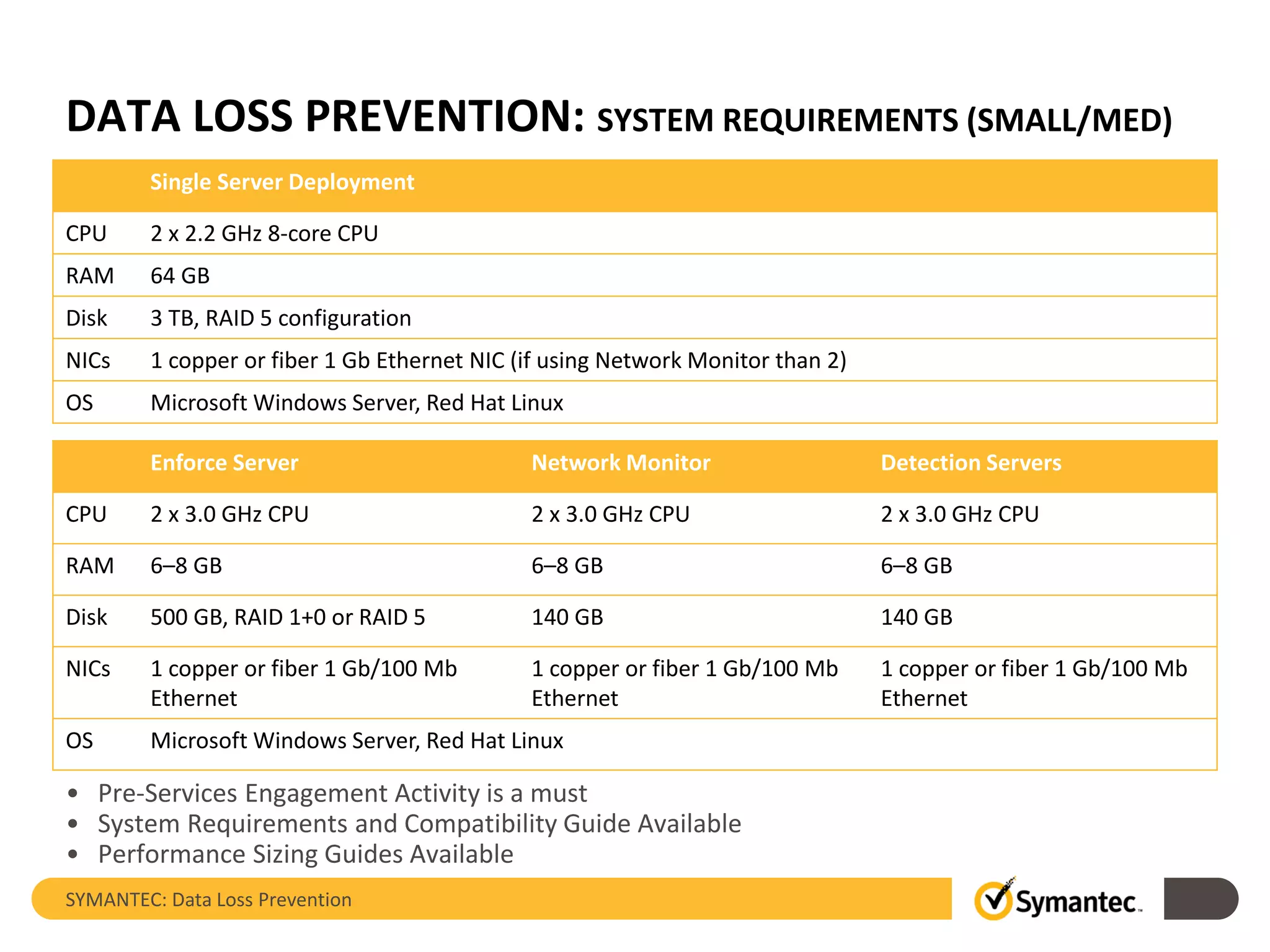
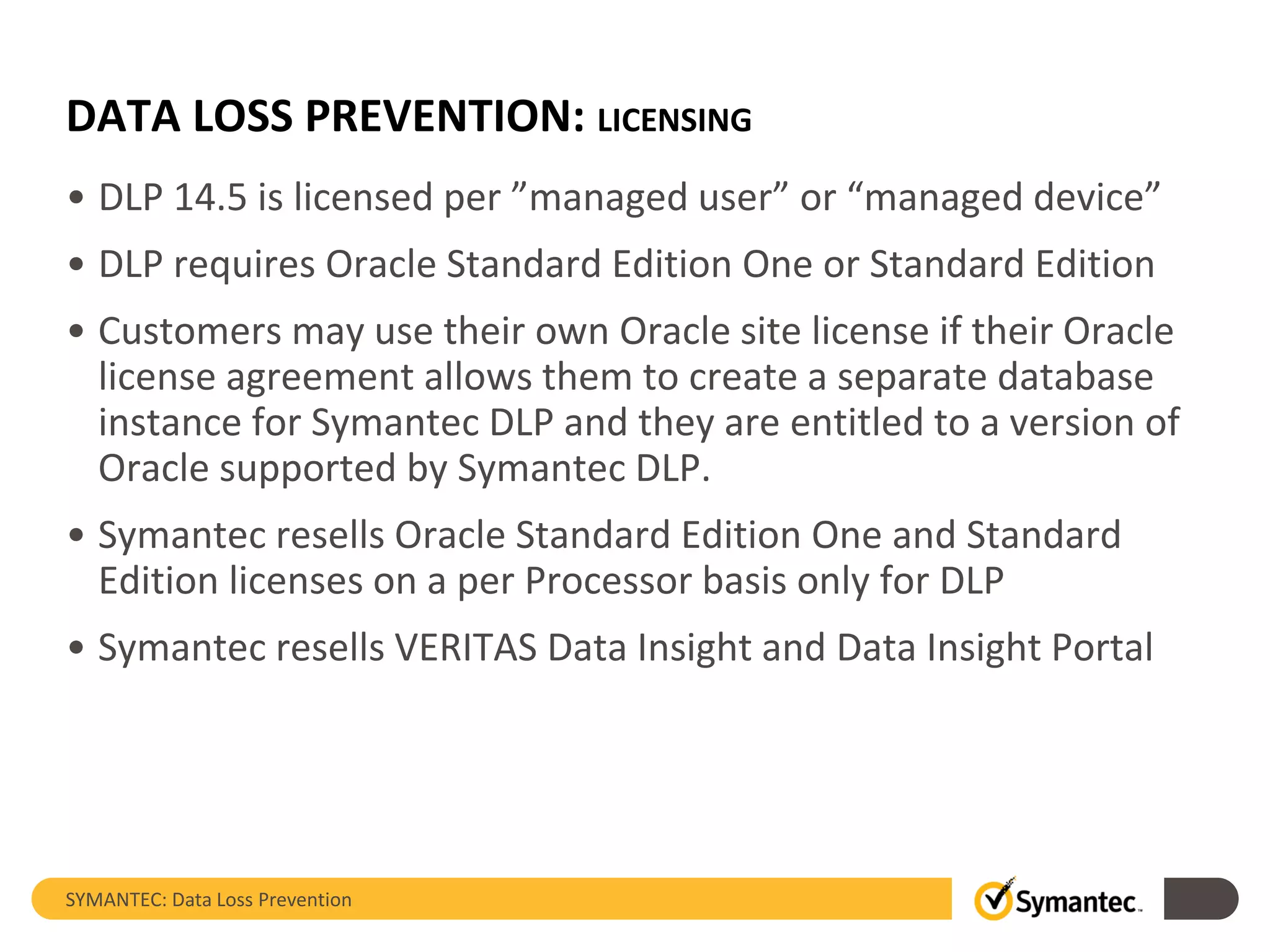
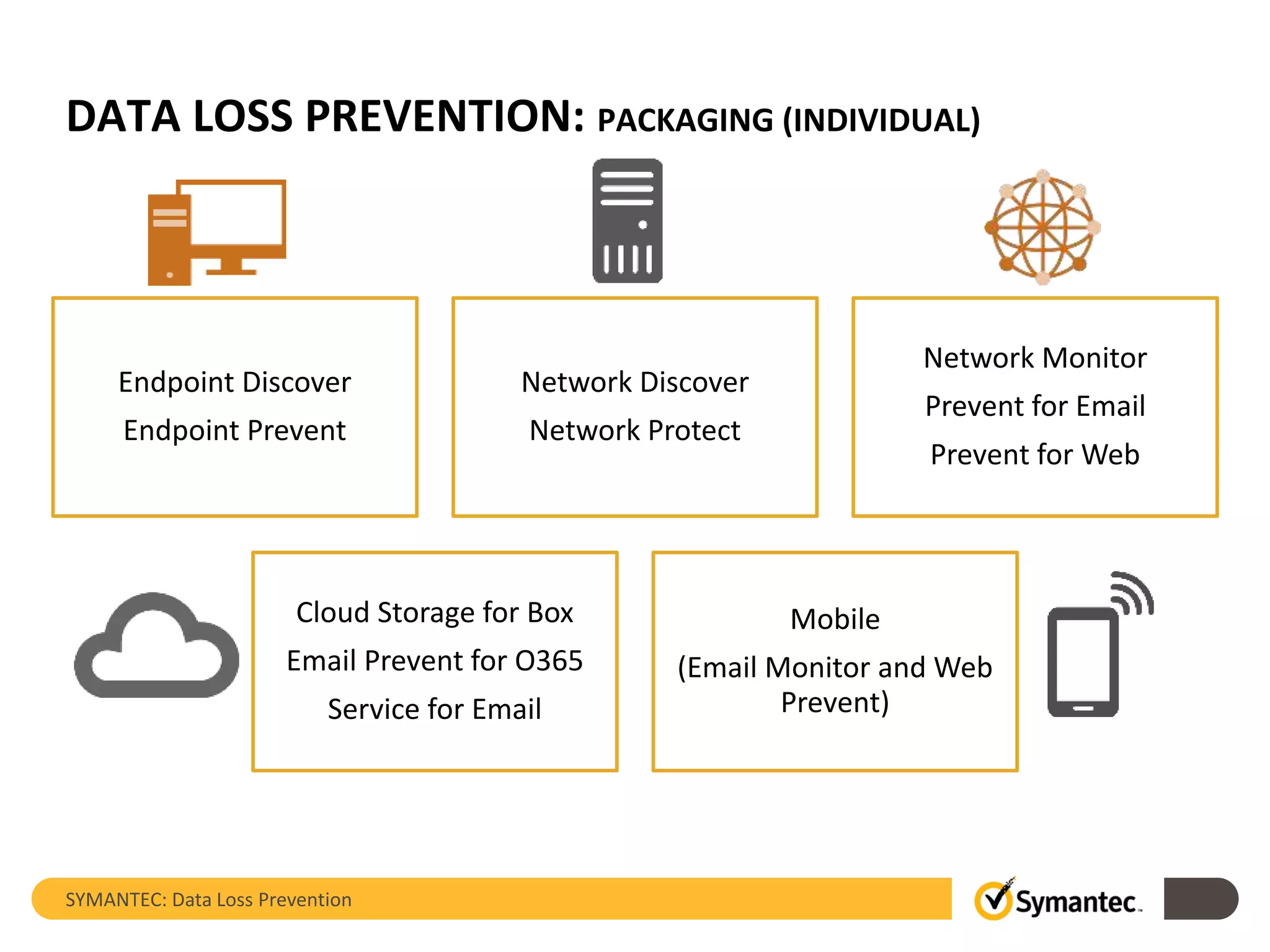
