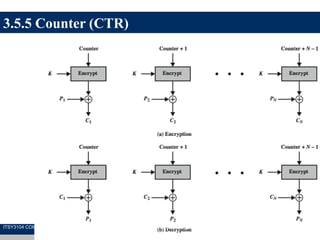
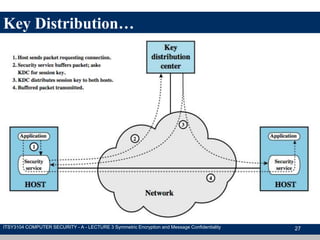
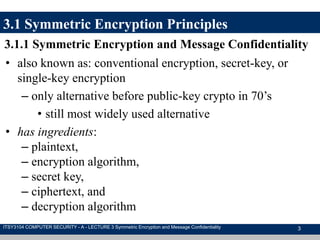
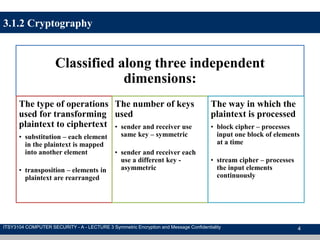
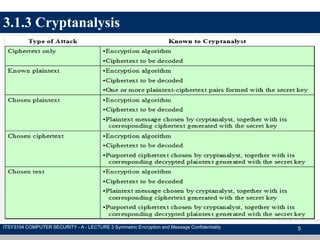
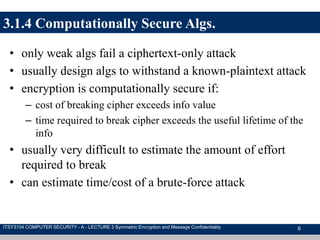
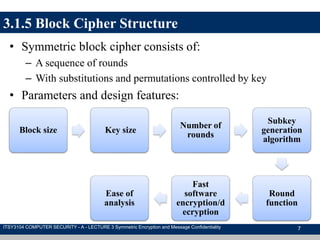
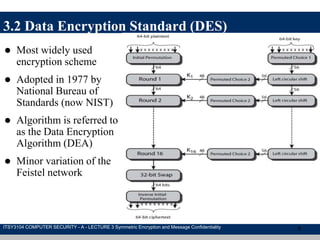
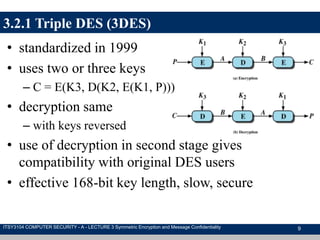
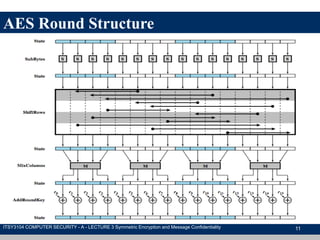
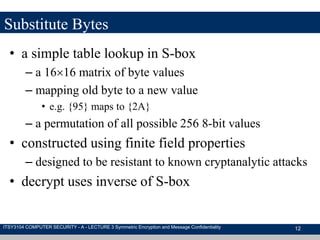
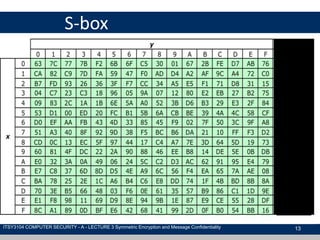
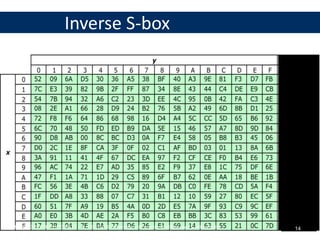
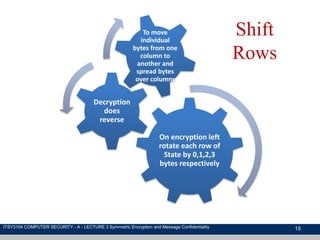
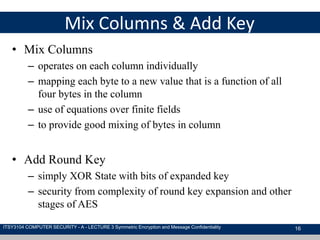
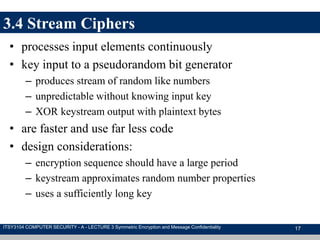
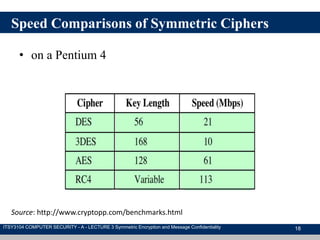
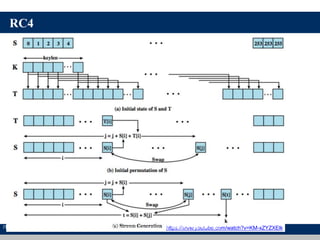
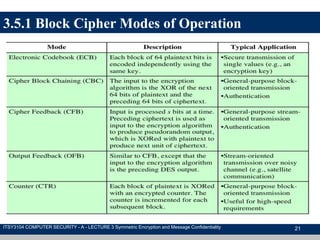
The document discusses symmetric encryption and message confidentiality, defining it as a conventional and widely-used method of encryption that relies on a single shared key for both encryption and decryption. It covers key concepts including the Data Encryption Standard (DES), Advanced Encryption Standard (AES), and various cipher modes such as ECB and CBC, along with their operational principles and security characteristics. Additionally, it highlights the importance of key distribution methods for maintaining encryption security.


![3.5.3 Cipher Block Chaining (CBC)
23
Cj = E(K, [Cj–1 Pj])
ITSY3104 COMPUTER SECURITY - A - LECTURE 3 Symmetric Encryption and Message Confidentiality](https://image.slidesharecdn.com/symmetricencryptionandmessageconfidentiality-170914061437/85/Symmetric-encryption-and-message-confidentiality-23-320.jpg)
![3.5.4 Cipher Feedback (CFB)
24
C1 = P1 Ss[E(K, IV)]
ITSY3104 COMPUTER SECURITY - A - LECTURE 3 Symmetric Encryption and Message Confidentiality](https://image.slidesharecdn.com/symmetricencryptionandmessageconfidentiality-170914061437/85/Symmetric-encryption-and-message-confidentiality-24-320.jpg)