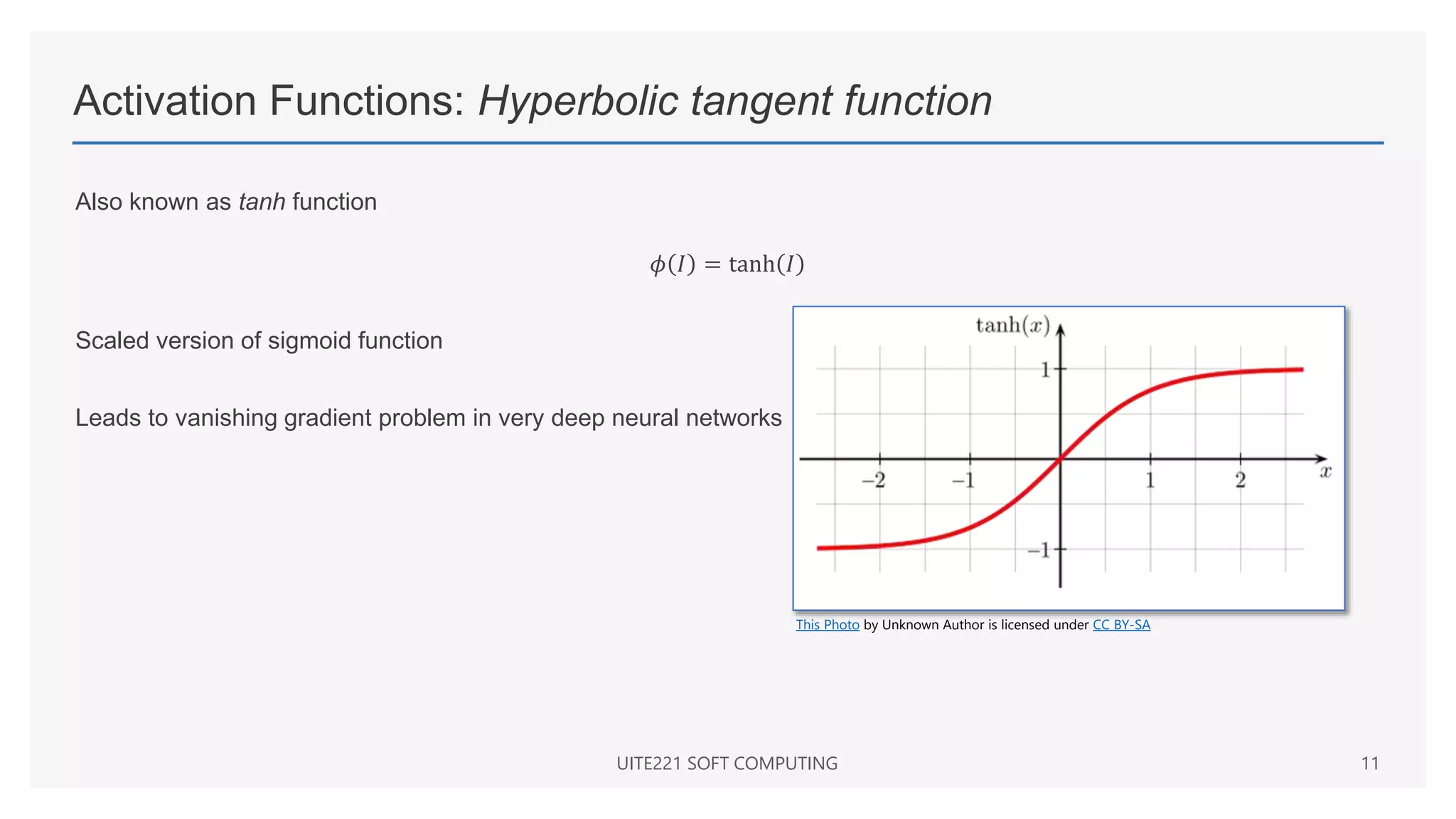
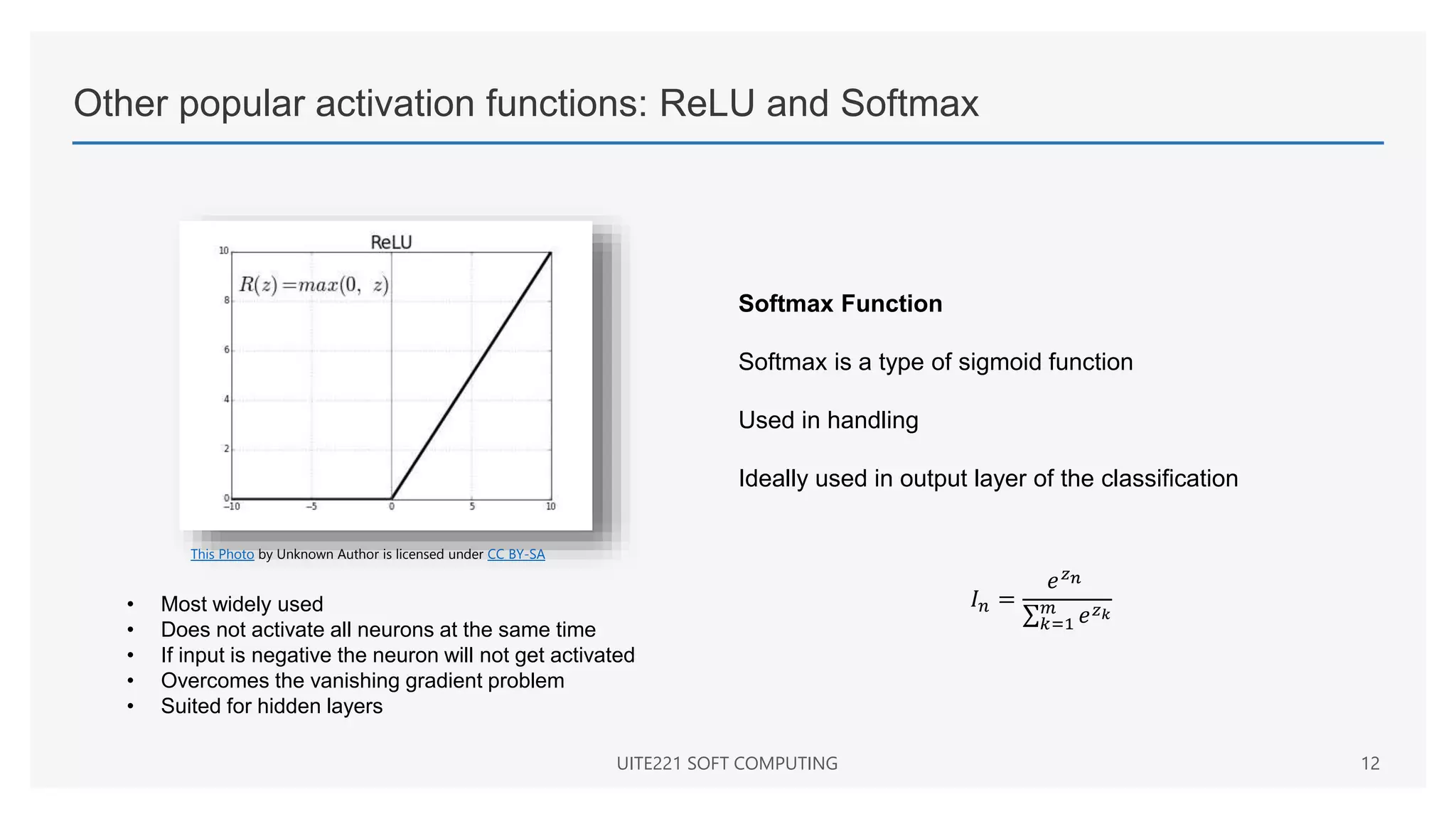
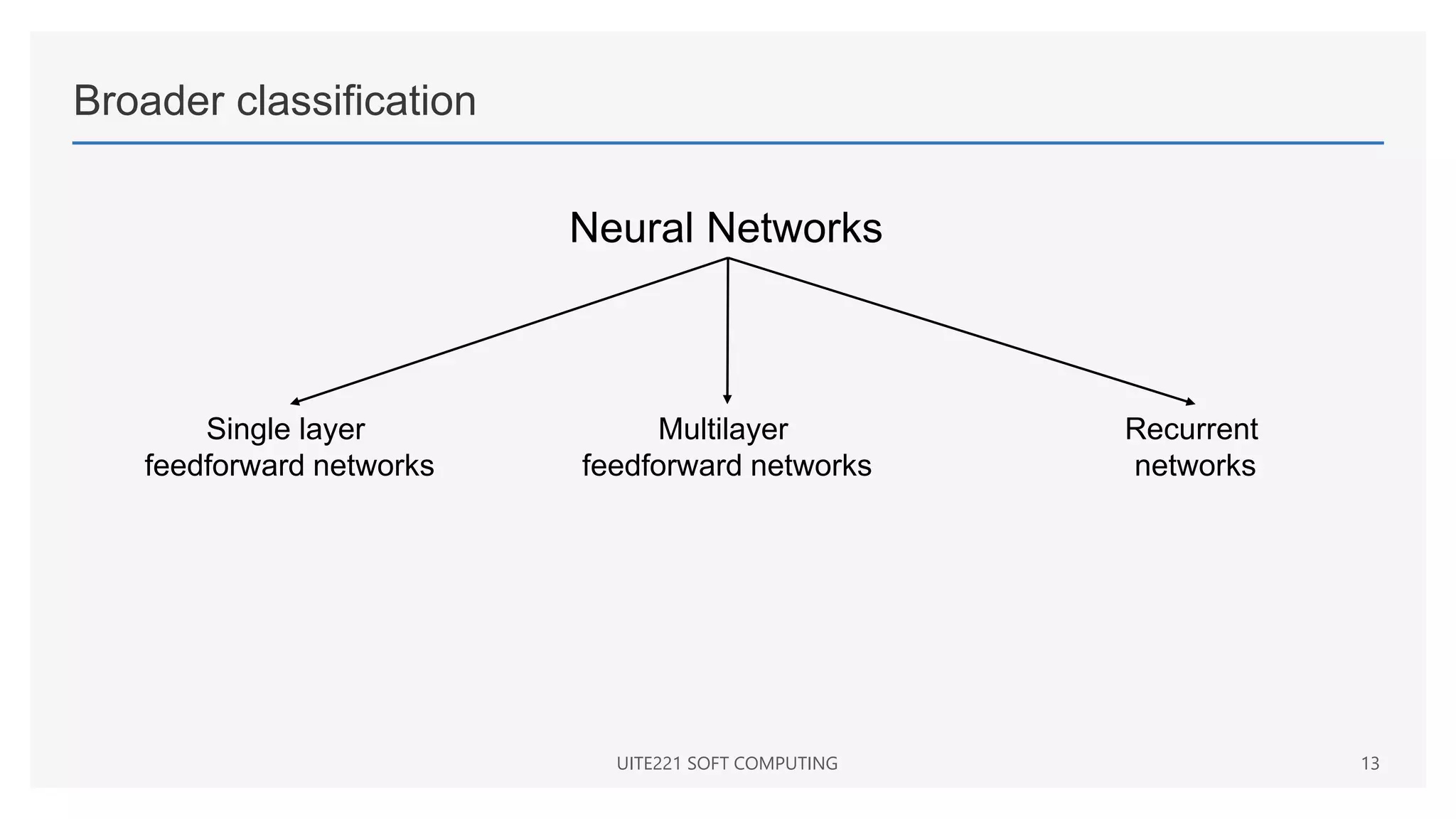
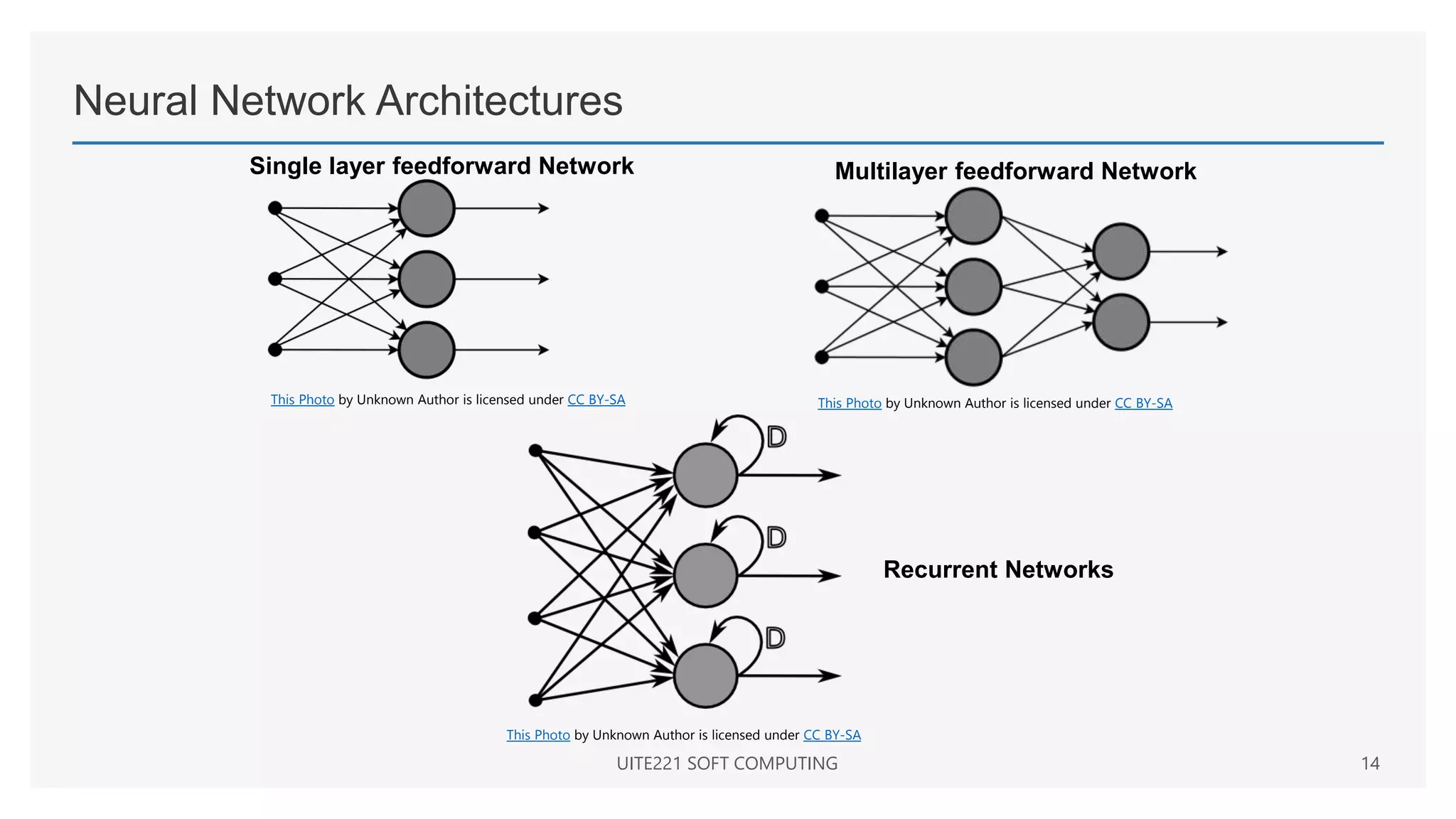
