1. The document defines computer security as protecting computer systems and information from harm, theft, and unauthorized use through preventing and detecting unauthorized computer system access.
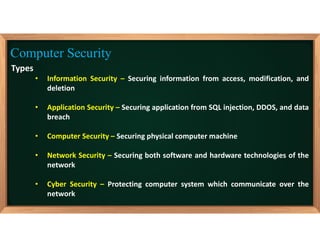
2. It discusses various types of computer security including information, application, computer, network, and cyber security and outlines common computer security threats like viruses, worms, phishing, rootkits, and key loggers.
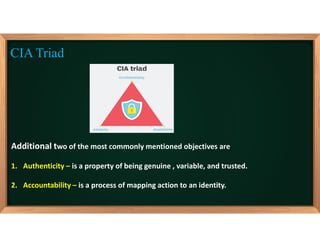
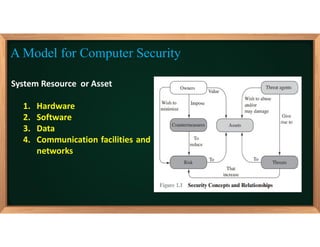
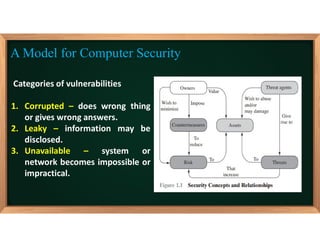
3. The document also covers fundamental computer security objectives of confidentiality, integrity, and availability and related terminology like adversaries, attacks, vulnerabilities, and security policies.