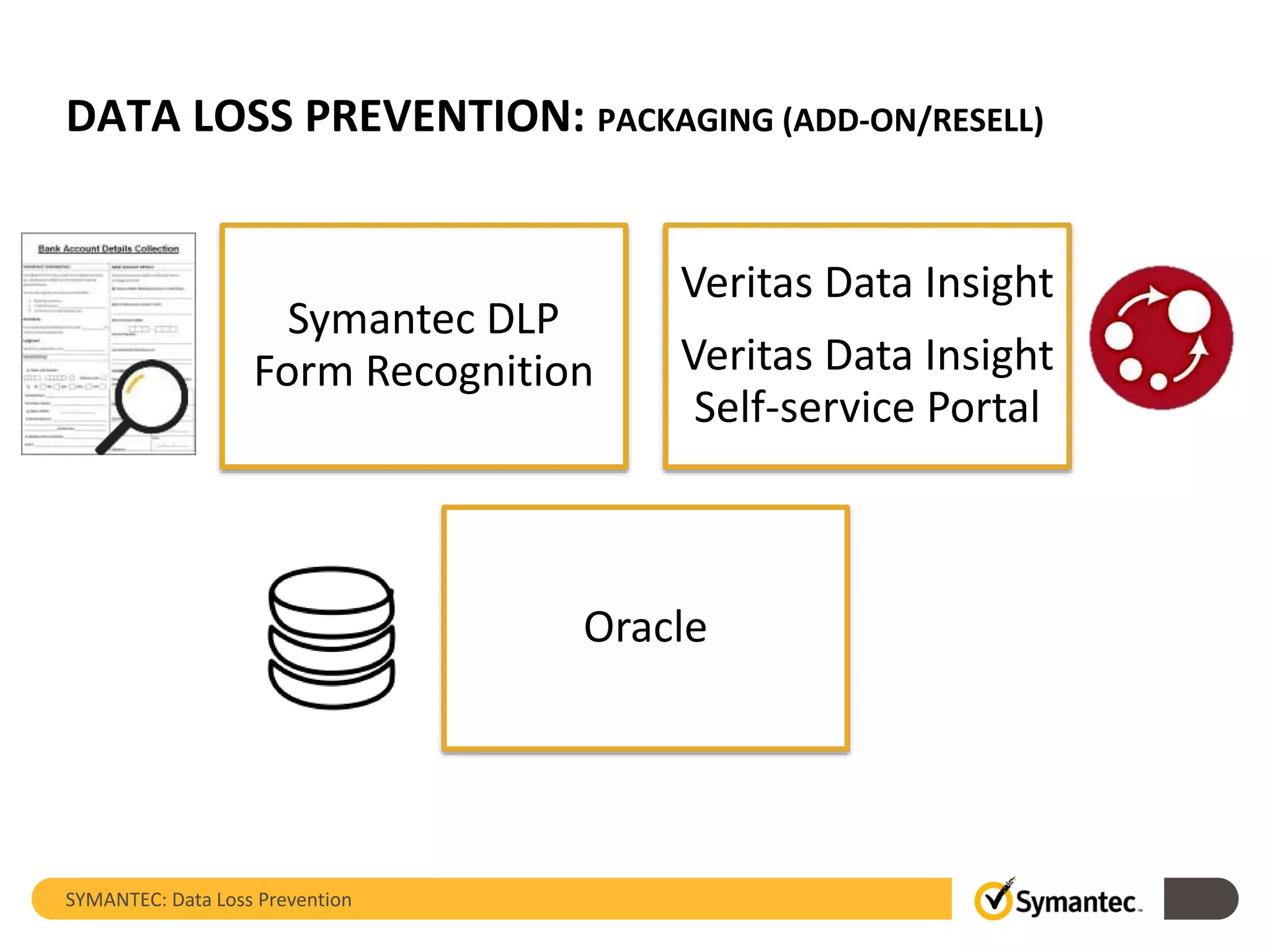
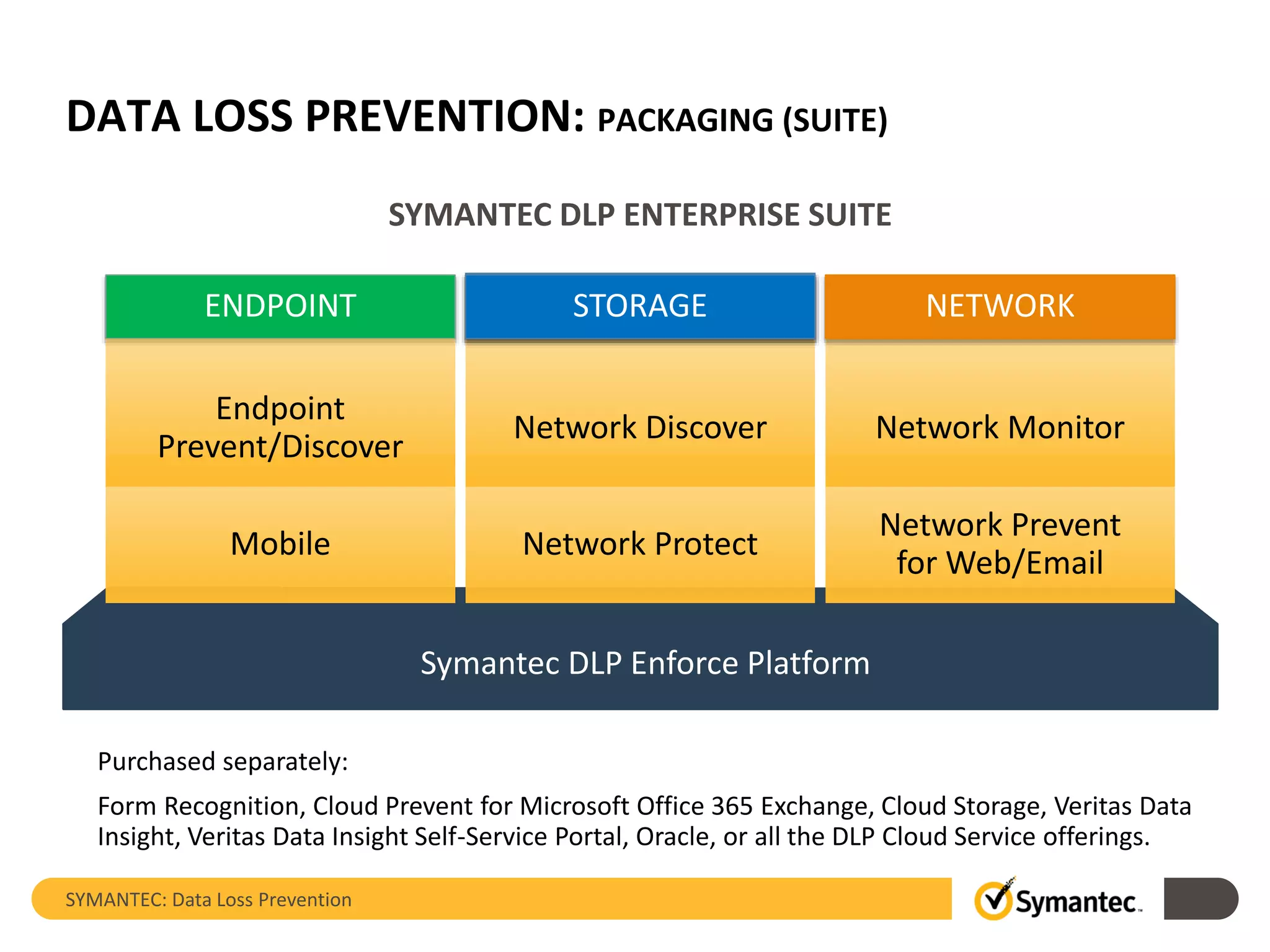
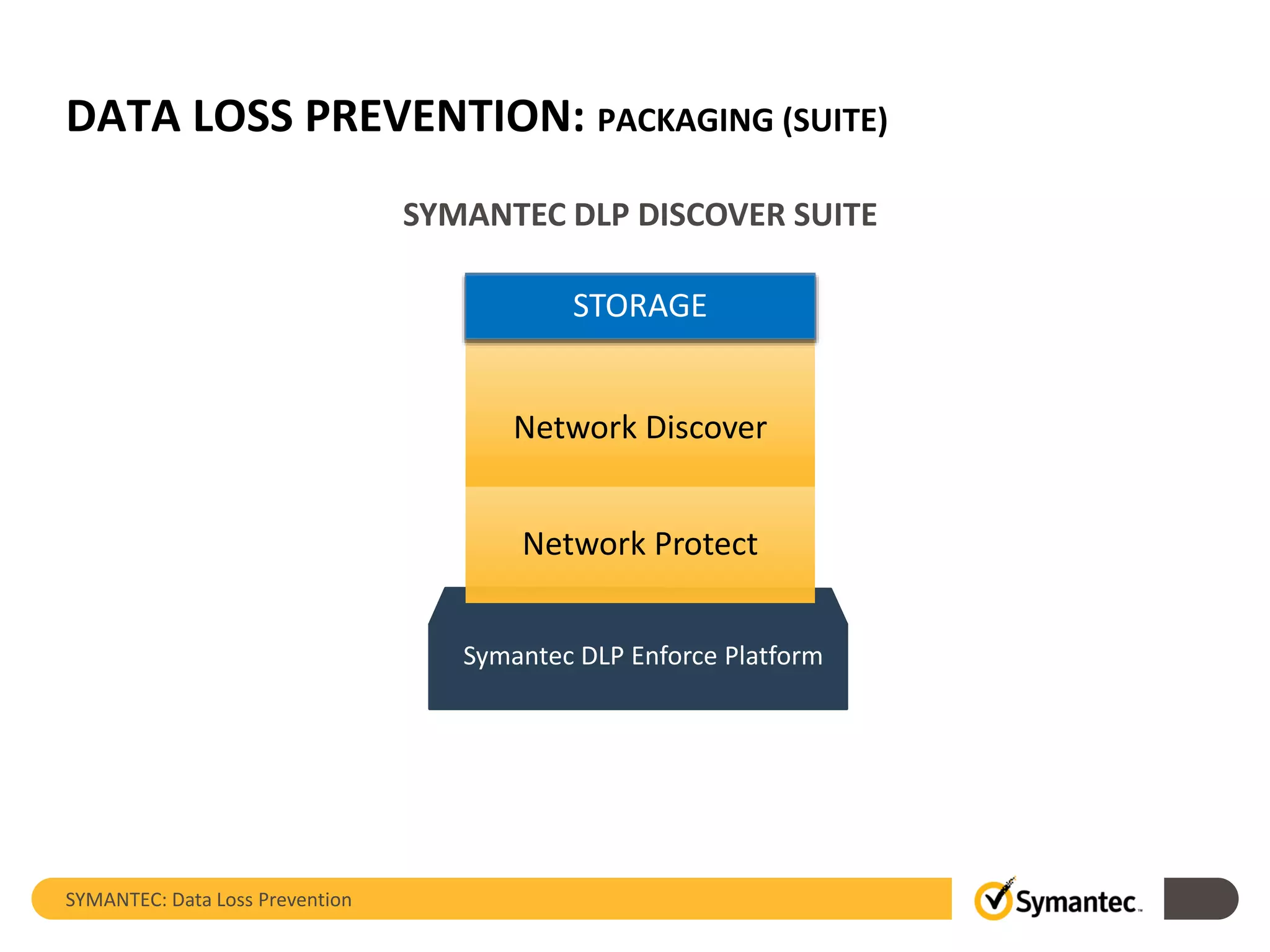