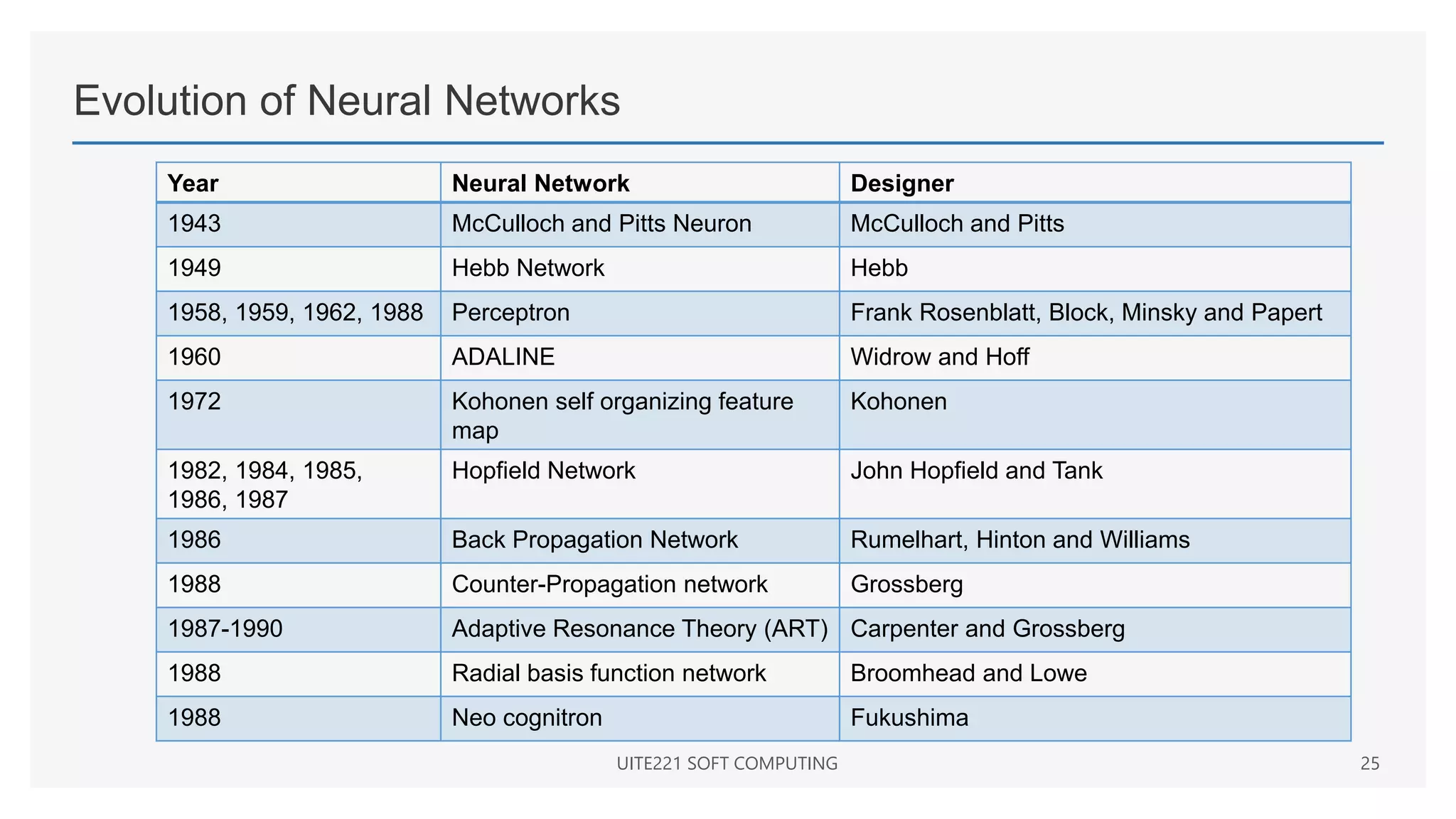
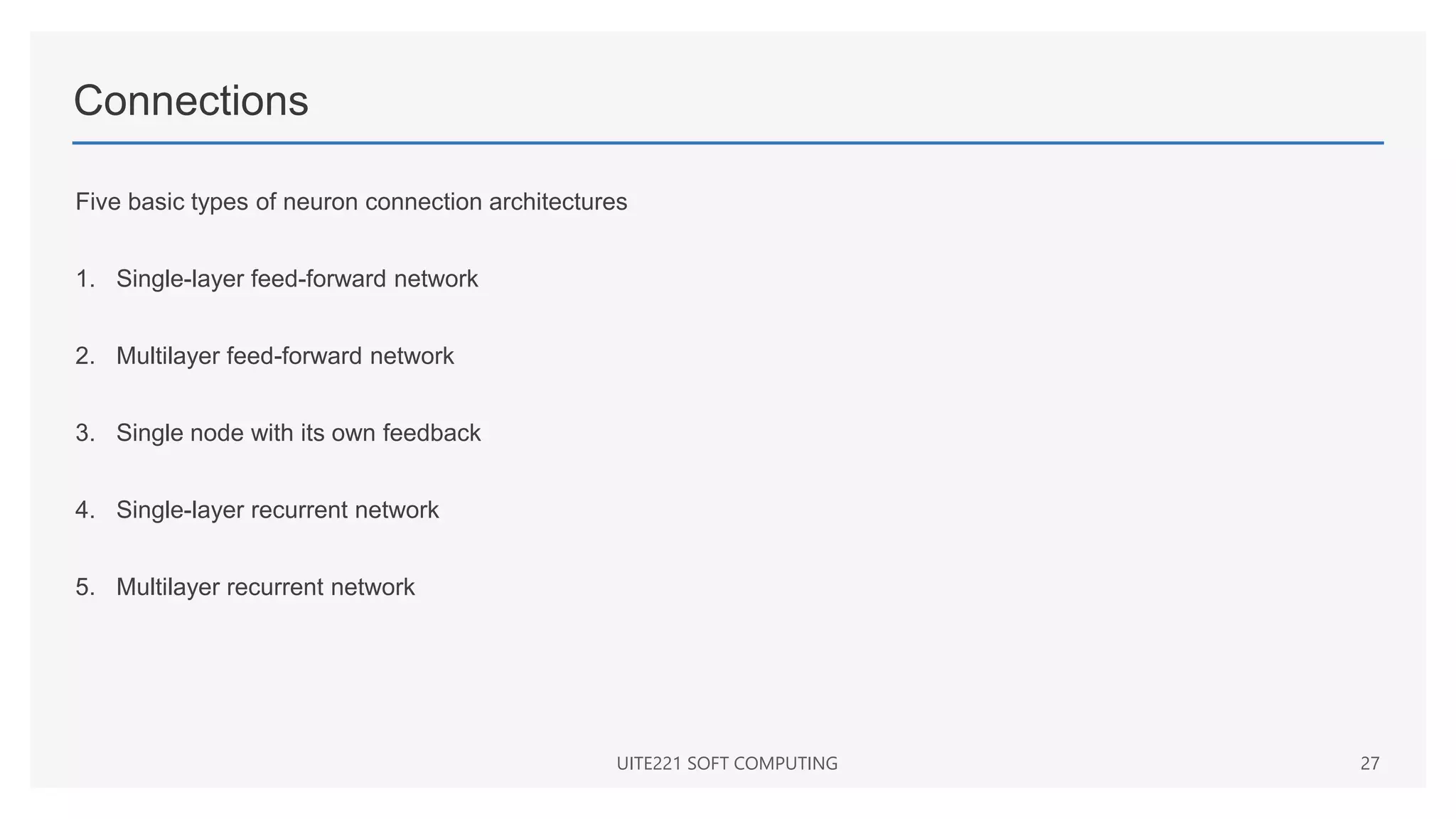
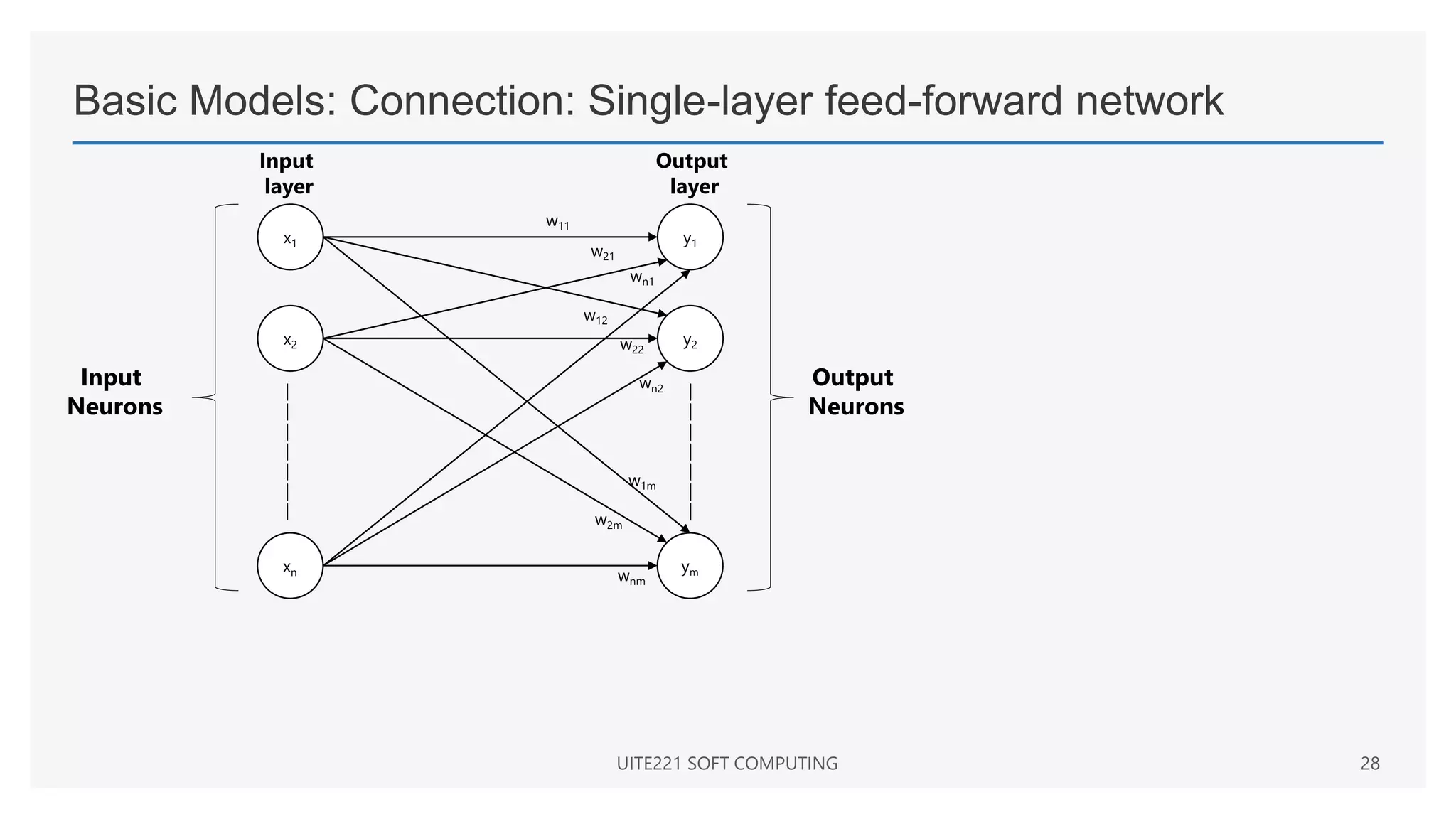
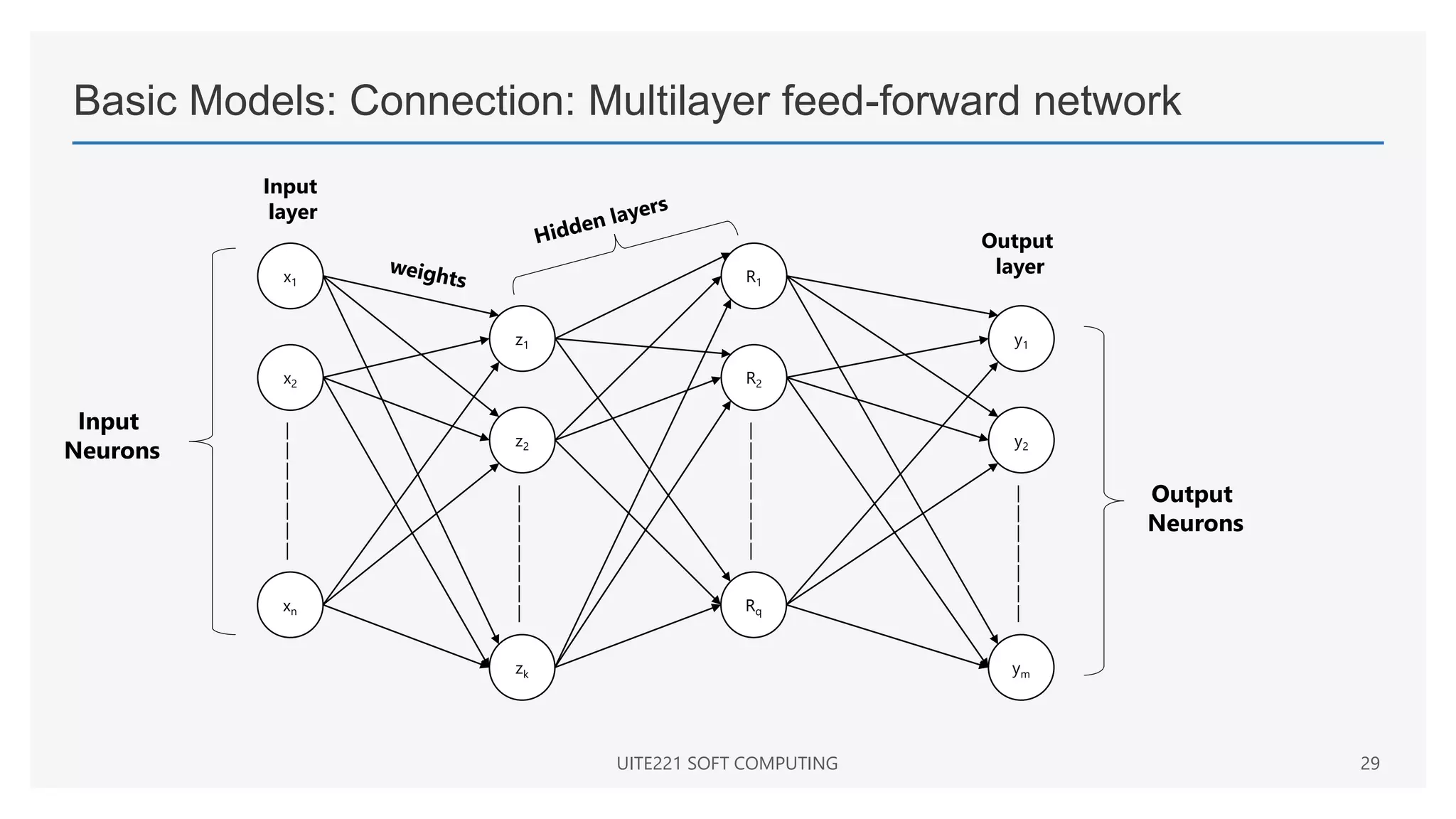
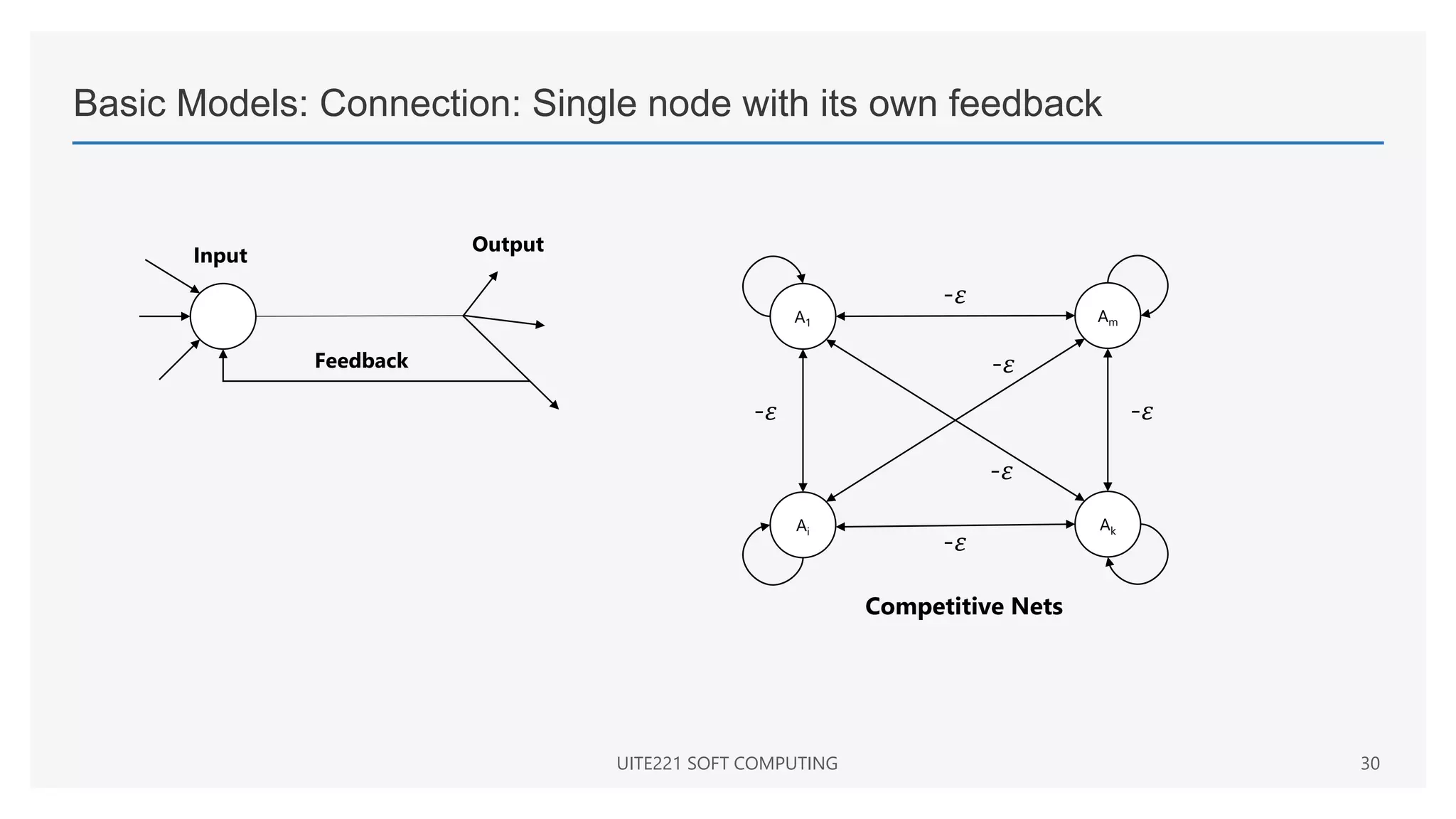
