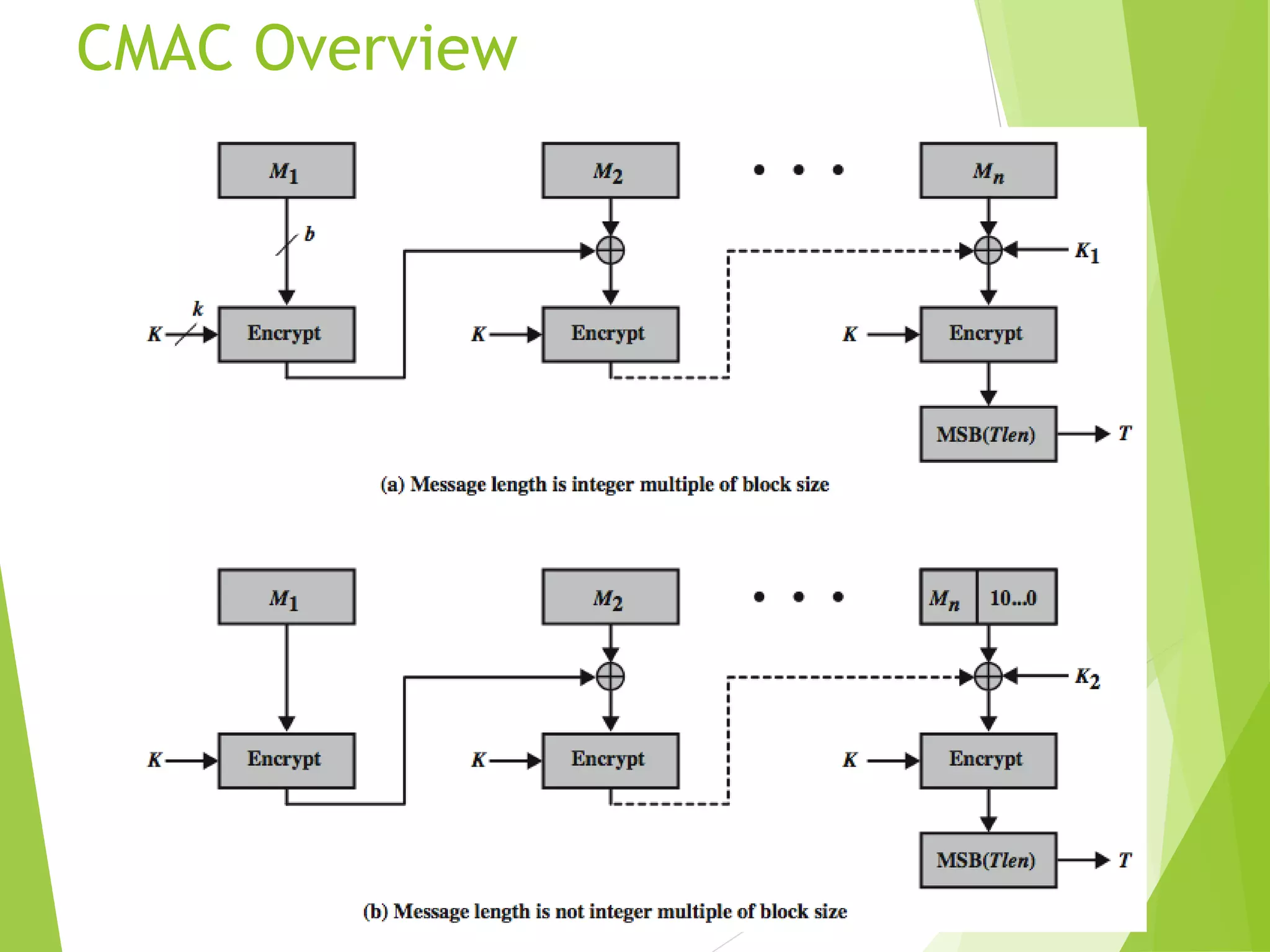
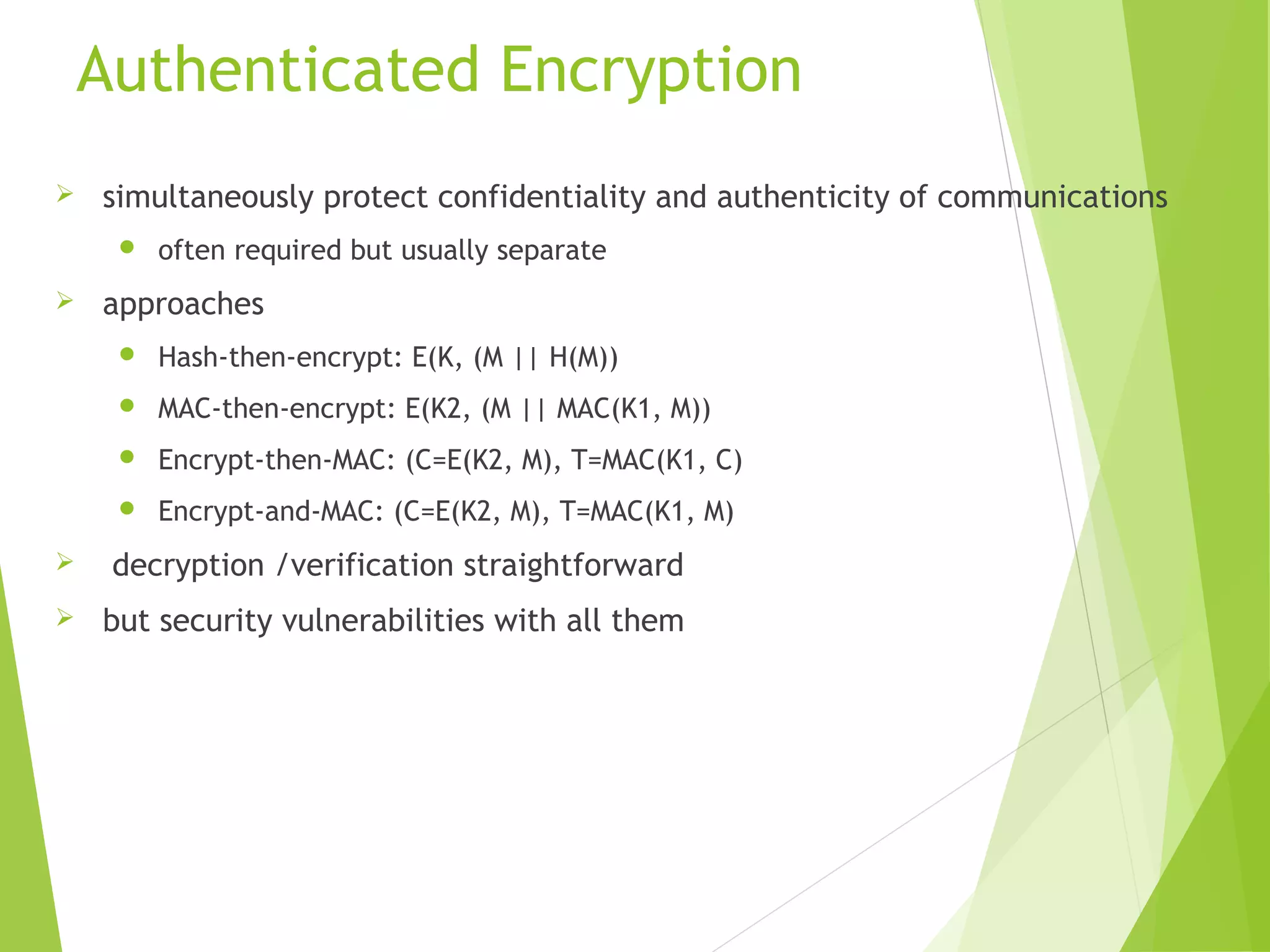
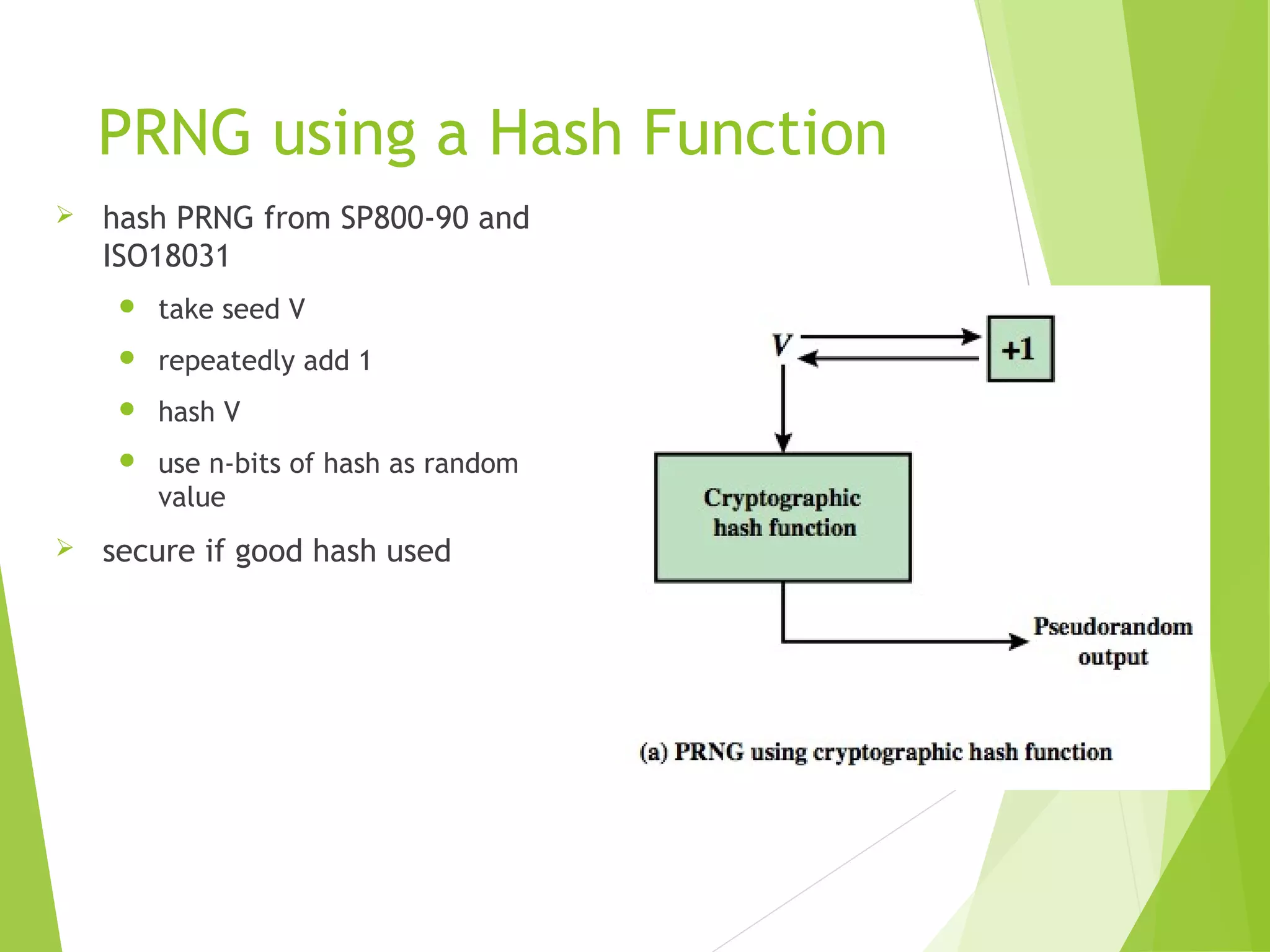
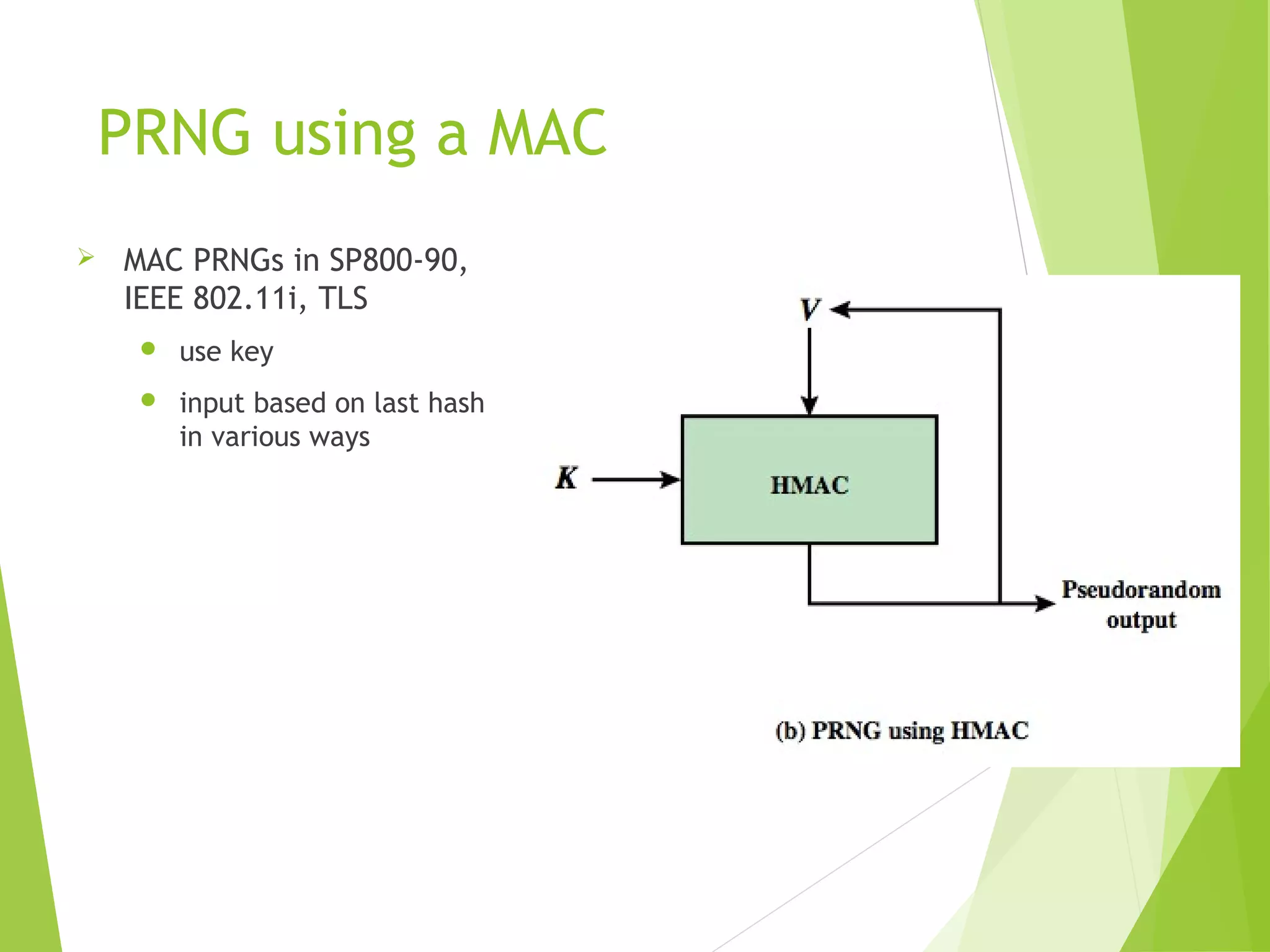
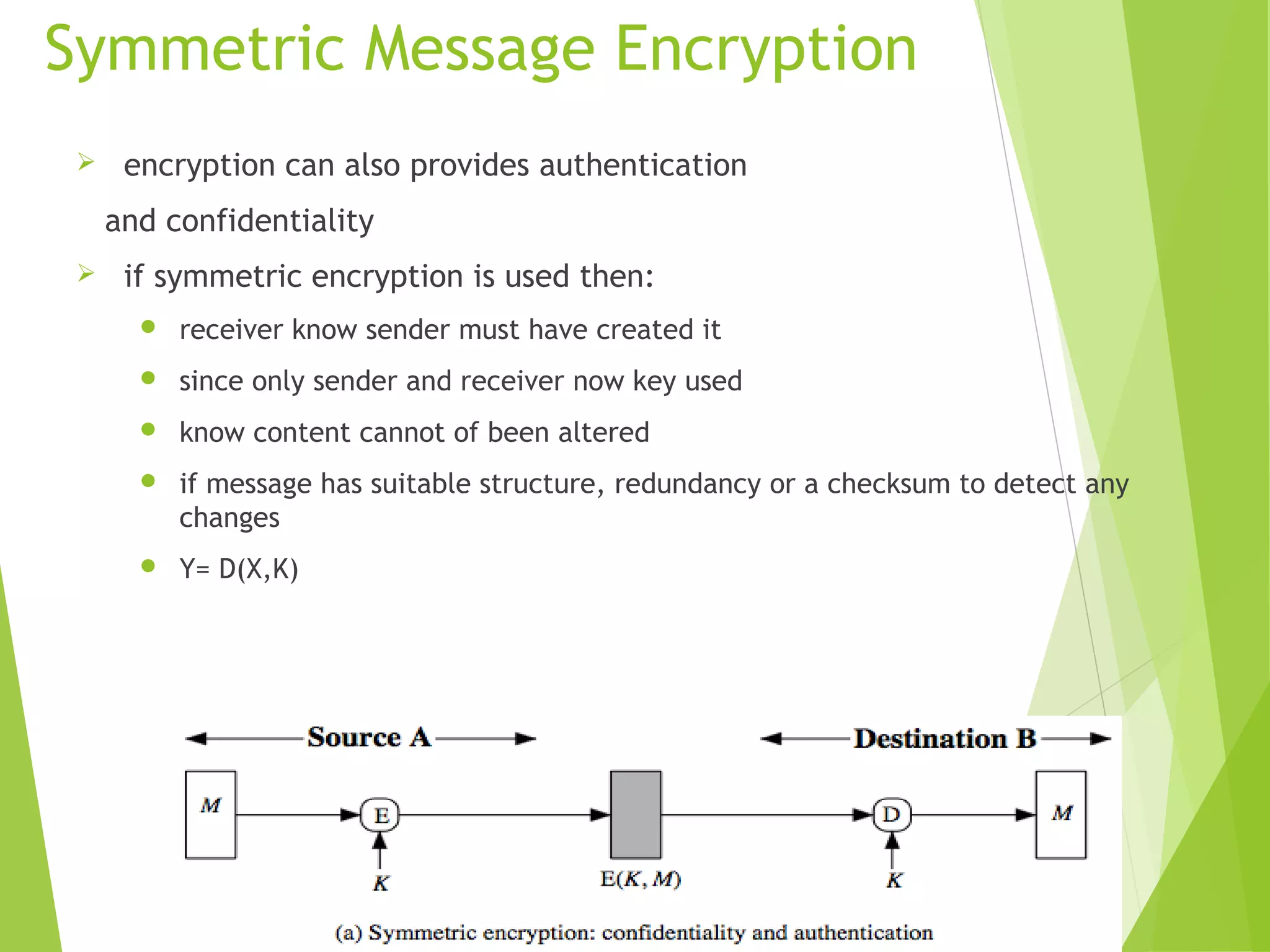
