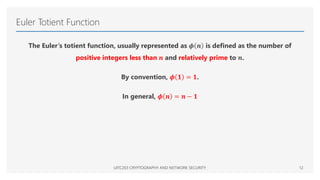
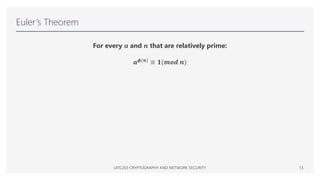
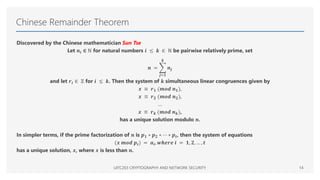
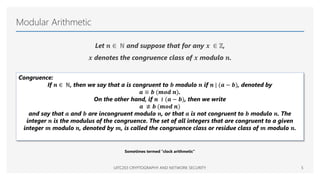
The document provides an overview of mathematical foundations essential to cryptography and network security, covering topics such as divisibility, modular arithmetic, the Euclidean algorithm, and prime numbers. It explains key concepts like the division algorithm, relative primality, Fermat's theorem, Euler's theorem, and the Chinese remainder theorem. Various algorithms are detailed, including the extended Euclidean algorithm for finding greatest common divisors.




![Euclidean Algorithm
Let 𝒂, 𝒃 ∈ ℤ (𝒂 ≥ 𝒃 > 𝟎), and set 𝒂 = 𝒓−𝟏, 𝒃 = 𝒓 𝟎. By repeatedly applying the Division
Algorithm, we get 𝒓𝒋−𝟏 = 𝒓𝒋 𝒒𝒋+𝟏 + 𝒓𝒋+𝟏 with 𝟎 < 𝒓𝒋+𝟏 < 𝒓𝒋 for all 𝟎 ≤ 𝒋 < 𝒏, where 𝒏 is the
least non-negative number such that 𝒓 𝒏+𝟏 = 𝟎, in which case 𝒈𝒄𝒅 𝒂, 𝒃 = 𝒓𝒏.
An equivalent definition: 𝒈𝒄𝒅 𝒂, 𝒃 = 𝒎𝒂𝒙 𝒌, 𝒔𝒖𝒄𝒉 𝒕𝒉𝒂𝒕 𝒌 𝒂 𝒂𝒏𝒅 𝒌 𝒃
A simpler form: Let 𝒂, 𝒃 > 𝟏 with 𝒃 ∤ 𝒂. Then,
gcd(𝒂, 𝒃) = gcd(𝒃, [𝒂 𝒎𝒐𝒅 𝒃])
UITC203 CRYPTOGRAPHY AND NETWORK SECURITY 6
The Euclidean algorithm GCD
Input: Integers 𝑎, 𝑏 with 𝑎 ≥ 𝑏 > 0
Output: The greatest common divisor
of 𝑎 and 𝑏
if 𝑏 𝑑𝑖𝑣𝑖𝑑𝑒𝑠 𝑎
return 𝑏
else
return 𝐺𝐶𝐷(𝑏, [𝑎 𝑚𝑜𝑑 𝑏])](https://image.slidesharecdn.com/week-3-200414011943/85/Mathematical-Foundations-of-Cryptography-6-320.jpg)