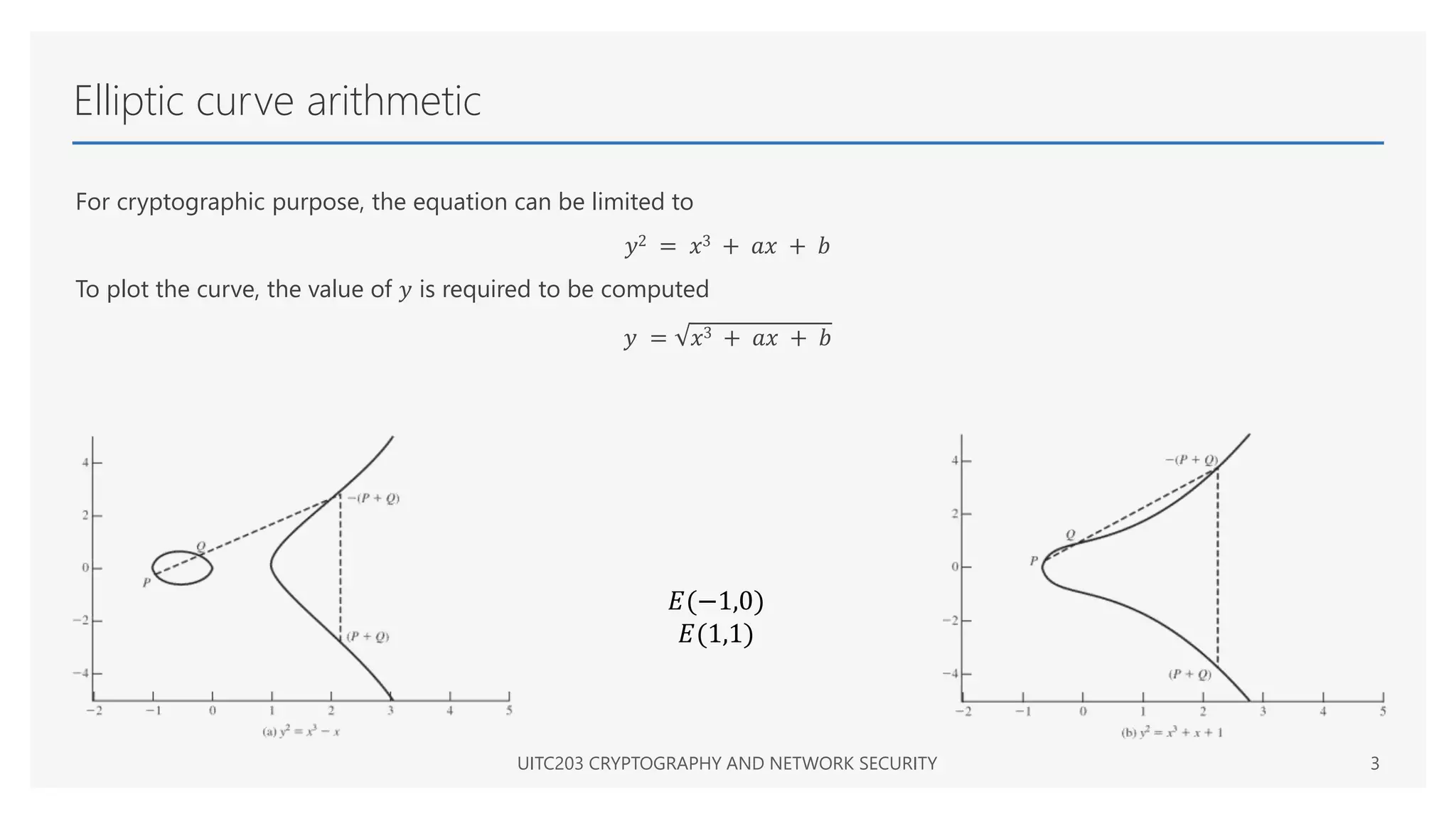
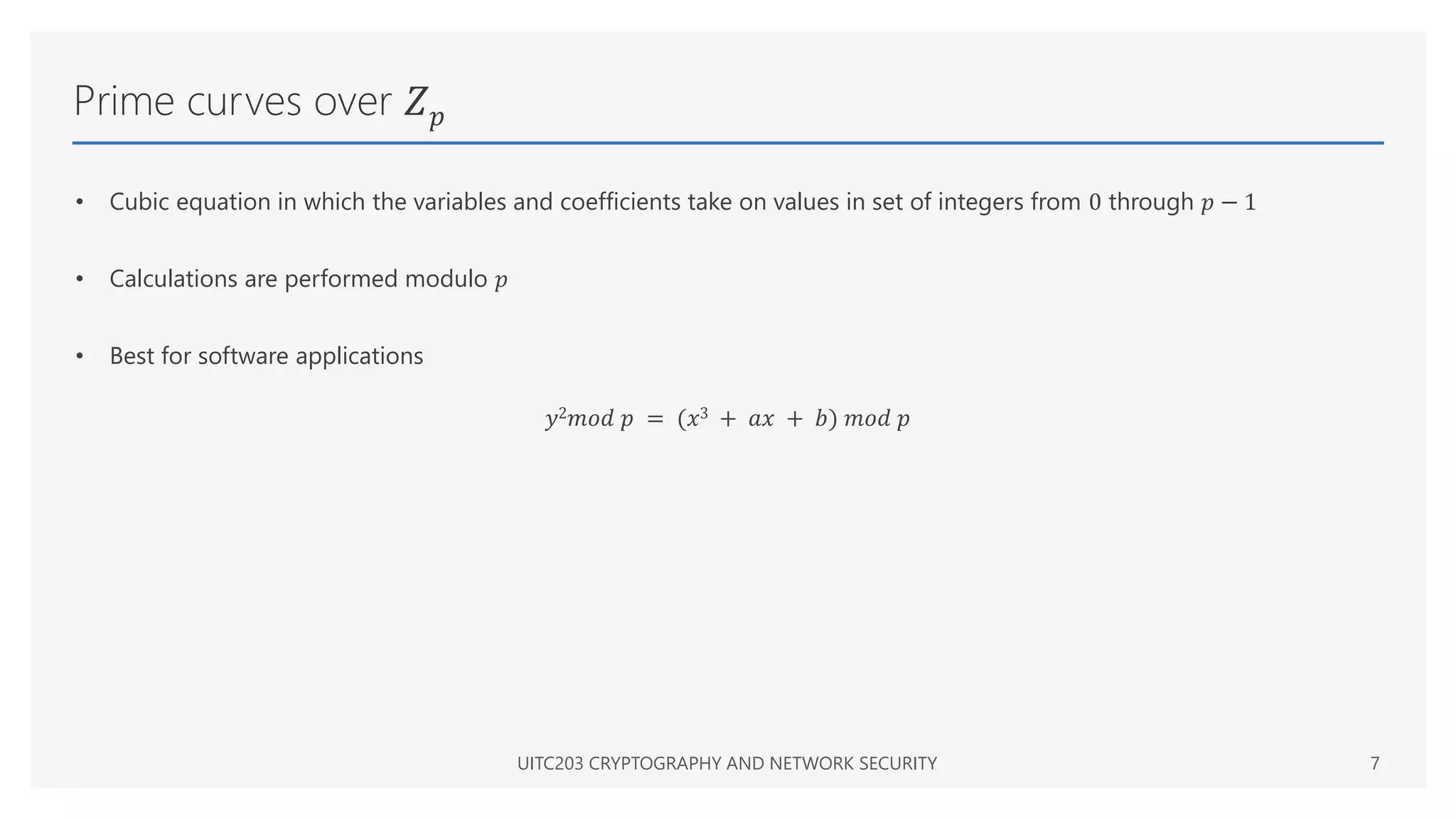
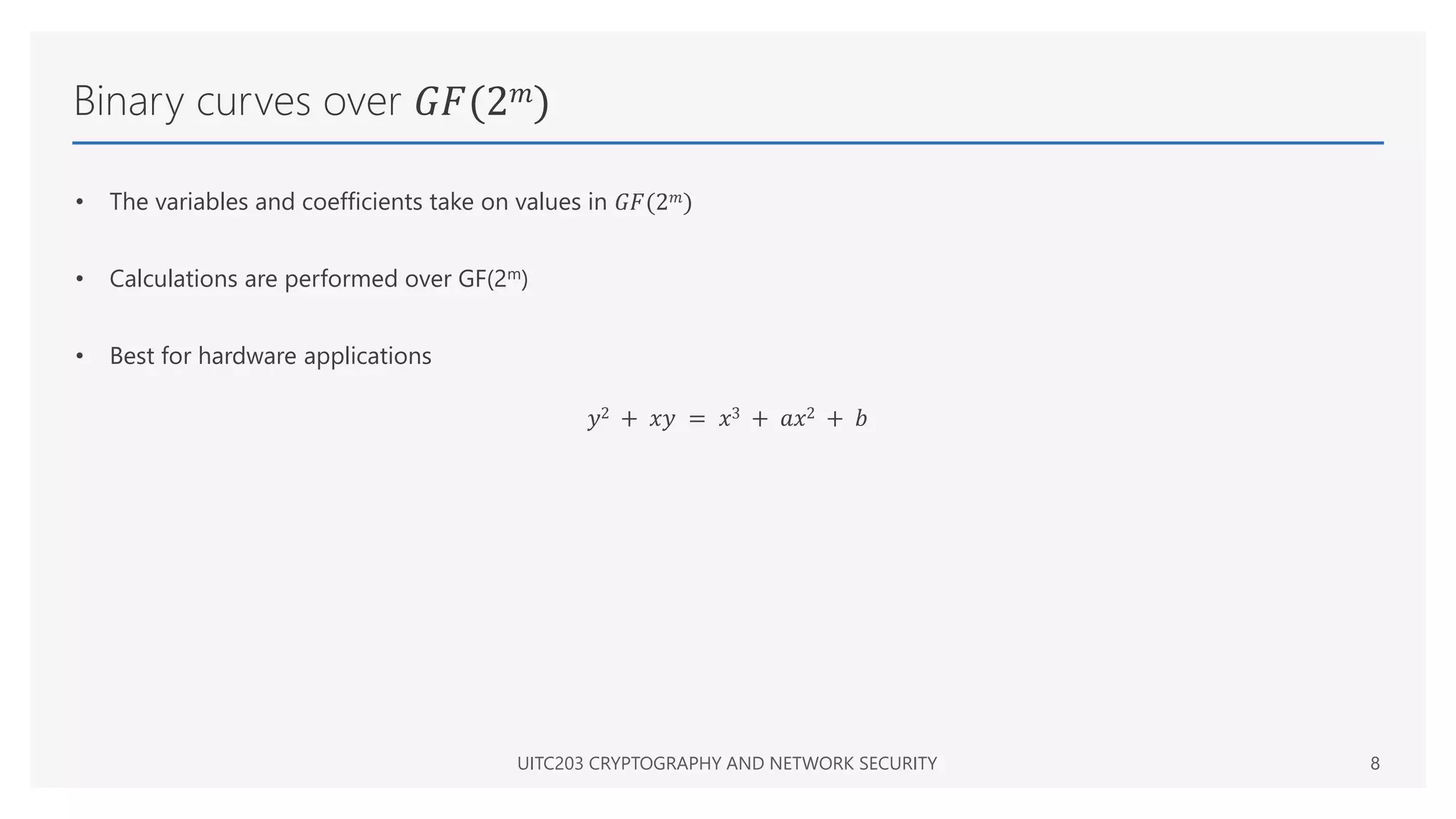
The document provides an overview of elliptic curve cryptography, detailing its mathematical foundation using Weierstrass equations and geometric interpretation of elliptic curve arithmetic. It describes the addition of points on elliptic curves and outlines two families of elliptic curves utilized in cryptographic applications: prime curves and binary curves. Additionally, it explains key generation and the Diffie-Hellman key exchange mechanism based on elliptic curves.