This document discusses cryptography in GSM networks. It provides background on common security requirements and introduces cryptography techniques like symmetric-key cryptography, public-key cryptography, and cryptographic hashes. It then discusses cryptography specifically used in GSM networks, including the A5/1 and A5/3 algorithms used for encryption. It notes issues with the security of these algorithms and proposes improving GSM network security.

























![Some Attacks on A5/1Some Attacks on A5/1
Passive Ciphertext-Only Attack[1]Passive Ciphertext-Only Attack[1]
Biased Birthday Attack[2]Biased Birthday Attack[2]
Random Subgraph Attack[2]Random Subgraph Attack[2]](https://image.slidesharecdn.com/cryptographyingsm-150302105551-conversion-gate01/75/Cryptography-in-GSM-37-2048.jpg)
![Possible Attack ScenariosPossible Attack Scenarios
Attacks on A5 can be in the following forms:[1]Attacks on A5 can be in the following forms:[1]
Call wire-tappingCall wire-tapping
Call HijackingCall Hijacking
Altering of SMSAltering of SMS
Call theft – Dynamic CloningCall theft – Dynamic Cloning](https://image.slidesharecdn.com/cryptographyingsm-150302105551-conversion-gate01/75/Cryptography-in-GSM-38-2048.jpg)

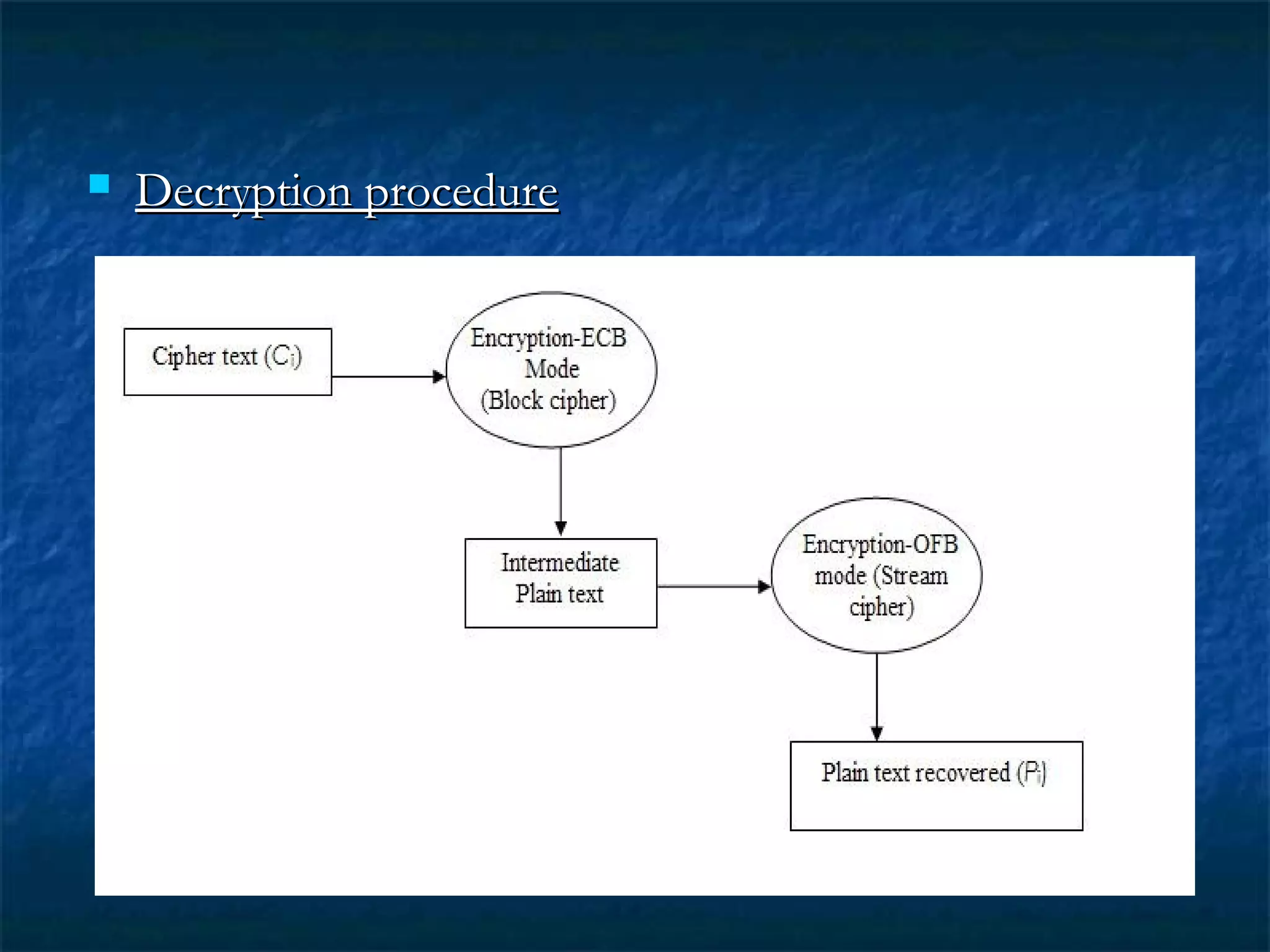

![ Reference:Reference:
[1]
[2]
[3] Lecture Notes of Haojin Zhu and Xiaodong Lin of the Department of Electrical and
Computer Engineering, University of Waterloo, Canada.
[4] Types & modes combined algorithm for data encryption and decryption by[4] Types & modes combined algorithm for data encryption and decryption by
D.M.A.B MailewaD.M.A.B Mailewa,, T.D.B WeerasingheT.D.B Weerasinghe,, C.A MunasingheC.A Munasinghe,, Piyal J. PereraPiyal J. Perera of theof the
Department of Computer Engineering, University of Peradeniya.Department of Computer Engineering, University of Peradeniya.](https://image.slidesharecdn.com/cryptographyingsm-150302105551-conversion-gate01/75/Cryptography-in-GSM-43-2048.jpg)
