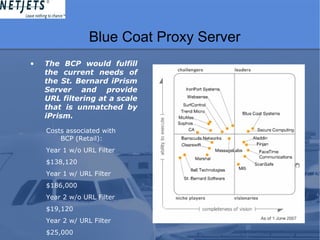
This document summarizes a presentation on preventing data leakage. It defines data leakage and data loss prevention. It identifies gaps in the company's current security measures, including a lack of mechanisms to capture sensitive data. It evaluates vendors that could address this gap, selecting Vontu. It discusses Vontu products that could protect data in motion and meet pricing estimates. It recommends additionally implementing Blue Coat Proxy to handle network loads and provide URL filtering to support the Vontu solution.