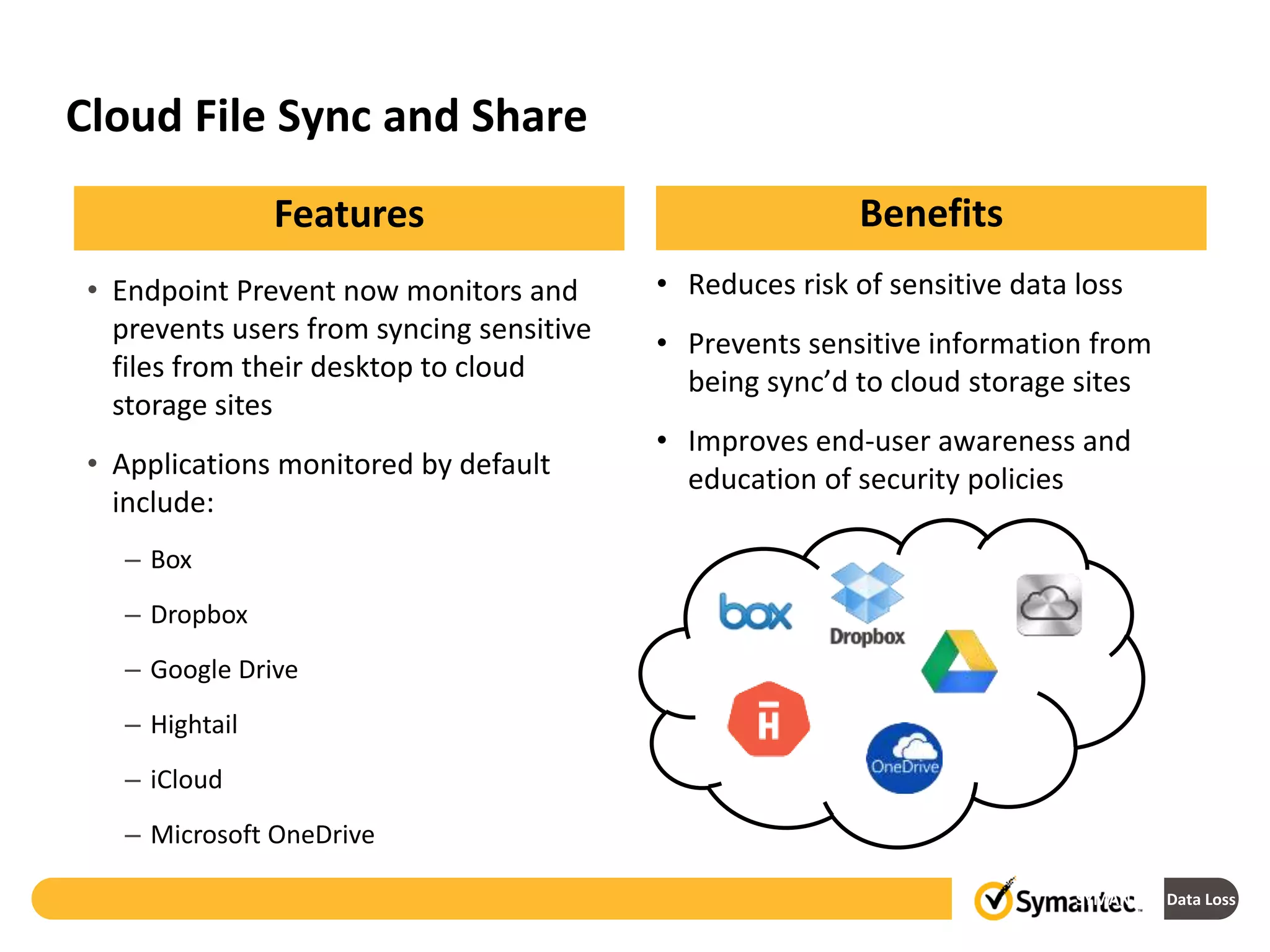
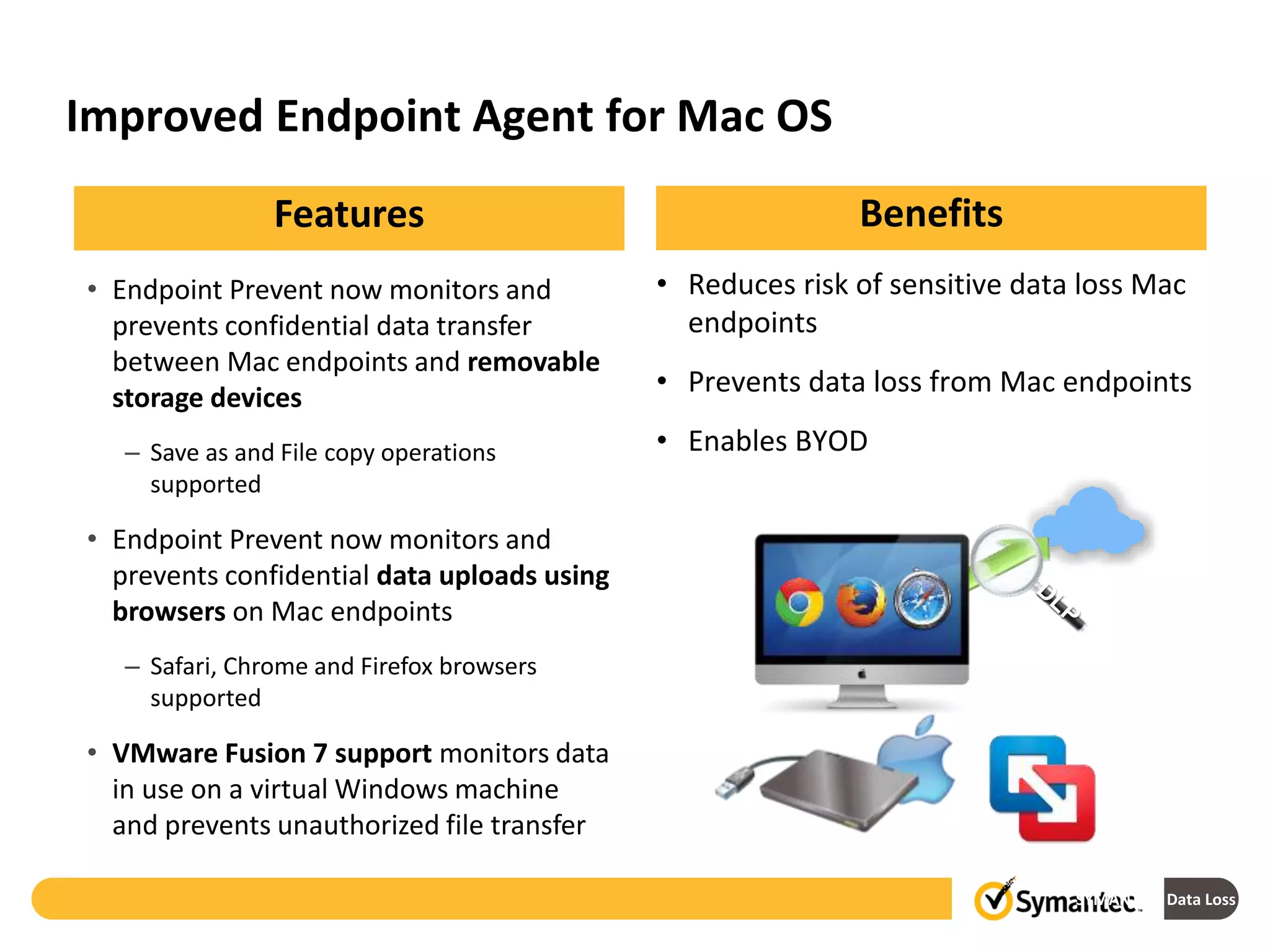
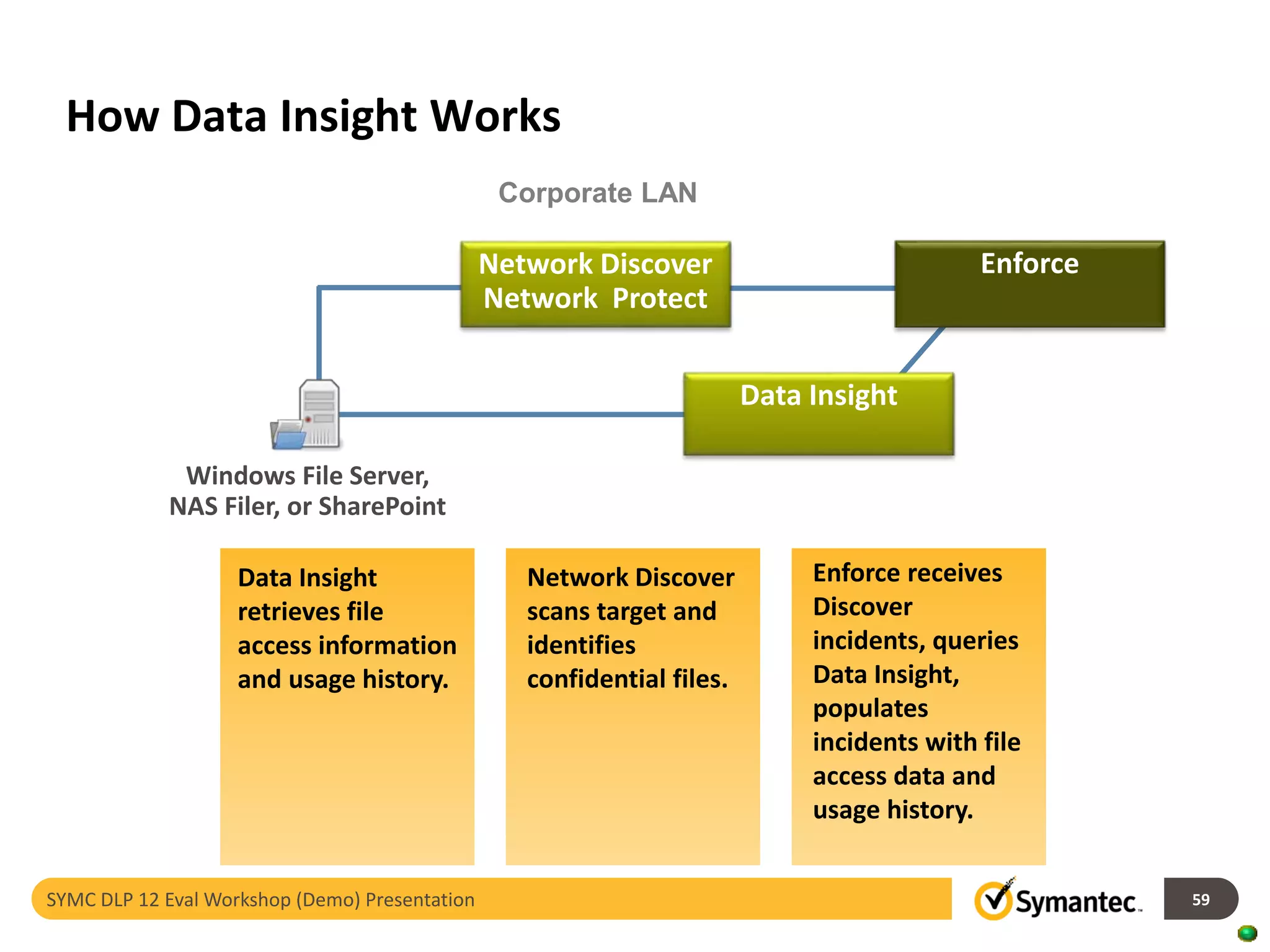
