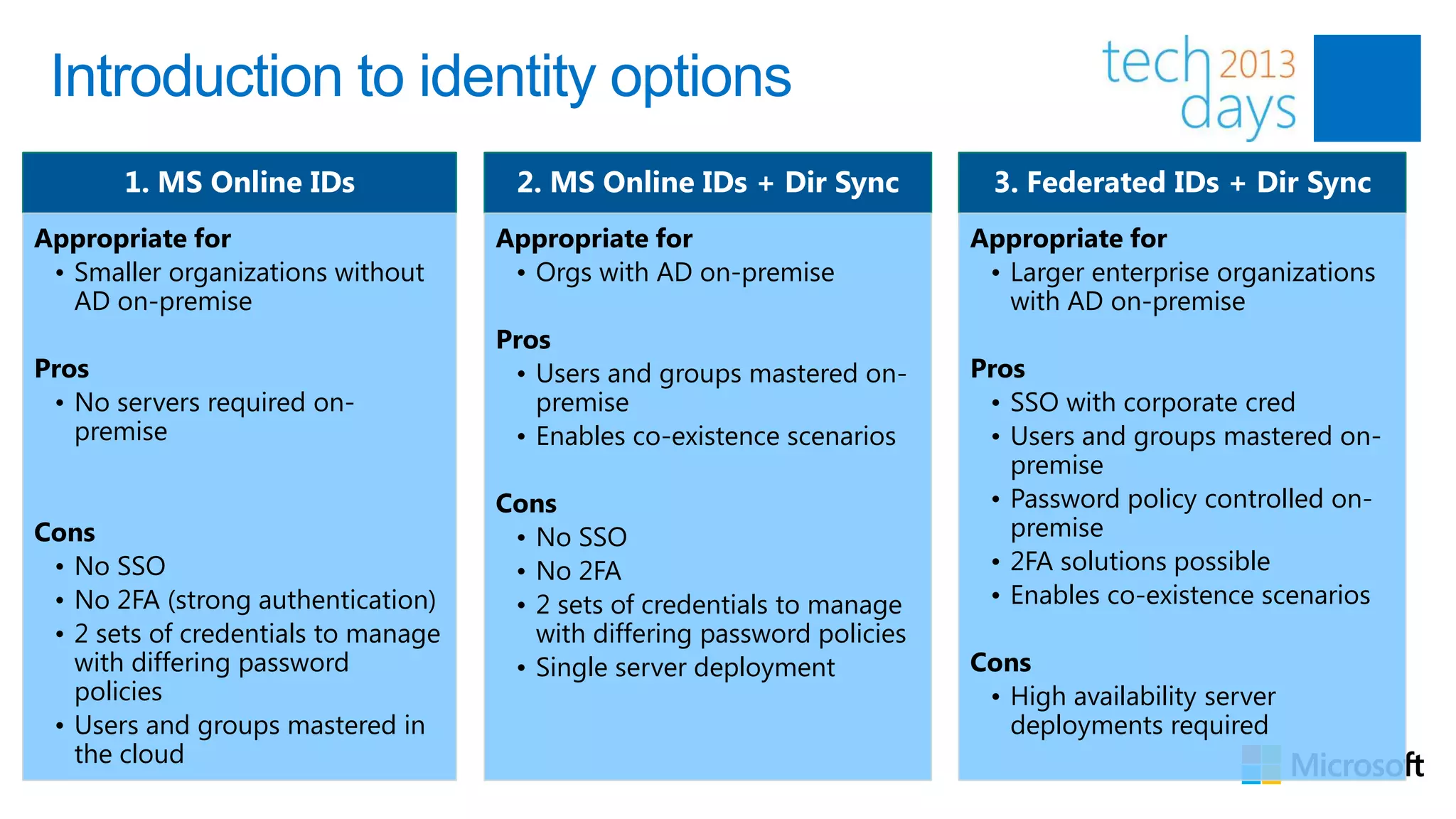
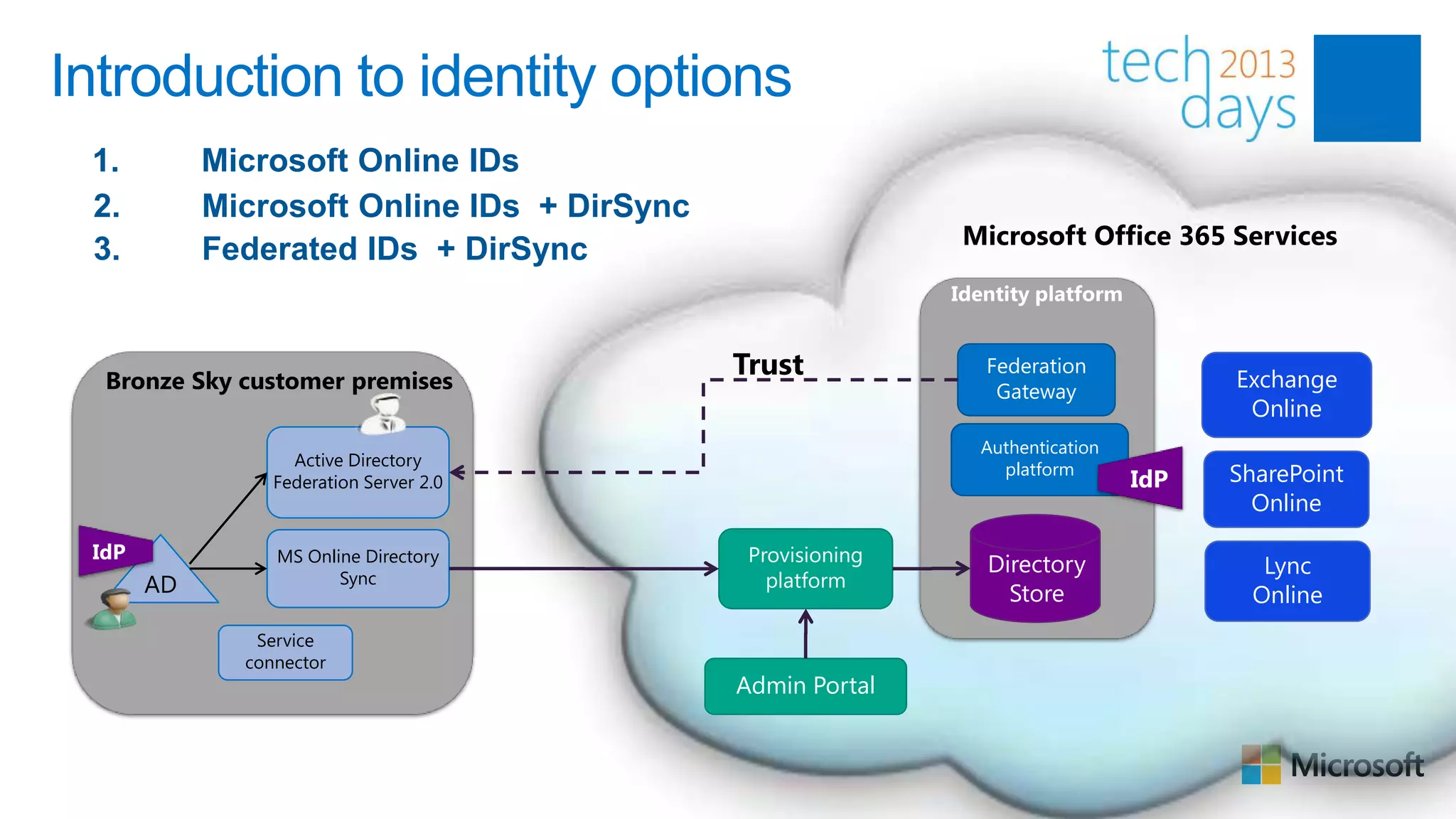
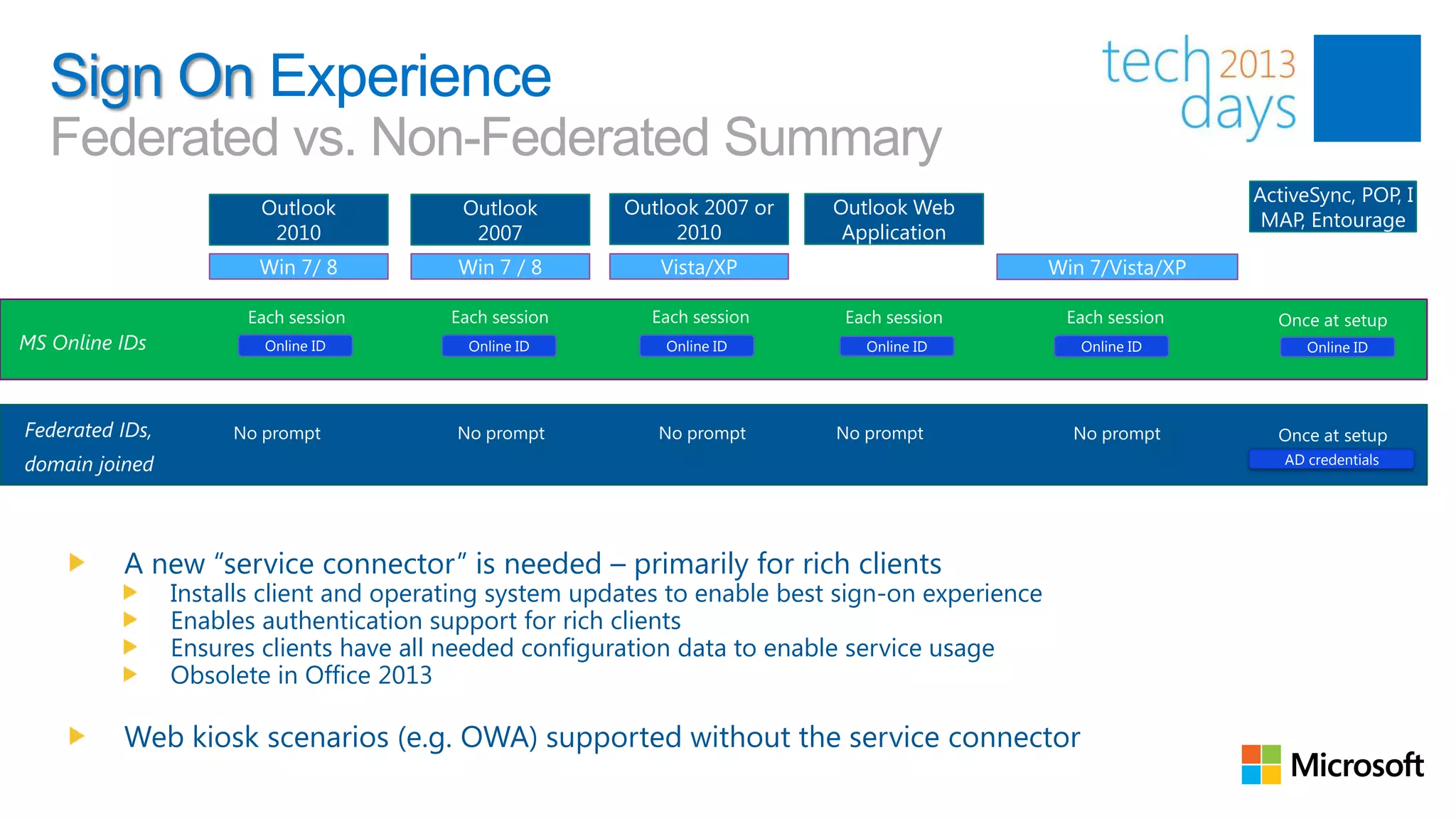
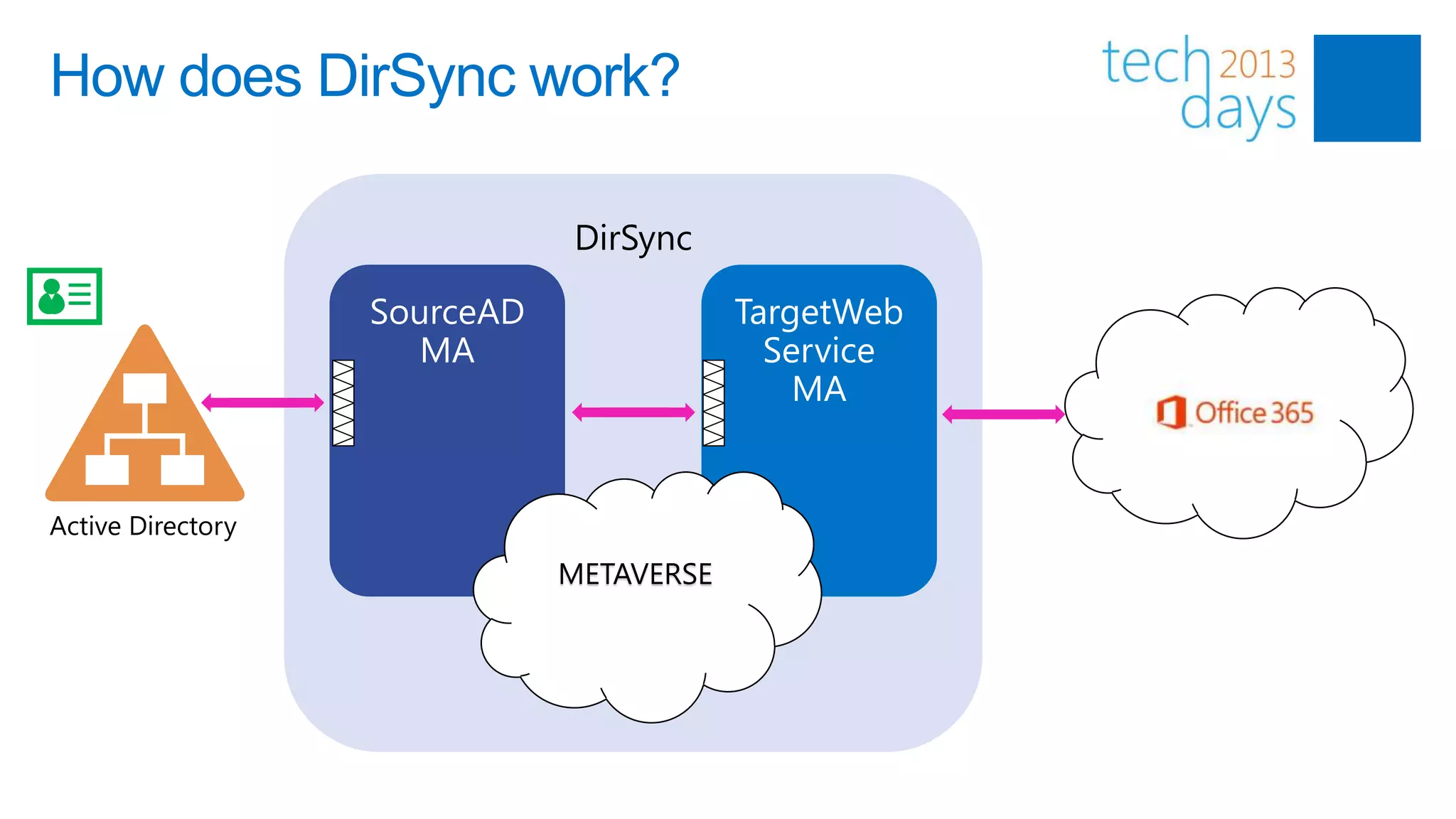
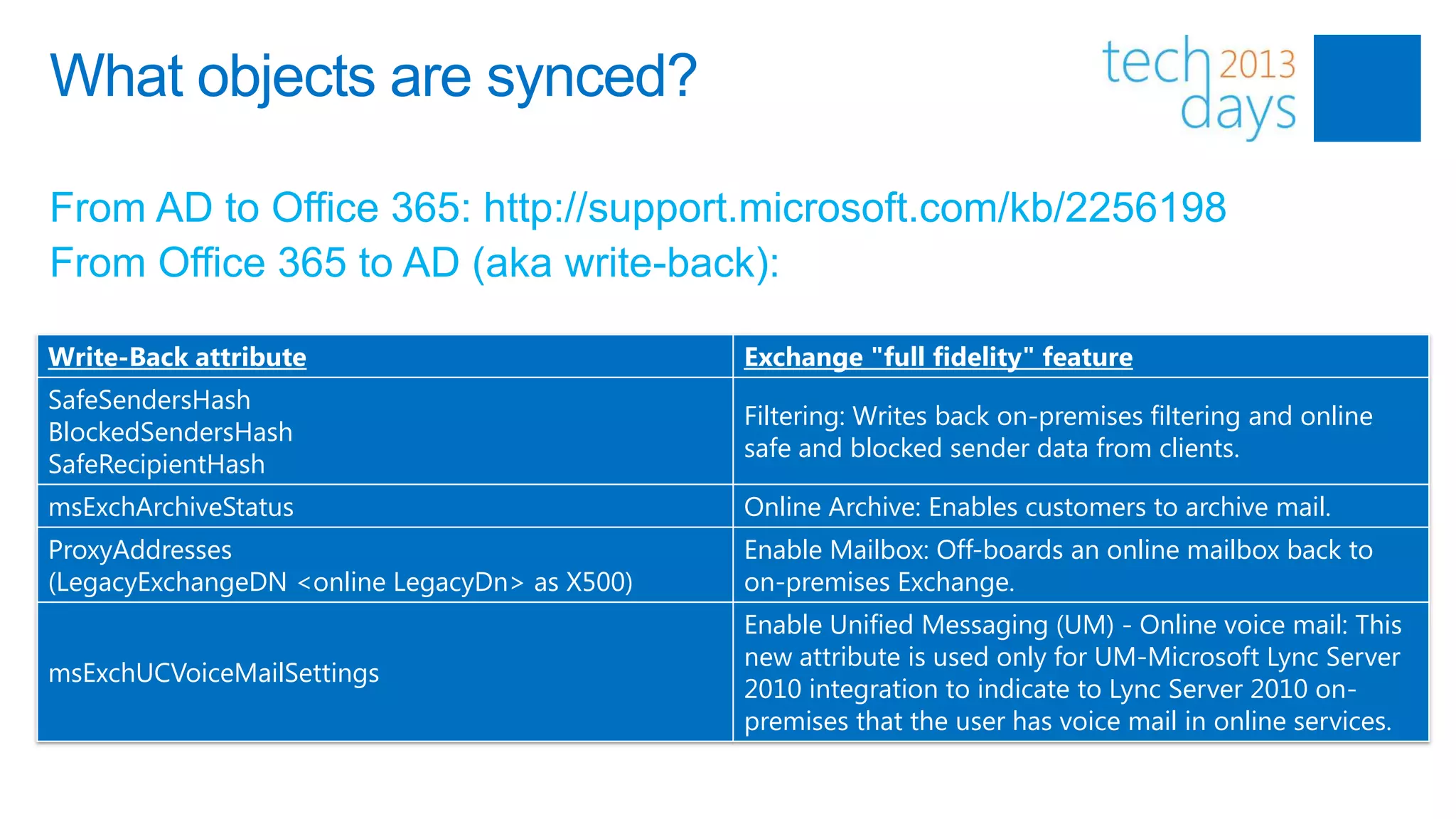
