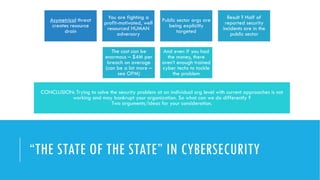
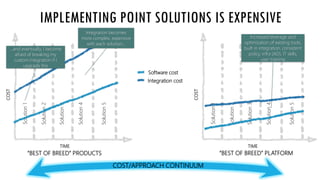
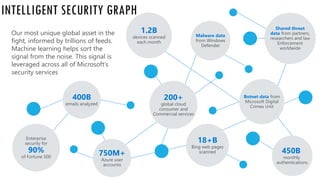
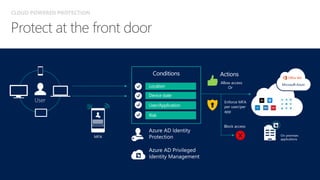
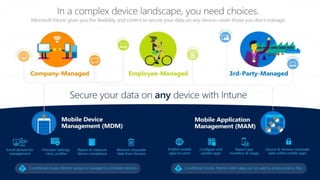
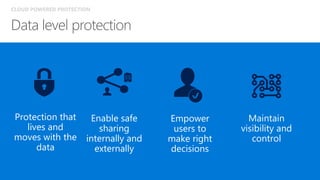
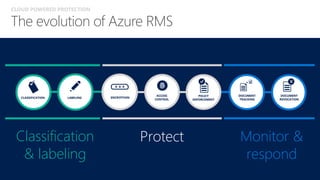
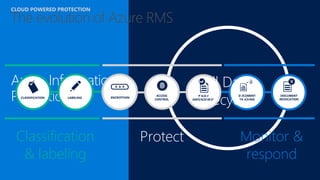
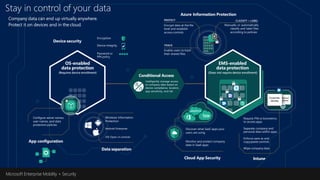
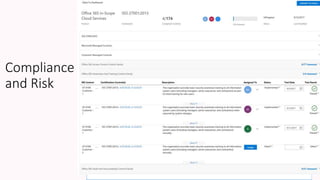
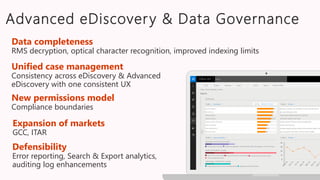
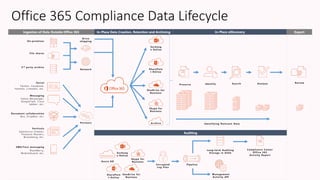
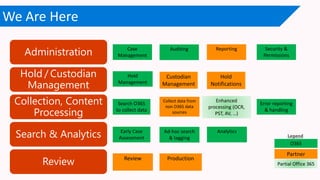
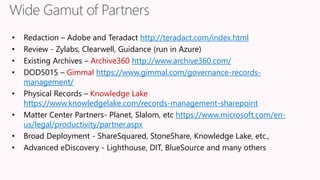
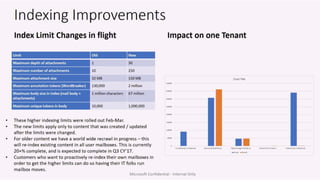
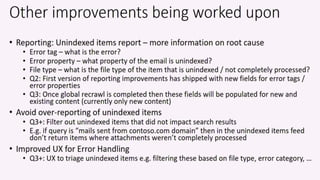
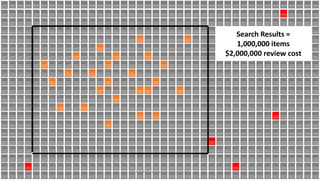
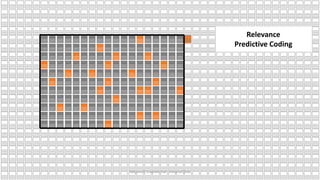
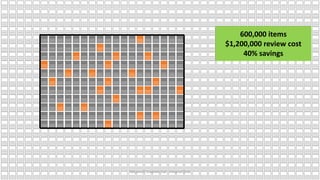
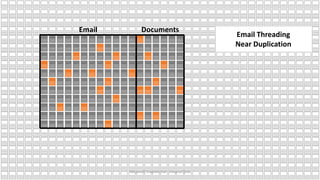
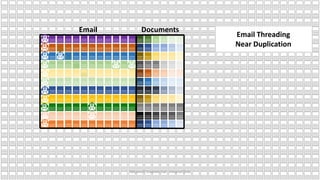
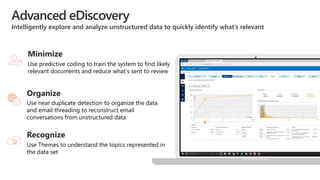
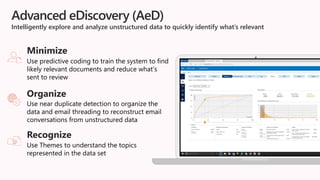
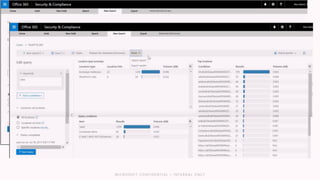
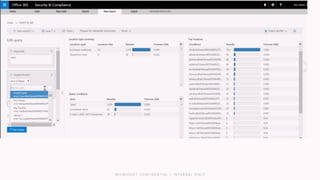
The document discusses the increasing cybersecurity threats facing public sector organizations, highlighting that they are often targeted by profit-motivated adversaries, resulting in significant breach costs and a shortage of trained cybersecurity professionals. It argues for the adoption of integrated, policy-driven security platforms and leveraging hyperscale cloud technologies to reduce complexity and enhance response capabilities. Additionally, it outlines various Microsoft security solutions and approaches for data protection, access control, and advanced e-discovery practices.