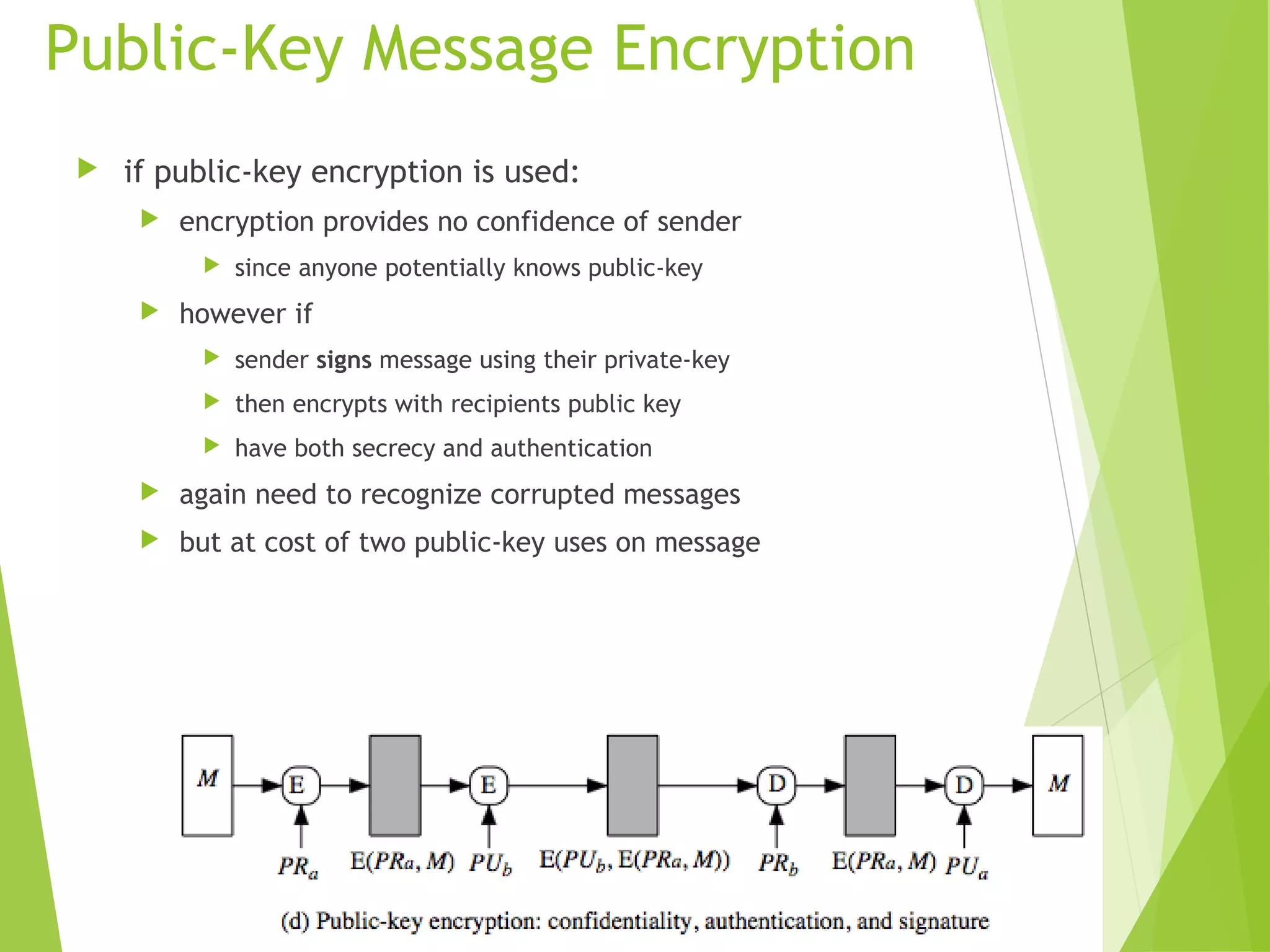
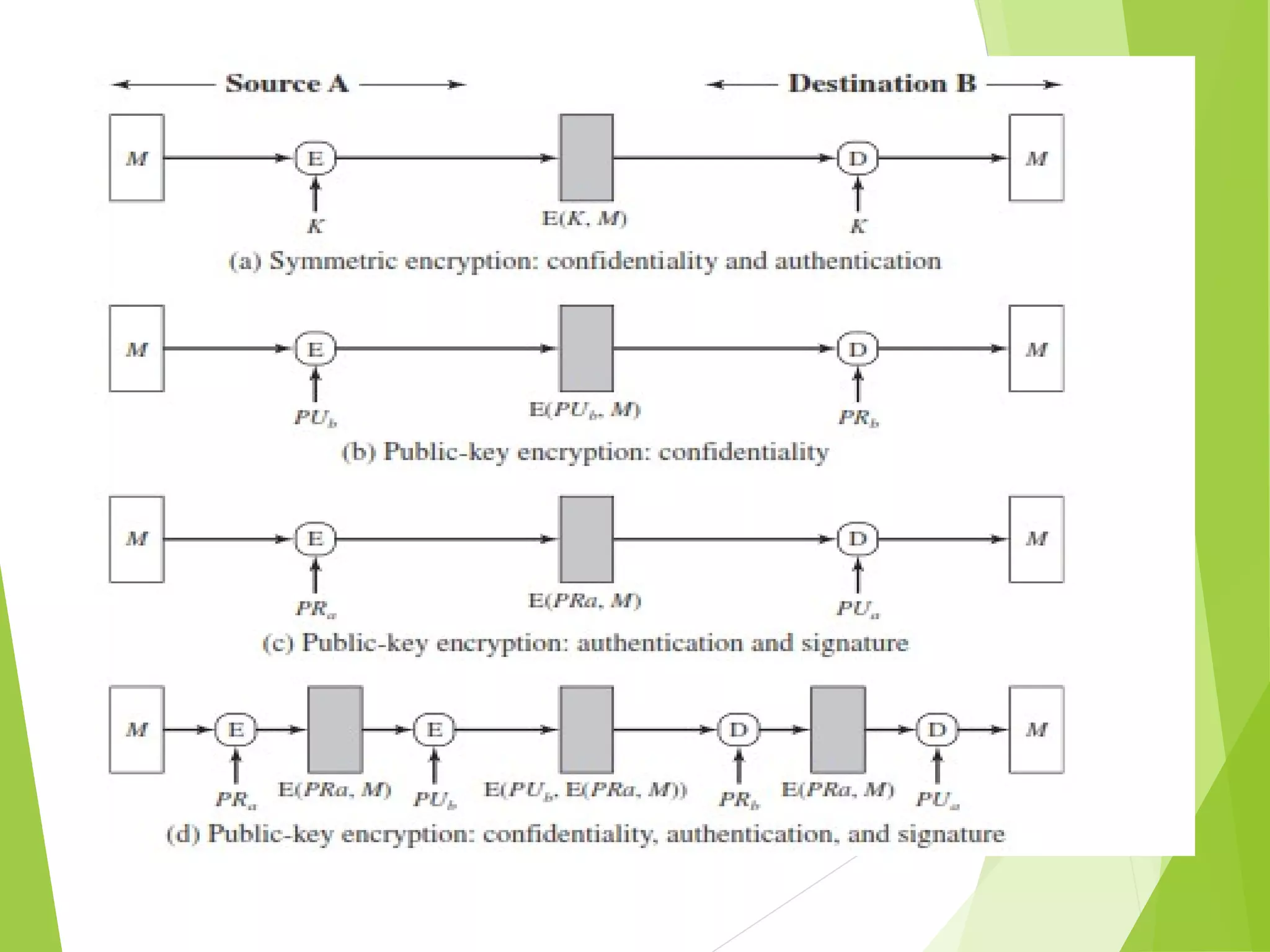
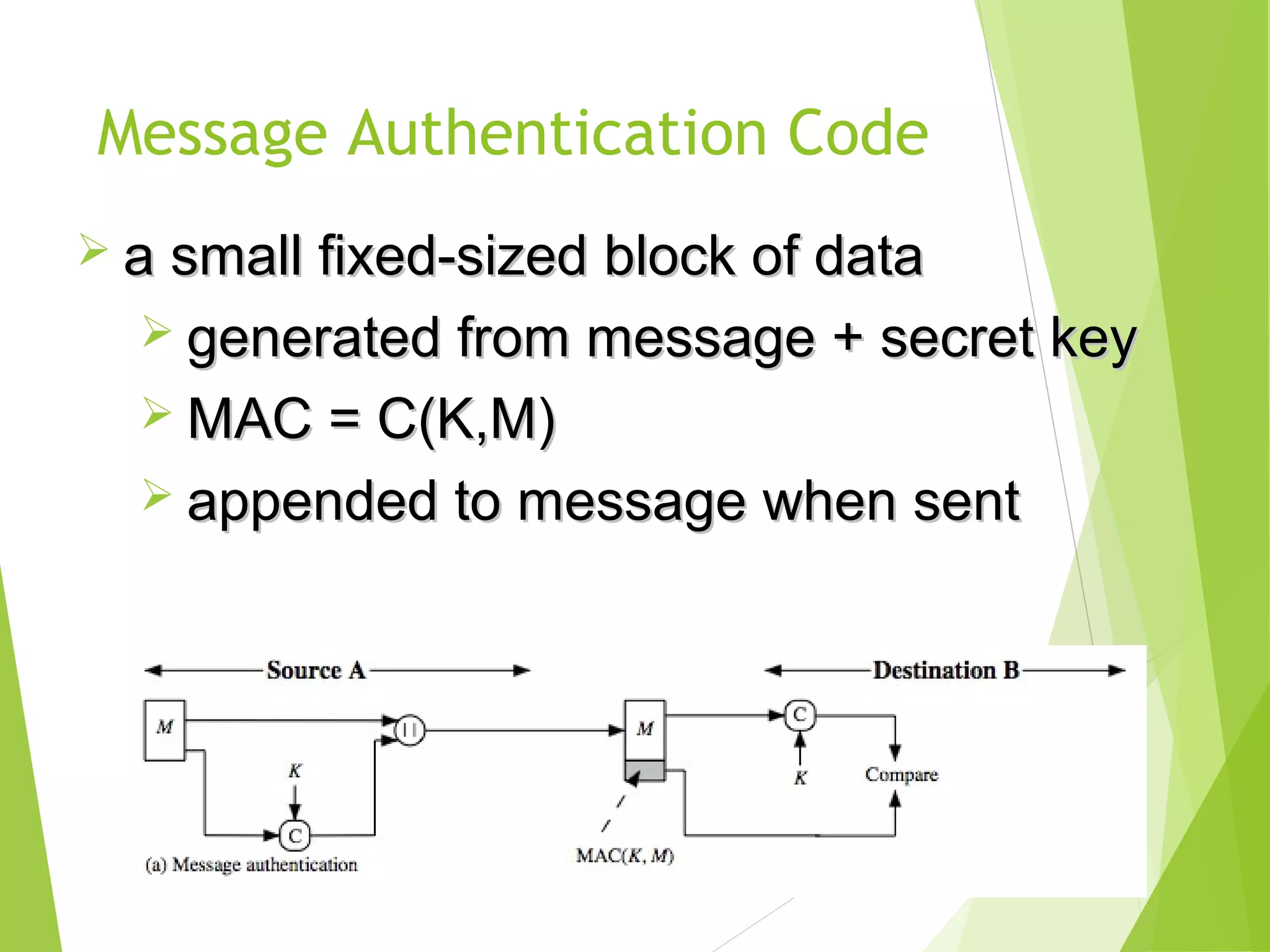
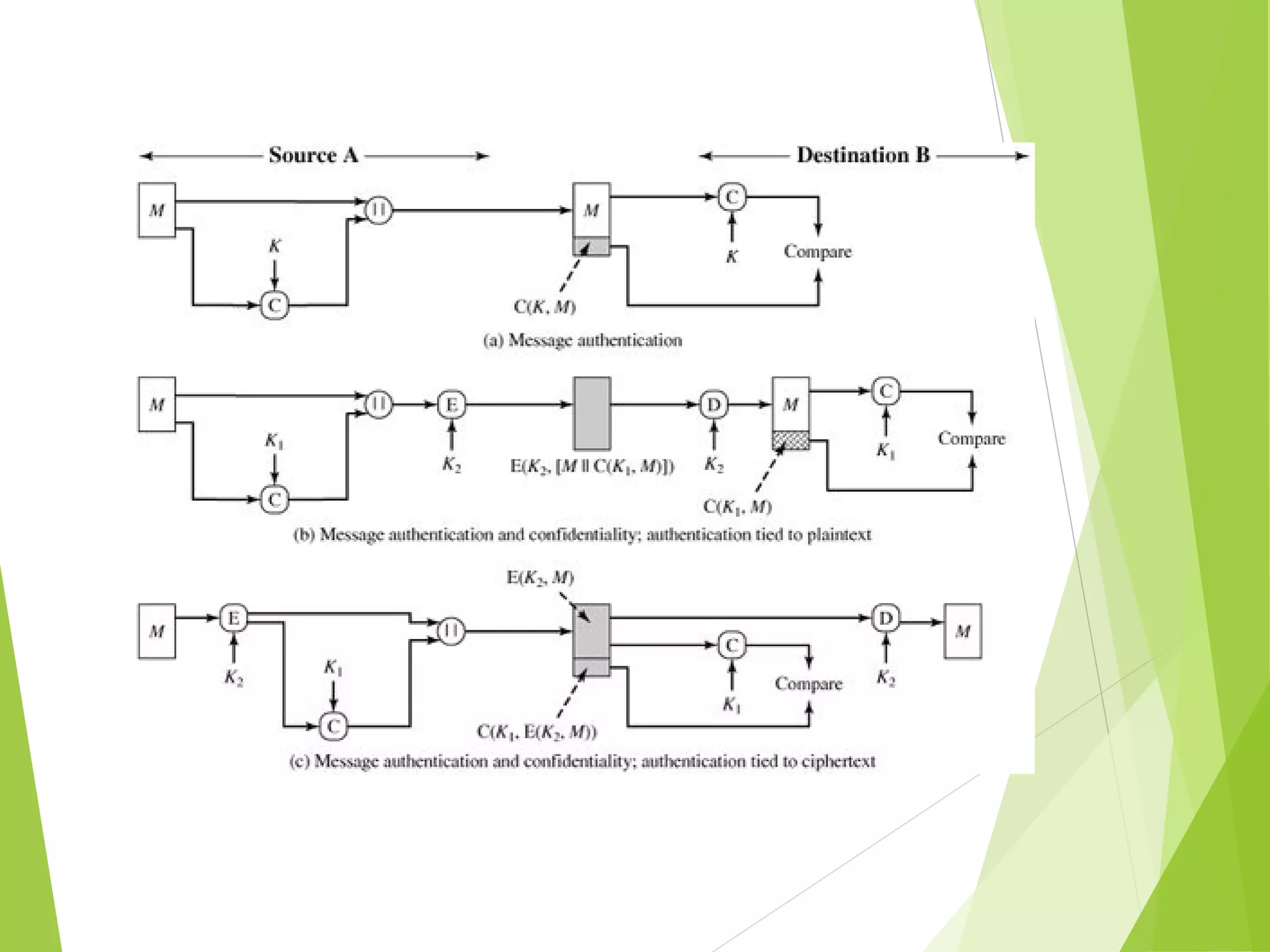