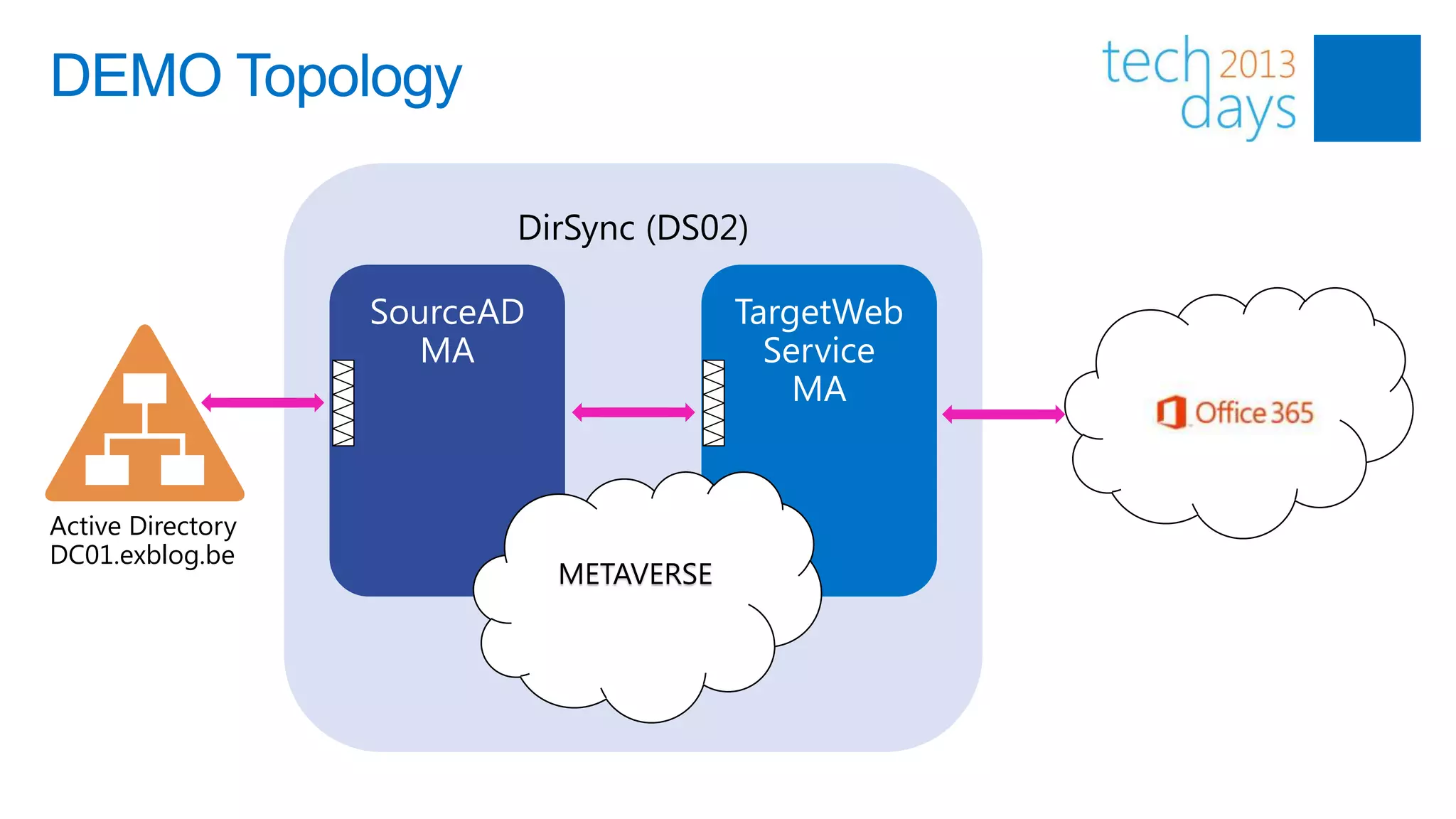
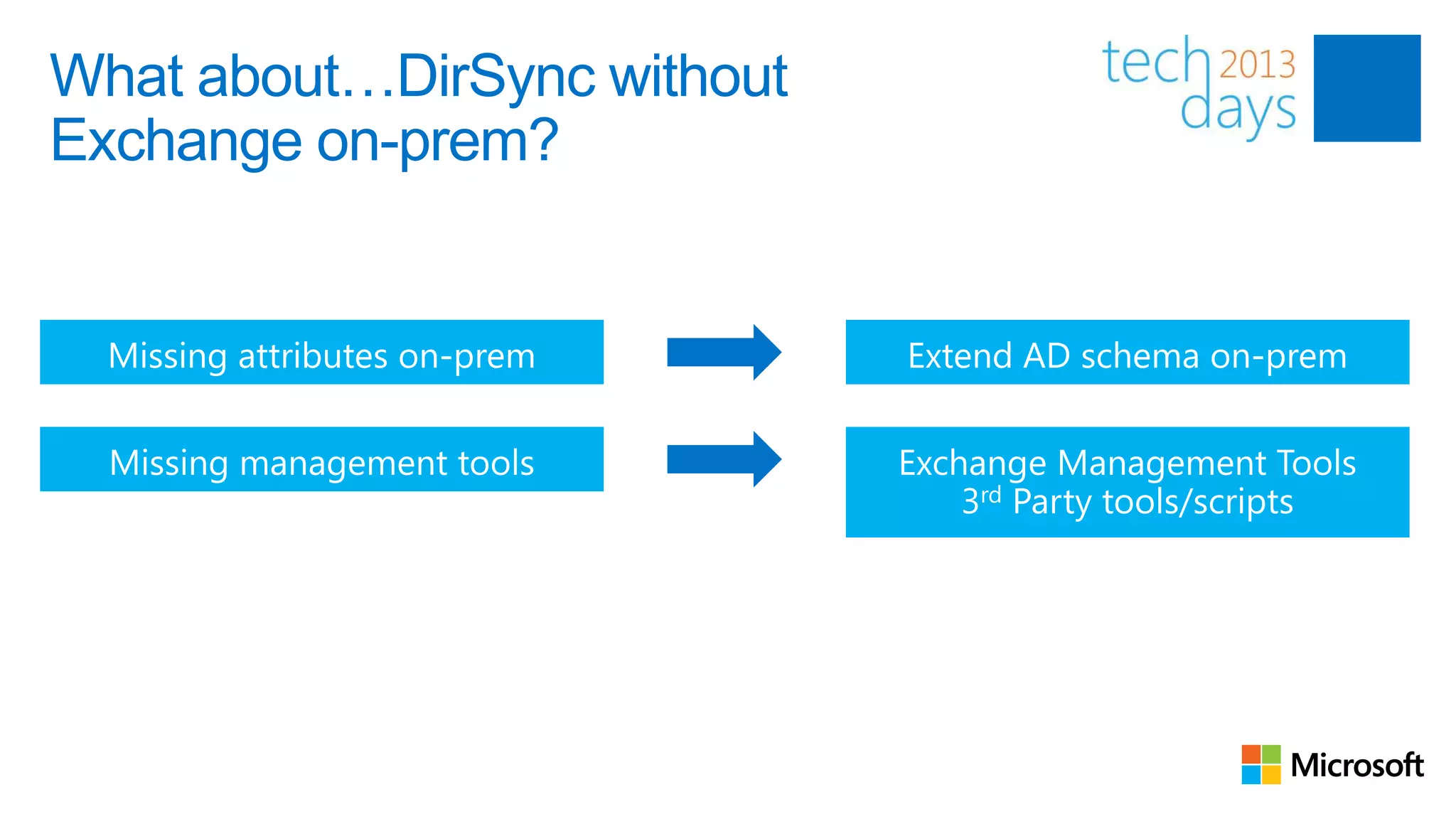
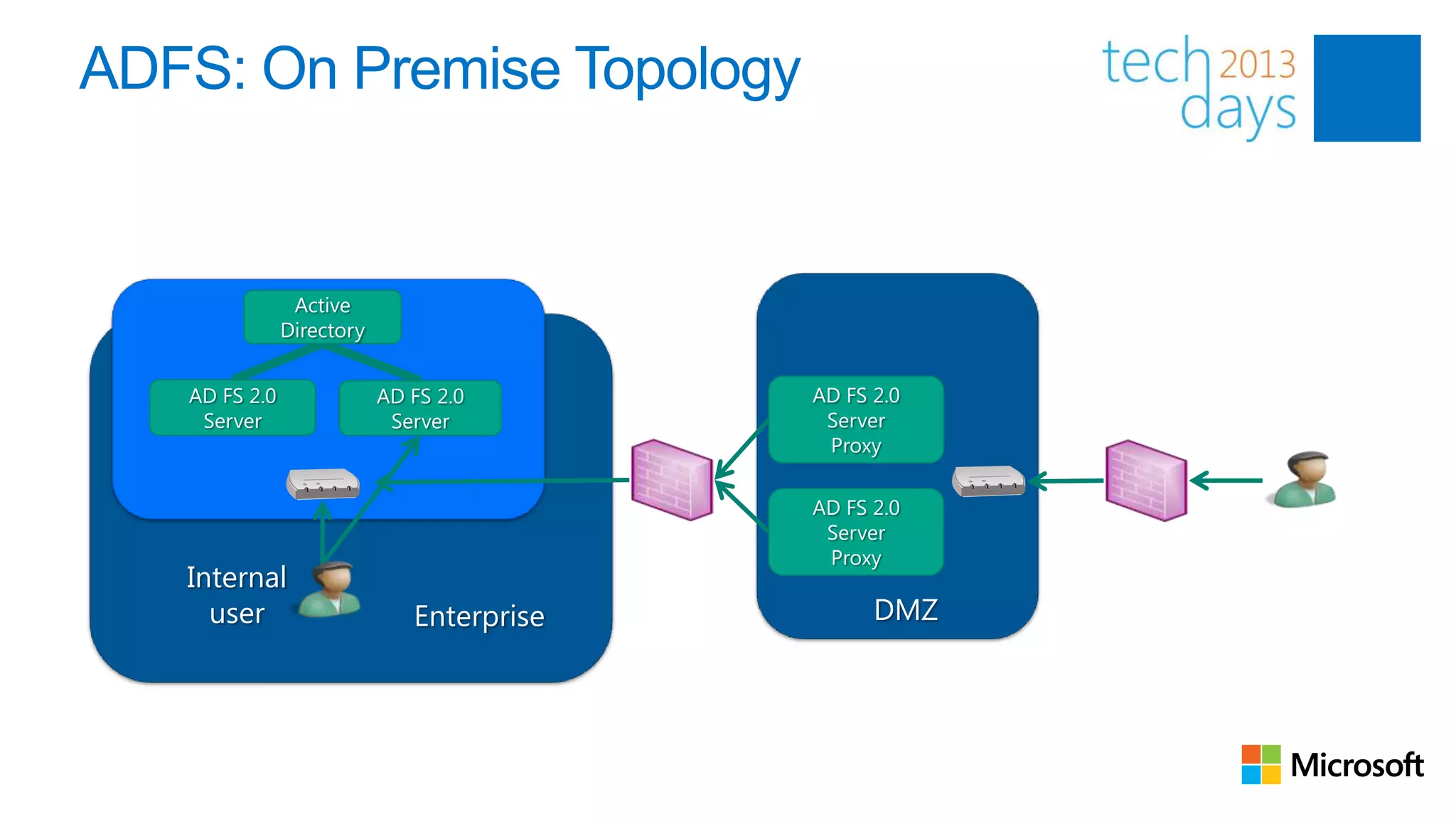
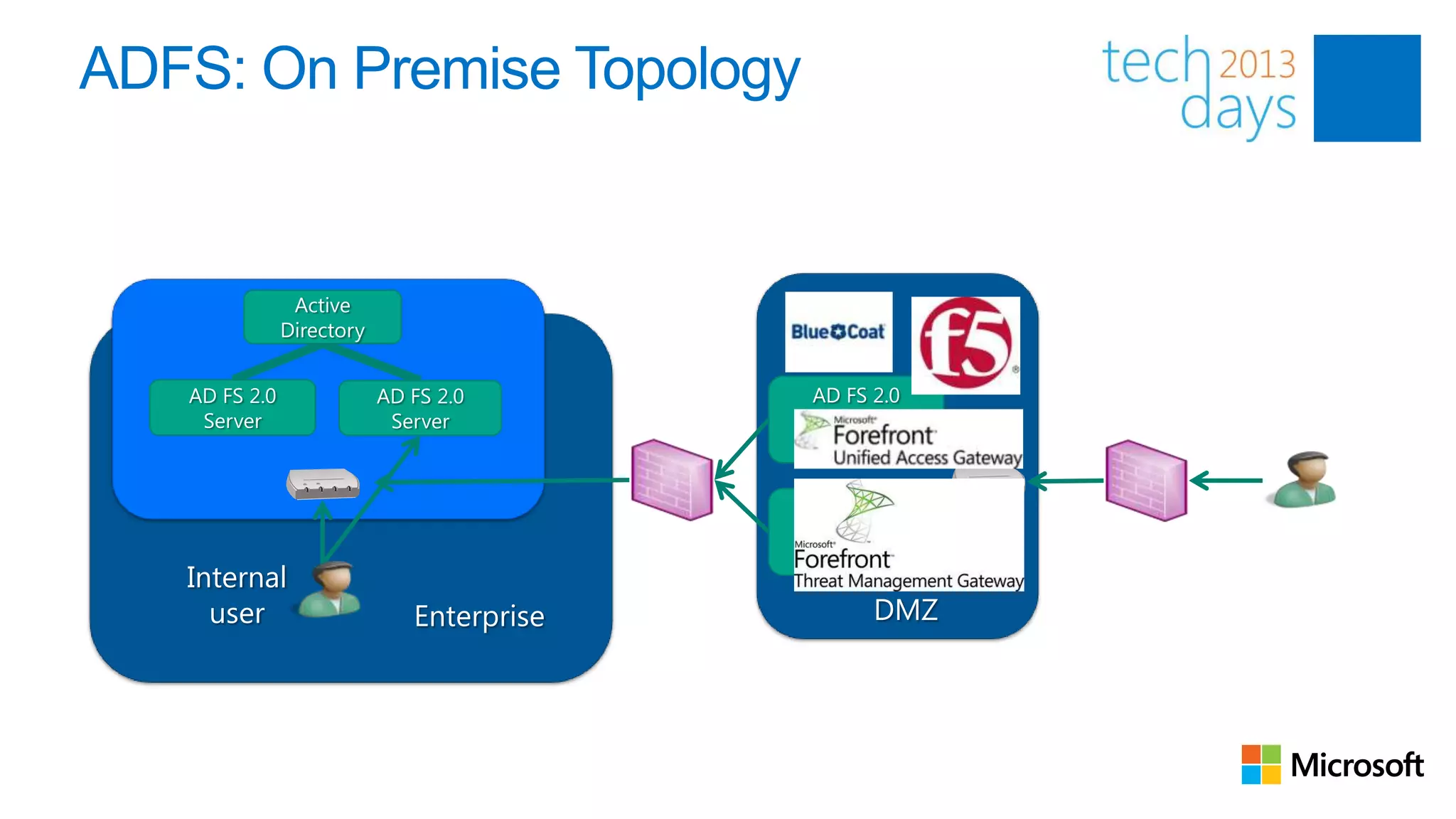
