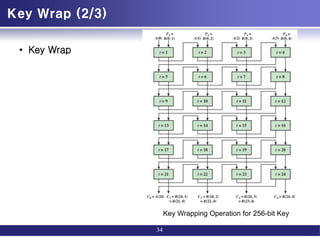
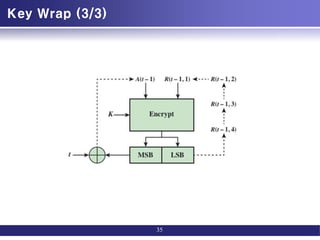
This document discusses message authentication techniques. It covers message authentication requirements such as preventing disclosure, modification, and repudiation of messages. It then describes various message authentication functions including hash-based MACs like HMAC, block cipher-based MACs like CMAC, and authenticated encryption modes like CCM and GCM. It also covers key wrapping and pseudorandom number generation using hash functions and MACs. The goal of message authentication codes and authenticated encryption is to verify that messages come from the alleged source and have not been altered.






![Message Authentication Functions (8/10)
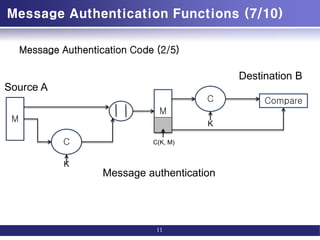
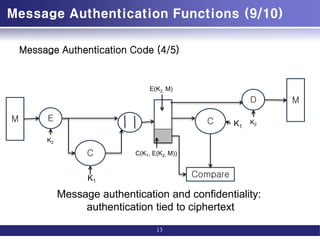
Message Authentication Code (3/5)
12
M
M
C
K1
E(K2, [M||C(K1, M)])
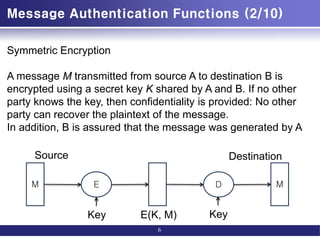
Message authentication and confidentiality:
authentication tied to plaintext
E
K2
M
C(K, M)
C
K1
Compare
D
K2](https://image.slidesharecdn.com/messageauthenticationandhashfunction-221213150813-325ecf24/85/Message-Authentication-and-Hash-Function-pdf-12-320.jpg)