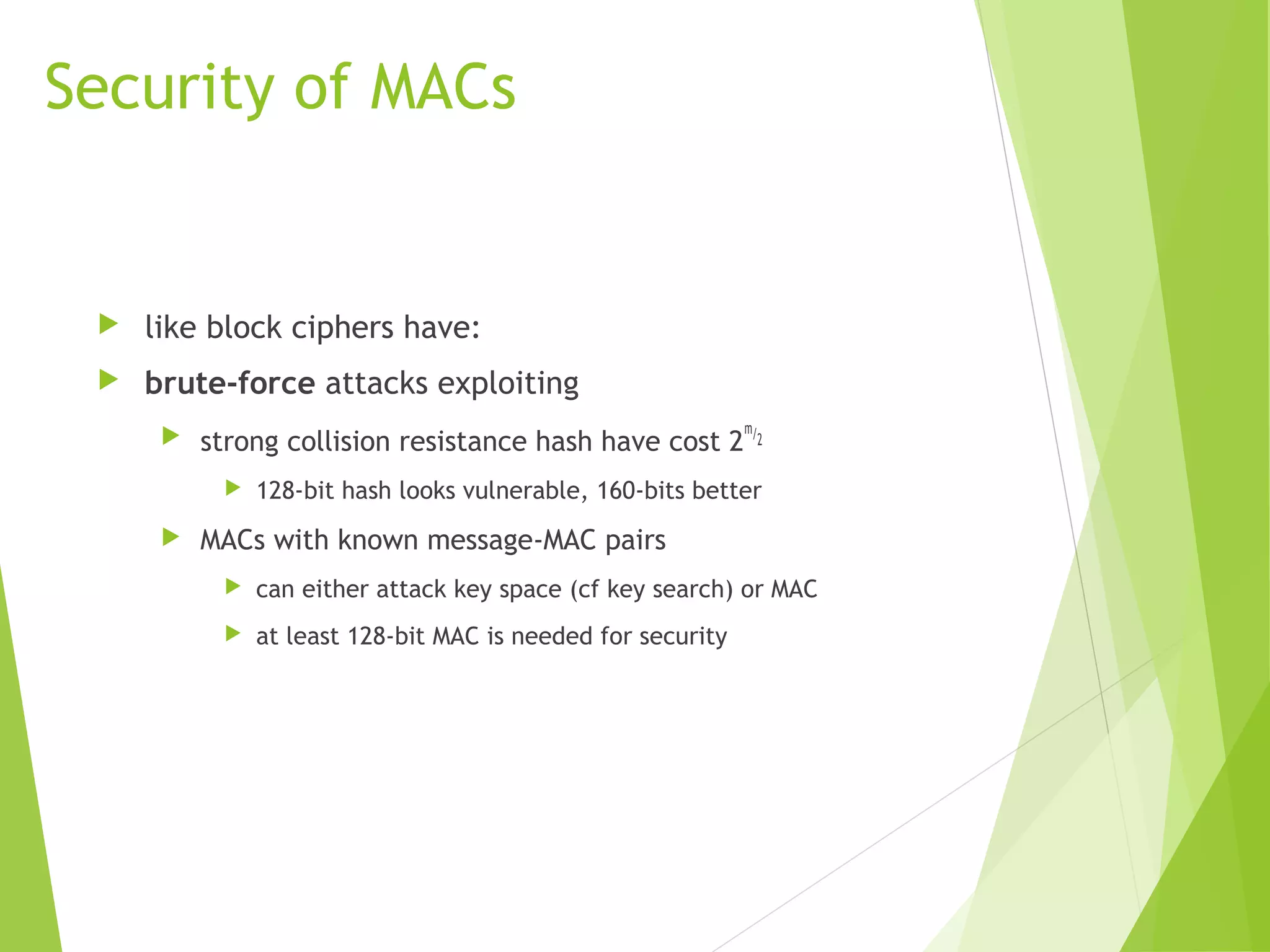
The document discusses message authentication codes (MACs), which verify the integrity of messages and confirm the identity of the sender. It explains the security requirements