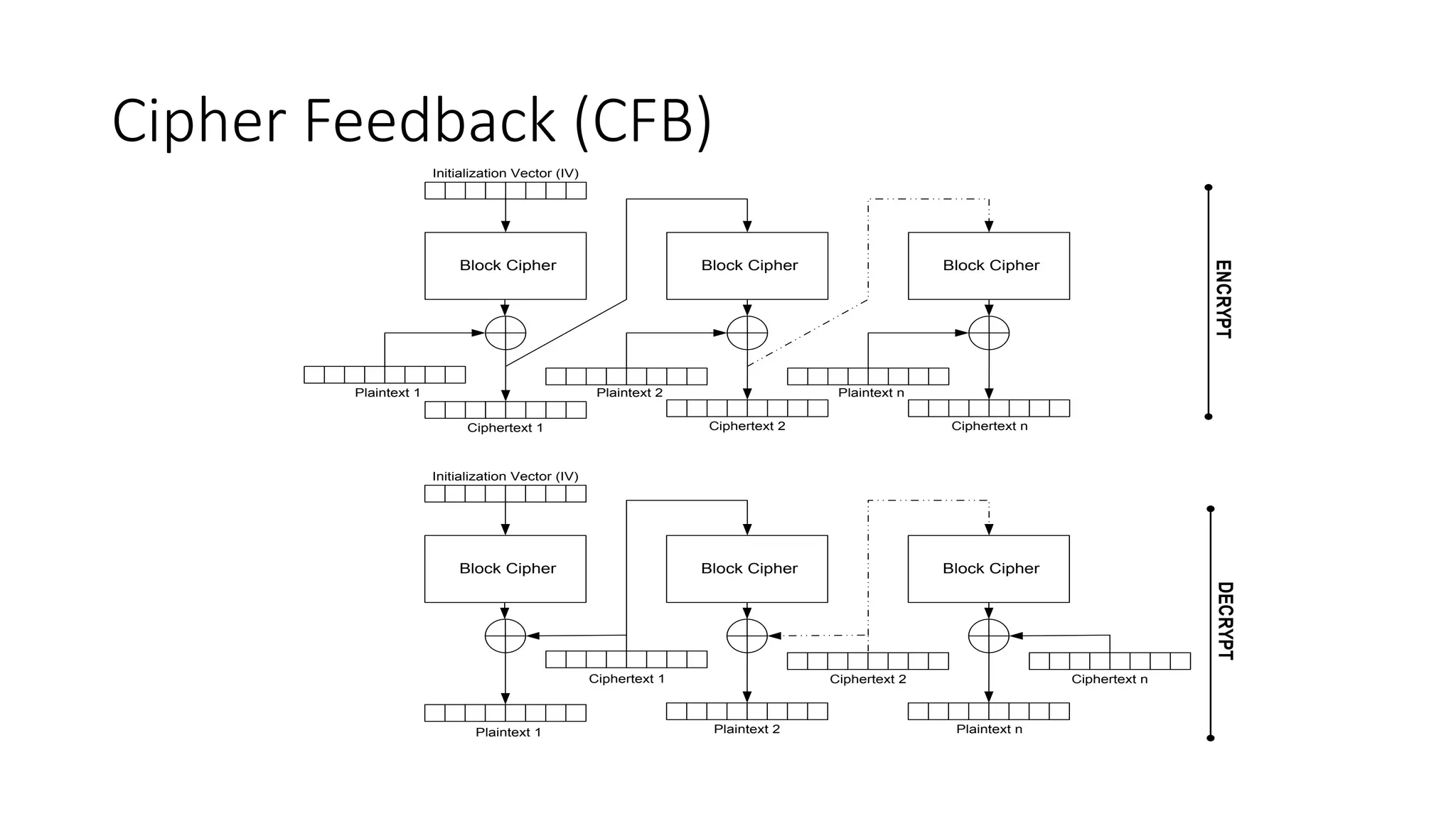
The document discusses authenticated encryption and the ASC-1 authenticated encryption stream cipher. It describes how authenticated encryption provides both confidentiality and authenticity. Generic composition methods for combining encryption and authentication are analyzed, but are not very efficient. ASC-1 performs encryption and authentication in a single pass using leak extraction from intermediate cipher rounds. Bits are leaked and XORed with the plaintext to generate the ciphertext. ASC-1 specification and decryption/encryption processes are also outlined.