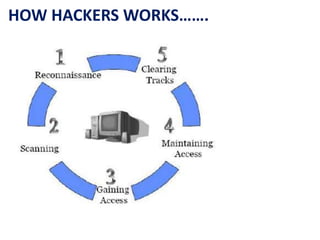
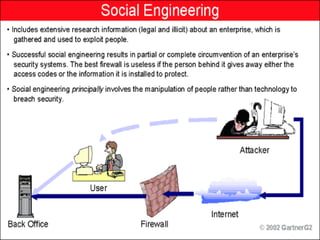
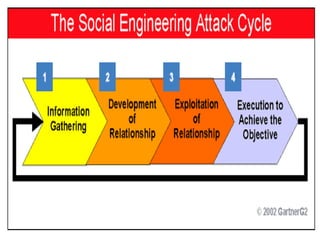
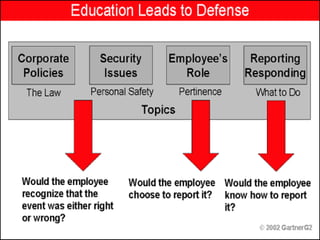
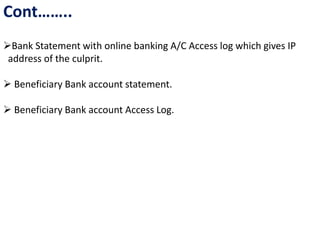
This document discusses cyber ethics and hacking. It begins with an introduction to why security is important and defines hacking. It then discusses different types of hackers like hackers, crackers, phreaks, and script kiddies. The document outlines strategies for ethical hackers and malicious hackers. It also discusses the importance of vulnerability research and provides conclusions about security.