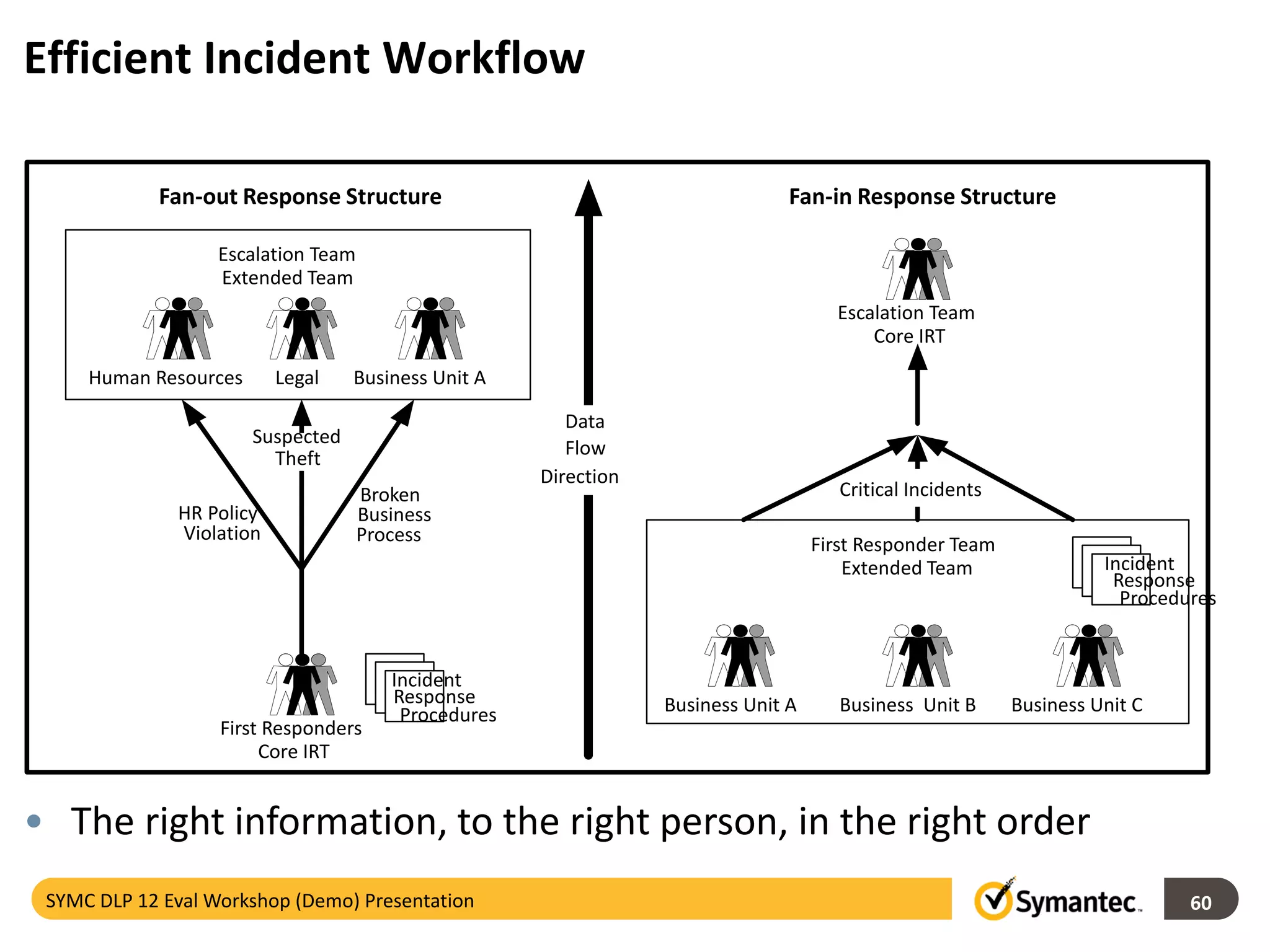
Symantec's Data Loss Prevention (DLP) solution provides comprehensive protection against data leaks by identifying and managing sensitive information across various platforms, including cloud and mobile environments. The solution encompasses features such as monitoring, incident response, and policy enforcement, aimed at safeguarding confidential data from unauthorized access and loss. Key components include endpoint, network, storage, and mobile DLP functionalities, ensuring a robust defense against cyber threats and compliance with governance regulations.