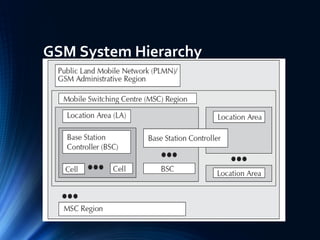
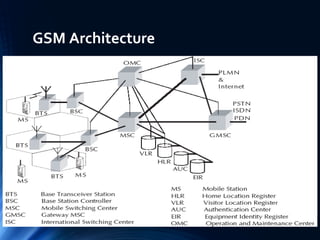
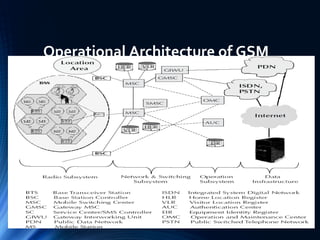
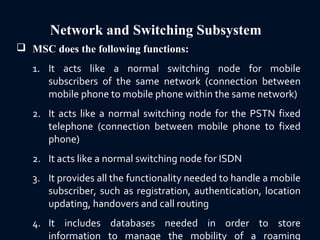
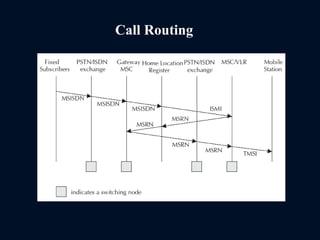
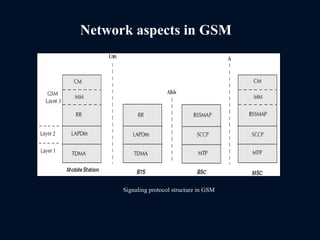
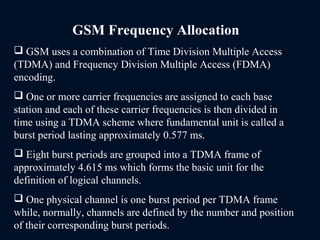
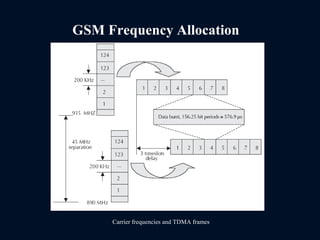
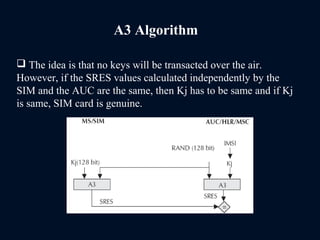
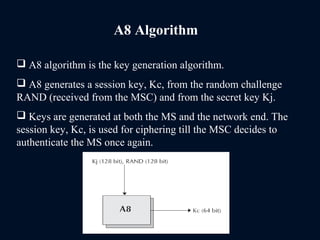
The document provides a comprehensive overview of the Global System for Mobile Communications (GSM), detailing its architecture, key components, and functionalities such as call routing and SMS services. It describes the use of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access (TDMA), the roles of Mobile Switching Centers (MSC), and the databases like Home Location Register (HLR) and Visitor Location Register (VLR) essential for call processing. The document also touches on GSM security, mobile station identification, and the operational aspects of SMS within the network.