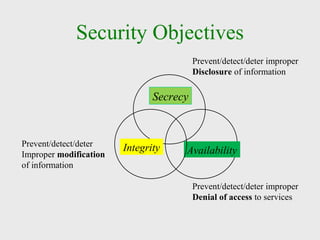
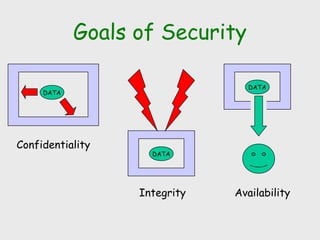
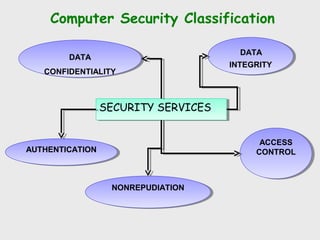
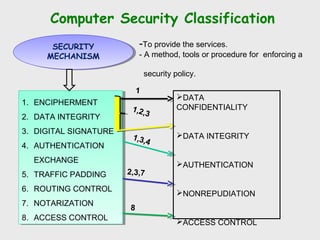
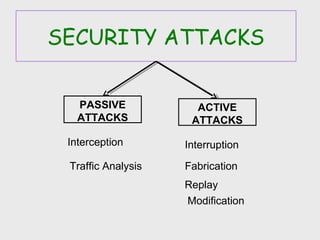
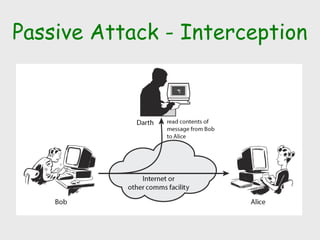
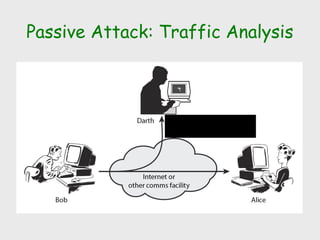
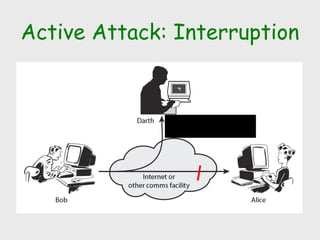
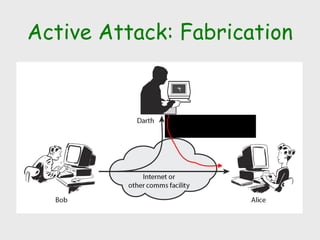
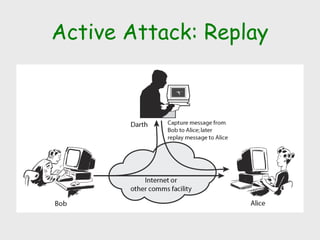
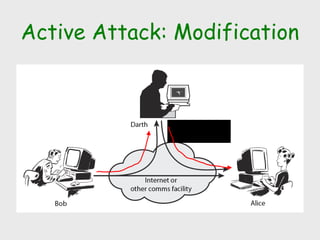
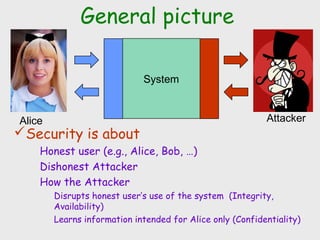
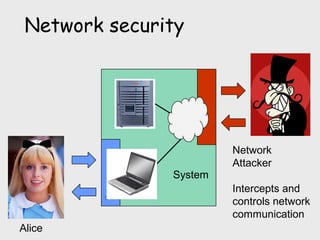
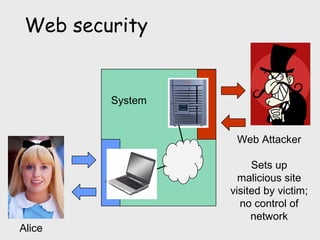
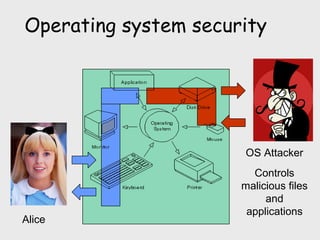
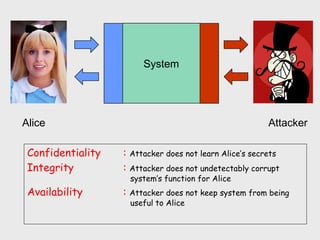
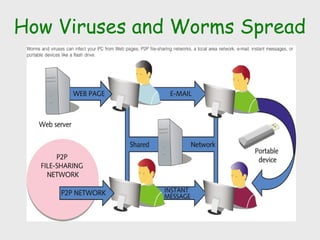
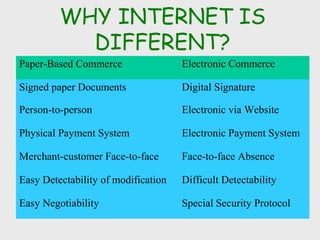
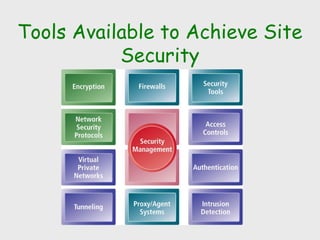
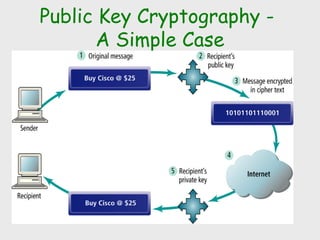
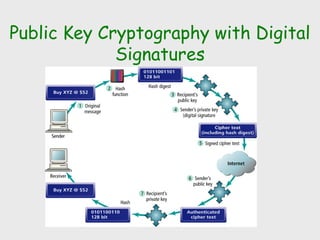
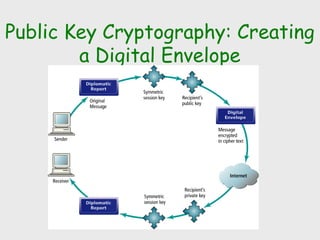
The document discusses computer security, including its objectives of secrecy, availability, and integrity. It covers security policies, threats like intercepted emails and unauthorized access. The goals of security are outlined as data confidentiality, integrity, and availability. Security mechanisms are used to provide services like confidentiality, integrity, authentication, and access control. Both passive attacks like interception and active attacks like modification are described. The document also discusses security classification, attacks, and tools to achieve security like encryption, public key cryptography, secure communication channels, firewalls, and proxies. It notes the tension between security and other values like ease of use and public safety.