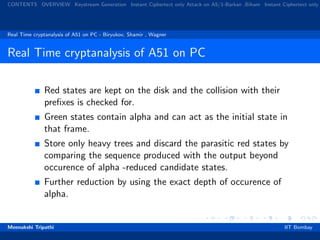
This document analyzes cryptographic attacks on the A5/1 stream cipher used in GSM cellular networks. It first describes the structure and key generation process of A5/1. It then summarizes several known attacks on A5/1 including:
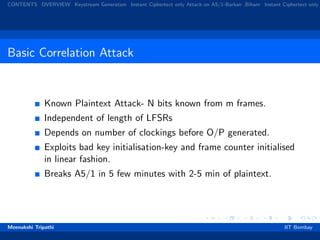
1) A man-in-the-middle attack developed by Barkan and Biham that recovers the key through a known plaintext attack on the weaker A5/2 cipher and an active attack on A5/1.
2) A time-memory tradeoff attack developed by Golic that recovers the key by building a tree of possible internal states.
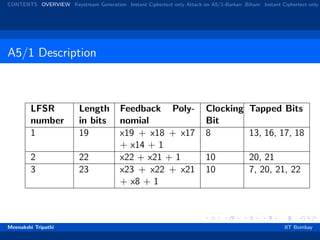
3) An attack developed by Biryukov, Shamir, and

![CONTENTS OVERVIEW Keystream Generation Instant Ciphertext only Attack on A5/1-Barkan ,Biham Instant Ciphertext only
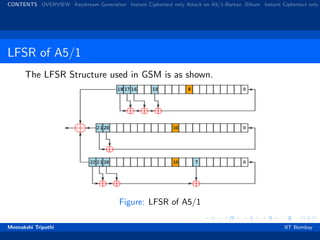
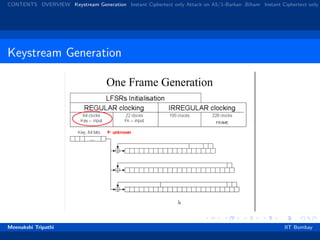
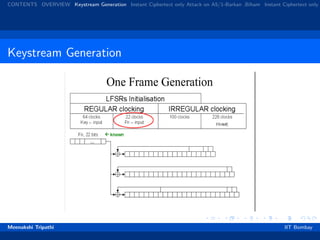
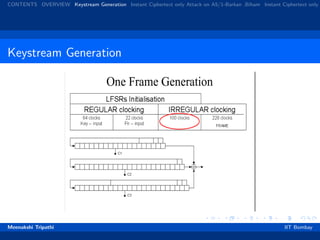
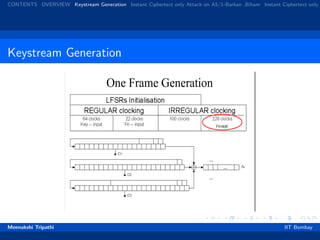
Steps for Key Generation
All 3 registers are zeroed.
64 cycles (regular clocking): R[0] = R[0] ⊗ Kc [i]
22 cycles (regular clocking): R[0] = R[0] ⊗ Fc [i].
100 cycles (majority rule clocking), output discarded.
228 cycles (majority rule clocking) to produce the output bit
sequence.
Meenakshi Tripathi IIT Bombay](https://image.slidesharecdn.com/cryptoppt-130902011138-phpapp01/85/Cryptoppt-5-320.jpg)
![CONTENTS OVERVIEW Keystream Generation Instant Ciphertext only Attack on A5/1-Barkan ,Biham Instant Ciphertext only
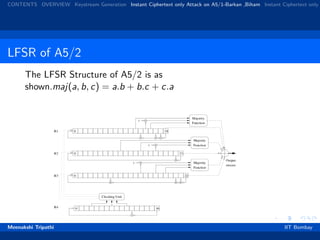
Structure of A5/2
A5/2 is much weaker cipher, used as base for man in the
middle attack on A5/1
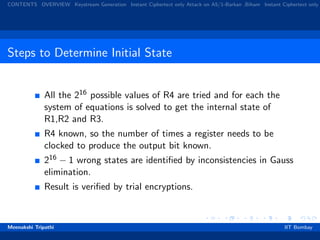
A5/2 has 4 LFSRs -R1, R2, R3 and R4 of length 19, 22, 23, 17.
R4 Controls the clocking of the other three registers with bits
R4[3], R4[7] and R4[10].
Output is: XOR of majority output of 3 registers and the
MSB of each register.
One bit of each register is forced to be 1 after initialisation.
Meenakshi Tripathi IIT Bombay](https://image.slidesharecdn.com/cryptoppt-130902011138-phpapp01/85/Cryptoppt-12-320.jpg)

![CONTENTS OVERVIEW Keystream Generation Instant Ciphertext only Attack on A5/1-Barkan ,Biham Instant Ciphertext only
Cryptanalysis of alleged A5 Stream cipher-Golic
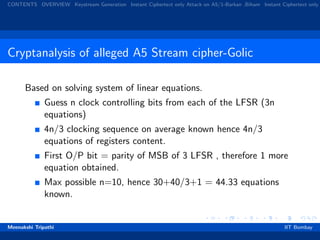
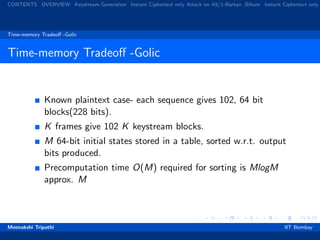
Build a tree with valid options corresponding to 3 inputs to
majority clock control function.
5 branches per node so on avg. 2.5 valid options for each
path.
By exhaustive search, on average consider 1/2 of the values to
get the remaining bits .
Initial state s[0] from s[101] by guessing the number of 1’s in
the clocking sequence.
Check the state by generating s[101] again.
Meenakshi Tripathi IIT Bombay](https://image.slidesharecdn.com/cryptoppt-130902011138-phpapp01/85/Cryptoppt-18-320.jpg)
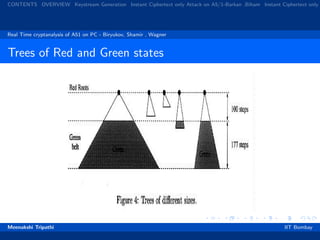
![CONTENTS OVERVIEW Keystream Generation Instant Ciphertext only Attack on A5/1-Barkan ,Biham Instant Ciphertext only
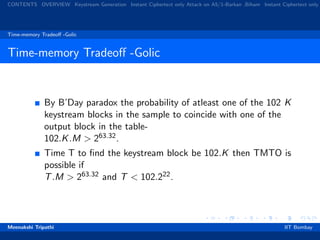
Comparison of Various Attacks
Attack Type Pre
compu-
tation
Analysis
Com-
plexity
Data
Com-
plexity
Memory
Complexi
Golic [1] TMTO 235.65 227.67 228.8 862 GB
Barkan,Biham
[4]
Man
in the
middle
Nil 247 Ciphertext
only
M = 228.8
Biryukov,
Shamir [3]
TMTO 248 2 minutes 214.7 146 GB
Biham,
Dulkelman[2]
TMTO 238 239.91 220.8 32 GB
Meenakshi Tripathi IIT Bombay](https://image.slidesharecdn.com/cryptoppt-130902011138-phpapp01/85/Cryptoppt-29-320.jpg)