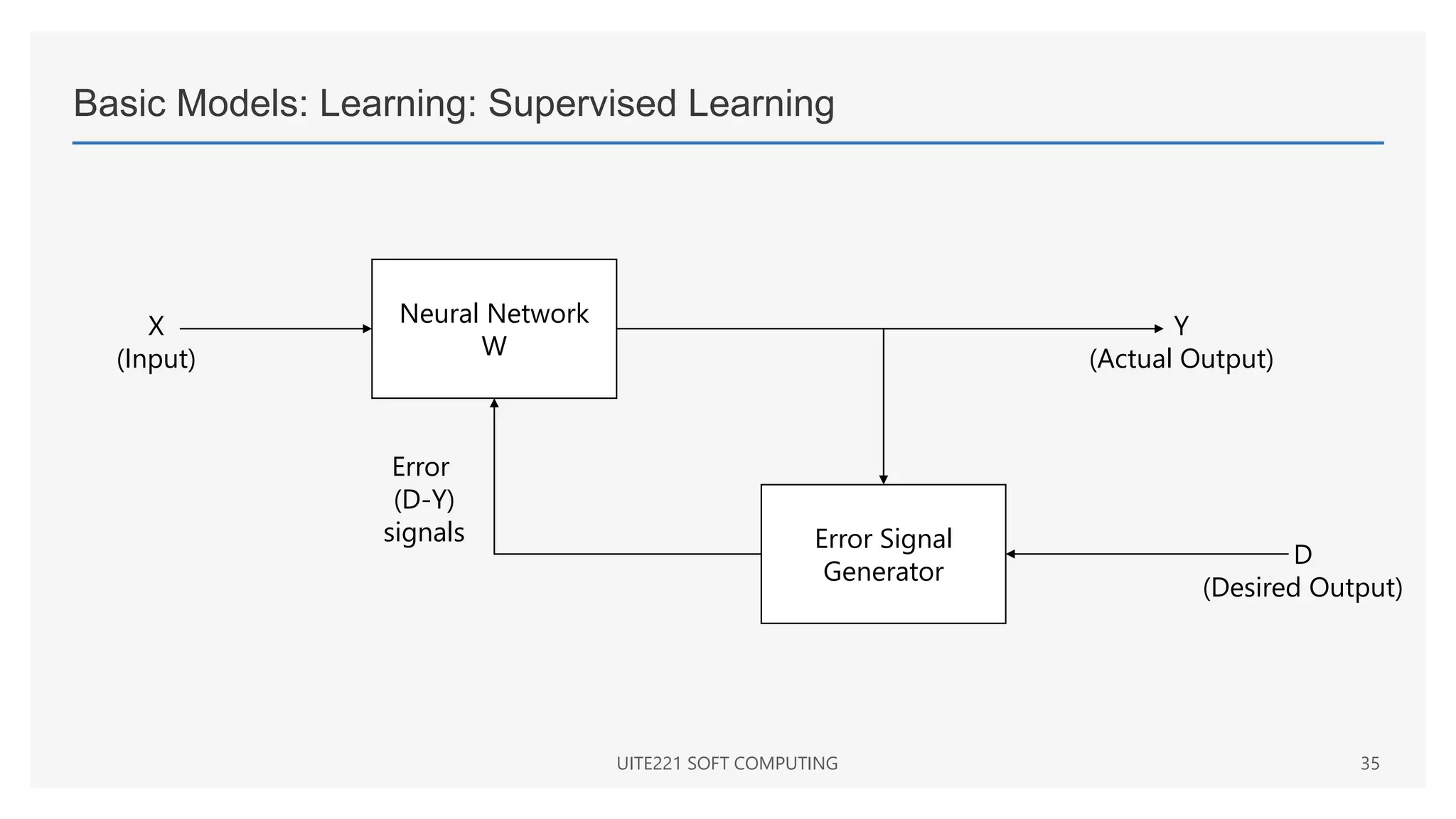
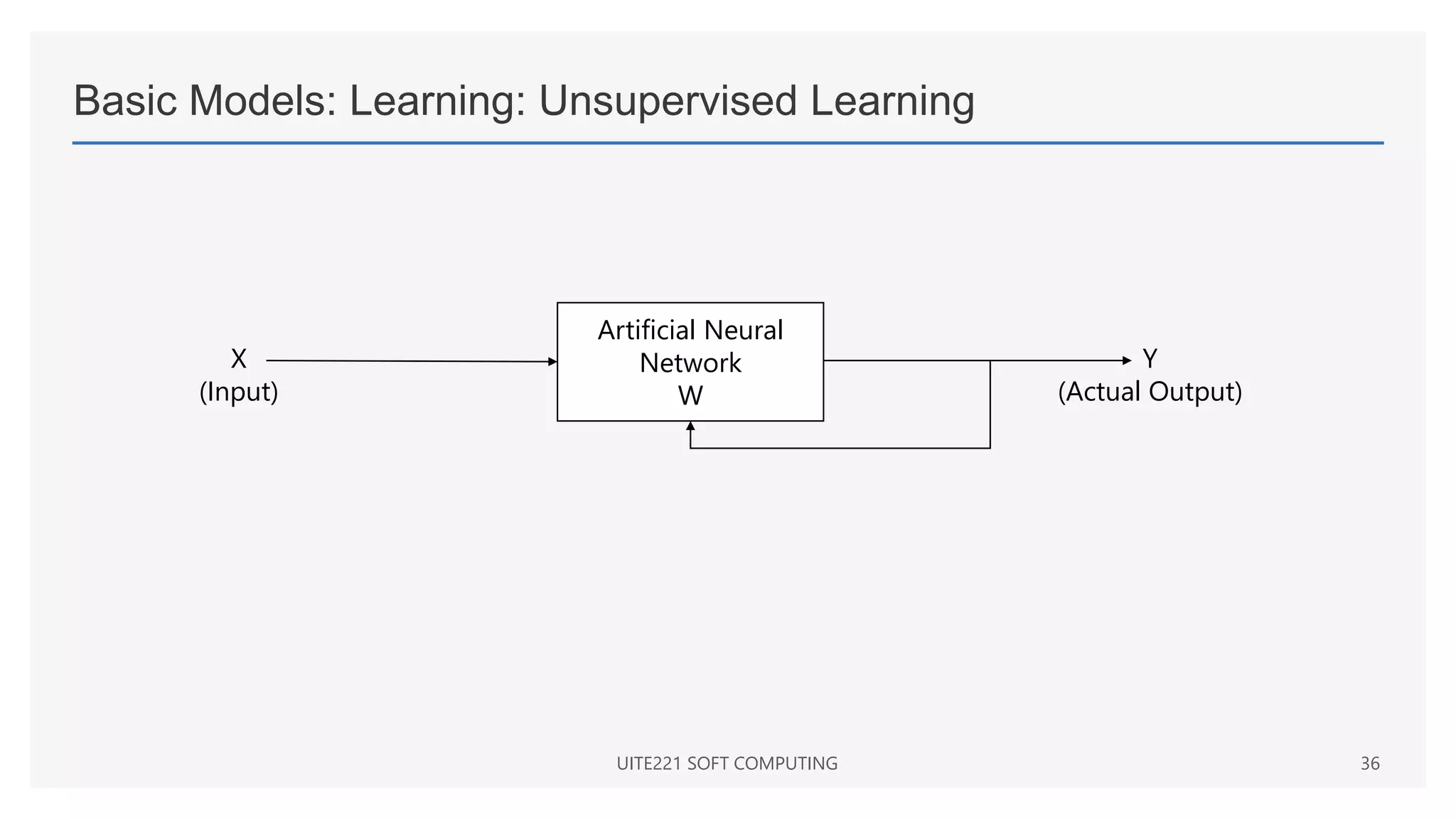
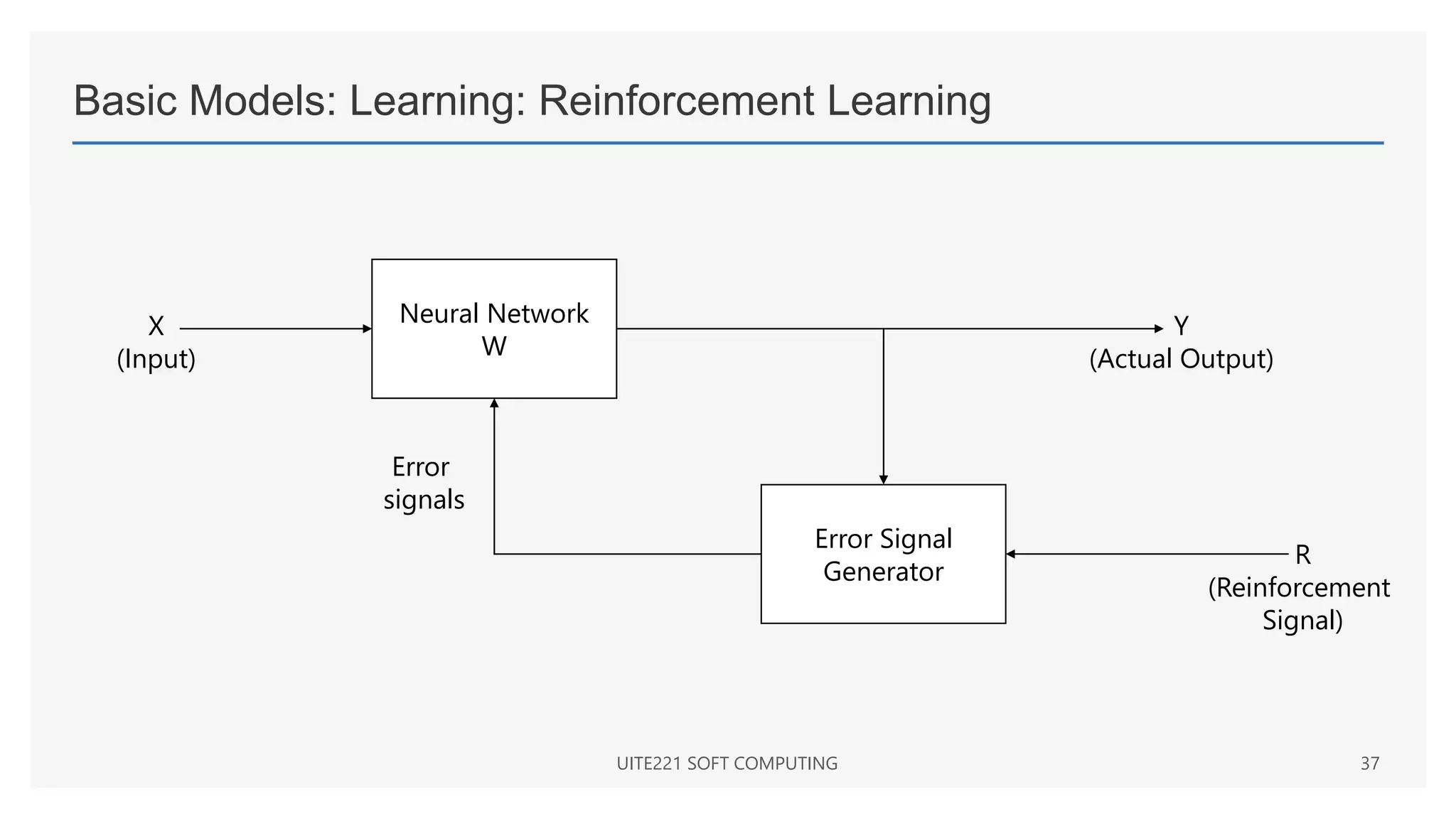
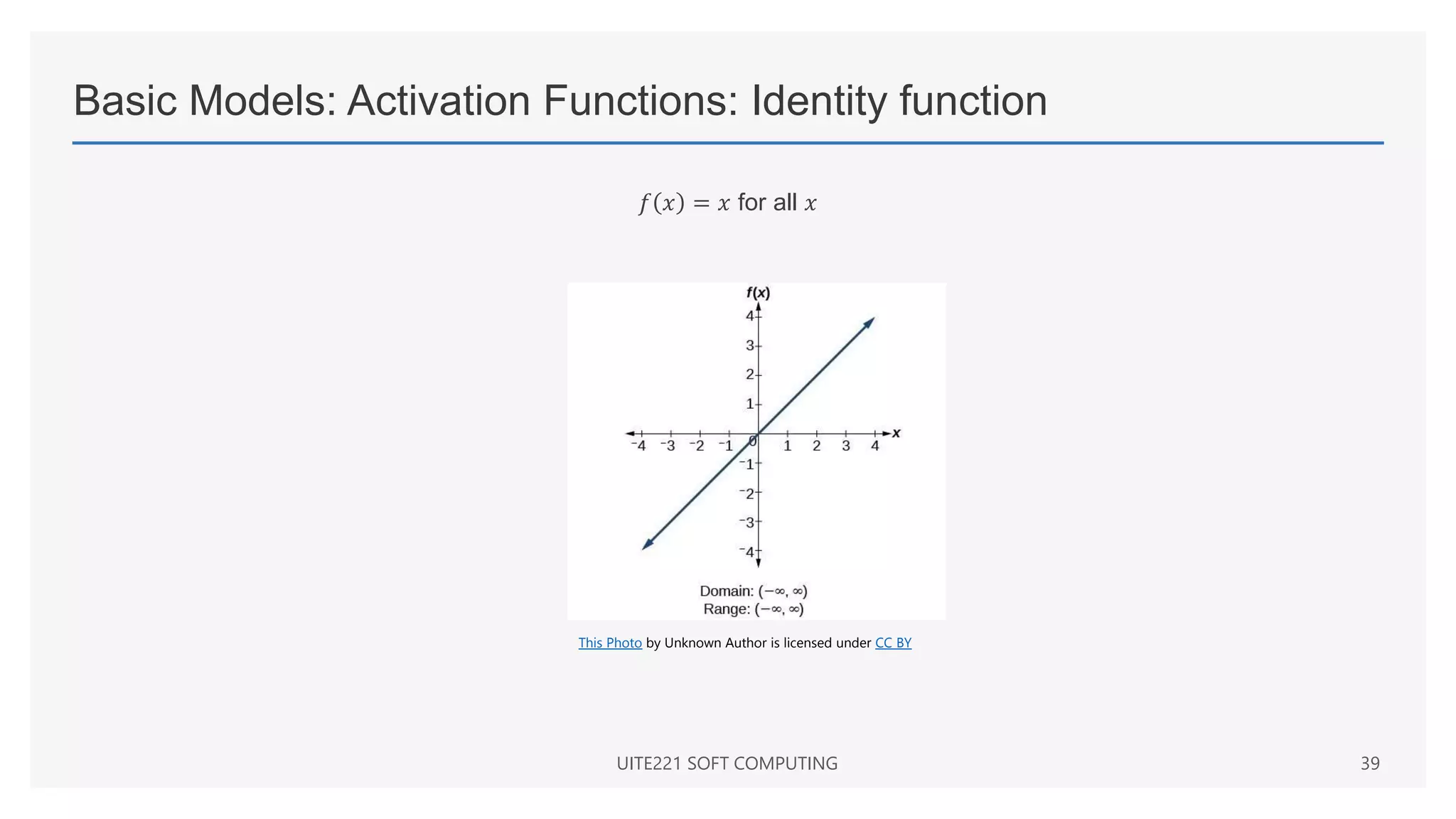