for MACs, different methods of generating them, such as using cryptographic hash functions or symmetric block ciphers, and introduces HMAC and CMAC. Additionally, it covers the role of pseudorandom number generation in the context of MACs and the importance of maintaining confidentiality and authenticity in communications.












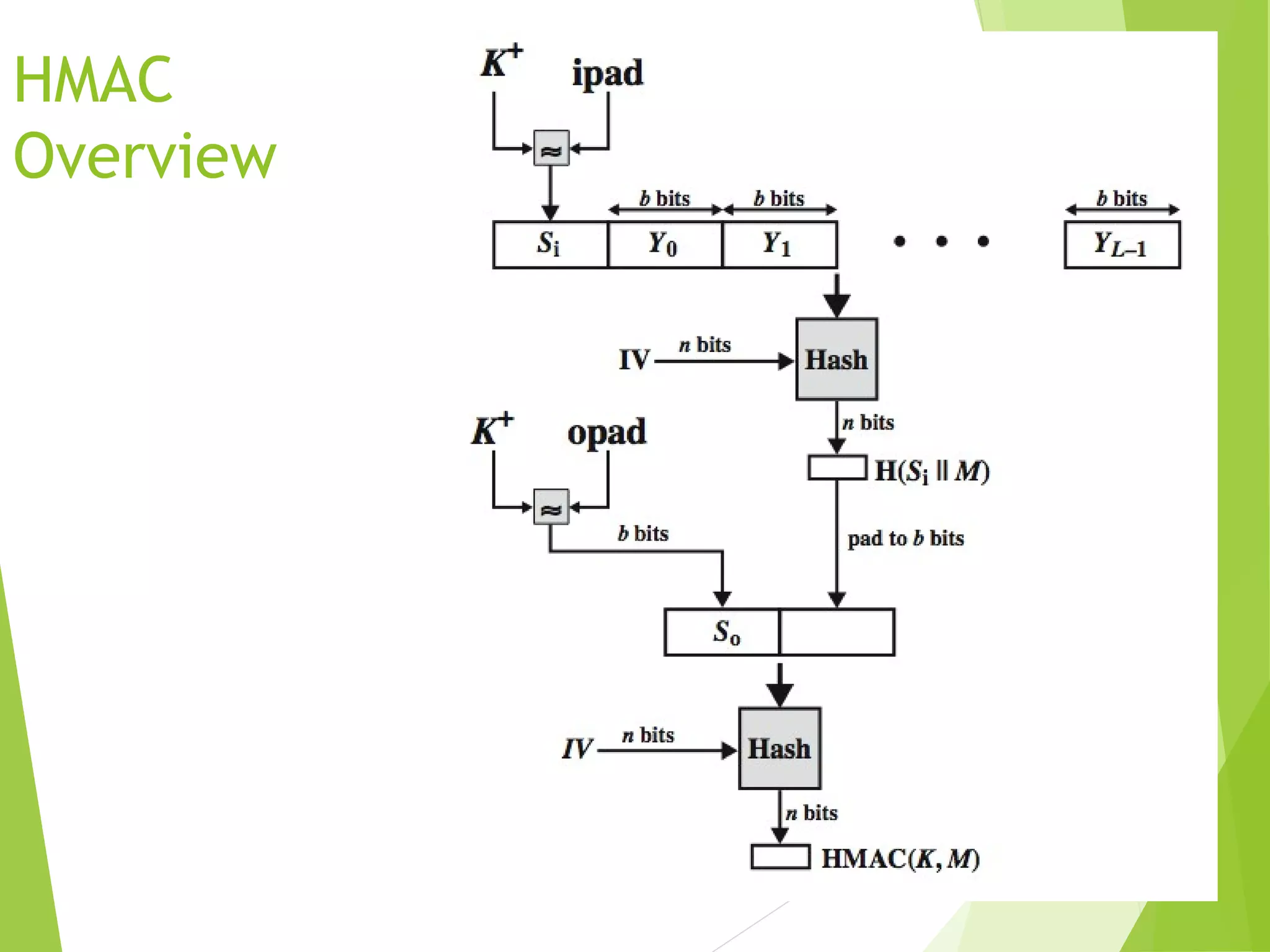
![HMAC
