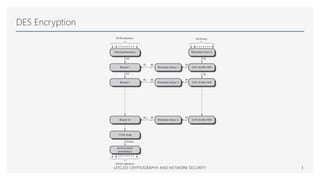
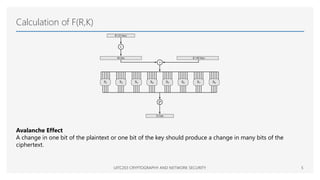
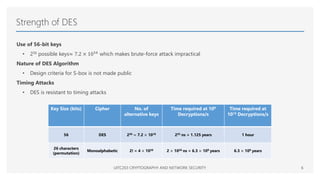
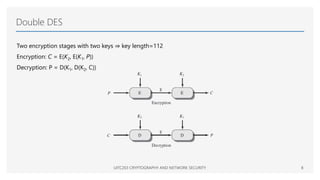
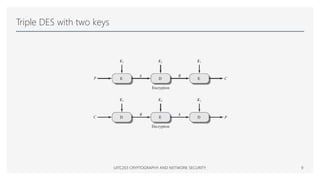
The document discusses the Data Encryption Standard (DES), a symmetric encryption algorithm introduced in 1977, which encrypts data in 64-bit blocks using a 56-bit key. It highlights the strength of DES against brute-force attacks and timing attacks, along with its various modes of operation and extensions like double and triple DES. References for further reading on cryptography and network security are also provided.