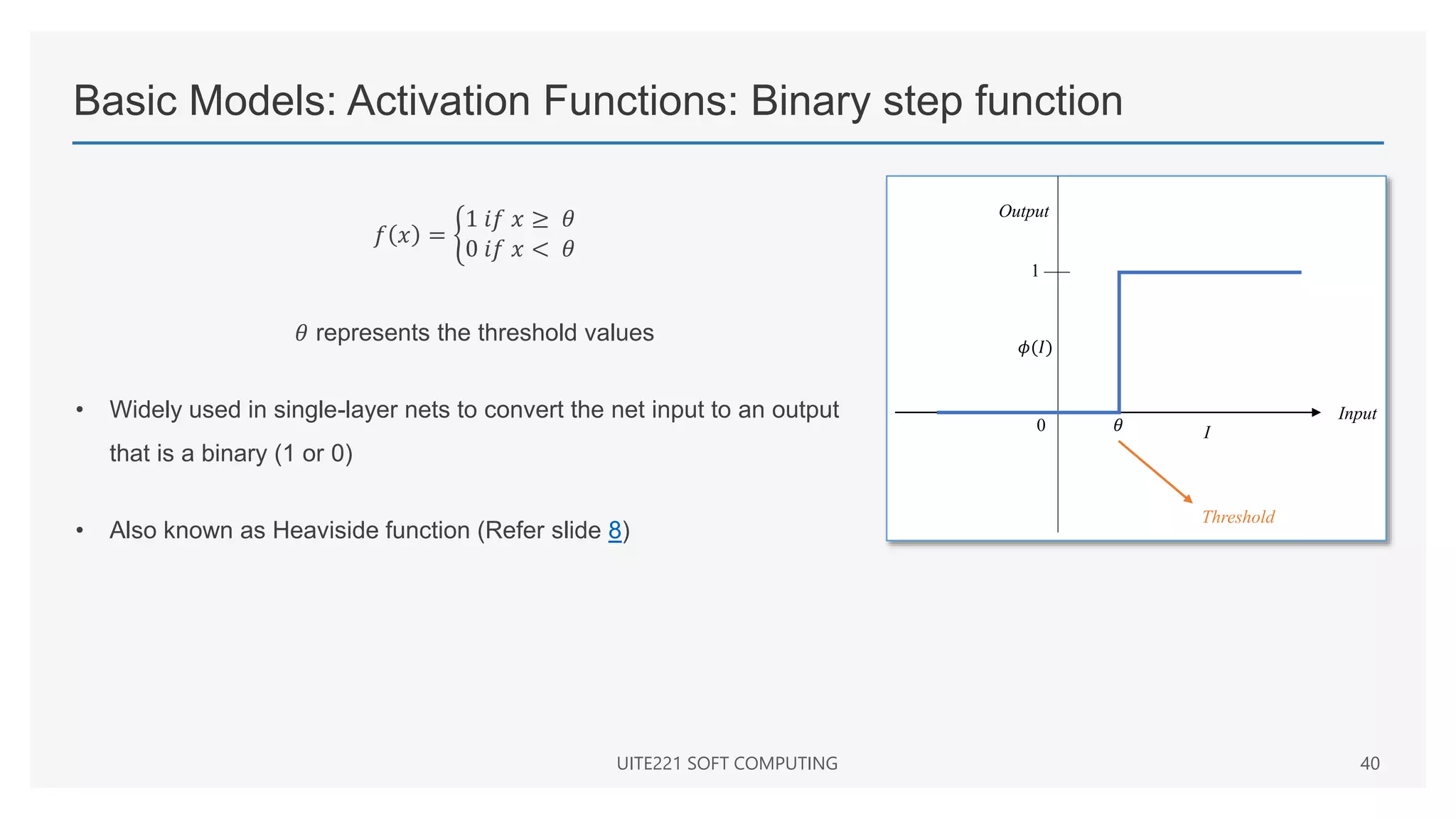
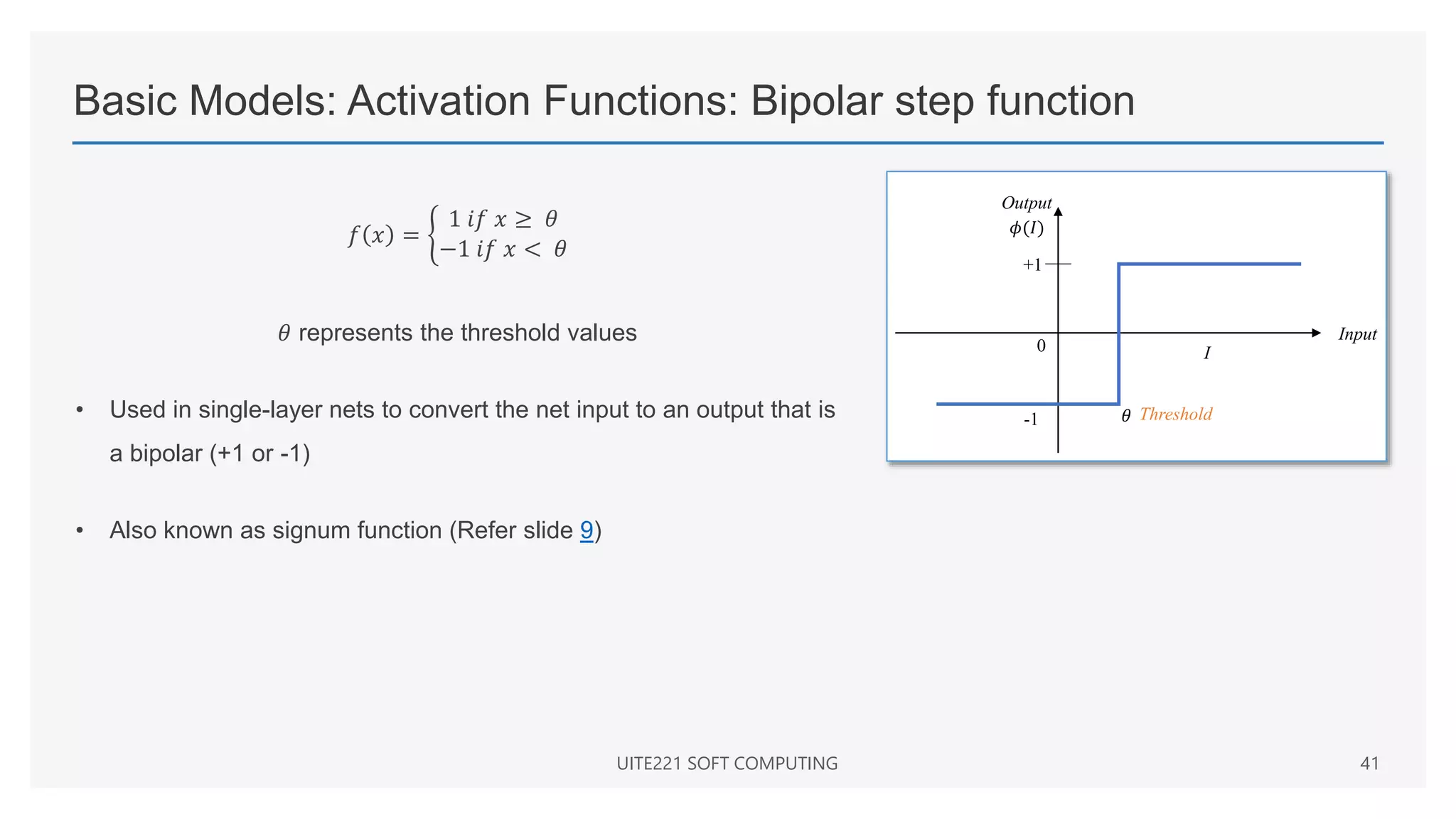
This document provides a comprehensive overview of artificial neural networks and their components, including various architectures, learning methods, and activation functions. It discusses the evolution of neural networks, the theoretical underpinnings of modeling, and explores applications in fields such as pattern recognition and optimization. Key terminologies such as weights, biases, and learning rates are also defined to aid understanding of neural network functionalities.