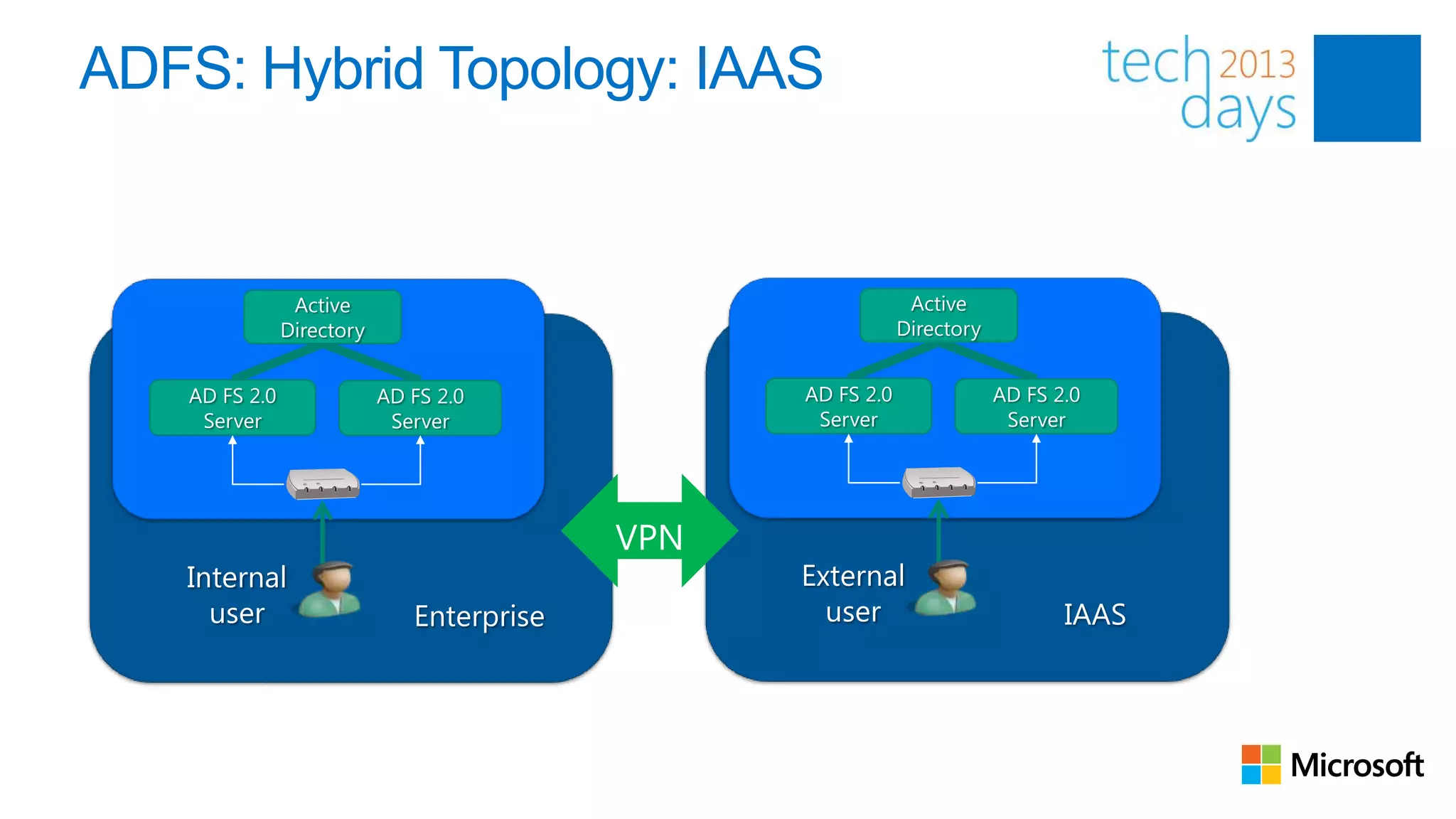
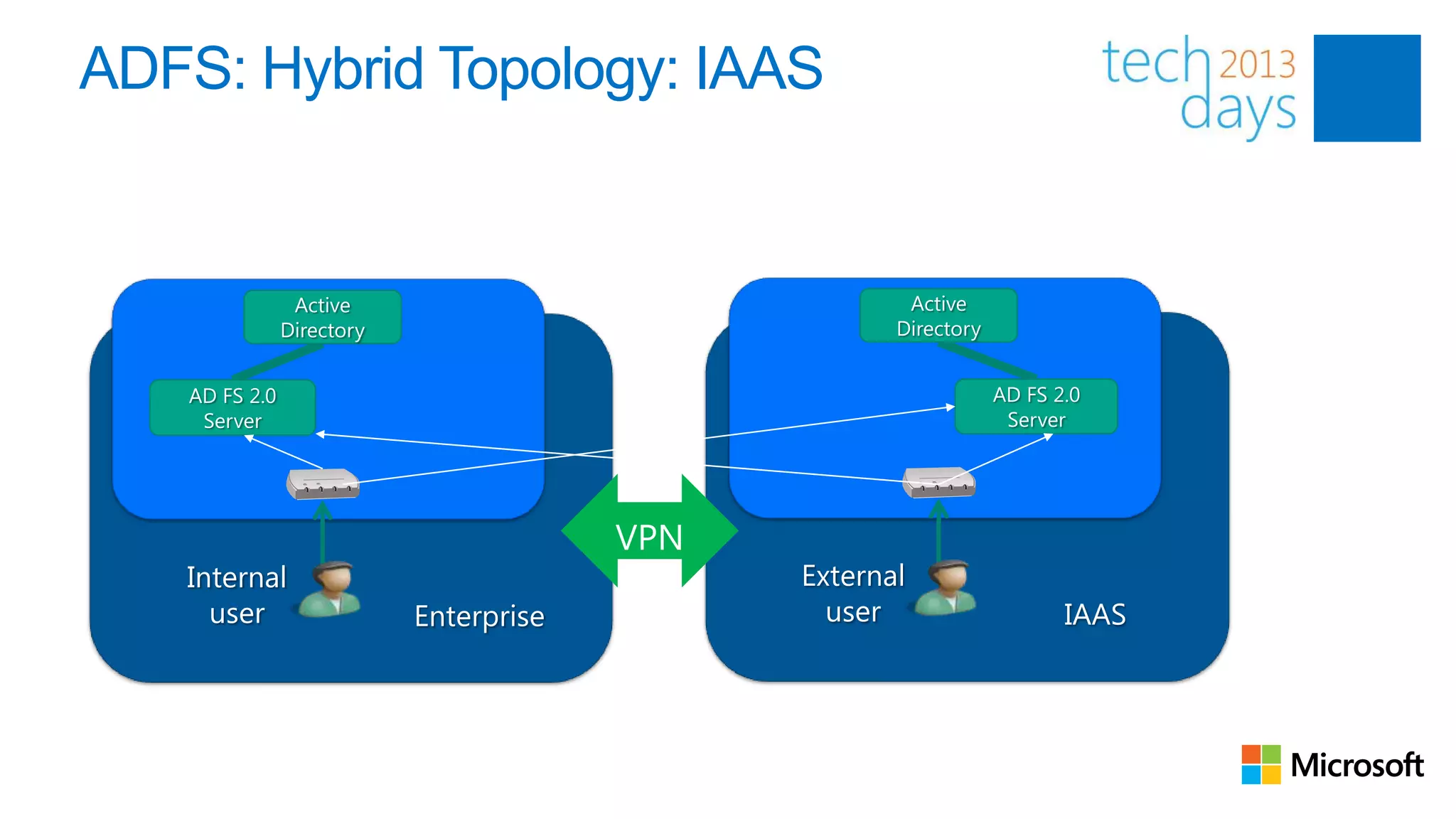
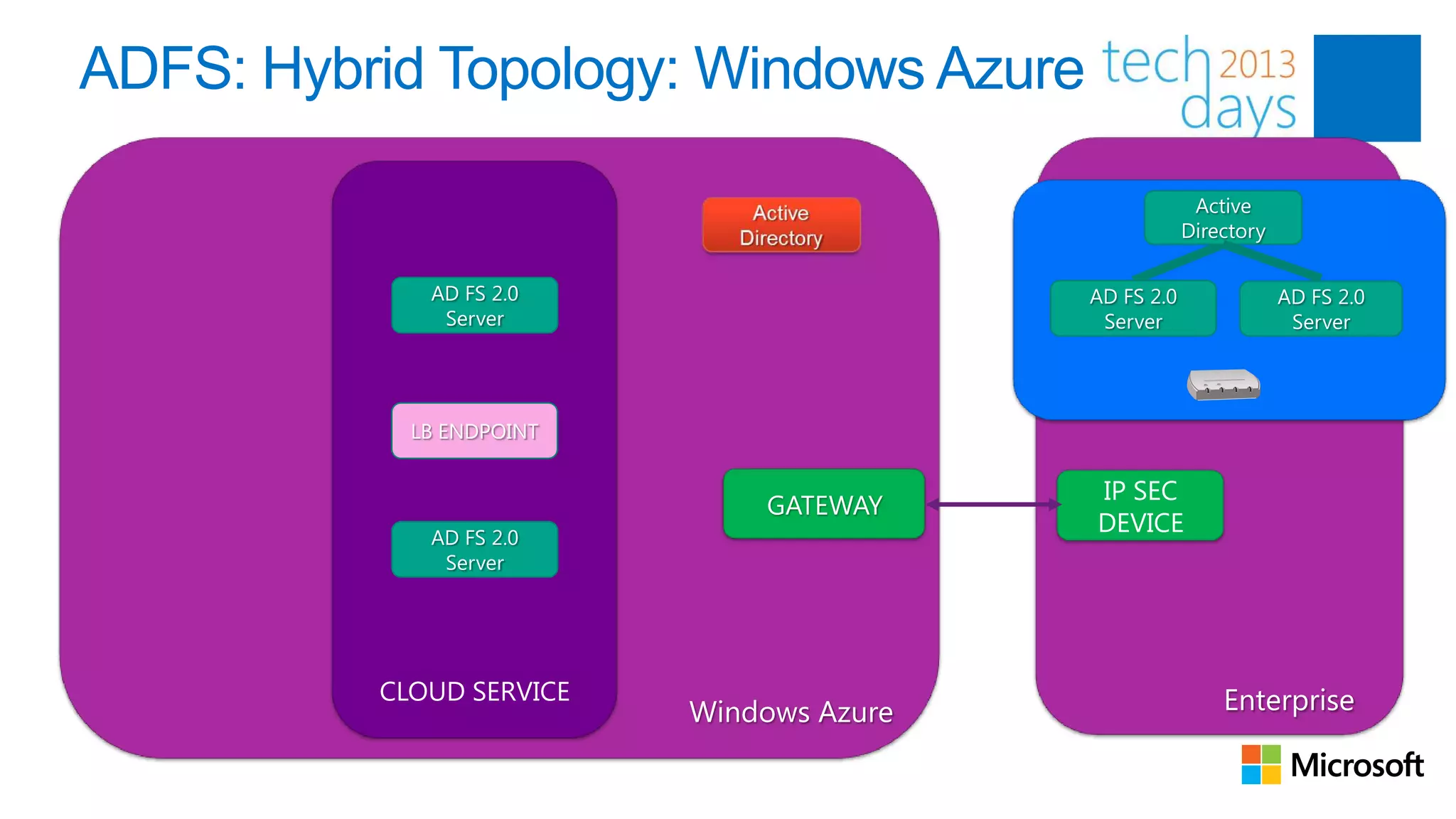
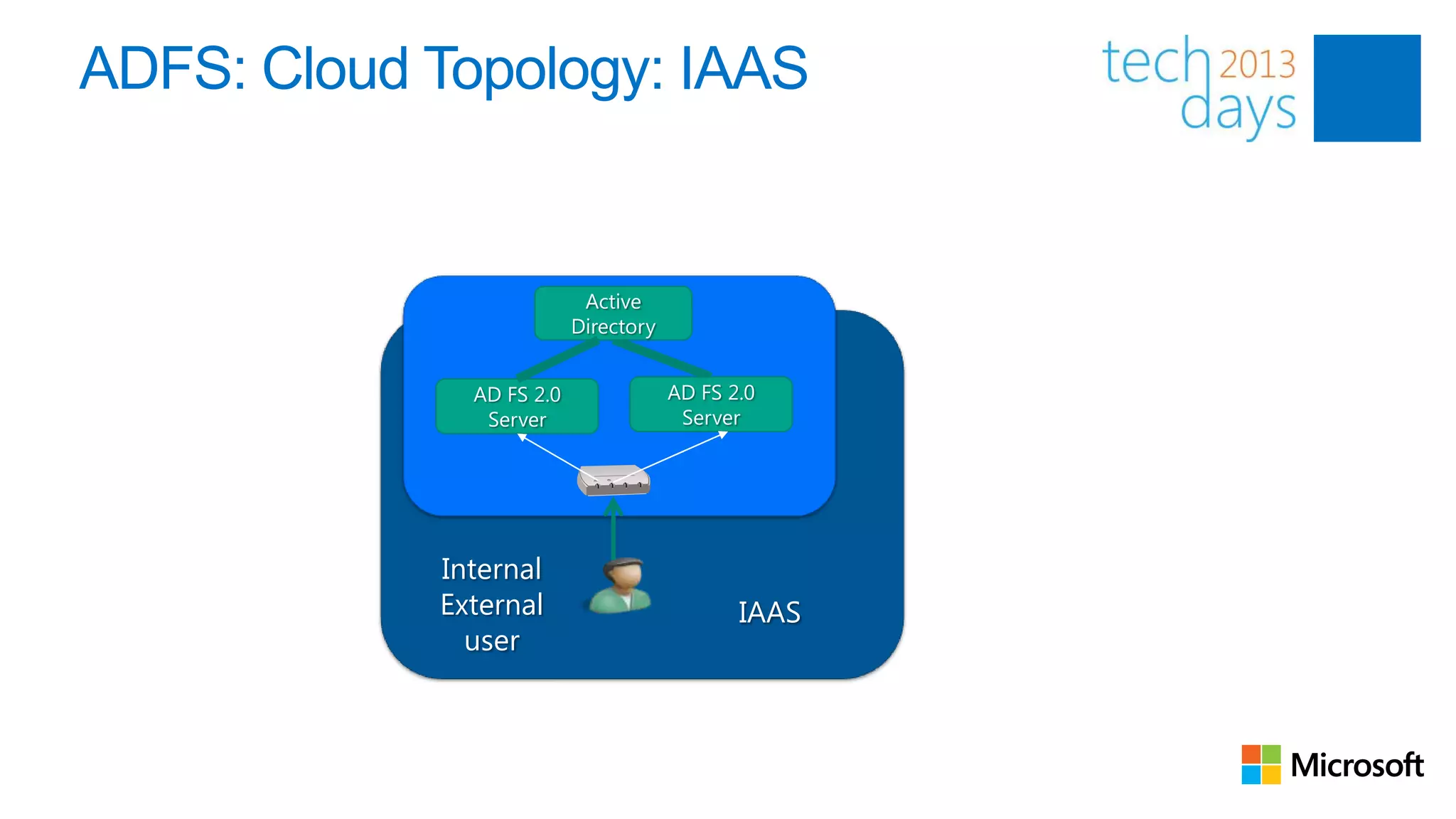
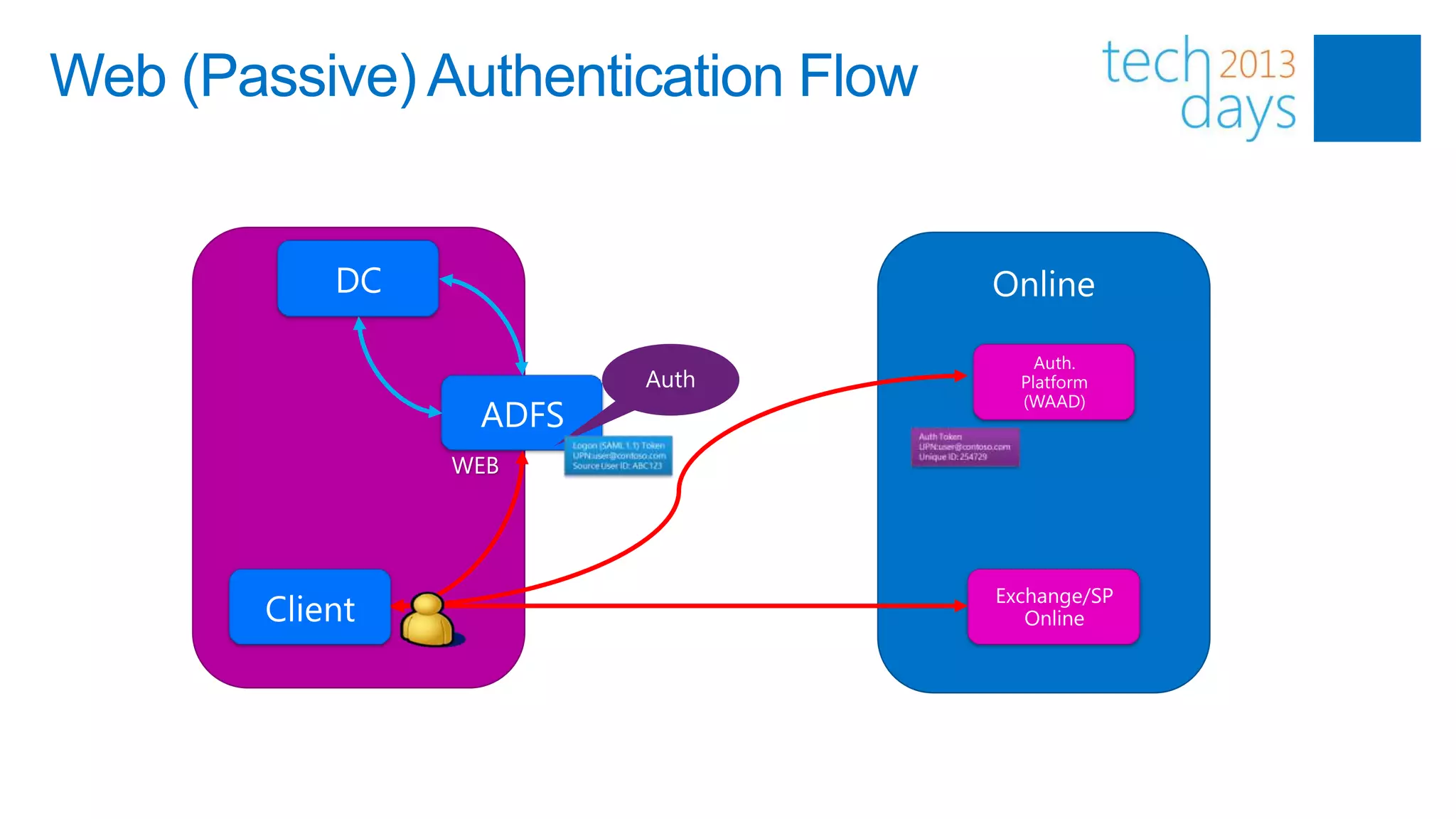
