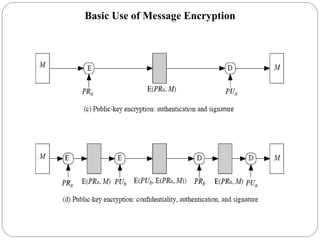
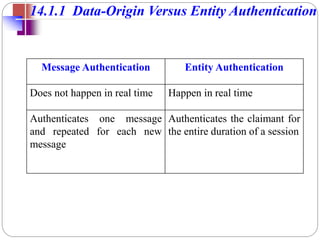
This document provides an overview of message authentication and integrity. It discusses the need for authentication in network security and outlines different authentication functions including message encryption, message authentication codes (MACs), and hash functions. It describes how MACs are generated using a secret key and message and provides the requirements for MACs. The document also discusses the MD5 and SHA hash algorithms, explaining their processes and analyzing their security strengths and weaknesses.




































![Block Ciphers as Hash Functions
• Can use block ciphers as hash functions
Using H0=0 and zero-pad of final block
compute: Hi = EMi
[Hi-1]
Use final block as the hash value
Similar to CBC but without a key
• Resulting hash is too small (64-bit)
Due to direct birthday attack
Due to “meet-in-the-middle” attack
• Other variants also susceptible to attack](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-41-320.jpg)

![• Cryptanalytic attacks exploit structure
Like block ciphers want brute-force attacks to be the best
alternative.
• Have a number of analytic attacks on iterated hash functions.
CVi = f[CVi-1, Mi]; H(M)=CVN
Typically focus on collisions in function f.
Like block ciphers is often composed of rounds.
Attacks exploit properties of round functions.
Hash Functions and MAC Security](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-43-320.jpg)





![Implementation Steps
Step 2: Append length A 64-bit length
contains the length of the original message modulo
264
The expanded message is Y0, Y1, …, YL-1; the total
length is L × 512 bits
The expanded message can be thought of as a multiple
of 16 32-bit words
Let M[0 … N-1] denote the word of the resulting
message, where N = L × 16](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-49-320.jpg)

![Implementation Steps
Step 4: Process message in 512-bit (16-word) blocks
Heart of the algorithm called a compression function Consists
of 4 rounds
The 4 rounds have a similar structure, but each uses a different
primitive logical functions, referred to as F, G, H, and I
Each round takes as input the current 512-bit block (Yq), 128-
bit buffer value ABCD and updates the contents of the buffer
Each round also uses the table T[1 … 64], constructed from
the sine function; T[i] = 232 × abs(sin(i))
The output of 4th round is added to the CVq to produce
CVq+1](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-51-320.jpg)

![Implementation Steps
Step 5: Output
After all L 512-bit blocks have been processed, the output
from the Lth stage is the 128- bit message digest
CV0 = IV
CVq+1 = SUM32(CVq, RFI[Yq, RFH[Yq, RFG[Yq, RFF[Yq, CVq]]])
MD = CVL
Where
IV = initial value of the ABCD buffer, defined in step 3
Yq = the qth 512-bit block of the message
L = the number of blocks in the message (including padding and
length fields)
CVq = chaining variable processed with the qth block of the message
RFx = round function using primitive logical function x
MD = final message digest value
SUM32 = addition modulo 232 performed separately on each word](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-53-320.jpg)
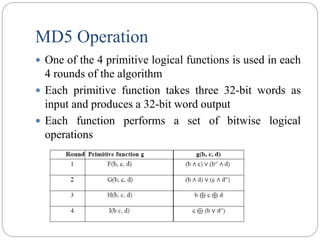
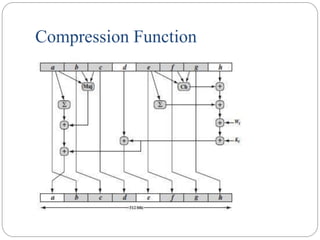
![MD5 Compression Function
Each round consists of a sequence of 16 steps operating on the buffer
ABCD
Each step is of the form
a ← b + (( a + g(b, c, d) + X[k] + T[i] <<< s )
where a,b,c,d = the 4 words of the buffer, in a specified order that varies across
steps g = one of the primitive functions F, G, H, I
<<s = circular left shift (rotation) of the 32-bit arguments by s bits
X[k] = M[q × 16 + k] = the kth 32-bit word in the qth 512-bit block of the
message
T[i] = the ith 32-bit word in table T
+ = addition modulo 232 `](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-54-320.jpg)







![Implementation Steps
Step 1: Append padding bits
The message is Padd d so that its bit length is congruent
to 896 modulo 1024 [length K ≡ 896 mod 1024]
Padding is always added, even if the message is already
of the desired length.
Thus, the number of padding bits is in the range of 1 to
1024.
The padding consists of a single 1-bit followed by the
necessary number of 0-bits.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-63-320.jpg)

























