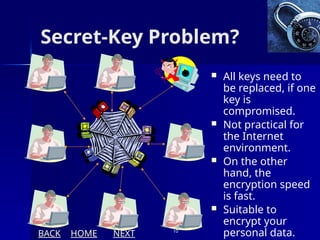
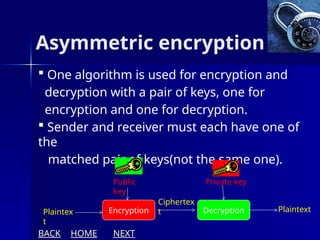
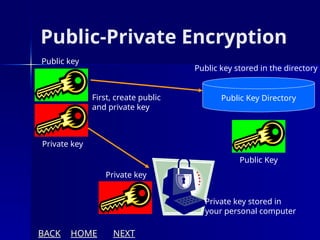
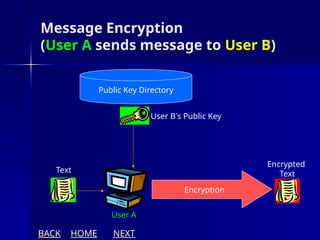
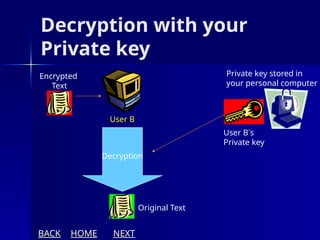
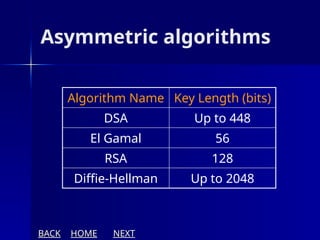
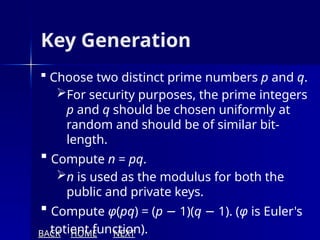
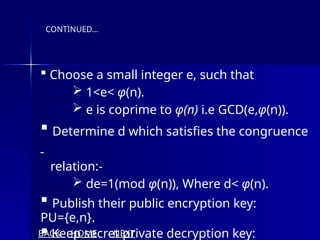
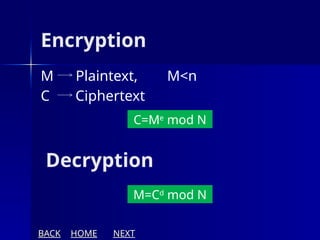
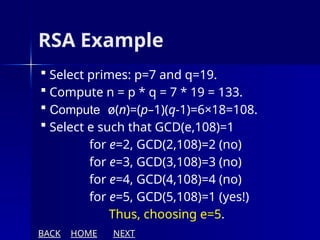
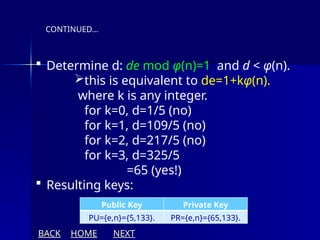
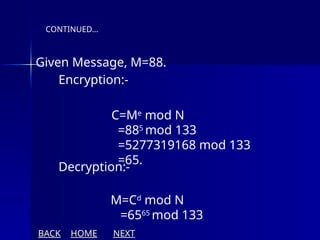
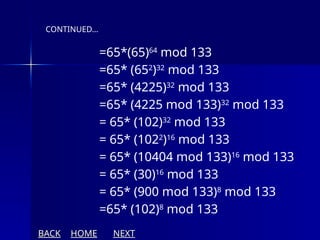
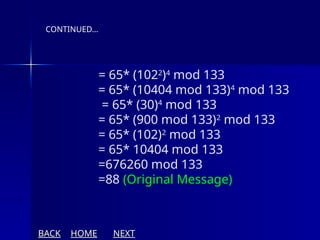
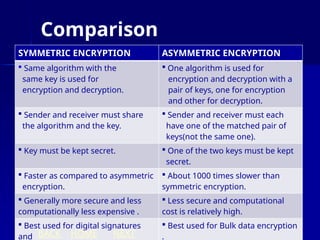
The document presents an overview of cryptography, specifically focusing on encryption and decryption methods, including symmetric (DES) and asymmetric (RSA) algorithms. It explains the fundamental concepts like plaintext, ciphertext, and the role of keys in data security, as well as the advantages and disadvantages of each encryption method. Additionally, it discusses key generation for RSA and its security considerations.