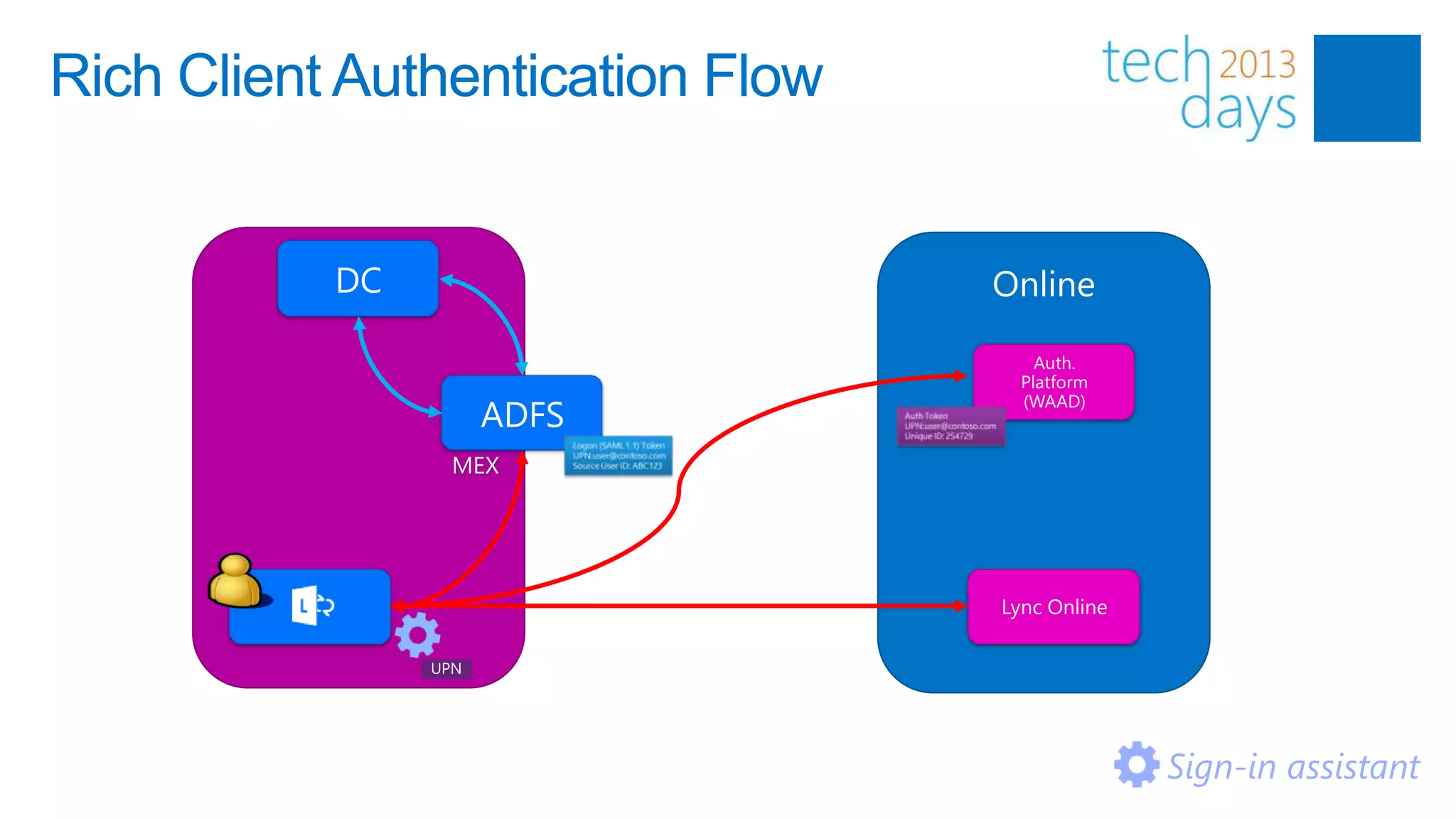
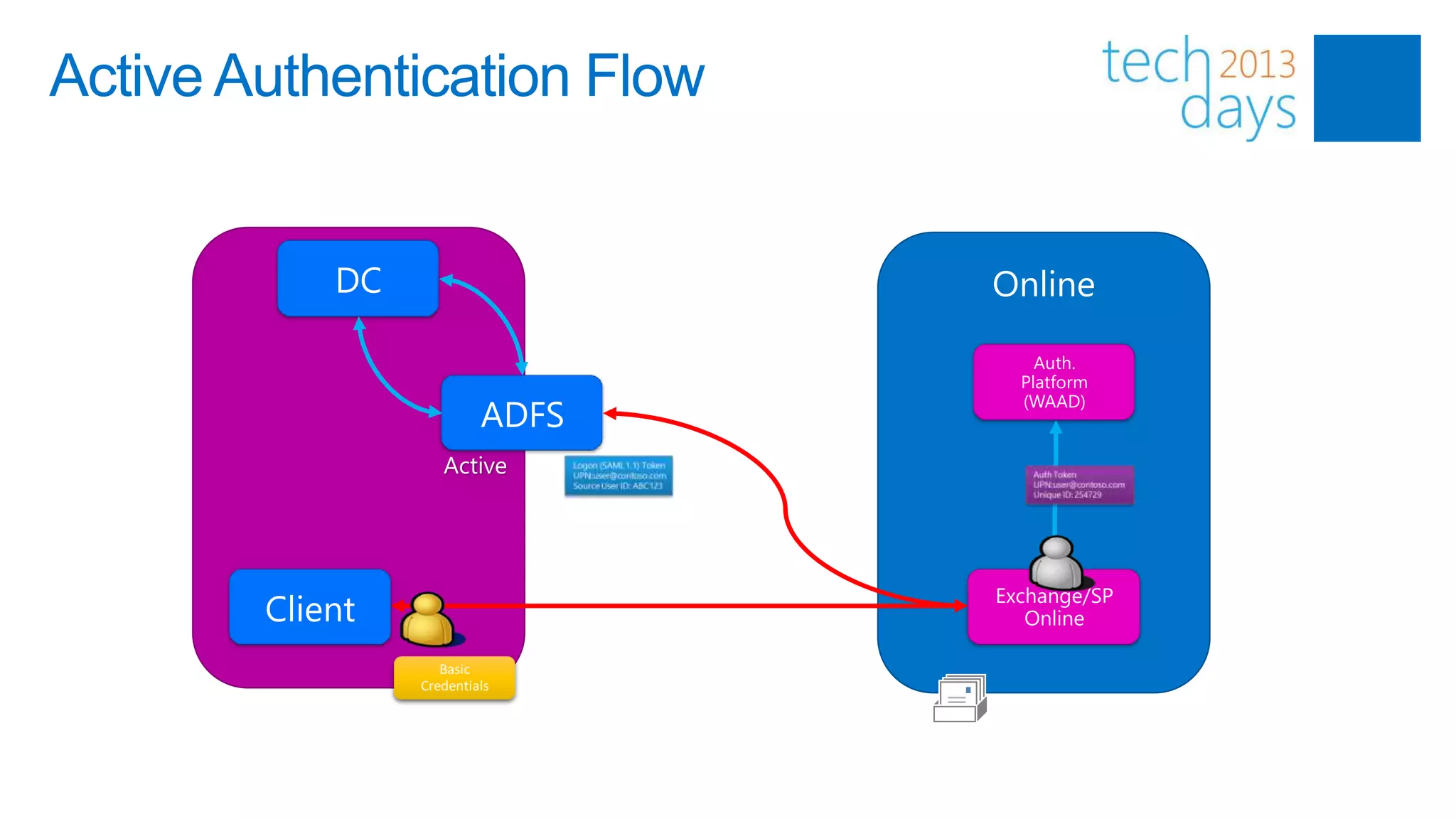
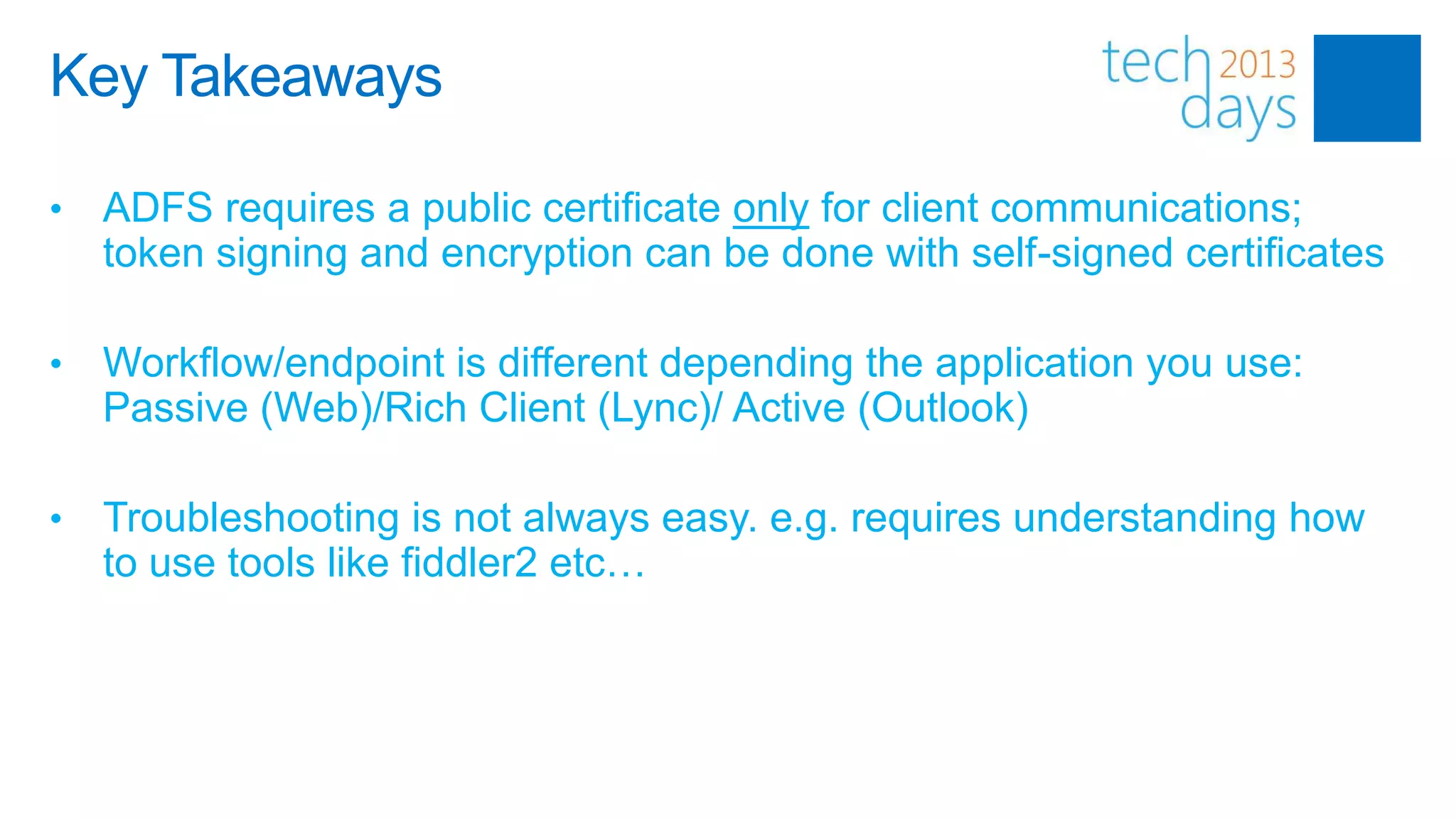
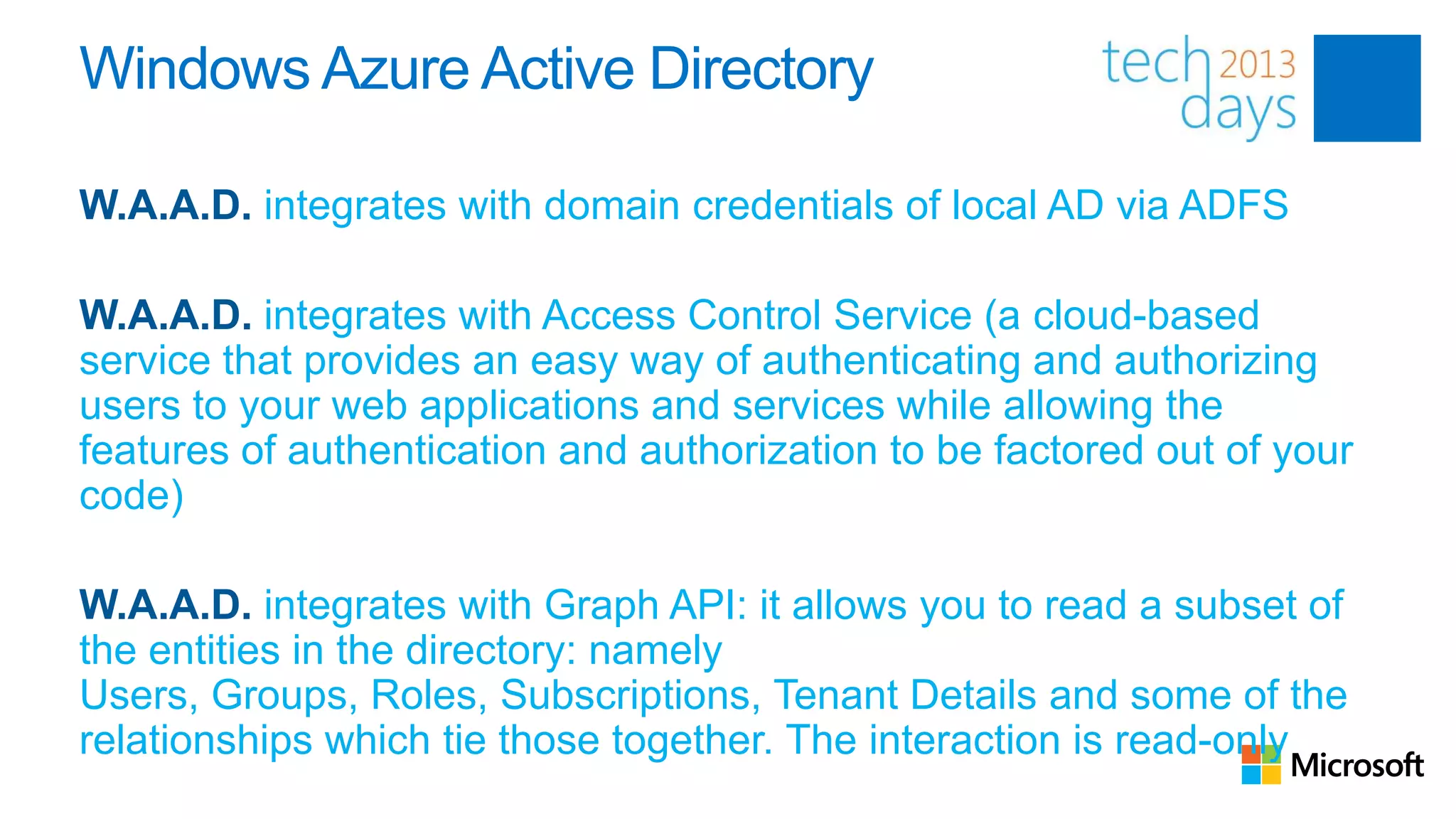
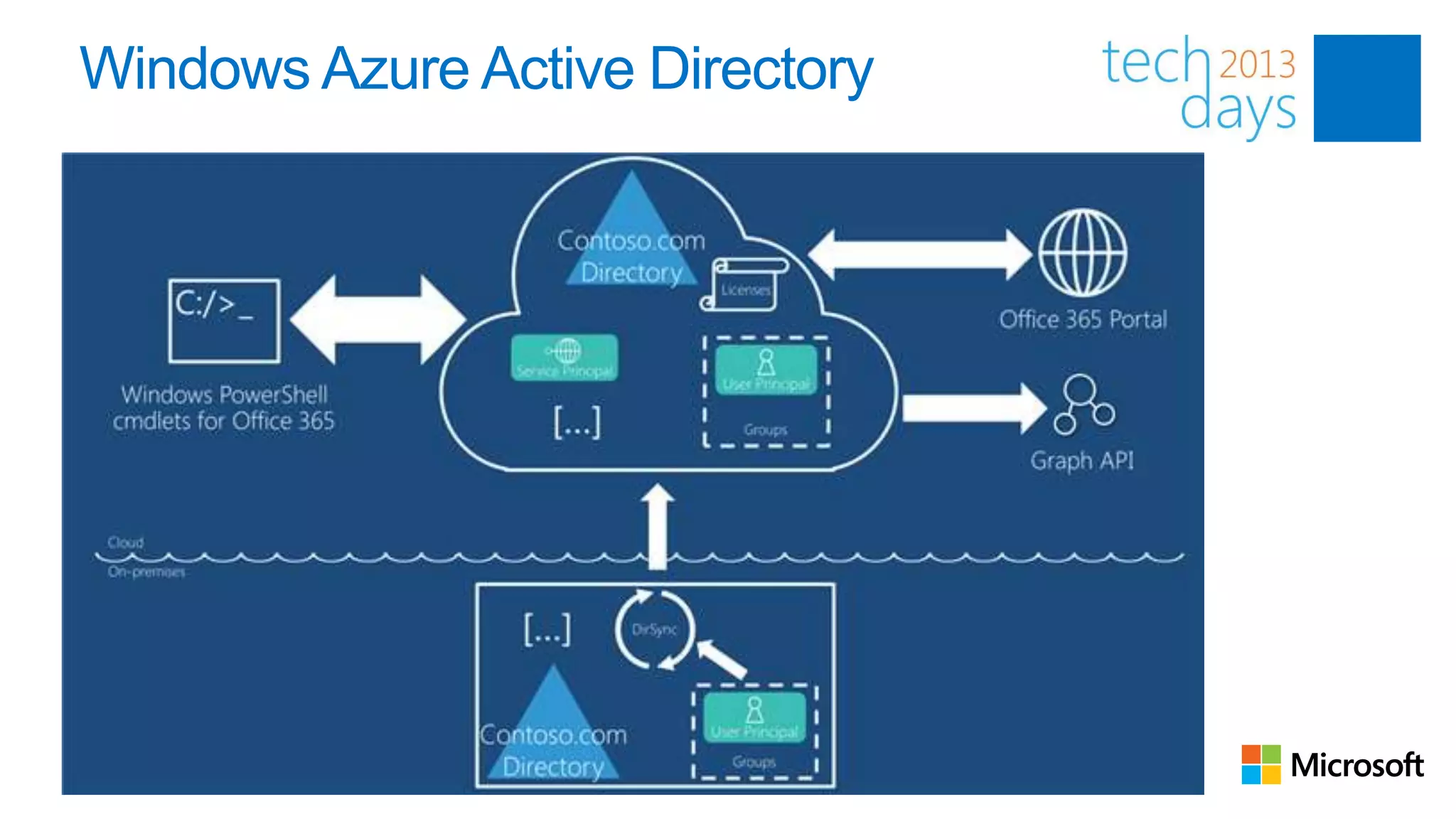