specified as Internet standard RFC2104
uses hash function on the message:
HMACK(M)= Hash[(K+
XOR opad) ||
Hash[(K+
XOR ipad) || M)] ]
where K+
is the key padded out to size
opad, ipad are specified padding constants
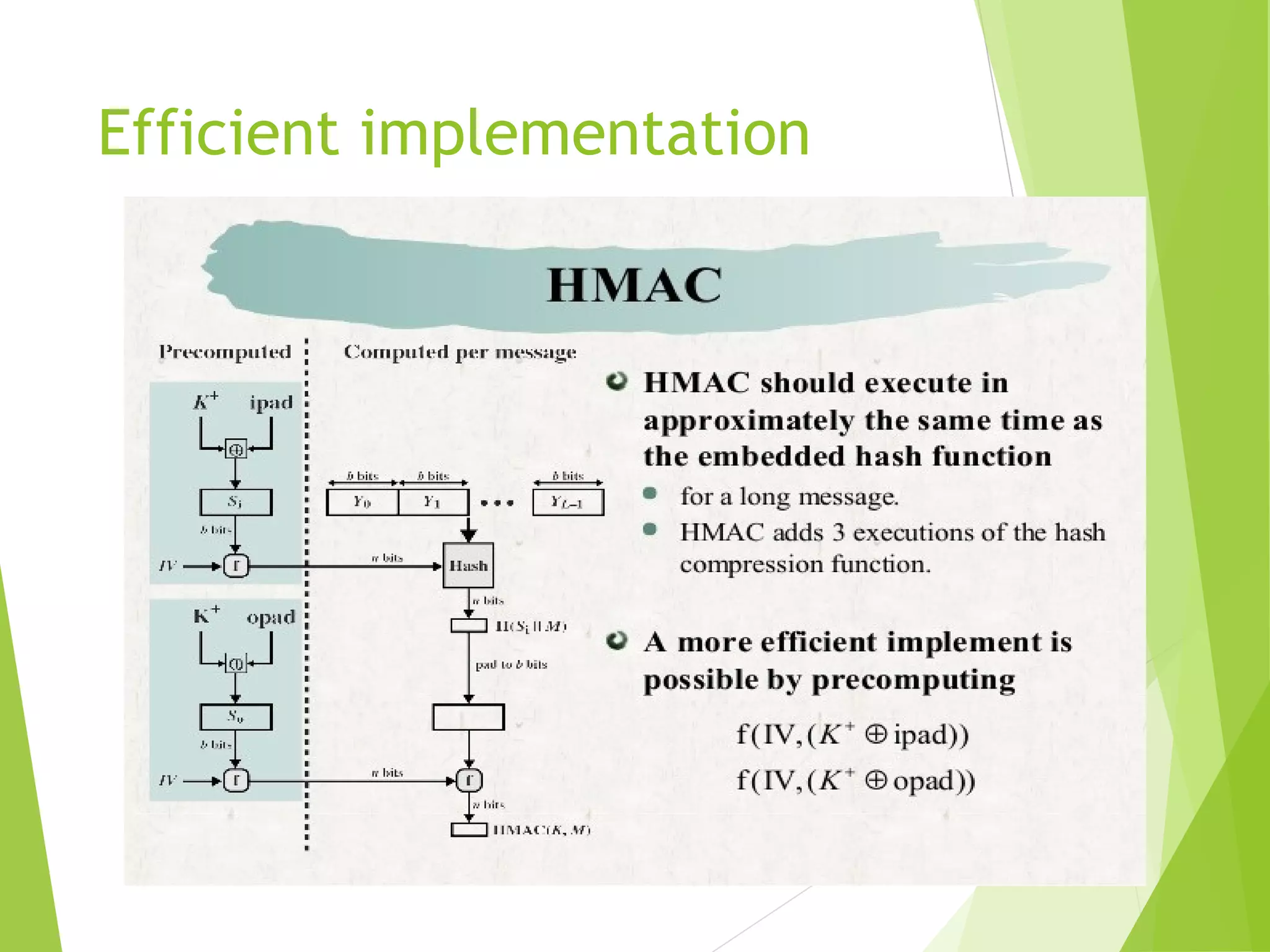
overhead is just 3 more hash calculations
than the message needs alone
any hash function can be used
eg. MD5, SHA-1, RIPEMD-160, Whirlpool](https://image.slidesharecdn.com/informationanddatasecuritycryptographyandnetworksecurity-170928114156/75/Information-and-data-security-cryptography-and-network-security-20-2048.jpg)