![Second Approach
[contd…]
Figure 14.2 Hashing
the password
Dictionary attack
Create a list of password, calculate the hash value,
and search the second-column entries to find a
match.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-94-320.jpg)
![Third Approach
[contd…]
Figure 14.3 Salting
the password
When the password is created, a random string, called
the salt, is concatenated to the password. The salted
password is then hashed.
The Unix OS uses a variation of this method.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-95-320.jpg)
![Fourth Approach
• Two identification techniques are combined.
• A good example of this type of authentication is the use of
an ATM card (something possessed) with a PIN (personal
identification number) (something known).
[contd…]](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-96-320.jpg)

![[contd…]
Figure 14.4 the third approach -- Lamport one-time password
Alice and Bob agree upon an
original password P0 and a counter n.
The system stores the identity of
Alice, the value of n and the hash.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-98-320.jpg)

![[contd…]
In challenge-response authentication, the claimant
proves that she knows a secret without sending it to
the verifier.
Note
The challenge is a time-varying value sent by the
verifier; the response is the result
of a function applied on the challenge.
Note](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-100-320.jpg)

![Second Approach
[contd...]
Figure 14.6 Timestamp challenge
The challenge message is the current time sent
from the verifier to the claimant.
The claimant encrypt Alice ID and time with
Alice-Bob secret key.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-102-320.jpg)
![Third Approach.
[contd…]
Figure 14.7 Bidirectional authentication
1. Alice ID
2. The challenge from Bob to Alice RB
3. Alice respond and send her challenge RA
4. Bob’s response. RA and RB are switched to prevent a replay attack.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-103-320.jpg)


![Second Approach
[contd…]
Figure 14.10 Bidirectional, asymmetric-key](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-106-320.jpg)

![Second Approach
[contd…]
Figure 14.12 Digital signature, bidirectional authentication](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-108-320.jpg)


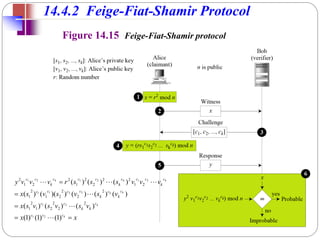
![Cave Example
[contd…]
Figure 14.14 Cave example
1. Alice chooses to go either right or left. After Alice disappears, Bob comes to
point 2 and asks Alice to come up from either the right or left.
2. if Alice knows the magic word, she will come up from the right direction. If
she does not know the word, she comes up from the right direction with ½
probability.
3. The game will be repeated many times.
The door can only be
opened with a magic word.
Alice claims that she knows
the word and that she can
open the door. Bob and
Alice are at pint 1. Alice
enters eh case and reaches
the point 2.](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-111-320.jpg)
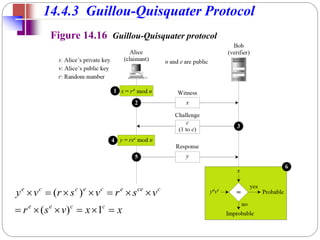












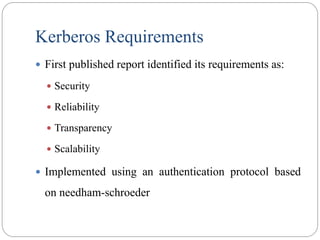
![Needham-Schroeder Protocol
original third-party key distribution protocol
for session between A B mediated by KDC
protocol overview is:
1. A KDC: IDA || IDB || N1
2. KDC A: E(Ka,[Ks||IDB||N1|| E(Kb,[Ks||IDA])])
3. A B: E(Kb, [Ks||IDA])
4. B A: E(Ks, [N2])
5. A B: E(Ks, [f(N2)])](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-126-320.jpg)

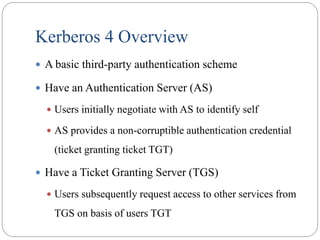
![One-Way Authentication
use refinement of KDC to secure email
since B no online, drop steps 4 & 5
protocol becomes:
1. A KDC: IDA || IDB || N1
2. KDC A: E(Ka, [Ks||IDB||N1 || E(Kb,[Ks||IDA])])
3. A B: E(Kb, [Ks||IDA]) || E(Ks, M)
provides encryption & some authentication
does not protect from replay attack](https://image.slidesharecdn.com/cs8792-cns-unitiv-211112040228/85/Cs8792-cns-unit-iv-128-320.jpg)