![Requirements for Message Authentication Codes
• If an opponent observes M and MAC(K, M), it should be
computationally infeasible for the opponent to construct a
message M such that
MAC(K, M) = MAC(K, M)
• MAC(K, M) should be uniformly distributed in the sense
that for randomly chosen messages, M and M, the
probability that
MAC(K, M) = MAC(K, M)
is 2-n, where n is the number of bits in the tag.
• Let M be equal to some known transformation on M. That
is, M = f(M). For example, f may involve inverting one or
more specific bits. In that case,
Pr [MAC(K, M) = MAC(K, M)] = 2-n
15](https://image.slidesharecdn.com/messageauthenticationandhashfunction-221213150813-325ecf24/85/Message-Authentication-and-Hash-Function-pdf-15-320.jpg)
![Security of MACs
• Brute-Force Attacks
– Computation resistance: Given one or more text-MAC pairs [xi,
MAC(K, xi)], it is computationally infeasible to compute any text-
MAC pair [x, MAC(K, x)] for any new input x≠xi.
– the level of effort for brute-force attack on a MAC algorithm can be
expressed as min(2k, 2n)
– k: key length
– n: number of MAC bits
• Cryptanalysis
– That is, an ideal MAC algorithm will require a cryptanalytic effort greater than or equal to the
brute-force effort.
16](https://image.slidesharecdn.com/messageauthenticationandhashfunction-221213150813-325ecf24/85/Message-Authentication-and-Hash-Function-pdf-16-320.jpg)
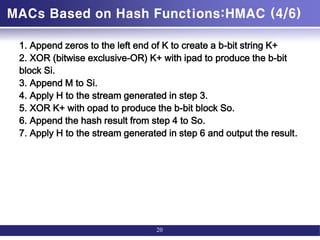
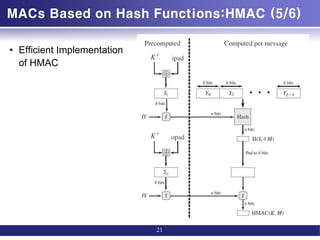
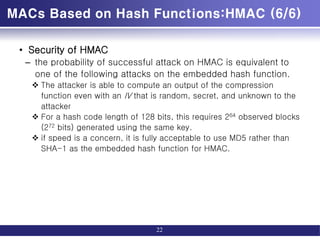
![MACs Based on Hash Functions:HMAC (3/6)
• HMAC(K,M)
= H[(K+ ⊕ opad) ∥
H[(K+ ⊕ ipad) ∥M]]
• H = embedded hash function (e.g., MD5,
SHA-1, RIPEMD-160)
• IV = initial value input to hash function
• M = message input to HMAC (including the
padding specified in the embedded
• hash function)
• Yi = i th block of M, 0 … i … (L - 1)
• L = number of blocks in M
• b = number of bits in a block
• n = length of hash code produced by
embedded hash function
• K = secret key; recommended length is Ú n; if
key length is greater than b, the
• key is input to the hash function to produce an
n-bit key
• K+ = K padded with zeros on the left so that
the result is b bits in length
• ipad = 00110110 (36 in hexadecimal) repeated b/8
times
• opad = 01011100 (5C in hexadecimal) repeated b/8
times
19](https://image.slidesharecdn.com/messageauthenticationandhashfunction-221213150813-325ecf24/85/Message-Authentication-and-Hash-Function-pdf-19-320.jpg)
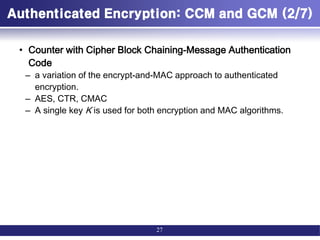
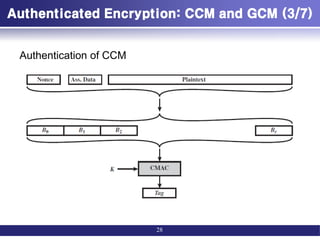
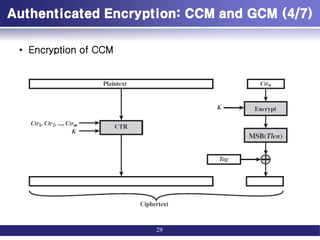
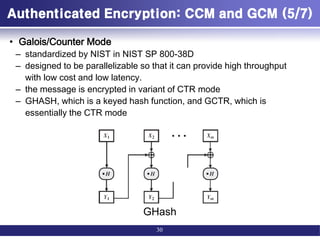
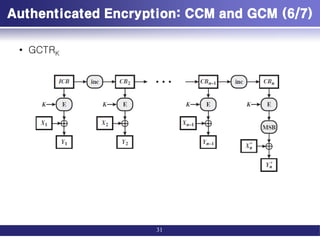
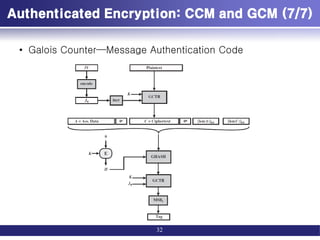
![Authenticated Encryption: CCM and GCM (1/7)
• Authenticated encryption: AE
– simultaneously protect confidentiality and authenticity (integrity) of
communications.
• Four common approaches to providing both
confidentiality and encryption for a message M.
– Hashing followed by encryption (H->E)
• First compute the cryptographic hash function over M as h = H(M).
• Then encrypt the message plus hash function: E(K, (M} h))
– Authentication followed by encryption (A->E)
• First authenticate the plaintext by computing the MAC value as T = MAC(K1, M).
• Then encrypt the message plus tag: E(K2, [M||T ]).
– Encryption followed by authentication (E->A)
• First encrypt the message to yield the ciphertext C = E(K2, M).
• Then authenticate the ciphertext with T = MAC(K1, C) to yield the pair (C, T).
– Independently encrypt and authenticate (E+A).
• Encrypt the message to yield the ciphertext C = E(K2, M).
• Authenticate the plaintext with T = MAC(K1, M) to yield the pair (C, T).
26](https://image.slidesharecdn.com/messageauthenticationandhashfunction-221213150813-325ecf24/85/Message-Authentication-and-Hash-Function-pdf-26-320.jpg)

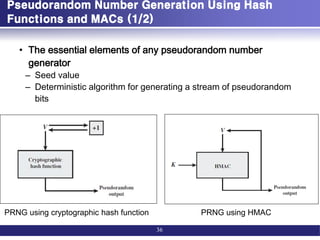
![Pseudorandom Number Generation Using Hash
Functions and MACs (2/2)
37
m = [n/outlen]
w0 = V
W = the null string
For i = 1 to m
wi = MAC(K, wi-1)
W = W||wii
Return leftmost n bits of W
m = [n/outlen]
W = the null string
For i = 1 to m
wi = MAC(K, (V|| i))
W = W||wi
Return leftmost n bits of W
m = [n/outlen]
A(0) = V
W = the null string
For i = 1 to m
A(i) = MAC(K, A(i - 1))
wi = MAC(K, (A(i) }V)
W = W||wi
Return leftmost n bits of W
NIST SP 800-90 IEEE 802.11i TLS/WTLS](https://image.slidesharecdn.com/messageauthenticationandhashfunction-221213150813-325ecf24/85/Message-Authentication-and-Hash-Function-pdf-37-320.jpg)