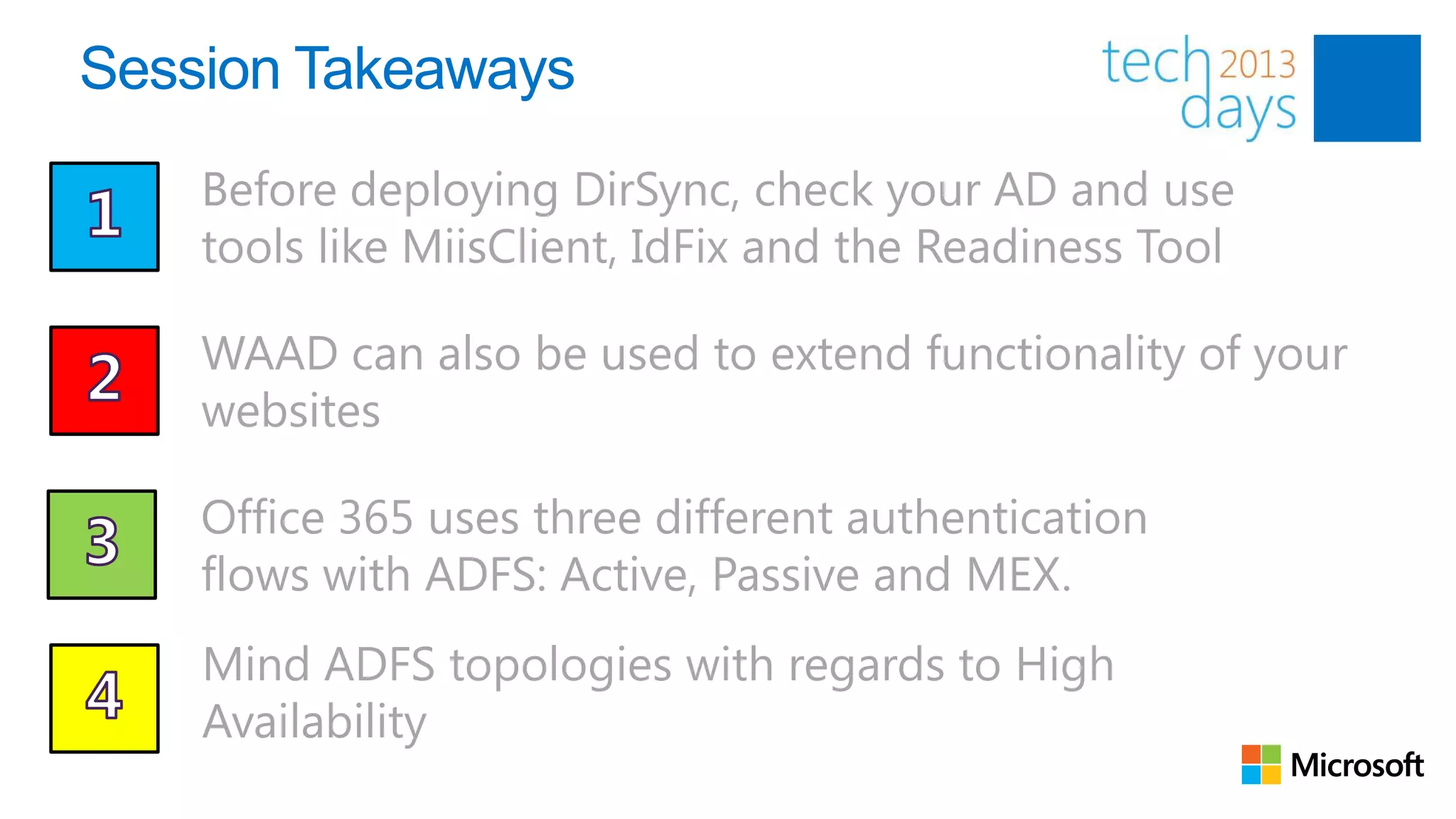
This document discusses identity and authentication options for Office 365. It covers Directory Synchronization (DirSync) which synchronizes on-premises Active Directory with Azure Active Directory. It also discusses Active Directory Federation Services (ADFS) which provides single sign-on for federated identities and different ADFS topologies including on-premises, hybrid and cloud. Additionally, it covers Windows Azure Active Directory and how it can be used to provide identity services for cloud applications. The key takeaways are to check Active Directory health before using DirSync, understand the different Office 365 authentication flows with ADFS, and that WAAD can extend identity functionality to websites.