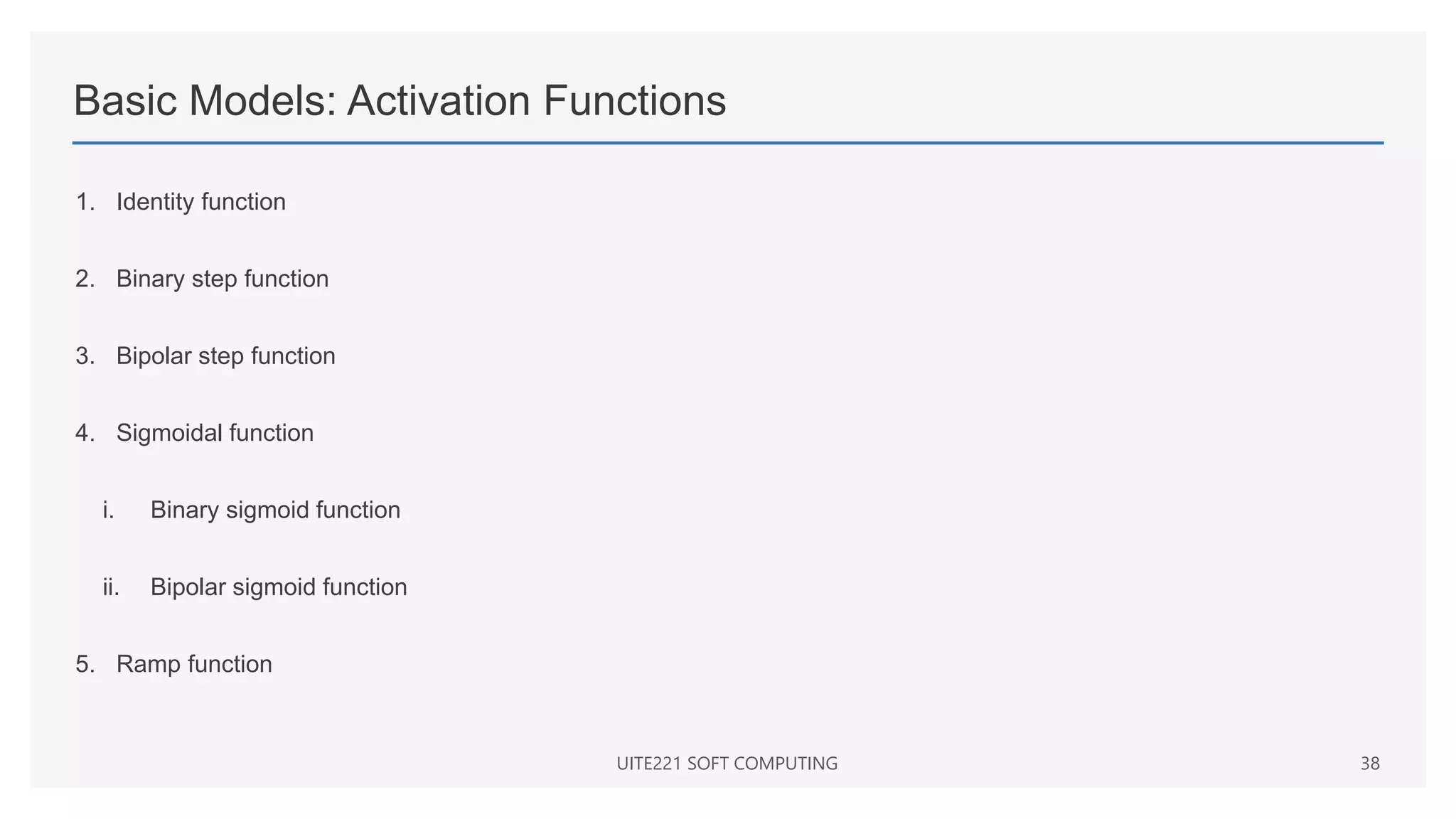
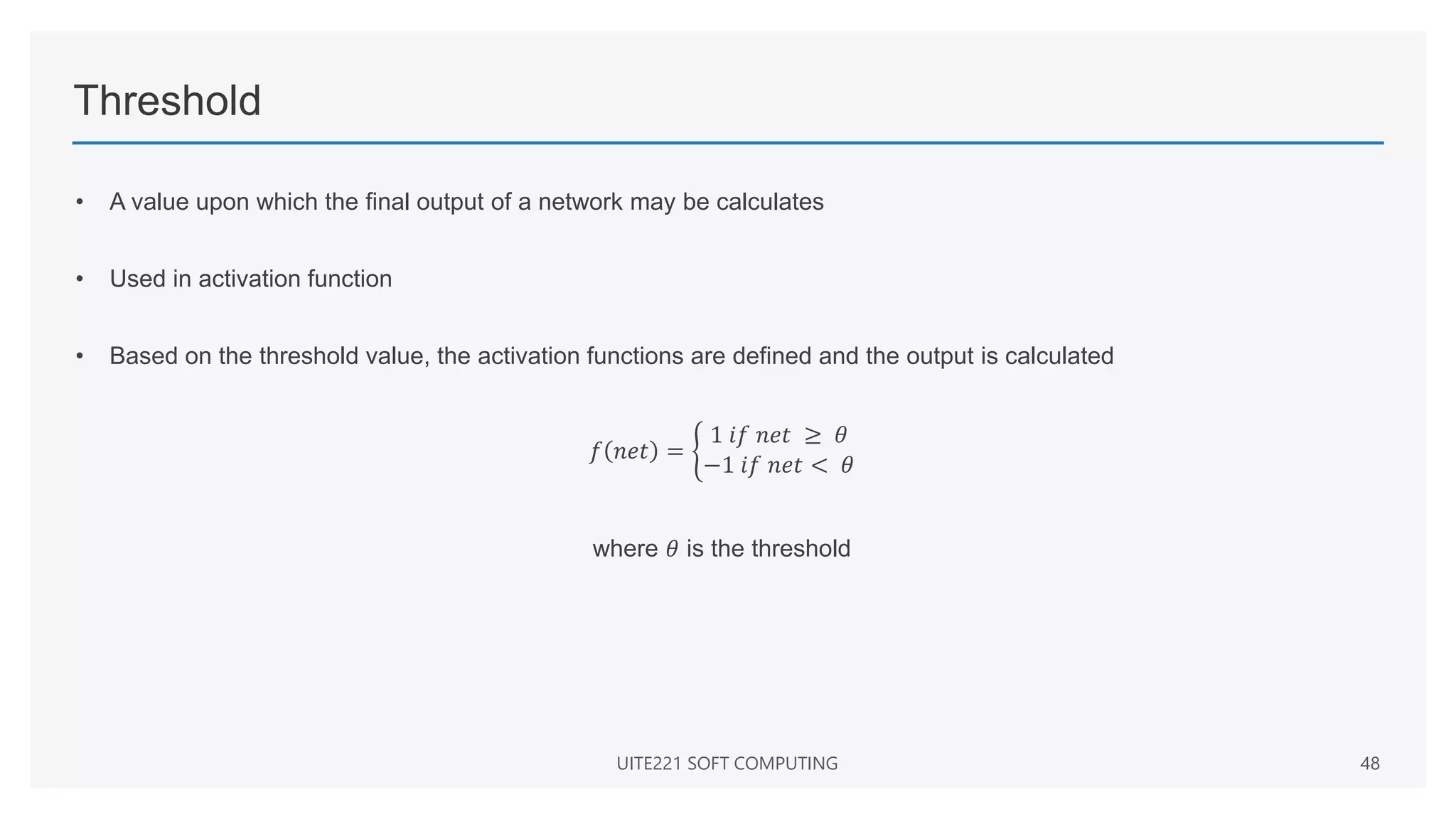
![Basic Models: Activation Functions: Sigmoidal function
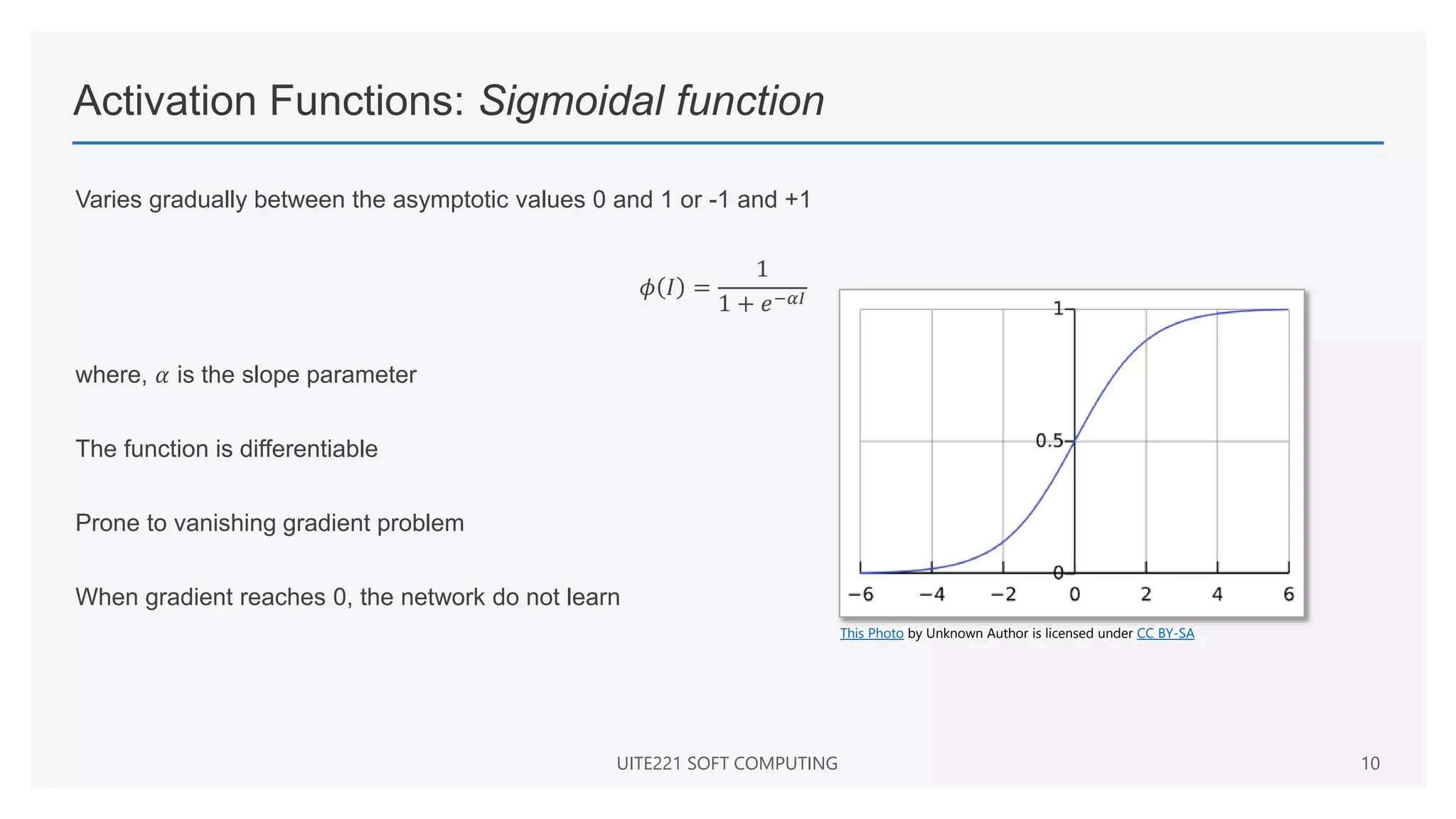
Binary sigmoid function
• Also known as logistic sigmoid function or unipolar sigmoid function
• Range is from 0 to 1
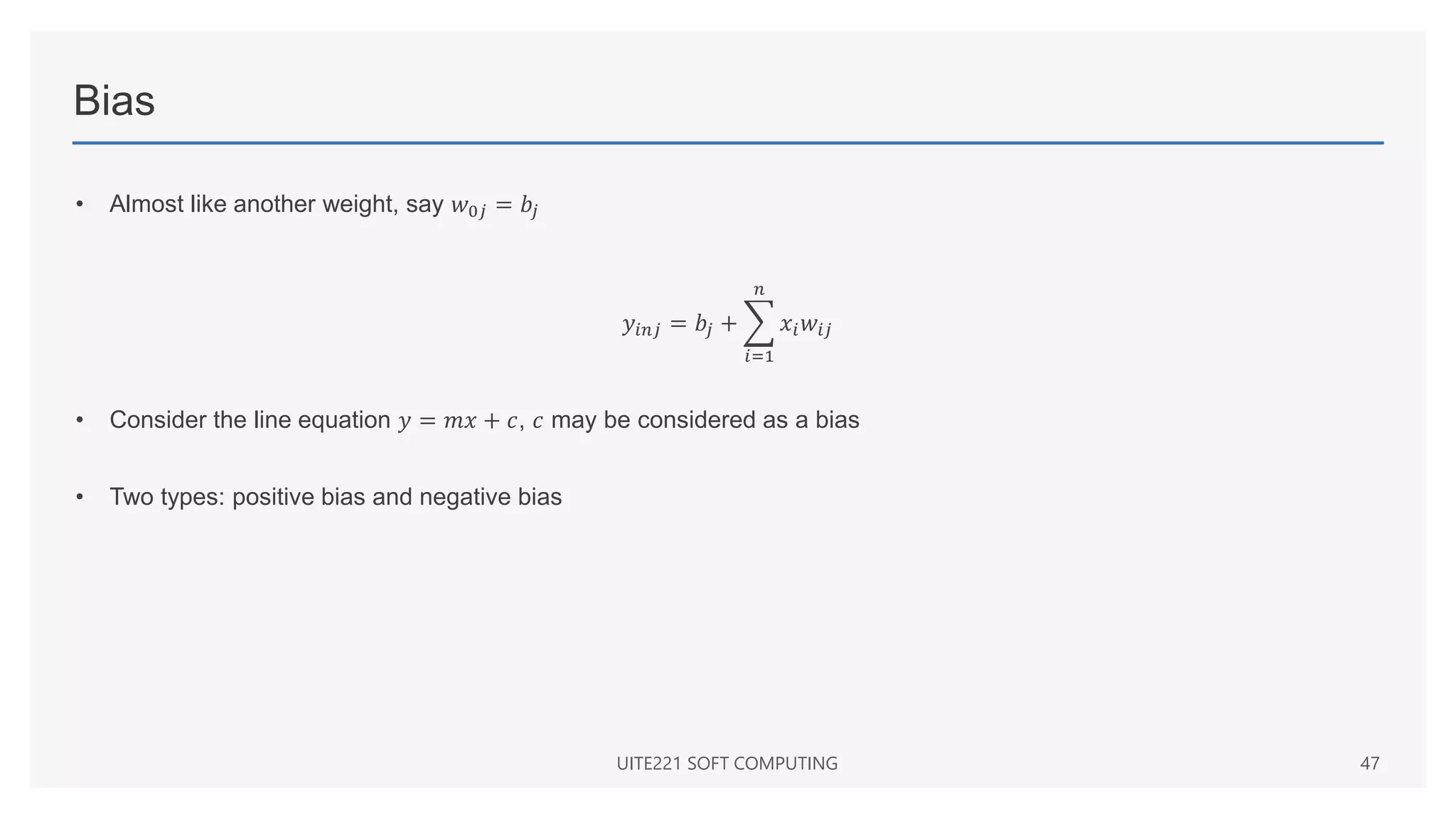
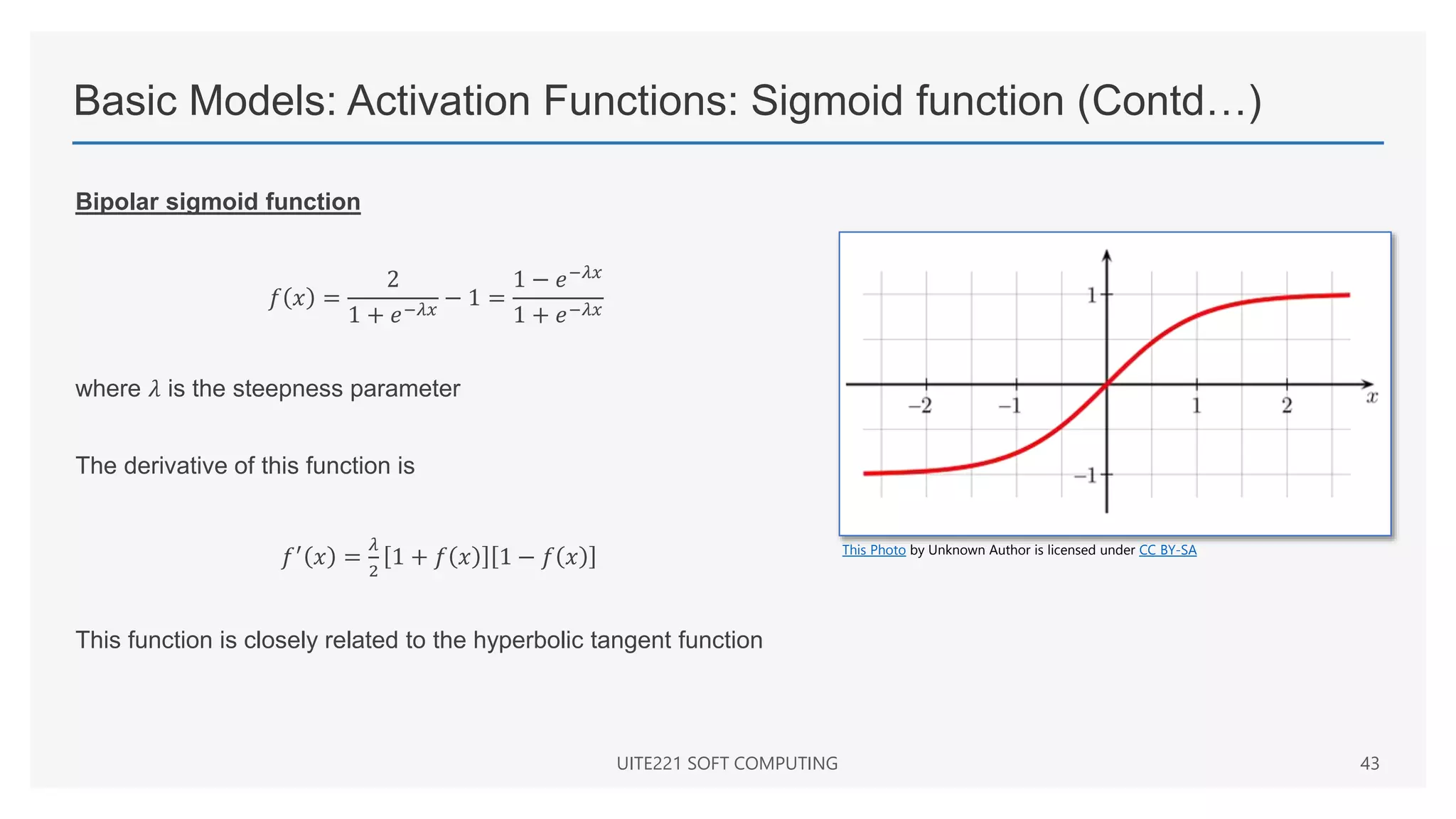
𝑓 𝑥 =
1
1 + 𝑒−𝜆𝑥
where 𝜆 is the steepness parameter
Derivative of this function is
𝑓′
𝑥 = 𝜆𝑓 𝑥 [1 − 𝑓(𝑥)]
UITE221 SOFT COMPUTING 42
This Photo by Unknown Author is licensed under CC BY-SA](https://image.slidesharecdn.com/introduction-artificialneuralnetworks-211008035827/75/Introduction-to-Artificial-Neural-Networks-42-2048.jpg)
![Weights
• Contains information about the input signal which is used to solve a problem
• Can be represented in terms of matrix
• Also known as connection matrix
• Weights encode long-term memory [LTM] and the activation states short-term memory [STM]
• Assume “n” processing elements and each element has “m” adaptive weights, weight matrix W is defined by
𝑊 =
𝑤1
𝑇
𝑤2
𝑇
⋮
𝑤𝑛
𝑇
=
𝑤11 𝑤12 …
𝑤21 𝑤22 …
⋮ ⋮ …
𝑤𝑛1 𝑤𝑛2 …
𝑤1𝑚
𝑤2𝑚
⋮
𝑤𝑛𝑚
UITE221 SOFT COMPUTING 46](https://image.slidesharecdn.com/introduction-artificialneuralnetworks-211008035827/75/Introduction-to-Artificial-Neural-Networks-46-2048.jpg)