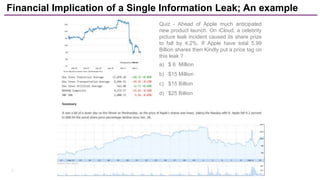
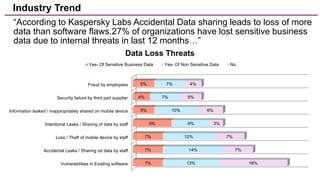
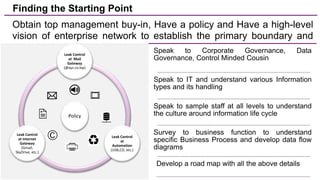
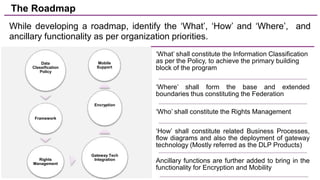
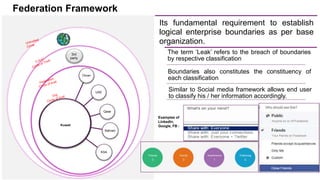
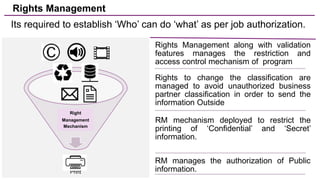
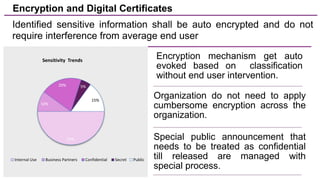
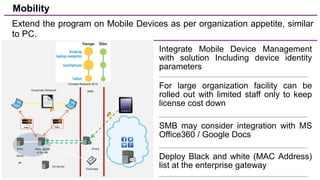
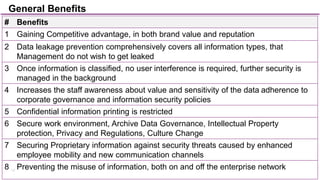
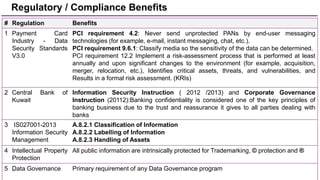
The document discusses trends in enterprise data leak prevention, highlighting that insider threats pose a greater risk than external hackers. It emphasizes the importance of an information classification policy and ancillary functions to effectively manage sensitive data and mitigate leaks. The text also outlines best practices for developing a comprehensive data leak prevention strategy, including obtaining management buy-in and integrating mobile device management.