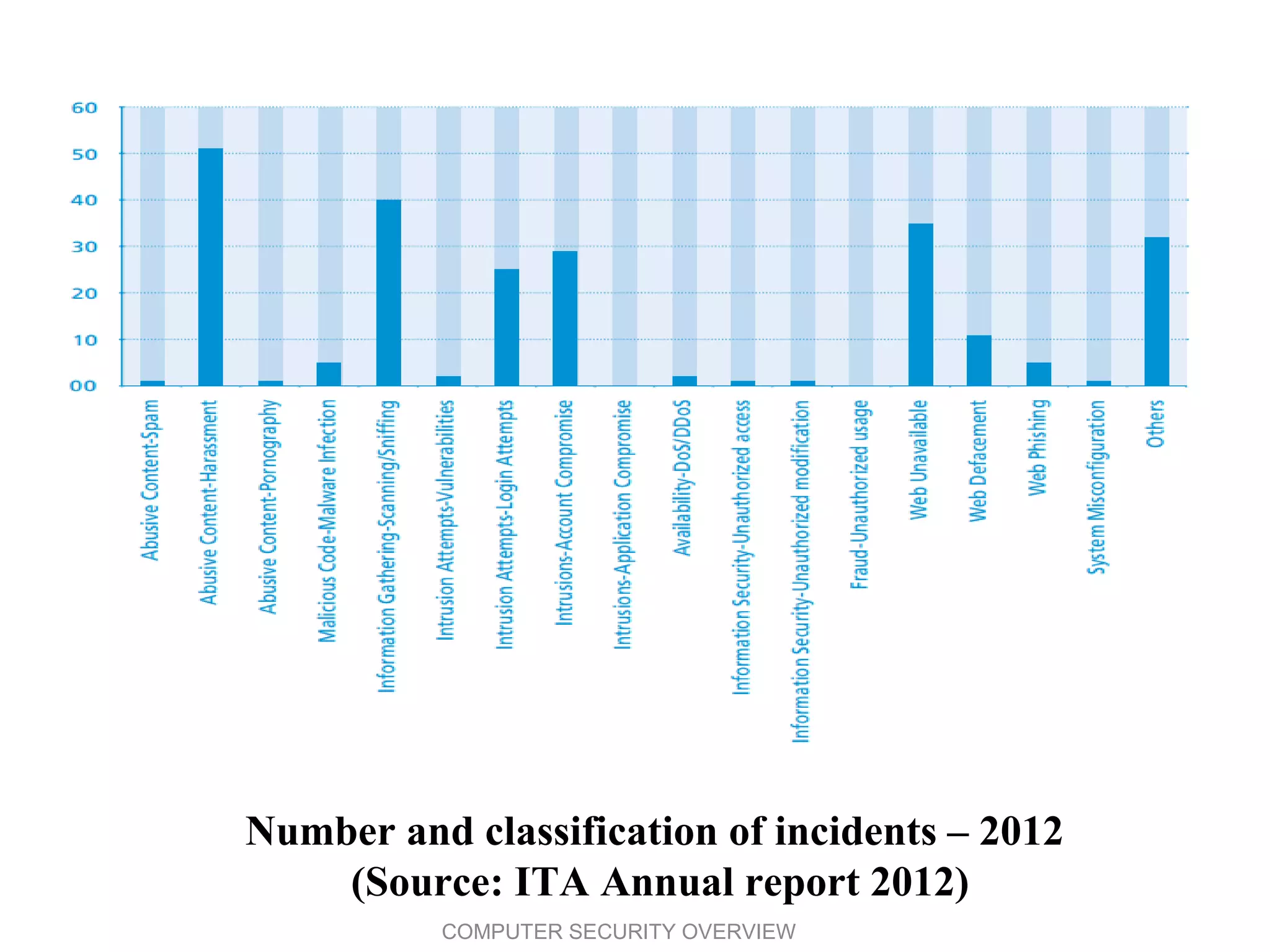
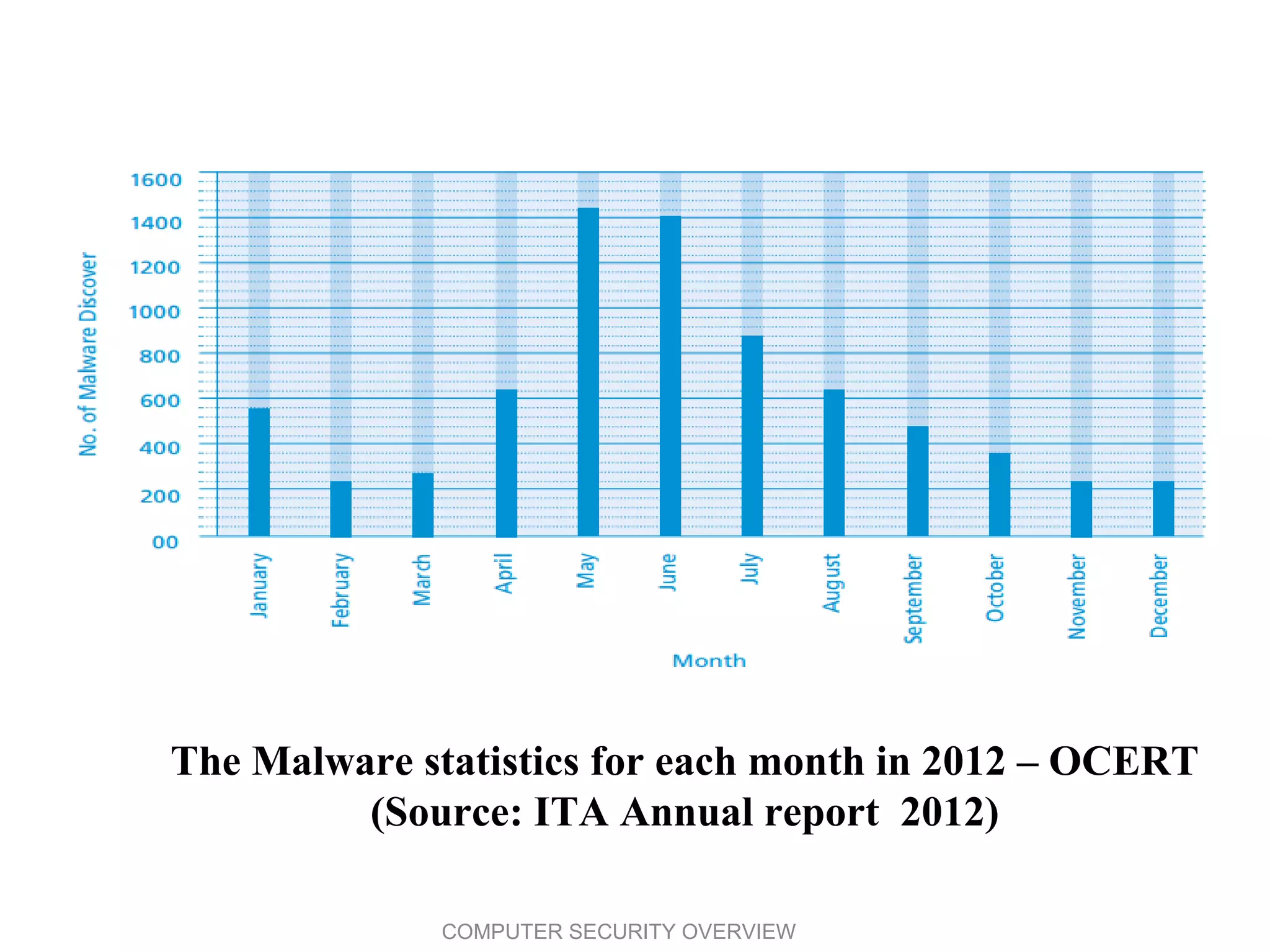
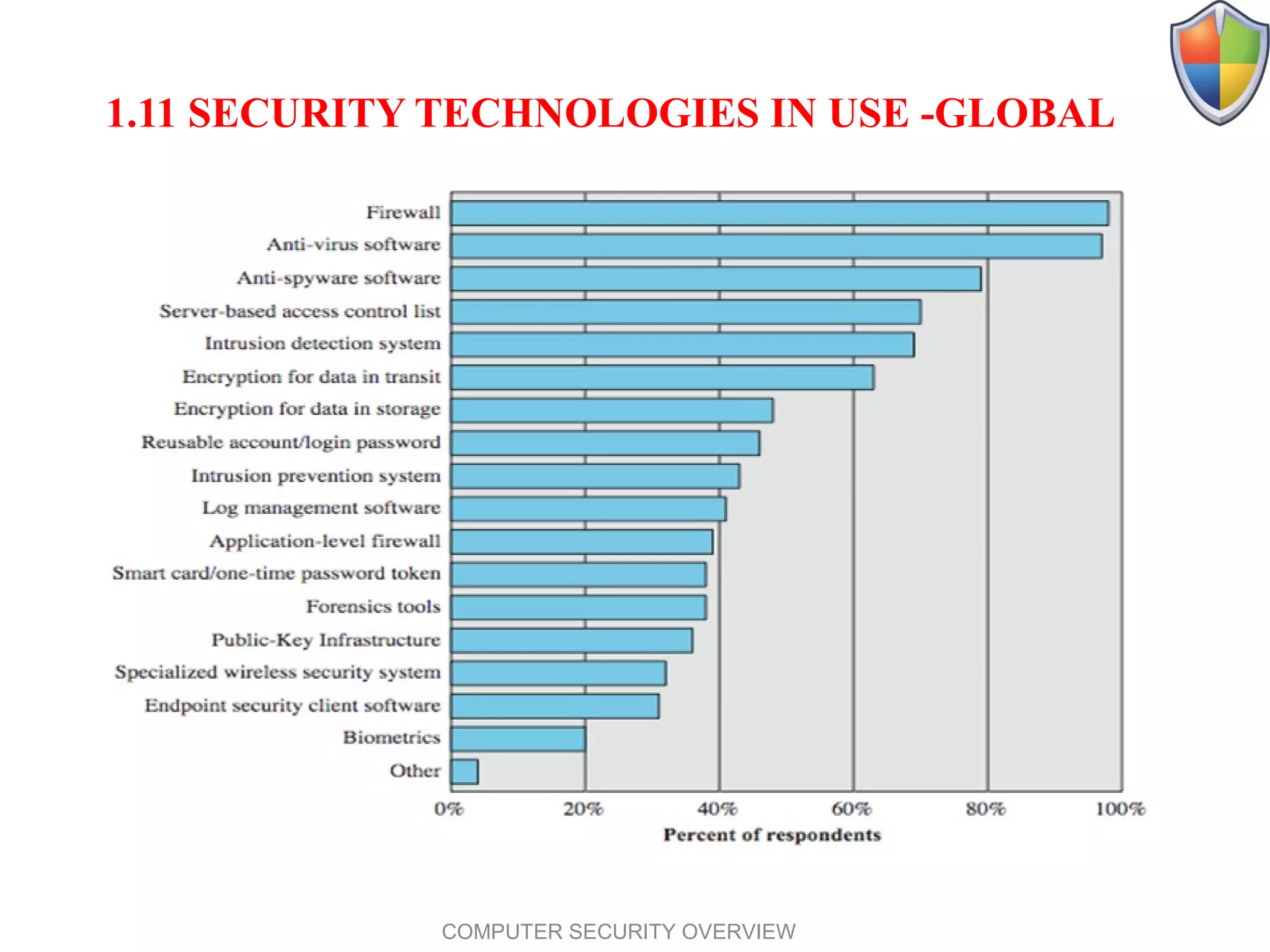
The document provides an overview of computer security, emphasizing the core concepts of confidentiality, integrity, and availability (CIA). It also outlines key security terms, vulnerabilities, threats, attack types, and countermeasures, along with statistics on cybercrime incidents in Oman and global security technologies. Overall, the document serves as a comprehensive guide to understanding the landscape of computer security and the challenges faced in protecting information systems.